- Apr 25, 2013
- 5,355
Malware adds new targets, the US is most affected country
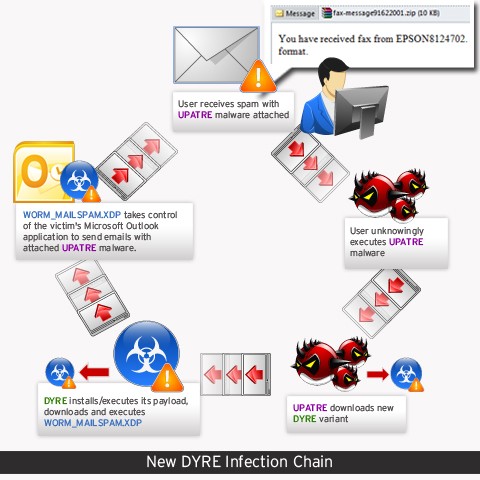
A recent version of Dyre banking Trojan has been observed to download on the infected computer a worm that uses Microsoft Outlook to compose email messages with Upatre malware downloader in the attachment.
The new infection chain is a repetitive cycle where Upatra reaches the system of a victim, downloads and installs Dyre, which in turn funnels in a worm that creates the messages with an attached copy of Upatre and sends them to a predefined list of recipients.
Malware self-destructs after doing its job
Security researchers at Trend Micro say that the contacts list of the victim is not used by the worm (detected by their products as WORM_MAILSPAM.XDP). Instead, it connects to a command and control (C&C) server that delivers all the necessary information. Among other parameters, this includes the list of recipients as well as the subject line and content of the message.
According to them, the worm initiates a self-destruct routine and deletes itself after the malicious emails have been sent.
“The malware uses the msmapi32.dll library (supplied by Microsoft Outlook) that to perform its mail-related routines perform its functions (e.g. Login, Send Mail, Attach Item),” says in a blog post on Friday Michael Marcos, threat response engineer at Trend Micro.
It uses SSL communication and command and control server in I2P
Also known as Dyreza, the banking Trojan now relies on multiple methods to prolong its activity.
Marcos notes that the new version of the malware uses the SSL cryptographic protocol to secure all its communication with the C&C server.
The addresses for the remote command machines are hard-coded in the malware, but it seems that the authors have also included a domain generation algorithm (DGA) to create a list of multiple domains that hide the real C&C server.
Furthermore, now Dyre has a C&C machine in the I2P (Invisible Internet Project) anonymity network. Similar to Tor, addresses in I2P cannot be accessed via a regular web browser, and to achieve anonymity, the connections are encrypted and run through multiple randomly selected machines before reaching its destination.
This communication tactic was also observed by Ronnie Tokazowski from PhishMe, whosaid that at the time of his analysis interacting with the I2P node resulted in failure, as no response was returned from the anonymous server.
Apart from the freshly included evasion strategies, researchers at Trend Micro claimed that the latest Dyre banking Trojan had expanded the number of targets to 355, most of the new ones relating to online bitcoin wallets and financial institutions.
Telemetry data from the security company reveals that the US is the most affected country in January, recording 68% of the infections. It is followed by Canada (10%) and Chile (4%).
