- Nov 15, 2016
- 867
Network of Fake Ad Agencies Distributed 1 Billion Bad Ads, Researchers Find
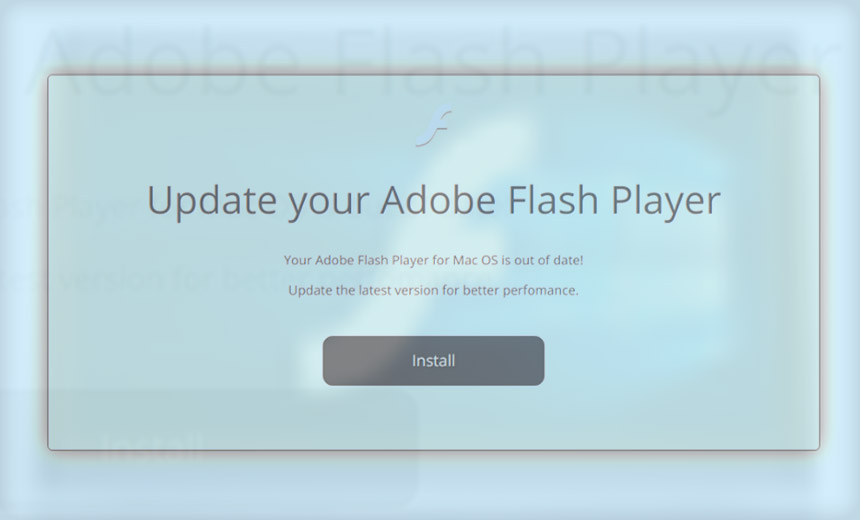
No Flash plug-in? No problem: Malicious ads will try to fake out Mac and Windows users anyway. (Source: Confiant)
The web is funded in large part through advertisements, but website users face an increasing security risk: malicious advertisements.
See Also: Addressing the Identity Risk Factor in the Age of 'Need It Now'
Cybercriminals realized long ago that the online advertising industry, if properly subverted, could be a near-perfect platform for distributing malware. While the ad industry has clocked these threats and taken steps to improve its defenses, their platforms continue to be manipulated by criminals, to the detriment of users.
The latest evidence of this malicious push comes via advertising security company Confiant. Late last year, it began to notice patterns within the malicious advertising it was blocking that pointed to a massive social engineering campaign.
The company's technology is aimed at publishers who want to protect their users from malware. The platform analyzes ads in real time and blocks those that contain malicious domains or strange JavaScript calls within ad tags, says Louis-David Mangin, Confiant's CEO and co-founder.
"No one has ever gone to jail for ad fraud. It's an incredibly lucrative avenue that is relatively safe for them to practice."
—Louis-David Mangin, Confiant
What unfurled last year was a large and fairly sophisticated operation Confiant has nicknamed Zirconium that served as many as a billion harmful ads across the web, including on some of the top trafficked sites. The ads didn't automatically exploit computers but instead relied on redirecting users to scammy sites and trying to social engineer them.
The release of Confiant's report appears to have caused the group to either disappear or better cover its tracks. Regardless, Mangin says he expects it to restart its operations.
"No one has ever gone to jail for ad fraud," Mangin says. "It's an incredibly lucrative avenue that is relatively safe for them to practice."
Fake Ad Agencies
Whoever launched Zirconium created 28 fraudulent ad agencies and took time to build each one's social media profile to make them appear legitimate. About 20 of those fake agencies then contracted with so-called demand-side platforms, or DSPs, which is online advertising parlance for services that connect advertising buyers with sellers.
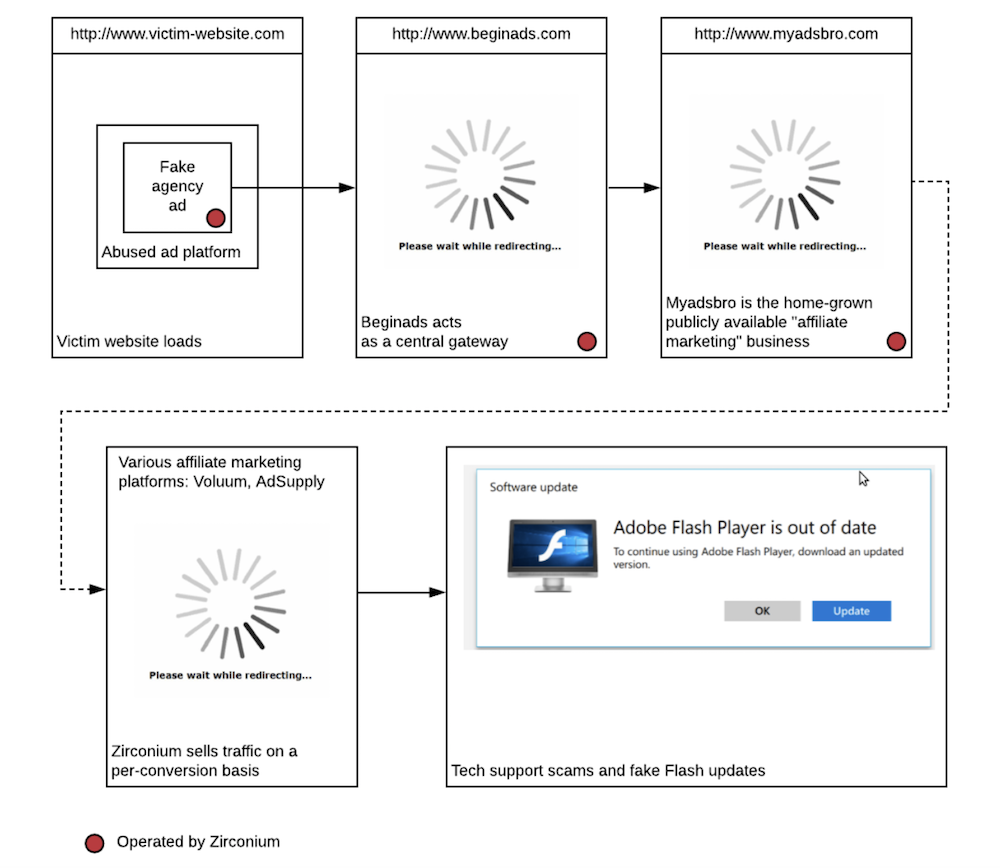
Zirconium: How attacks flow, once a user encounters a malicious website. (Source: Confiant)
Mangin says that the scale and number of DSPs that Zirconium was buying from was surprising. Many were "absolutely reputable" companies, he says, but they need to be more careful about what business they accept.
"The DSPs can absolutely do a much better job protecting and verifying clients," Mangin says. "There is a clear indication that the buy side does not properly vet clients who come in and offer the money."
Jerome Segura, the lead malware intelligence analyst at security firm Malwarebytes, who has extensively studied malvertising, says the online advertising industry should realize that these kinds of threats are as harmful as actual malware.
"It is a little disconcerting that fake ad agencies and cloaking in general continue to be a big problem for the advertising industry," says Segura, who has reviewed Confiant's findings.
Top Web Sites Affected
Confiant estimates that 62 percent of websites that are monetized through advertising may have served up Zirconium's bad ads, according to a post by its CTO, Jerome Dangu. That estimate is based on 600 websites that Confiant analyzed over a seven-day period, Mangin says.
For anyone who's browsing the web, encountering the ads - which are actually invisible to users - can be a frustrating experience. In one scenario, the ad hijacks a user's browser and redirects them to another domain. Once on the new domain, the browser window often can't be closed. In another variation, instead of redirecting someone to a new site, the malicious site is presented as an overlay to the current one, using an iframe in HTML.
The attack then relies on social engineering, trying to trick users into downloading a fake Flash update, entering information into a phishing form or falling for fake tech support schemes after false alerts flash, claiming their system is infected with malware.
