Gandalf_The_Grey
Level 76
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Apr 24, 2016
- 6,578
A threat actor has been targeting government entities with PureCrypter malware downloader that has been seen delivering multiple information stealers and ransomware strains.
Researchers at Menlo Security discovered that the threat actor used Discord to host the initial payload and compromised a non-profit organization to store additional hosts used in the campaign.
"The campaign was found to have delivered several types of malware including Redline Stealer, AgentTesla, Eternity, Blackmoon and Philadelphia Ransomware," the researchers say.
According to the researchers, the observed PureCrypter campaign targeted multiple government organization in the Asia-Pacific (APAC) and North America regions.
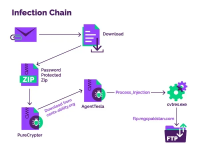
The attack begins with an email that has a Discord app URL pointing to a PureCrypter sample in a password-protected ZIP archive.
PureCrypter is a .NET-based malware downloader first seen in the wild in March 2021. Its operator rents it to other cybercriminals to distribute various types of malware.
When executed, it delivers the next-stage payload from a command and control server, which is the compromised server of a non-profit organization in this case.
The sample that the researchers at Menlo Security analyzed was AgentTesla. When launched, it establishes a connection to a Pakistan-based FTP server that is used to receive the stolen data.
The researchers found that the threat actors used leaked credentials to take control of the particular FTP server rather than setting it up their own, to reduce identification risks and minimize their trace.

PureCrypter malware hits govt orgs with ransomware, info-stealers
A threat actor has been targeting government entities with PureCrypter malware downloader that has been seen delivering multiple information stealers and ransomware strains.