- Dec 27, 2014
- 3,423
Krypto-Trojaner: TeslaCrypt 4.1A erschwert Desinfektion des Rechners, verschlüsselt weitere Formate
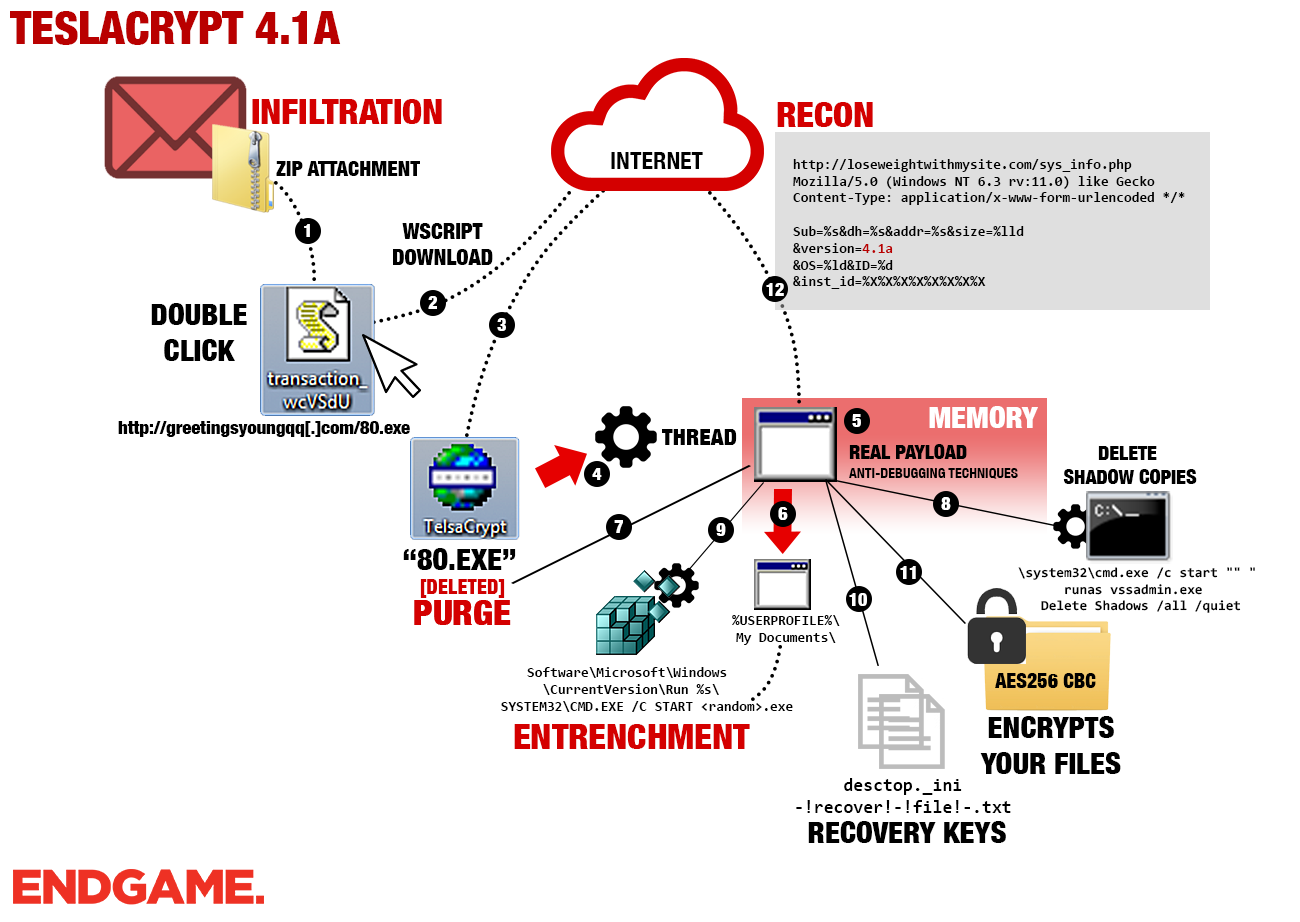
TeslaCrypt is one of the most successful crypto Trojans. And the developers are not tired to add new features to make life difficult for the victims. Version 4.1A encrypts even more formats more and makes it more difficult to disinfect the computer.
The developers of blackmail Trojan TeslaCrypt aren't tired yet of further optimizing their pest: Current version 4.1A has some new, nasty tricks on hand. According to an analysis of the security company Endgame, the new version now encrypts among others Bitcoin wallets and Scores. It also has an eye for files ending in .bak, being used by various programs for backups. Also, TeslaCrypt does not like being observed: Analysis tools such as Process Explorer from SysInternals or the Task Manager are being shut down by the malware.