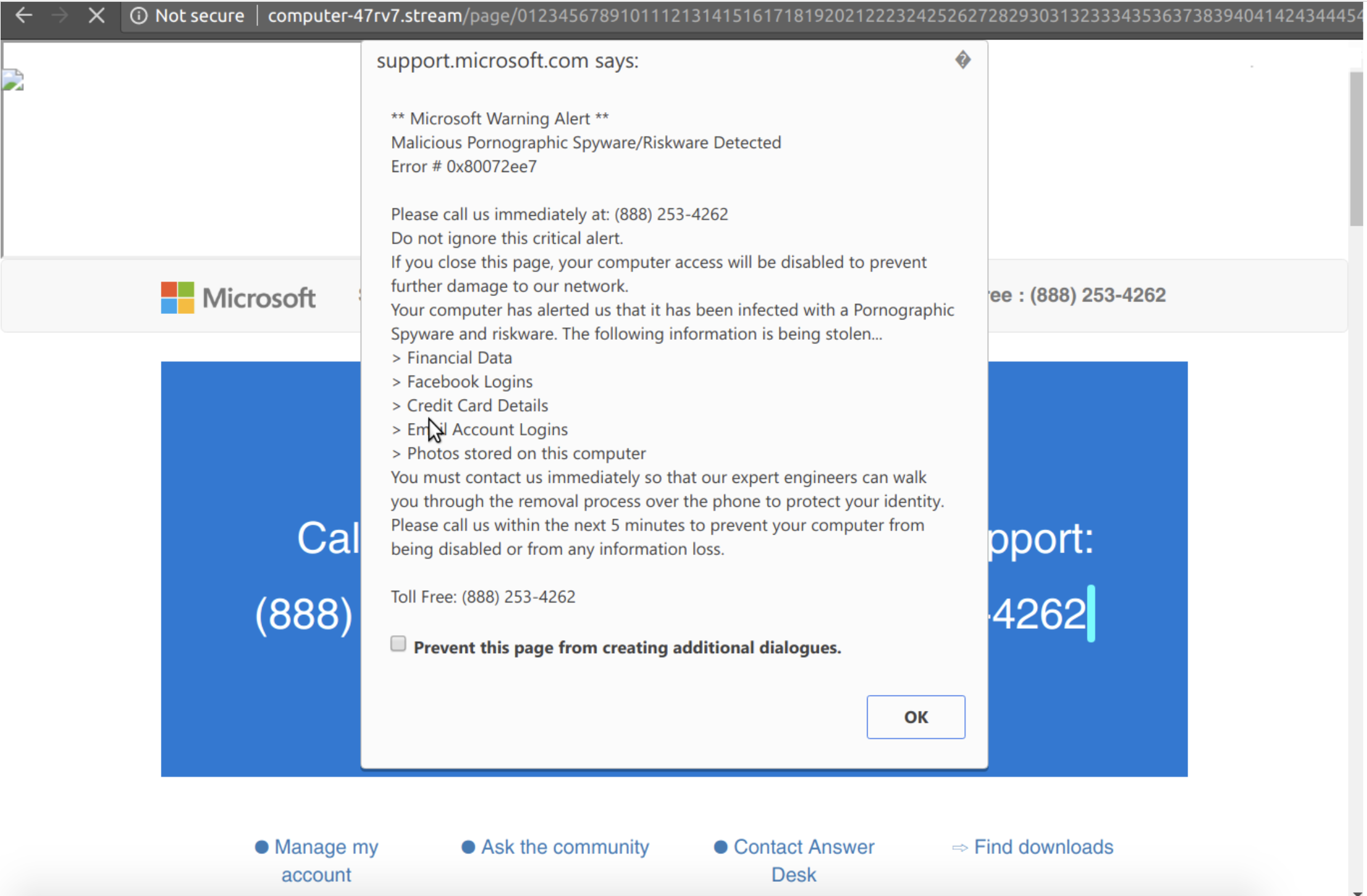
Sample tech support scam pushed to users through advertisements by the Zirconium malicious advertising group. (Source: Confiant.)
Google, however, is planning to release a fix to combat this involuntary redirection problem. In Chrome build 64, the browser will block redirects coming from third-party iframes and show an alert. Chrome will also stop another shady scenario, involving someone clicking on an item that launches a new tab, and the main window then automatically changing to unwanted content.
Exploit Kits Fall Out of Favor
For years, many criminals who wanted to launch online attacks relied on exploit kits, which are automated toolkits, often available via subscription from cybercrime-as-a-service providers. Exploit kits typically employ attack code, implanted on websites, to probe browsers for common software vulnerabilities and then unleash drive-by attacks that can infect a system with malware, allowing criminals to remotely control them as part of a botnet.
The discovery of Zirconium, however, bolsters evidence that exploit kits have been falling out of favor, in part due to improved browser security (see Neutrino Exploit Kit: No Signs of Life).
That's because exploit kits rely on a continuing stream of new flaws in widely used software. But thanks to efforts by Microsoft, Google and Mozilla, as well as plug-in makers such as Adobe and Oracle, browsers today are more secure than ever. The decreased use of Adobe System's Flash multimedia software in particular has made it much more difficult for attackers to subvert massive quantities PCs with little effort when building botnets.
"The drive-by threat landscape is driven by several external factors but ultimately determined by what makes threat actors the most return on their investment, with minimal effort," Segura at Malwarebytes says. "That low hanging fruit is no longer exploits but instead social engineering attacks."
