- May 14, 2016
- 1,597
From https://malwaretips.com/threads/3-1-17-9.67144/
Thanks to @Solarquest
oracamento82323423723.js
Why this sample ?
It uses unprintable char for its obfuscation / deobfuscation methods. and a big part of useless data.
This is the first time I will show this family here.
the problem with the unprintable chars, is that I will not be able to copy them here, so I will use some screenshots, and/or replace them on the analysis parts.
1) What it looks like :
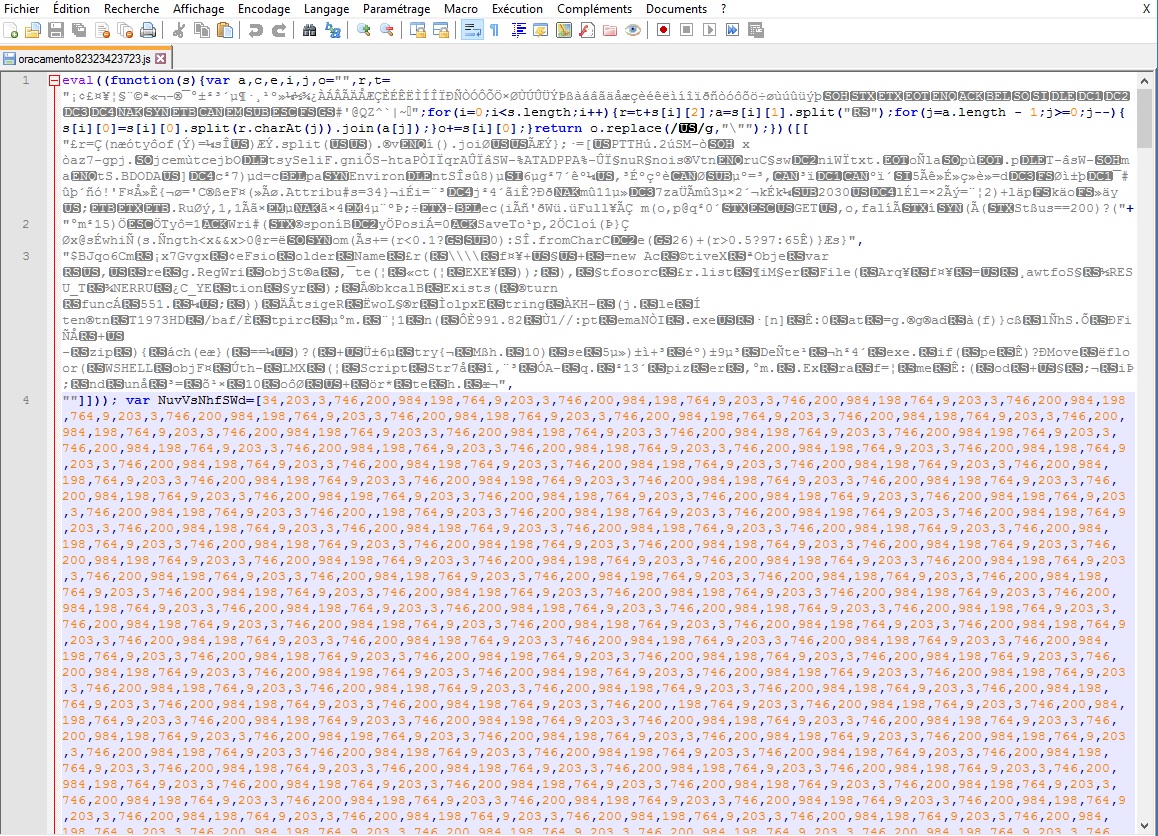
You can see normal chars, and unprintable chars : the part that are with blank letters and a grey or black background.
2) simplification :
First thing I noticed :
The long part with :
=> can be deleted : not used : only here to obfuscate a bit more.
The real important parts are on the new screenshot :
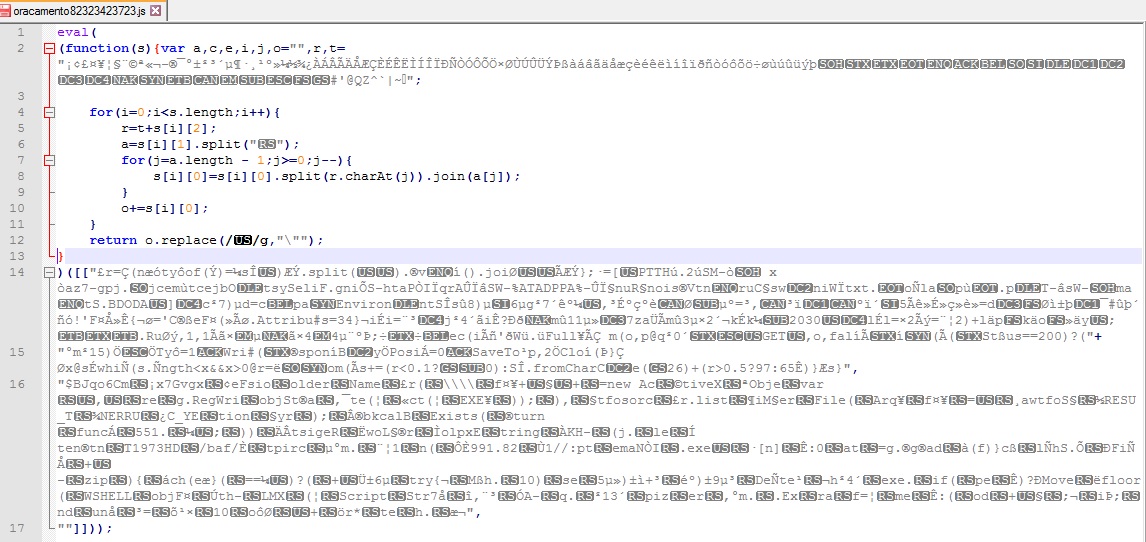
3) What are unprintable chars :
Each char has a code, that we name "char code", that can be given in decimal, hexadecimal, etc.
