- Jul 16, 2014
- 215
In May 2017, Google announced there are more than 2 billion Android users worldwide, making it one of the most popular smartphone operating system. But that also makes it most vulnerable and a lucrative target for cyber criminals.
Recently, IT security researchers at Kaspersky have detected a new Android malware aiming at stealing personal and financial information of unsuspecting users around the world. Dubbed Xafecopy by researchers, the malware has infected 4,800 users in 47 countries with over 37.5 percent damage identified by researchers in India followed by Mexico, Turkey, and Russia.
The malware targets WAP billing payment method and steals money from a targeted devices without the knowledge of the victim. The malware is hidden in utility apps such as BatteryMaster and claims to save battery time, but in reality, once the app is installed it loads malicious code on the targeted device.
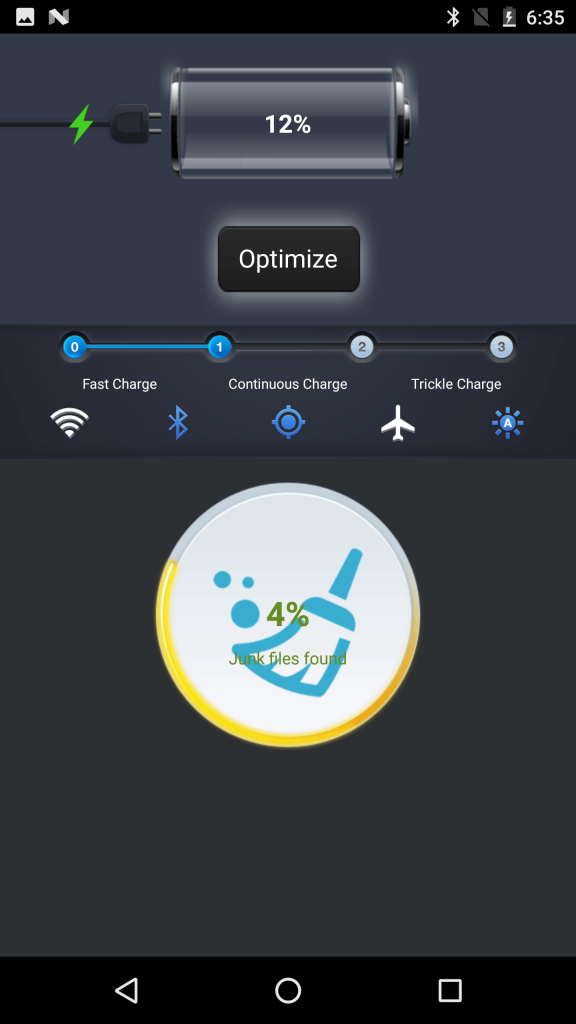
BatteryMaster app
From there, Xafecopy checks for websites with Wireless Application Protocol (WAP) billing feature and steals user money. The WAP billing is a type of mobile payment that charges fees directly to the user’s smartphone bill without the need of putting login credentials of card data. However, to bypass the ‘captcha’ system developed to protect users from theft and spams; the malware uses JavaScript files.
Furthermore, Xafecopy can also send SMS messages (most likely premium rate SMS), steal and delete incoming SMS messages.
Previously, Ztorg malware was found following similar tactics by using JavaScript files to by pass captcha.
Roman Unuchek, Senior Malware Analyst at Kaspersky Lab said that “WAP billing can be particularly vulnerable to so-called ‘clickjacking’ as it has a one-click feature that requires no user authorization. Our research suggests WAP billing attacks are on the rise. Xafecopy’s attacks targeted countries where this payment method is popular. The malware has also been detected with different modifications, such as the ability to text messages from a mobile device to Premium-rate phone numbers, and to delete incoming text messages to hide alerts from mobile network operators about stolen money.”
While users see a “Battery Master” interface the Trojan is trying to steal money
To protect yourself from this and other malware threats, Android users are advised not to download apps from third-party stores, do not install unnecessary apps and keep an eye on apps they download from Google Play Store since there are tons of malicious apps uploaded on the Store containing keyloggers logger and spyware.
Moreover, keep your devices updated, use a security software and scan your device on a daily basis.
Recently, IT security researchers at Kaspersky have detected a new Android malware aiming at stealing personal and financial information of unsuspecting users around the world. Dubbed Xafecopy by researchers, the malware has infected 4,800 users in 47 countries with over 37.5 percent damage identified by researchers in India followed by Mexico, Turkey, and Russia.
The malware targets WAP billing payment method and steals money from a targeted devices without the knowledge of the victim. The malware is hidden in utility apps such as BatteryMaster and claims to save battery time, but in reality, once the app is installed it loads malicious code on the targeted device.

BatteryMaster app
From there, Xafecopy checks for websites with Wireless Application Protocol (WAP) billing feature and steals user money. The WAP billing is a type of mobile payment that charges fees directly to the user’s smartphone bill without the need of putting login credentials of card data. However, to bypass the ‘captcha’ system developed to protect users from theft and spams; the malware uses JavaScript files.
Furthermore, Xafecopy can also send SMS messages (most likely premium rate SMS), steal and delete incoming SMS messages.
Previously, Ztorg malware was found following similar tactics by using JavaScript files to by pass captcha.
Roman Unuchek, Senior Malware Analyst at Kaspersky Lab said that “WAP billing can be particularly vulnerable to so-called ‘clickjacking’ as it has a one-click feature that requires no user authorization. Our research suggests WAP billing attacks are on the rise. Xafecopy’s attacks targeted countries where this payment method is popular. The malware has also been detected with different modifications, such as the ability to text messages from a mobile device to Premium-rate phone numbers, and to delete incoming text messages to hide alerts from mobile network operators about stolen money.”
While users see a “Battery Master” interface the Trojan is trying to steal money
To protect yourself from this and other malware threats, Android users are advised not to download apps from third-party stores, do not install unnecessary apps and keep an eye on apps they download from Google Play Store since there are tons of malicious apps uploaded on the Store containing keyloggers logger and spyware.
Moreover, keep your devices updated, use a security software and scan your device on a daily basis.
Last edited by a moderator:
