- Feb 4, 2016
- 2,520
Some cyber-espionage outfits are so advanced that it takes months of sleuthing and digging through malware code to discover the ways they've carried out some of their hacks.
One such outfit is Turla, the codename given to a cyber-espionage group believed to be operating out of Russia, and which has been seen hitting targets that usually pose a political interest for the Russian state.
The group, active since 2007 but believed to have ties to cyber-espionage groups that were active in the 90s, was recently spotted hitting employees at embassies and consulates in post-Soviet states.
Malware appears to come from official Adobe servers
According to a 29-page report ESET published yesterday, Turla hackers have been using benign-looking Flash Player installers to deliver their code.
At first analysis, even if victims downloaded the files from sketchy sources, the file would connect to the actual Adobe domains and IP addresses to download and install the necessary files.
In spite of the legitimate-looking web traffic, employees at these embassies and consulates received a new backdoor trojan named Mosquito.
The attacks with the Mosquito backdoor have taken place since July 2016 and allowed the Turla group to siphon off important documents and infect the victim with additional malware.
ESET: Adobe was not compromised
ESET says it positively ruled out the scenario that Turla hackers somehow or someway managed to compromise Adobe's servers.
Something like this would have been noticed right away. Instead, ESET believes that Turla hackers might have shown off their creativity once more and moved the compromised vector further lower on the software supply chain.
ESET experts believe that Turla hackers were able to carry out a Man-in-the-Middle attack during the Adobe Flash Player installation process taking place on the victim's PC, by replaced the legitimate installer with their own, booby-trapped copy.
This allowed the file transfer to appear it came from Adobe's servers, but the actual files were switched somewhere in transit by the Turla hackers.
All clues point to another ISP-level compromise
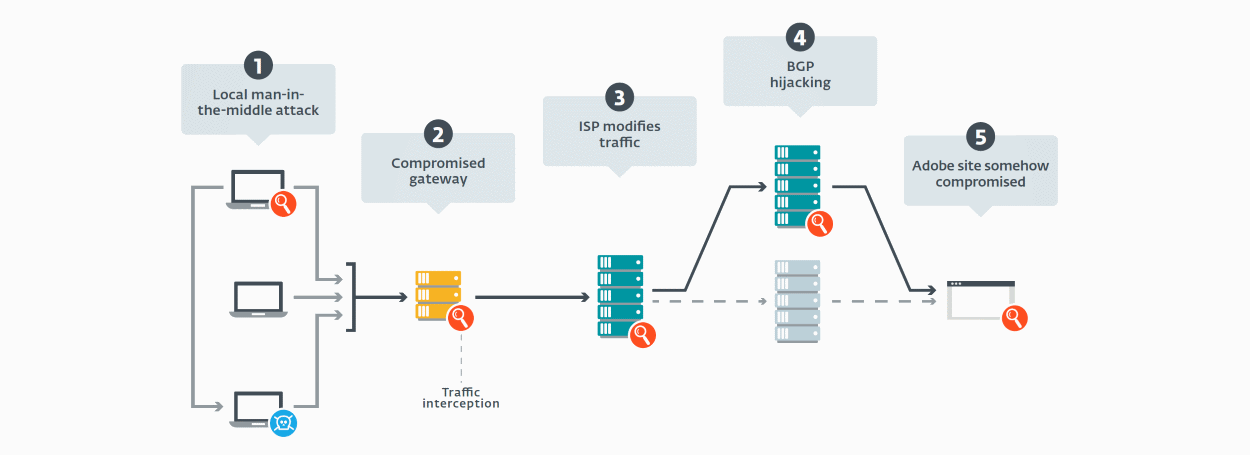
The point where the switcheroo took place is currently unknown, even to ESET researchers. They suspect four scenarios:
The most plausible scenario is option number three. This is because ISP-level MitM attacks have already taken place in the past.
- A machine within the network of the victim’s organization could be hijacked so that it acts as a springboard for a local Man-in-the-Middle (MitM) attack. This would effectively involve on-the-fly redirection of the traffic of the targeted machine to a compromised machine on the local network.
- The attackers could also compromise the network gateway of an organization, enabling them to intercept all the incoming and outgoing traffic between that organization’s intranet and the internet.
- The traffic interception could also occur at the level of internet service providers (ISPs), a tactic that – as evidenced by recent ESET research into surveillance campaigns deploying FinFisher spyware – is not unheard of. All the known victims are located in different countries, and we identified them using at least four different ISPs.
- The attackers could have used a Border Gateway Protocol (BGP) hijack to re-route the traffic to a server controlled by Turla, although this tactic would probably rather quickly set off alarm bells with Adobe or BGP monitoring services.
Back in September 2017, ESET reported that an unknown cyber-espionage group compromised an ISP and switched the files downloaded by certain targets. Attackers replaced legitimate files for WhatsApp, Skype, Avast, WinRAR, VLC Player, and others with files infected with the FinFisher spyware suite.
ESET didn't attribute those attacks to any particular hacking group, but they provide the best explanation for the recent mysterious Turla hacks. It's relatively well-known now that cyber-espionage groups take inspiration from one another.