silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,159
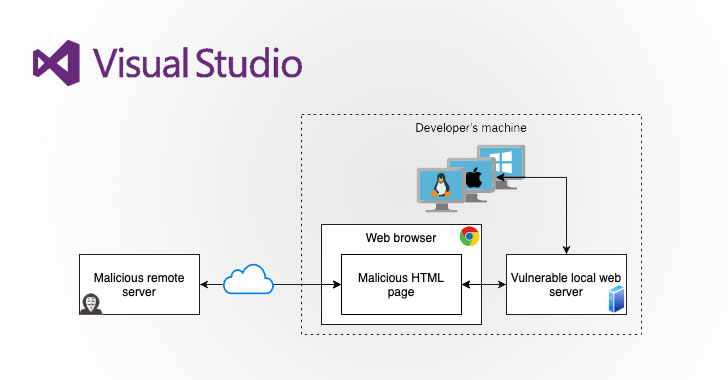
Severe security flaws uncovered in popular Visual Studio Code extensions could enable attackers to compromise local machines as well as build and deployment systems through a developer's integrated development environment (IDE).
The vulnerable extensions could be exploited to run arbitrary code on a developer's system remotely, in what could ultimately pave the way for supply chain attacks.
Some of the extensions in question are "LaTeX Workshop," "Rainbow Fart," "Open in Default Browser," and "Instant Markdown," all of which have cumulatively racked up about two million installations between them.
"Developer machines usually hold significant credentials, allowing them (directly or indirectly) to interact with many parts of the product," researchers from open-source security platform Synk said in a deep-dive published on May 26. "Leaking a developer's private key can allow a malicious stakeholder to clone important parts of the code base or even connect to production servers."
VS Code extensions, like browser add-ons, allow developers to augment Microsoft's Visual Studio Code source-code editor with additional features like programming languages and debuggers relevant to their development workflows. VS Code is used by 14 million active users, making it a huge attack surface.
Newly Discovered Bugs in VSCode Extensions Could Lead to Supply Chain Attacks
Researchers Uncover Bugs in VSCode Extensions That Could Lead to Supply Chain Attacks