On a text file, or a file with content that can be read or write as file text, the char codes used as values correspond to a writable single char, with the aim to be understandable / readable.
But there are other values with another meaning, that are not used to give an understandable / readable char.
From NON PRINTABLE CHARACTERS :
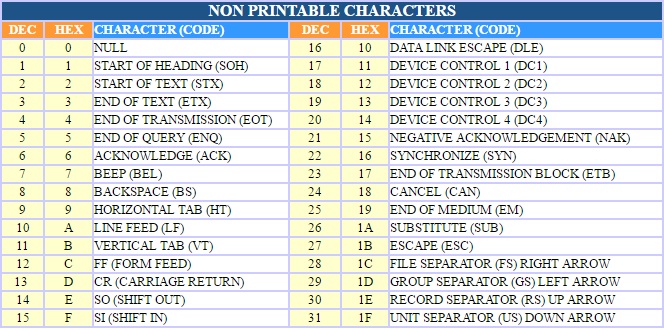
We can see in this table non printable chars, with their code in DEC and HEX.
Some of these chars appear on the sample I am analyzing currently.
For example, none of these char codes can represent a char. An editor will shows these chars with their special name, like SOH that means "Start of Heading", or RS that means "Record Separator" / "Up Arrow"
This is a part of a string used in the current sample :

SOH , STX, EOT, etc, => each one count as a single char, but are represented here like if it has 3 / 2 chars in white with grey background : their name, to tell us that they are unprintable chars.
If you click before SOH and then on the right arrow, the cursor will move after SOH in one step , and will be before STX (because it represents only one char, but unprintable).
The problem using this unprintable chars : if you try to open the sample on a debugger, or copy-paste the content on an editor : these unprintable chars will not appear.
Example : the same string I put above on the screenshot, copy-paste here :
Thanks to @Solarquest
oracamento82323423723.js
Why this sample ?
It uses unprintable char for its obfuscation / deobfuscation methods. and a big part of useless data.
This is the first time I will show this family here.
the problem with the unprintable chars, is that I will not be able to copy them here, so I will use some screenshots, and/or replace them on the analysis parts.
1) What it looks like :
You can see normal chars, and unprintable chars : the part that are with blank letters and a grey or black background.
2) simplification :
First thing I noticed :
The long part with :
var NuvVsNhfSWd=[34,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198,764,9,203,3,746,200,984,198........
...
]
...
]
=> can be deleted : not used : only here to obfuscate a bit more.
The real important parts are on the new screenshot :
3) What are unprintable chars :
Each char has a code, that we name "char code", that can be given in decimal, hexadecimal, etc.
On a text file, or a file with content that can be read or write as file text, the char codes used as values correspond to a writable single char, with the aim to be understandable / readable.
But there are other values with another meaning, that are not used to give an understandable / readable char.
From NON PRINTABLE CHARACTERS :
We can see in this table non printable chars, with their code in DEC and HEX.
Some of these chars appear on the sample I am analyzing currently.
For example, none of these char codes can represent a char. An editor will shows these chars with their special name, like SOH that means "Start of Heading", or RS that means "Record Separator" / "Up Arrow"
This is a part of a string used in the current sample :
If you click before SOH and then on the right arrow, the cursor will move after SOH in one step , and will be before STX (because it represents only one char, but unprintable).
The problem using this unprintable chars : if you try to open the sample on a debugger, or copy-paste the content on an editor : these unprintable chars will not appear.
Example : the same string I put above on the screenshot, copy-paste here :
üýþ#'@QZ^`|~";
You can see that the part from SOH to GS ... doesn't appear.
BUT this part is really present when I am on the MT editor, even if I can't see it : when the cursor reaches to the part where this unprintable chars should appear (but not appear), I click several times on the right arrow, and the cursor stays at the same place, until all unprintable chars have been taken into account => then, the cursor moves on last normal chars
ONCE the post is saved, these parts are lost...
You can see that the part from SOH to GS ... doesn't appear.
BUT this part is really present when I am on the MT editor, even if I can't see it : when the cursor reaches to the part where this unprintable chars should appear (but not appear), I click several times on the right arrow, and the cursor stays at the same place, until all unprintable chars have been taken into account => then, the cursor moves on last normal chars
ONCE the post is saved, these parts are lost...
Last edited: