- Dec 27, 2016
- 1,480
Since Friday, more than three lakh computers in over 150 countries have been in the grips of WannaCry attack, with their workstations locked for ransom.
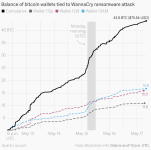
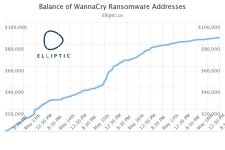
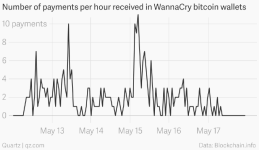
While the famous variant is still attacking the unpatched PCs around the world, some hope can be seen now with the release of decryption tools.
WannaCry Ransomware Decryption Keys
The WannaCry's encryption scheme works by generating a pair of keys on the victim's computer that rely on prime numbers, a "public" key and a "private" key for encrypting and decrypting the system’s files respectively.
To prevent the victim from accessing the private key and decrypting locked files himself, WannaCry erases the key from the system, leaving no choice for the victims to retrieve the decryption key except paying the ransom to the attacker.
But here's the kicker: WannaCry "does not erase the prime numbers from memory before freeing the associated memory," says Guinet.
Based on this finding, Guinet released a WannaCry ransomware decryption tool WannaKey, that basically tries to retrieve the two prime numbers, used in the formula to generate encryption keys from memory.
"It does so by searching for them in the wcry.exe process. This is the process that generates the RSA private key. The main issue is that the CryptDestroyKey and CryptReleaseContext does not erase the prime numbers from memory before freeing the associated memory." says Guinet
So, that means, this method will work only if:
"This is not really a mistake from the ransomware authors, as they properly use the Windows Crypto API."
While WannaKey only pulls prime numbers from the memory of the affected computer, the tool can only be used by those who can use those prime numbers to generate the decryption key manually to decrypt their WannaCry-infected PC’s files.
WanaKiwi: WannaCry Ransomware Decryption Tool
Good news is that another security researcher, Benjamin Delpy, developed an easy-to-use tool called "WanaKiwi," based on Guinet's finding, which simplifies the whole process of the WannaCry-infected file decryption.
All victims have to do is download WanaKiwi tool from Github and run it on their affected Windows computer using the command line (cmd).
WanaKiwi works on Windows XP, Windows 7, Windows Vista, Windows Server 2003 and 2008, confirmed Matt Suiche from security firm Comae Technologies, who has also provided some demonstrations showing how to use WanaKiwi to decrypt your files.
Although the tool won't work for every user due to its dependencies, still it gives some hope to WannaCry's victims of getting their locked files back for free even from Windows XP, the aging, largely unsupported version of Microsoft's operating system.



While the famous variant is still attacking the unpatched PCs around the world, some hope can be seen now with the release of decryption tools.
WannaCry Ransomware Decryption Keys
The WannaCry's encryption scheme works by generating a pair of keys on the victim's computer that rely on prime numbers, a "public" key and a "private" key for encrypting and decrypting the system’s files respectively.
To prevent the victim from accessing the private key and decrypting locked files himself, WannaCry erases the key from the system, leaving no choice for the victims to retrieve the decryption key except paying the ransom to the attacker.
But here's the kicker: WannaCry "does not erase the prime numbers from memory before freeing the associated memory," says Guinet.
Based on this finding, Guinet released a WannaCry ransomware decryption tool WannaKey, that basically tries to retrieve the two prime numbers, used in the formula to generate encryption keys from memory.
"It does so by searching for them in the wcry.exe process. This is the process that generates the RSA private key. The main issue is that the CryptDestroyKey and CryptReleaseContext does not erase the prime numbers from memory before freeing the associated memory." says Guinet
So, that means, this method will work only if:
- The affected computer has not been rebooted after being infected.
- The associated memory has not been allocated and erased by some other process.
"This is not really a mistake from the ransomware authors, as they properly use the Windows Crypto API."
While WannaKey only pulls prime numbers from the memory of the affected computer, the tool can only be used by those who can use those prime numbers to generate the decryption key manually to decrypt their WannaCry-infected PC’s files.
WanaKiwi: WannaCry Ransomware Decryption Tool
Good news is that another security researcher, Benjamin Delpy, developed an easy-to-use tool called "WanaKiwi," based on Guinet's finding, which simplifies the whole process of the WannaCry-infected file decryption.
All victims have to do is download WanaKiwi tool from Github and run it on their affected Windows computer using the command line (cmd).
WanaKiwi works on Windows XP, Windows 7, Windows Vista, Windows Server 2003 and 2008, confirmed Matt Suiche from security firm Comae Technologies, who has also provided some demonstrations showing how to use WanaKiwi to decrypt your files.
Although the tool won't work for every user due to its dependencies, still it gives some hope to WannaCry's victims of getting their locked files back for free even from Windows XP, the aging, largely unsupported version of Microsoft's operating system.
Last edited:
