silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,154
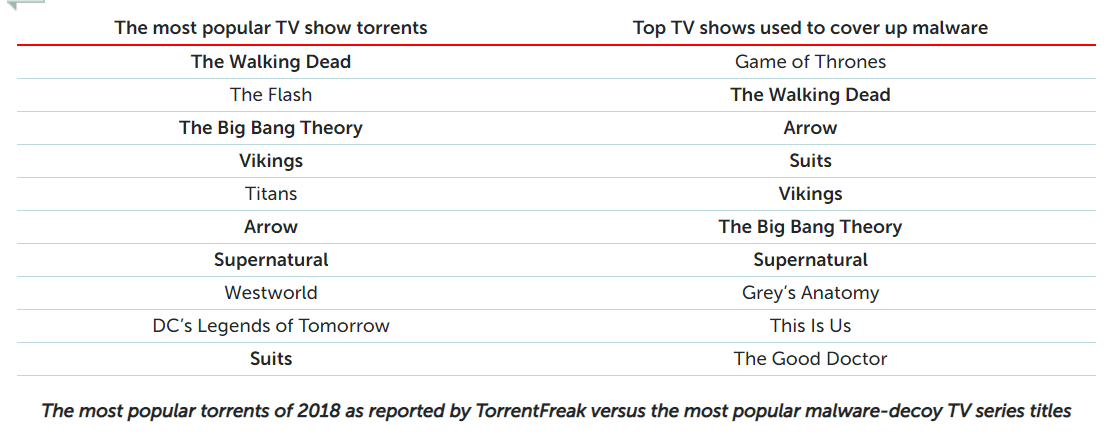
As Game of Thrones’ eighth season approaches, fans are getting ready for the ultimate clash of living vs. dead, fire vs. ice, human vs. monster. But they should be careful where they get their Jon Snow fix from; fresh analysis has concluded that the fantasy series is cybercriminals’ favorite target for disguising malware in illegal content downloads.
Game of Thrones accounted for 17 percent of all infected pirated content that researchers with Kaspersky Lab tracked last year, with 20,934 users attacked – even though no new episodes were released in 2018. And it came in as the most-targeted show despite being only the eighth most-popular to illegally stream, according to researchers; it also didn’t make the top 10 for torrent popularity.
“In many regions, popular programs are also consumed via illegal channels, such as torrent-trackers and unauthorized streaming platforms,” according to a Monday report from Kaspersky Lab. “Unlike legitimate resources, torrent trackers and hosted files may prompt a user to download a file that looks like an episode of a TV show, but is in fact malware with a similar name.”
Let’s face it, getting something for nothing has a certain appeal. So while most people should know by now that downloading pirated content is a high-stakes game that can result in a massive cyber-infection for one’s device, the reality is that tapping illegal markets for popular shows (especially those hosted on premium channels) continues to thrive as a practice.
The blockbuster HBO series is starting up again with its eighth and final season on April 14, and fans are a-twitter with anticipation. Not all of those fans have an HBO subscription however, so activity via pirate sites is expected to remain popular.
The danger lies not just with new episodes, either; binge-watching previous seasons before the premiere is a common activity as well. For example, the GoT Season 1 episode “Winter is Coming” is the most-targeted episode of the show, according to Kaspersky Lab’s findings.
The firm is not expecting GoT’s domination on the infected pirated content front to wane in 2019, either; malware is coming, so to speak.
“The first and final episodes, attracting the most viewers, are likely to be at greatest risk of malicious spoofing,” said Anton Ivanov, security researcher at Kaspersky Lab, in the analysis. “Online fraudsters tend to exploit people’s loyalty and impatience, so may promise brand new material for download that is in fact a cyberthreat. Keeping in mind that the final season of Game of Thrones starts this month, we would like to warn users that it is highly likely there will be a spike in the amount of malware disguised as new episodes of this show.”

