- Mar 29, 2018
- 7,106
A question was raised on Wilders about Windows Defender Sandbox recently and it got me thinking: Has WD sandbox been incorporated into Tamper Protection? M$ as usual provides little documentation and the two official sources I know of are these: Tamper Protection and Windows Defender Sandbox. They are very general explanations and I can find no other current official explanation about them.
Previously, when WD Sandbox was enabled you would see this
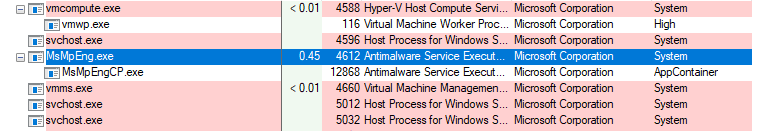
I was curious so I enabled WD Sandbox on my system and here is what I see
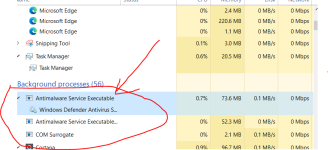 Clearly the names are not the same in these two images.
Clearly the names are not the same in these two images.
I understand some of WD's processes have new names in 1903+ and this only complicates things more in terms of finding answers to my question. Any Windows gurus are free to offer there expertise or opinions.
Previously, when WD Sandbox was enabled you would see this
I was curious so I enabled WD Sandbox on my system and here is what I see
 Clearly the names are not the same in these two images.
Clearly the names are not the same in these two images.I understand some of WD's processes have new names in 1903+ and this only complicates things more in terms of finding answers to my question. Any Windows gurus are free to offer there expertise or opinions.
