- Feb 13, 2017
- 1,486
Exploits linked to leaked NSA hacking tools have been causing havoc recently, with the WannaCry ransomware infecting more than 300,000 systems.
WannaCry made use of the previously unknown SMB exploit EternalBlue, but the leak included details of several others. Microsoft has released patches, but are they in place on all your PCs?
The simplest and most reliable way to find out is to run Windows Update and check for missing patches. If a system hasn’t been updated for a while, you’ll be missing far more than the NSA patches, and it’s important to get them all.
Chinese antivirus vendor Qihoo 360 has released an alternative in NSA Cyber Weapons Defense Tool, a simple program which checks for all NSA-related exploit patches, and also installs them if they’re not present.
The interface is straightforward. Run the program, it displays your protection status; clicking "Fix" installs any missing patches.
NSA Cyber Weapons Defense Tool bundles Microsoft’s various patches, enabling it to work online (unpack the executable with 7-Zip or something similar to find out more). Although this can be effective, we’re not happy about a program installing Windows patches without explaining what it’s doing. It doesn’t seem wise to install Windows updates from a third-party provider, either.
One extra complication we noticed is that tool doesn’t seem to detect every patched system (that is, it’ll falsely flag some fully updated systems as unprotected). Our guess is that the patches come in several forms, stand-alone and as rollups, and the program isn’t detecting them all.
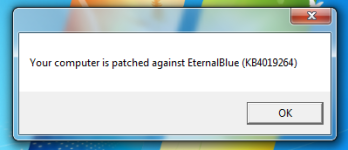
Check-EternalBlue, a small personal project by an ESET staffer, is a small and simple VBS script which checks for the EternalBlue patch only.
There’s no real interface, just one message explaining that the script is going to access your list of installed updates, and another stating whether it thinks your PC is patched.
The script ran without difficulty on our test PC, but that won’t be the case everywhere. VBS files are often used by malware, and it’s possible your security settings and software may block them.
Check-EternalBlue also had problems detecting whether the patch was installed. This doesn’t make it useless -- if it tells you you’re patched, you really are -- but means you can’t completely trust an "unprotected" verdict.
What might make Check-EternalBlue interesting anyway is that it’s a simple, plain-text VBS script. If you might ever want to create a similar tool in future, to detect whether a particular Windows patch is installed, you might be able to amend the script to do the job.
NSA Cyber Weapons Defense Tool and Check-EternalBlue are available now for Windows.
Two ways to check your PC is patched against EternalBlue
WannaCry made use of the previously unknown SMB exploit EternalBlue, but the leak included details of several others. Microsoft has released patches, but are they in place on all your PCs?
The simplest and most reliable way to find out is to run Windows Update and check for missing patches. If a system hasn’t been updated for a while, you’ll be missing far more than the NSA patches, and it’s important to get them all.
Chinese antivirus vendor Qihoo 360 has released an alternative in NSA Cyber Weapons Defense Tool, a simple program which checks for all NSA-related exploit patches, and also installs them if they’re not present.
The interface is straightforward. Run the program, it displays your protection status; clicking "Fix" installs any missing patches.
NSA Cyber Weapons Defense Tool bundles Microsoft’s various patches, enabling it to work online (unpack the executable with 7-Zip or something similar to find out more). Although this can be effective, we’re not happy about a program installing Windows patches without explaining what it’s doing. It doesn’t seem wise to install Windows updates from a third-party provider, either.
One extra complication we noticed is that tool doesn’t seem to detect every patched system (that is, it’ll falsely flag some fully updated systems as unprotected). Our guess is that the patches come in several forms, stand-alone and as rollups, and the program isn’t detecting them all.
Check-EternalBlue, a small personal project by an ESET staffer, is a small and simple VBS script which checks for the EternalBlue patch only.
There’s no real interface, just one message explaining that the script is going to access your list of installed updates, and another stating whether it thinks your PC is patched.
The script ran without difficulty on our test PC, but that won’t be the case everywhere. VBS files are often used by malware, and it’s possible your security settings and software may block them.
Check-EternalBlue also had problems detecting whether the patch was installed. This doesn’t make it useless -- if it tells you you’re patched, you really are -- but means you can’t completely trust an "unprotected" verdict.
What might make Check-EternalBlue interesting anyway is that it’s a simple, plain-text VBS script. If you might ever want to create a similar tool in future, to detect whether a particular Windows patch is installed, you might be able to amend the script to do the job.
NSA Cyber Weapons Defense Tool and Check-EternalBlue are available now for Windows.
Two ways to check your PC is patched against EternalBlue