- Nov 15, 2016
- 867
Crypto-Lockers Remain Serious Threat Despite Recent Attack Volume Decline

Ransomware continues to pose a clear and present threat to businesses and consumers.
See Also: How to Scale Your Vendor Risk Management Program
"From a business standpoint, the biggest threat, especially at the end of last year, was ransomware," says Adam Kujawa, director of malware intelligence at security firm Malwarebytes.
One measure of the problem is the many different types of ransomware available to would-be cybercriminals, be they based in their parents' basement or part of a larger organized crime ring.
ID Ransomware, a site that allows victims to upload a ransom note or encrypted file to identify the ransomware that crypto-locked them, now counts 542 ransomware families, starting with 4rw5w, 777 and 7ev3n, and ending with ZipLocker, Zipper and Zyklon.
That count represents a sharp increase from October 2016, when the service listed just 200 ransomware families.
It's unclear how many of the 342 new types of ransomware have been built from scratch or may have been modified from previous efforts.
"I bet you a lot of them are based off of Hidden Tier, which was that open source ransomware that some researchers created, saying, 'I want to help the world by spreading this open source ransomware,'" Kujawa says. "The code was taken and then modified to be more malicious, and then you started seeing things in the wild actually utilizing it." (See Cybercrime-as-a-Service Economy: Stronger Than Ever)
Low Barriers to Entry
For anyone who wants to use ransomware to generate illicit gains, barriers to entry remain low (see Want to Get Into Ransomware? This Kit Costs Just $175).
Xavier Mertens, a Belgian-based security researcher and Internet Storm Handler, on Thursday described a darknet website he found that generates new ransomware, on demand, for anyone who provides a bitcoin address to which ransoms will get deposited. In return, whoever is offering the service says they will automatically take a 10 percent cut of ransoms.
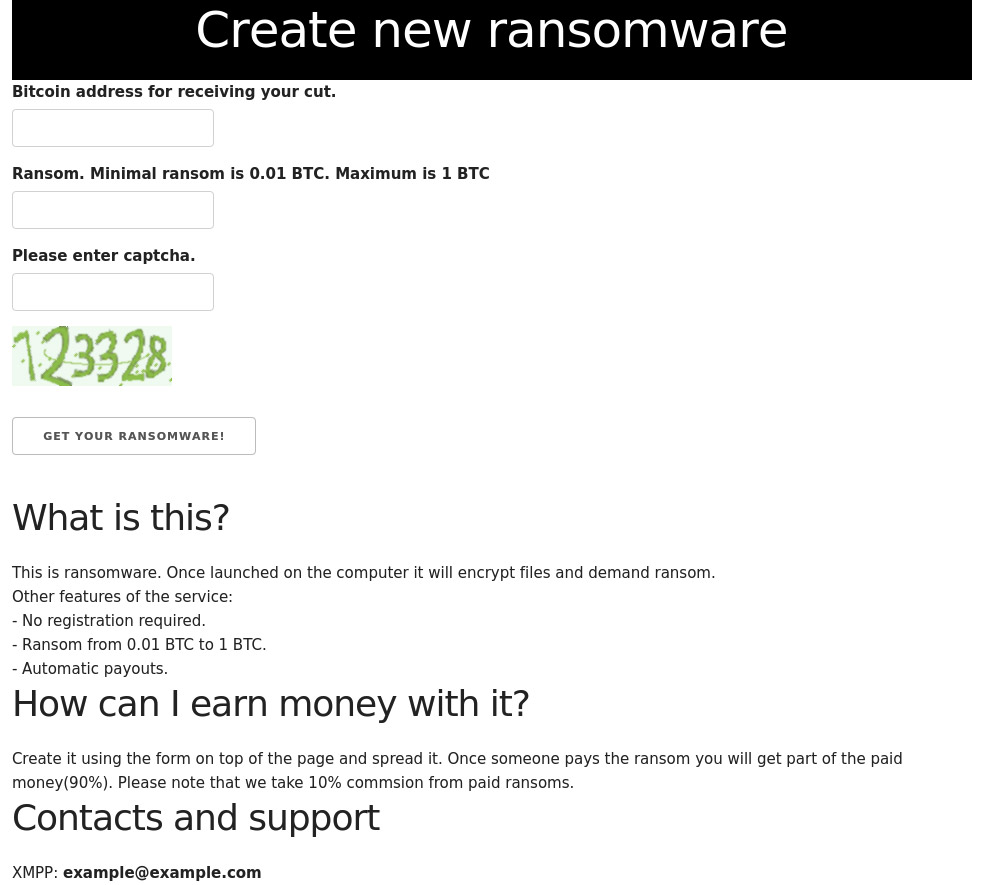
Source: Xavier Martens
"The process is straightforward: You just have to specify your bitcoin address to get the ransom, select the amount - minimum amount is 0.01 BTC, max 1BTC - and you get a nice malicious PE [portable executable] file delivered a few seconds later," Mertens writes in a blog post.
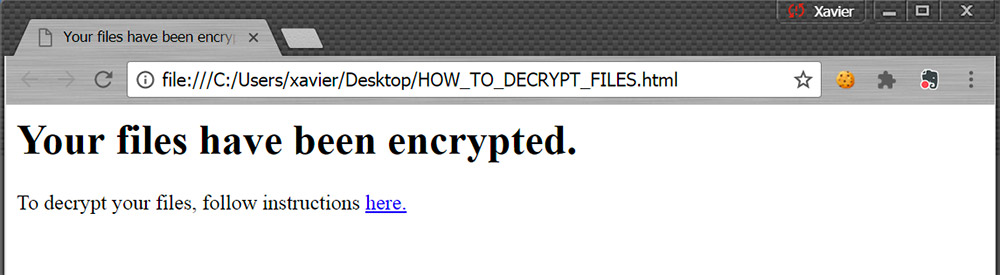
Source: Xavier Martens
"I tested the ransomware in a sandbox running a Windows 7 64bits protected by the Microsoft AV and all security features enabled," he says. "A few minutes later, my files were encrypted." He says crypto-locked files had a ".cypher" extension added to the end. It's not clear which, if any, ransomware families may have previously exhibited this type of behavior.
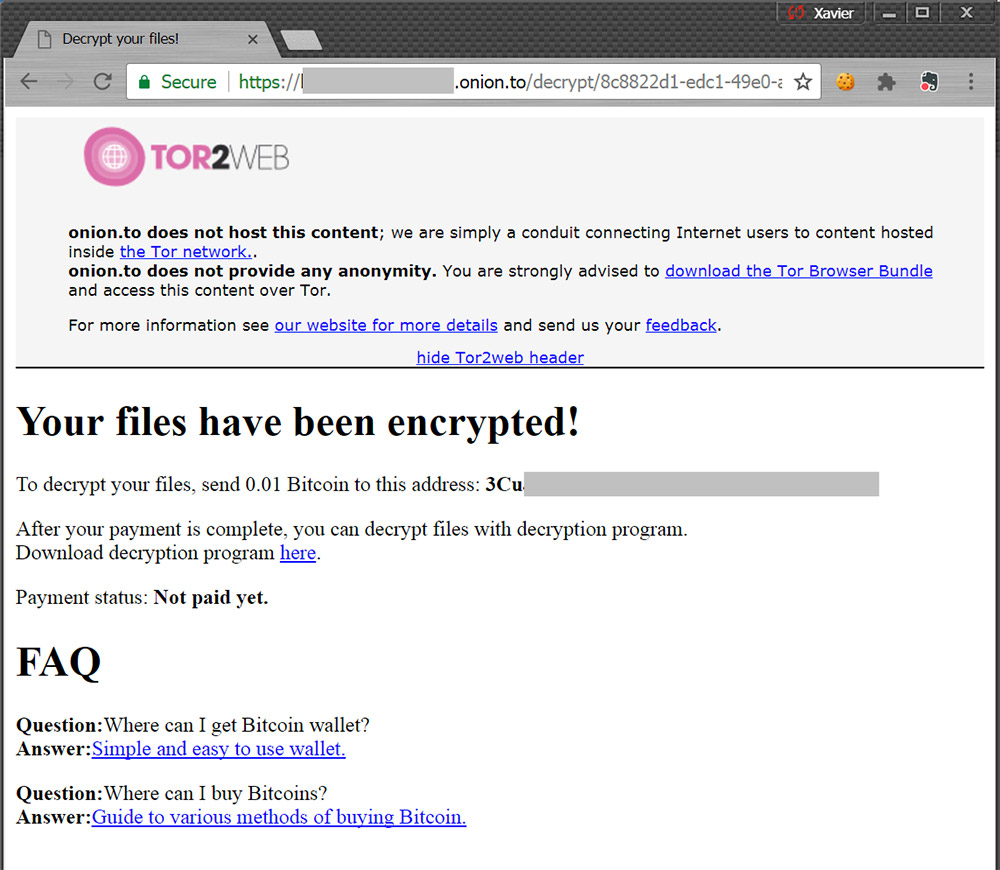
Source: Xavier Martens
Mertens says that the generated file was mostly unrecognized by anti-virus engines on the VirusTotal service. He also suspects the service is still in beta.
