- Apr 25, 2013
- 5,355
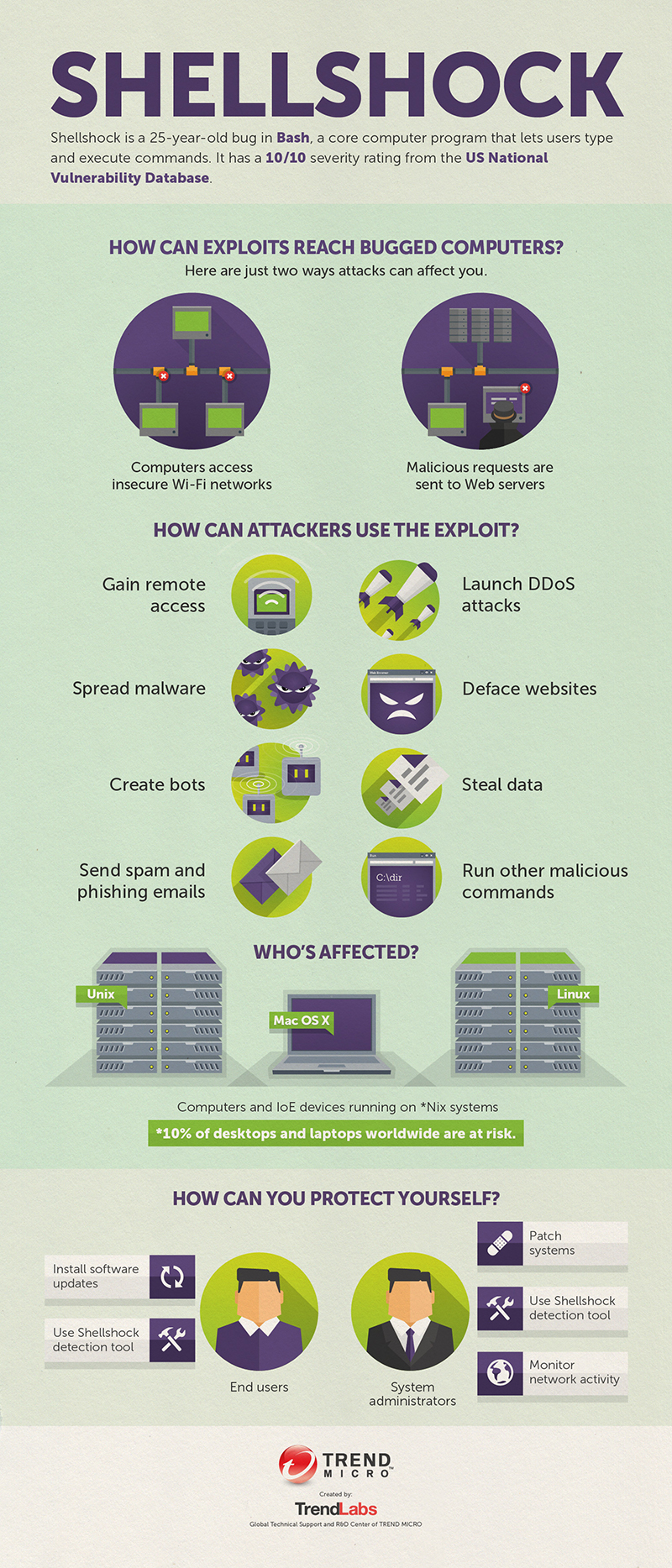
What To Do
Our technical post does a great job of detailing some general steps everyone should take to respond to this issue as well as the specific steps that Trend Micro customers should take.
There is currently a patch available for most affected distributions that partially addresses the vulnerability. Work continues on a more complete solution.
This issue is urgent and should be addressed immediately. Fortunately, the response plan is very straight forward.
1. If you’re an end-user, watch for patches for your Mac, your Android phone, other devices you may have.
2. If you’re running LINUX systems, deploy BASH patches immediately.
3. If you’re running LINUX/APACHE webservers using BASH scripts, consider retooling your scripts to use something other than BASH until a patch is available.
4. If you’re the customer of a hosted service, get in touch with them to find out if they’re vulnerable and find out their remediation plans if they are.
Your next step to protect your servers should be:
- Make sure that you have an IPS deployed in front of any vulnerable servers and that IPS is enabled and actively blocking exploits for CVE–2014–7169. Deep Security is available in a fully functioning trial (software or service—) that can immediately help customers.
- As patches become available, be sure to deploy them as quickly as possible to ensure layered coverage (in conjunction with your IPS).
- Continue to monitor the situation as it evolves.
- Temporarily switch your shell to one without this vulnerability. This vulnerability currently only exists in bash, other shells are unaffected. Here’s an how-to for Mac OS X.
- Once a patch is made available for your operating system, deploy it.
Trend Micro customers should refer to our knowledge base article on our support site. It’s the go-to page for all of our products and how this vulnerability relates to them. Please continue to refer back to this page as the situation evolves we will continue to provide updates there.
What protection does Trend Micro has in place for this vulnerability?
Trend Micro Deep Security customers must apply the update DSRU14-028 and assign the following rule:
If you’re not already a Trend Micro customer, you can download or sign up for our Deep Security product which is being updated to provide protections for this vulnerability from attack.
http://blog.trendmicro.com/bash-shellshock-vulnerability/