L
LabZero
Thread author
Hijack Hunter is a free application that deals with scan PC content organizing the various data collected. Hijack Hunter is a very useful application about recognition of the threats that may be present. This software is capable of detecting only the most important data, the ones that allow you to control which areas of the operating system infected by a malware.
It is essential to start it with administrator rights.
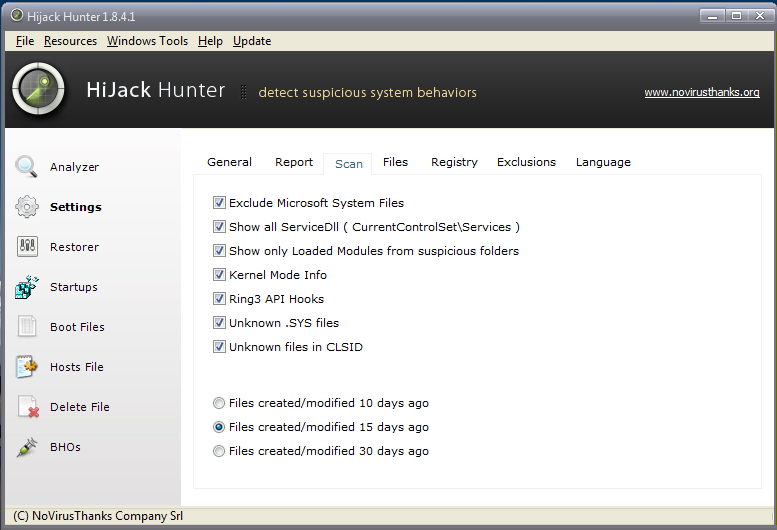
Perhaps the most interesting tab is "Scan": Here you can customize the "depth" of scans from Hijack Hunter. By default (recommended), the program exclude, from the report produced, all those files that are closely related to the operation of the OS or that are otherwise known components for Microsoft applications (Microsoft System Files).
This box, if checked, prevents Hijack Hunter show, in the log file generated after the scan in the form of text files, processes known as explorer.exe or svchost.exe.
The program can show the loaded modules from folders that appear suspicious and It is then able to perform a "kernel mode" control. By activating the option "Kernel Mode Info" Hijack Hunter will install its own (. sys) driver to analysis of what is happening to kernel level.
I'm going to try to explain, briefly, what is this control to understand the complexity work of this little tool. Information in memory, can be divided into two categories: "data" and "code".
The "data" refers to the bytes that are not executed. Some examples are data structures that are directly related to the operation of the kernel of the system or data for a Word document being drafted. The data is usually stored in memory regions called "heap", "stack" or "pool".
The code instead refer to executable "instructions" that the processor must manage to do its job.
Rootkit (developed for Windows) are able to be invisible by altering the contents of memory with the goal to change the behavior of the operating system or the way the data is presented to the user. Rootkit "work" on the code, on data or on both categories of information stored in memory (memory patching).
When we talk about privileges level with which an application runs, we use the term "ring". With "ring 0" identifies the processes that are running in kernel mode and "ring 3" the user mode applications such as the browser, Notepad, and so on.
When the processor operates in kernel mode, it has access to all registers and the system memory.
When CPU operates in user mode (level 3) It's allowed access only to those areas of memory that can be used in "user mode".
Because the code runs in kernel mode,It can have access to all areas of the system, being able to run programs in this context is the goal of many advanced malware and rootkit.
If, for example, we want to have the list of running processes, the first step is to open the Task Manager. This application, however, work in user mode while running kernel mode code that takes care of retrieving the list of running processes. For this type of activity, the Windows Task Manager invokes a function called NTQuerySystemInformation and into NTDLL.dll library. A routine operating in kernel mode receives the request and draws on a special kernel structure called System Service Descriptor Table (SSDT).
When the system interface it with the kernel to perform operations requested by applications or by using the shell, you could have a potential point of attack, exploited by a rootkit with the goal of altering the normal flow of information and therefore compromise the correct operation of Windows.
Before a function, able to interface with the operating system kernel, can be invoked (for example a function that creates a new file), you must have previously imported by the application that intends to make use of it. This means that the library (.dll file) containing the function, must be loaded in the memory space used by the application and adding in a special table called Import Address Table. This is another opportunity that a rootkit has to change the normal flow of information.
Another method used by attackers (rootkits developers), to alter the procedure for executing code in user mode, is often referred to as inline (int) patching or inserting a trampoline. The rootkit, in this case, edit the first few bytes that characterize the function attacked. So, the rootkit becomes able to filter the data returned, output, by the function. The possibilities are endless: the rootkit can thus, for example, to remove a file from a list of files in a given folder. In this way, It can hide to the user, the operating system and installed applications of malicious files connected to the functioning of rootkits or other malware.
The NtQueryDirectoryFile (API) is often the target of attack for the peculiarity of return the list of files and folders stored in any directory on the disk.
Hijack Hunter, using "Kernel Mode Info" lets go to work at kernel level (in the region of memory reserved to the kernel and accessible only to elevated privileges:"ring 0") highlighting any suspicious activities related, for example, the action of malware (rootkit).
The kernel exports the functions to interact with the operating system, but these functions are not readily accessible from a user mode program because they are working with two privilege (ring 3 in "user mode"). The operating system, then, provides the functions in "user mode" (often exported by libraries ntdll.dll, Kernel32.dll, advapi32.dll, ...) that act as a bridge between the application executing in user mode and the kernel of Windows.
Any program makes use of the API in "ring 3": this is the only way to interact with the operating system: Microsoft .Net, Java or any other framework, create an "abstract level" to make life easier (for us coders ). The Ring3 API Hooks feature of Hijack Hunter allows you to check that the exported functions in "ring 3" may have not been intercepted by some malware.
). The Ring3 API Hooks feature of Hijack Hunter allows you to check that the exported functions in "ring 3" may have not been intercepted by some malware.
When we examine the report of Hijack Hunter, under "Ring3 API Hooks", we consider that not all items shown are to be considered as malicious. Indeed, most of them are probably completely legitimate. This type of analysis, combined with Kernel Mode Info, however, may help the user (expert) to see what is happening on the system.
The option "Files created/modified 15 days ago" lets you find all those files are present on your system that have been created or modified in the last 15 days. This is a very useful information because, in the case of a malware infection occurred in recent times, you can figure out which system files have been changed.
Finally, "Unknown Files with .sys extension and Unknown CLSID Files" allow to find unknown elements that are not closely related to the proper functioning of the operating system. Hijack Hunter compiles a list of WDM (Windows Driver Model .sys extension) that are not known. In "Unknown Files with .sys extensions" section, Hijack Hunter can list drivers absolutely legitimate, related to benign applications (it is common to find in the list, for example, drivers used by antivirus and antimalware, from virtualization solutions, from some hardware devices and so on). For each object is paired with the name of the manufacturer and its MD5 signature. In this way it is possible to discern any harmful components from legitimate ones.
Regarding the "Unknown CLSID Files", Hijack Hunter indicates those files "declared" in the registry that have been paired with the CLSID identification code. The CLSID is a 128-bit code that is used by Windows to manage a specific file. CLSID codes can be used to "mask" the real name of a file (very interesting topic that I hope to talk in the coming threads). In this case, It is specify the name of the manufacturer and MD5 signature of the file.
We can copy the MD5 signature shown in the report of Hijack Hunter and copy it to VirusTotal: If the file is already known, you will get the required information.
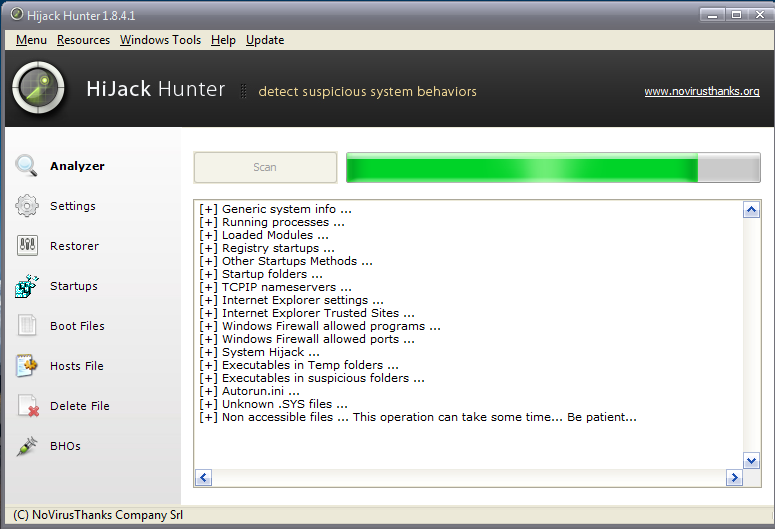
Returning to the Analyze tab and click on the Scan button, this will start the procedure of system analysis.
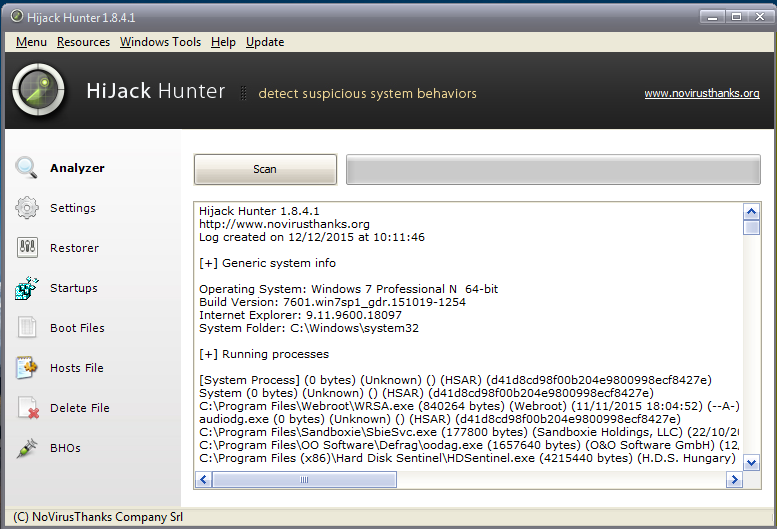
At the end of the procedure, which could take several minutes to complete (especially if you are left turned on all scan options), Hijack Hunter will produce a final report.
I remember that the report generated should be analyzed by an expert user because it contains the keys for the presence of a malware on your system but also many references to components absolutely legitimate.
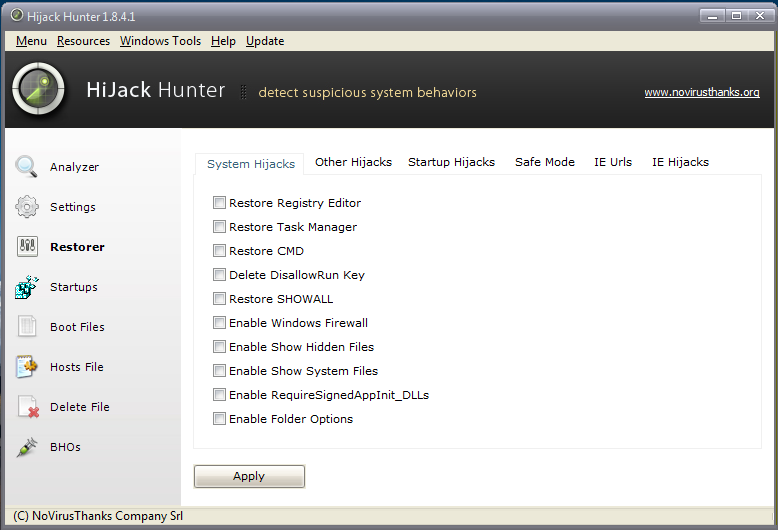
Interesting the Restorer section who restores the default configuration of Windows in case some harmful components they had applied restrictions.
For example, some malware disable Windows safe mode, others cause inaccessible the prompt, the "task manager" or Registry Editor (REGEDIT). In these situations, you can use Hijack Hunter to restore the correct values and delete any limitation imposed.