Ransomware Attacks Ease Off
The easy availability of ransomware in 2017 helped fuel what Malwarebytes, in a new report, calls a "banner year for ransomware." The firm reports that ransomware attacks against businesses increased by 90 percent last year, while those against consumers increased 93 percent. Last September, nearly 7 percent of all online attacks against businesses involved malware, it reports.
Infections in the early part of 2017 were driven by Locky and Cerber, while GlobeImposter and WannaCry dominated from July to September, it notes. Both WannaCry and the later NotPetya attacks improved on the ransomware concept by adding "ransom-worm" capabilities allowing them to spread by targeting exploits such as EternalBlue.
"The primary pushers of ransomware are made up of a few families that hold most of the market share, either due to a better overall product to sell on the darknet or a special relationship with the holders and herders of malicious spam botnets and exploit kits," which remain the primary techniques for distributing malware, the report says (see Dridex Banking Trojan Phishing Campaign Ties to Necurs).
But by the end of 2017, Malwarebytes recorded a decline in the volume of online attacks involving ransomware against both businesses and consumers. It also found that the pace of new ransomware development appeared to have slowed, with innovation growing "stale."
Ransomware Detections at Businesses (2016–17)
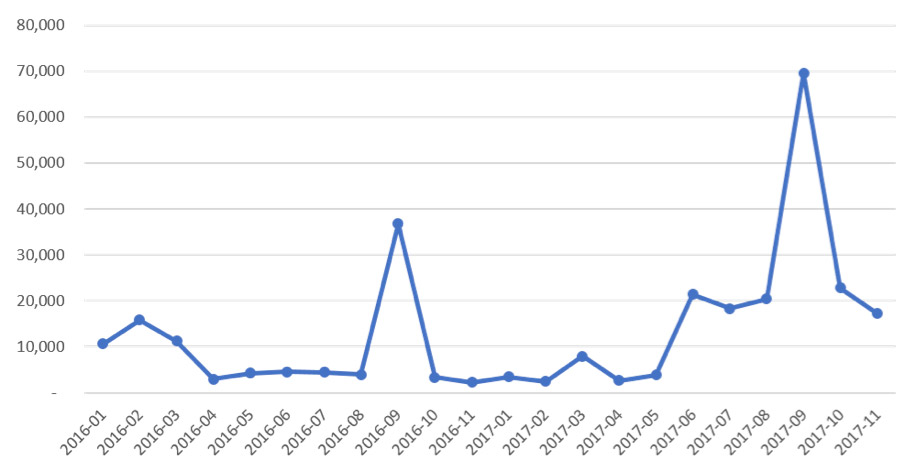
Source: Malwarebytes
Malwarebytes' Kujawa emphasizes that despite the overall number of ransomware attack attempts having decreased in recent months - largely in favor of cryptocurrency mining malware - ransomware remains a clear and present danger.
"Ransomware is never going to go away," he says. "It is a genius attack. It focuses directly on extorting money from the victim, there's no third-party sale that has to be made, there's nothing like that. It's just: 'Hey, you want your files back, give me back money.' It's simple and that's the amazing thing about it."
String of Healthcare Sector Hits
There are also signs that attackers could be getting more focused, especially against corporate targets. "A string of recent attacks suggests that ransomware operators are sharply ramping up their focus on healthcare organizations," tweets Troels Oerting, Group CISO of Barclays Bank. "Last week, Allscripts became the third organization in the health sector to get hit by ransomware since the start of this year" (see Allscripts Ransomware Attack a Reminder of Cloud Risks).
Organizations in the healthcare sector have long been a favorite target for extortion outfits, including ransomware gangs, because of the time-sensitive nature of their work. Literally, without access to essential data, people can die (see Ransomware Extortion: A Question of Time).
So while the overall volume of ransomware attacks may have recently declined, in many respects it appears to be business as usual for ransomware-using shakedown artists.