TeslaCrypt hunts down specific file extensions, that might be of value for the user, but spares out system files. The recently added extensions denominated .bak .bsa, .litesql, .tiff and .wallet. The ending .bak is used by various programs for backups, .bsa is a file format by the {Video Game] Developer Bethesda (Fallout 3, The Elder Scrolls and more). In .litesql files to TeslaCrypt probably hopes that it concerns databases, .tiff is a common graphic format. Furthermore, it hunts for .wallet files the blackmailer: This ending is used for example by the widespread Bitcoin Wallet multi HD.
In addition, the ransomware developers incorporated measures that the analysis of the infected computer becomes more difficult: The pest kills among others the Task Manager. A user noticing unusual disk activity and wish to discover what process is responsible for it might be left out in the cold. Even the Process Explorer from SysInternals was shut down by the trojan. Disinfection of the infected computer is also difficult because TeslaCrypt also prevents the execution of the Registry Editor, the command prompt, and the configuration tool msconfig. With lastmentioned, you can quickly find out whether there are suspicious processes running at startup. The crypto Trojan moreover tries to hinder debugging.
According to the analysis, TeslaCrypt still is largely spread by mails with attachments . The annex contains a zip archive that contains a JavaScript file. It involves the Downloader Nemucod which recharges the actual threat and performs.
Users can quite easily protect themselves by the Windows Script Host being disabled, which is responsible for running scripts. As described in c't 7/16 on page 79, you put in an registry entry:
HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Windows Script Host \ Settings
a string called "Enabled" and sets its value to "0".
If this results in complications, because a programme does not run without an Host, set the value to "1" to activate the system component again. It is even easier to import we prepared registry files, we offer a free downloadable version.
ftp://ftp.heise.de/pub/ct/listings/1607-078.zip
Thank you for reading guys, I hope the translation isn't too bad
TeslaCrypt is one of the most successful crypto Trojans. And the developers are not tired to add new features to make life difficult for the victims. Version 4.1A encrypts even more formats more and makes it more difficult to disinfect the computer.
The developers of blackmail Trojan TeslaCrypt aren't tired yet of further optimizing their pest: Current version 4.1A has some new, nasty tricks on hand. According to an analysis of the security company Endgame, the new version now encrypts among others Bitcoin wallets and Scores. It also has an eye for files ending in .bak, being used by various programs for backups. Also, TeslaCrypt does not like being observed: Analysis tools such as Process Explorer from SysInternals or the Task Manager are being shut down by the malware.
TeslaCrypt hunts down specific file extensions, that might be of value for the user, but spares out system files. The recently added extensions denominated .bak .bsa, .litesql, .tiff and .wallet. The ending .bak is used by various programs for backups, .bsa is a file format by the {Video Game] Developer Bethesda (Fallout 3, The Elder Scrolls and more). In .litesql files to TeslaCrypt probably hopes that it concerns databases, .tiff is a common graphic format. Furthermore, it hunts for .wallet files the blackmailer: This ending is used for example by the widespread Bitcoin Wallet multi HD.
In addition, the ransomware developers incorporated measures that the analysis of the infected computer becomes more difficult: The pest kills among others the Task Manager. A user noticing unusual disk activity and wish to discover what process is responsible for it might be left out in the cold. Even the Process Explorer from SysInternals was shut down by the trojan. Disinfection of the infected computer is also difficult because TeslaCrypt also prevents the execution of the Registry Editor, the command prompt, and the configuration tool msconfig. With lastmentioned, you can quickly find out whether there are suspicious processes running at startup. The crypto Trojan moreover tries to hinder debugging.
According to the analysis, TeslaCrypt still is largely spread by mails with attachments . The annex contains a zip archive that contains a JavaScript file. It involves the Downloader Nemucod which recharges the actual threat and performs.
Users can quite easily protect themselves by the Windows Script Host being disabled, which is responsible for running scripts. As described in c't 7/16 on page 79, you put in an registry entry:
HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Windows Script Host \ Settings
a string called "Enabled" and sets its value to "0".
If this results in complications, because a programme does not run without an Host, set the value to "1" to activate the system component again. It is even easier to import we prepared registry files, we offer a free downloadable version.
ftp://ftp.heise.de/pub/ct/listings/1607-078.zip

Thank you for reading guys, I hope the translation isn't too bad