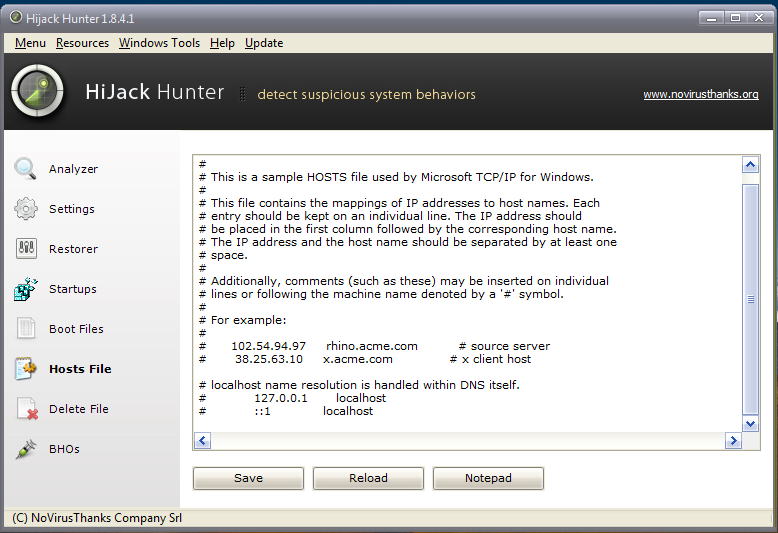
Hijack Hunter also offers some tools: programs that run when you start Windows (autoruns), boot files, the HOSTS file, BHO, etc.
I conclude this long and complex review hoping to have explained to you how this fantastic tool works, perhaps It is underestimated but It is indispensable especially against rootkit and deep malware.
Hijack Hunter: Inspect your PC and generate detailed security report
Thanks for reading and, as usual, sorry for mistakes.
It is essential to start it with administrator rights.
Perhaps the most interesting tab is "Scan": Here you can customize the "depth" of scans from Hijack Hunter. By default (recommended), the program exclude, from the report produced, all those files that are closely related to the operation of the OS or that are otherwise known components for Microsoft applications (Microsoft System Files).
This box, if checked, prevents Hijack Hunter show, in the log file generated after the scan in the form of text files, processes known as explorer.exe or svchost.exe.
The program can show the loaded modules from folders that appear suspicious and It is then able to perform a "kernel mode" control. By activating the option "Kernel Mode Info" Hijack Hunter will install its own (. sys) driver to analysis of what is happening to kernel level.
I'm going to try to explain, briefly, what is this control to understand the complexity work of this little tool. Information in memory, can be divided into two categories: "data" and "code".
The "data" refers to the bytes that are not executed. Some examples are data structures that are directly related to the operation of the kernel of the system or data for a Word document being drafted. The data is usually stored in memory regions called "heap", "stack" or "pool".
The code instead refer to executable "instructions" that the processor must manage to do its job.
Rootkit (developed for Windows) are able to be invisible by altering the contents of memory with the goal to change the behavior of the operating system or the way the data is presented to the user. Rootkit "work" on the code, on data or on both categories of information stored in memory (memory patching).
When we talk about privileges level with which an application runs, we use the term "ring". With "ring 0" identifies the processes that are running in kernel mode and "ring 3" the user mode applications such as the browser, Notepad, and so on.
When the processor operates in kernel mode, it has access to all registers and the system memory.
When CPU operates in user mode (level 3) It's allowed access only to those areas of memory that can be used in "user mode".
Because the code runs in kernel mode,It can have access to all areas of the system, being able to run programs in this context is the goal of many advanced malware and rootkit.
If, for example, we want to have the list of running processes, the first step is to open the Task Manager. This application, however, work in user mode while running kernel mode code that takes care of retrieving the list of running processes. For this type of activity, the Windows Task Manager invokes a function called NTQuerySystemInformation and into NTDLL.dll library. A routine operating in kernel mode receives the request and draws on a special kernel structure called System Service Descriptor Table (SSDT).
When the system interface it with the kernel to perform operations requested by applications or by using the shell, you could have a potential point of attack, exploited by a rootkit with the goal of altering the normal flow of information and therefore compromise the correct operation of Windows.
Before a function, able to interface with the operating system kernel, can be invoked (for example a function that creates a new file), you must have previously imported by the application that intends to make use of it. This means that the library (.dll file) containing the function, must be loaded in the memory space used by the application and adding in a special table called Import Address Table. This is another opportunity that a rootkit has to change the normal flow of information.
