- Dec 29, 2014
- 1,711
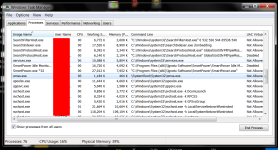
SMSvcHost.exe started running on boot on a system I am trying to get cleaned up and set up properly for more use. Not sure when it started autostarting as I haven't been looking over Task Manager as much as on the main system. Also, when I do look over TM I don't see all the processes unless I select "Show processes from all Users". Haven't been doing that much on this system. BTW, running on an admin account, and I would like to begin the march to SUA. Think it might take a while for this project. Maybe 2 weeks I guess.
One quick question before the rest. This system get its internet connection via ethernet with a wi-fi connected desktop next to it. Could this be why port sharing is running? I can't find a reference for this on Google.
Here is the rest. If the above is true, please disregard below.
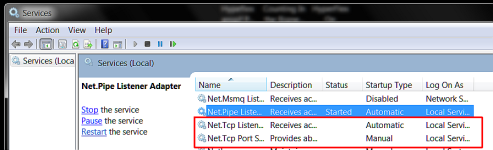
SMSvcHost.exe starts I believe via a service called NetTcpPortSharing. The service is set to manual, but something seems to be starting the service on boot, so I wanted to find out what. This is mainly because I don't see it running on any other systems. So I added the location of SMSvcHost.exe to the vulnerables list of NVT ERP, hoping I could get some information on an alert or in the log. I also scanned the list of allowed processes to see if it was allowed so I could delete the entry if so. Then I scanned the list of allowed command lines to see if I could find anything that might indicate it was starting SMSvcHost.exe. Didn't see anything, so I rebooted to see if NVT ERP would alert when the SMSvcHost.exe tried to run. No luck...no alert. I would love to have some idea of why there is no alert if anyone thinks they might know. Location of SMSvcHost.exe:
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.exe
Best information I could find on port sharing:
Net.TCP Port Sharing
Didn't help me much.
This system is kind of a mess. I have Wireshark on the system attempting to learn to capture packets and analyze them and so on and several other tools like SpyStudio, which is a nice application for capturing real-time run-time activities of a process. I feel like I am learning to a significant degree with these applications, but at the same time, they introduce some complicating and somewhat unknown elements to me. Example is WinPcap with Wireshark. I don't know anything about WinPcap except that it is required to capture with Wireshark. I really need to update software on the PC too. It hasn't been used as much as the main, and so I will be working on that too.
Thx for any help...
One quick question before the rest. This system get its internet connection via ethernet with a wi-fi connected desktop next to it. Could this be why port sharing is running? I can't find a reference for this on Google.
Here is the rest. If the above is true, please disregard below.
SMSvcHost.exe starts I believe via a service called NetTcpPortSharing. The service is set to manual, but something seems to be starting the service on boot, so I wanted to find out what. This is mainly because I don't see it running on any other systems. So I added the location of SMSvcHost.exe to the vulnerables list of NVT ERP, hoping I could get some information on an alert or in the log. I also scanned the list of allowed processes to see if it was allowed so I could delete the entry if so. Then I scanned the list of allowed command lines to see if I could find anything that might indicate it was starting SMSvcHost.exe. Didn't see anything, so I rebooted to see if NVT ERP would alert when the SMSvcHost.exe tried to run. No luck...no alert. I would love to have some idea of why there is no alert if anyone thinks they might know. Location of SMSvcHost.exe:
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\SMSvcHost.exe
Best information I could find on port sharing:
Net.TCP Port Sharing
Didn't help me much.
This system is kind of a mess. I have Wireshark on the system attempting to learn to capture packets and analyze them and so on and several other tools like SpyStudio, which is a nice application for capturing real-time run-time activities of a process. I feel like I am learning to a significant degree with these applications, but at the same time, they introduce some complicating and somewhat unknown elements to me. Example is WinPcap with Wireshark. I don't know anything about WinPcap except that it is required to capture with Wireshark. I really need to update software on the PC too. It hasn't been used as much as the main, and so I will be working on that too.
Thx for any help...