Microsoft has had to battle a set of
PrintNightmare vulnerabilities for months. If exploited, people can run programs with SYSTEM privileges, causing security issues. While Microsoft has issued patches and shared fixes, problems persist. I spoke with Benjamin Delpy, head of Research & Development Security Center at Banque de France, about the PrintNightmare vulnerabilities. Delpy has been on the forefront of discovering PrintNightmare vulnerabilities since they emerged and is often cited as the discoverer of issues related to Windows Print Spooler.
Before we dive into the ins and outs of PrintNightmare vulnerabilities, it's worth explaining what they are. There isn't a single PrintNightmare vulnerability. Instead, it's a "generic category of flaws in the Printing Spooler," Delpy says. "Basically, we use the term PrintNightmare now to describe vulnerability in the Windows Printing Spooler involving the installation of a driver and/or a printer."
Delpy explains that while Microsoft has worked to address the issue, that its efforts don't eliminate the source of vulnerabilities (emphasis added):
Microsoft introduced several fixes, but for now, none of them completely address all security problem regarding driver/printer installation for unprivileged users. Their fix now limits the default behavior of the spooler to NOT allow unprivileged users to install a driver (even legit one).
They prefer to avoid the full problem, [rather] than to redesign some part of the product.
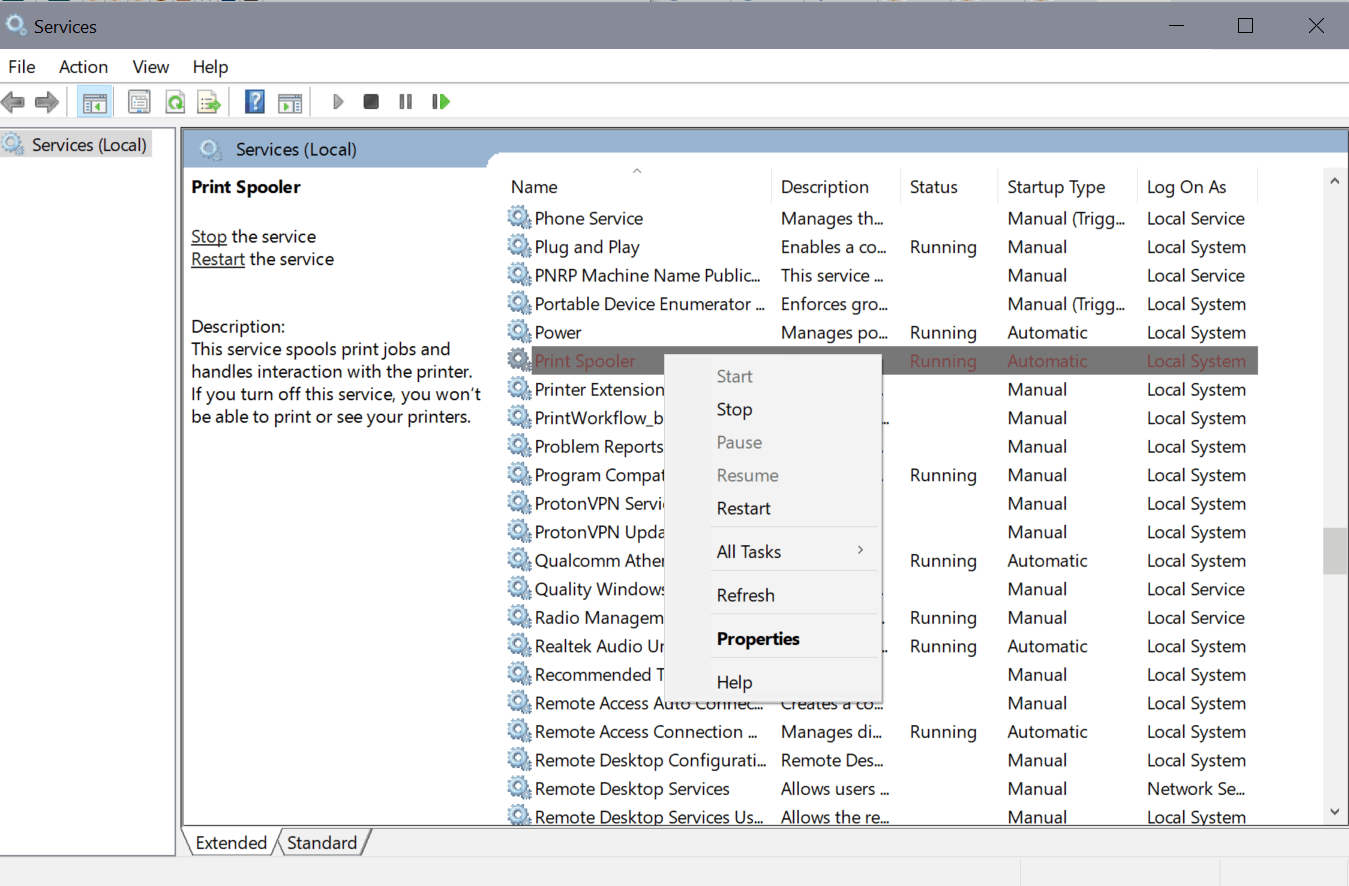
Security experts have joked about some of Microsoft's proposed solutions to PrintNightmare vulnerabilities. "Microsoft [is] a running gag by posting official workarounds like "Disable Printing Spooler," Delpy says.
The researcher explains that while PrintNightmare vulnerabilities aren't much of a threat for individual users, that they present a serious security risk for businesses.
"For individuals ... this is nearly nothing ... individuals are nearly every time administrator of their computer, and personal computer are nearly never reachable from the internet ... so [it's] not really a problem," Delpy explains.
The researcher continues, "This is a real problem for enterprises/organization/etc., because usually users are not admin (I hope

). With PrintNightmare vulnerabilities, when they run a program, macro, script, it can escalate privileges to SYSTEM and compromise the whole system. On some systems (shared desktop), it can even lead to capture credentials of other users/administrators to compromises other systems on the network. A 'Local Privilege Escalation' can often lead to "Remote Code E̶s̶c̶a̶l̶a̶t̶i̶o̶n̶ Execution."
Fixing the PrintNightmare vulnerabilities is complicated, in large part because it's a legacy component, explains Delpy:
"At this time, it's very difficult to fix all problems in a such legacy components. Protocols behinds it is documented for NT 3.1 ... On a security point of view, it must be completely rewritten to be fully isolated and to NOT have SYSTEM privilege ... it's a legacy of the past that must not exist anymore."
I asked Delpy if he thinks PrintNightmare will ever be completely fixed. His response was not optimistic:
It depends on so many things. To be honest, I think — if they invest some manpower — they can fix many problems around printer/driver installation. But at this time, they seem to prefer an attitude to prevent non-administrators [from taking] some basic action like they did before. [Which leaves] the responsibility to enterprise to bypass it or not ... it's not very responsible from Microsoft, but [lets them avoid having] to really fix deeper problems. If they choose to rewrite the spooler engine for a new one, yes, they can fix lots of actual (and future problems), but as you've seen, it's not a sexy topic for them.
Delpy warns that these types of vulnerabilities are often exploited in the wild. The cost of attacking someone through a discovered vulnerability is relatively low, and the process can be automated.

www.bleepingcomputer.com