Another method used by attackers (rootkits developers), to alter the procedure for executing code in user mode, is often referred to as inline (int) patching or inserting a trampoline. The rootkit, in this case, edit the first few bytes that characterize the function attacked. So, the rootkit becomes able to filter the data returned, output, by the function. The possibilities are endless: the rootkit can thus, for example, to remove a file from a list of files in a given folder. In this way, It can hide to the user, the operating system and installed applications of malicious files connected to the functioning of rootkits or other malware.
The NtQueryDirectoryFile (API) is often the target of attack for the peculiarity of return the list of files and folders stored in any directory on the disk.
Hijack Hunter, using "Kernel Mode Info" lets go to work at kernel level (in the region of memory reserved to the kernel and accessible only to elevated privileges:"ring 0") highlighting any suspicious activities related, for example, the action of malware (rootkit).
The kernel exports the functions to interact with the operating system, but these functions are not readily accessible from a user mode program because they are working with two privilege (ring 3 in "user mode"). The operating system, then, provides the functions in "user mode" (often exported by libraries ntdll.dll, Kernel32.dll, advapi32.dll, ...) that act as a bridge between the application executing in user mode and the kernel of Windows.
Any program makes use of the API in "ring 3": this is the only way to interact with the operating system: Microsoft .Net, Java or any other framework, create an "abstract level" to make life easier (for us coders
When we examine the report of Hijack Hunter, under "Ring3 API Hooks", we consider that not all items shown are to be considered as malicious. Indeed, most of them are probably completely legitimate. This type of analysis, combined with Kernel Mode Info, however, may help the user (expert) to see what is happening on the system.
The option "Files created/modified 15 days ago" lets you find all those files are present on your system that have been created or modified in the last 15 days. This is a very useful information because, in the case of a malware infection occurred in recent times, you can figure out which system files have been changed.
Finally, "Unknown Files with .sys extension and Unknown CLSID Files" allow to find unknown elements that are not closely related to the proper functioning of the operating system. Hijack Hunter compiles a list of WDM (Windows Driver Model .sys extension) that are not known. In "Unknown Files with .sys extensions" section, Hijack Hunter can list drivers absolutely legitimate, related to benign applications (it is common to find in the list, for example, drivers used by antivirus and antimalware, from virtualization solutions, from some hardware devices and so on). For each object is paired with the name of the manufacturer and its MD5 signature. In this way it is possible to discern any harmful components from legitimate ones.
Regarding the "Unknown CLSID Files", Hijack Hunter indicates those files "declared" in the registry that have been paired with the CLSID identification code. The CLSID is a 128-bit code that is used by Windows to manage a specific file. CLSID codes can be used to "mask" the real name of a file (very interesting topic that I hope to talk in the coming threads). In this case, It is specify the name of the manufacturer and MD5 signature of the file.
We can copy the MD5 signature shown in the report of Hijack Hunter and copy it to VirusTotal: If the file is already known, you will get the required information.
Returning to the Analyze tab and click on the Scan button, this will start the procedure of system analysis.
At the end of the procedure, which could take several minutes to complete (especially if you are left turned on all scan options), Hijack Hunter will produce a final report.
I remember that the report generated should be analyzed by an expert user because it contains the keys for the presence of a malware on your system but also many references to components absolutely legitimate.
Interesting the Restorer section who restores the default configuration of Windows in case some harmful components they had applied restrictions.
For example, some malware disable Windows safe mode, others cause inaccessible the prompt, the "task manager" or Registry Editor (REGEDIT). In these situations, you can use Hijack Hunter to restore the correct values and delete any limitation imposed.
Hijack Hunter also offers some tools: programs that run when you start Windows (autoruns), boot files, the HOSTS file, BHO, etc.
I conclude this long and complex review hoping to have explained to you how this fantastic tool works, perhaps It is underestimated but It is indispensable especially against rootkit and deep malware.
Hijack Hunter: Inspect your PC and generate detailed security report
Thanks for reading and, as usual, sorry for mistakes.