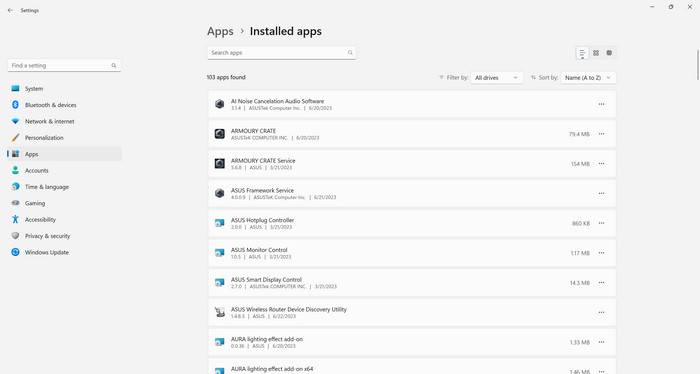
Adobe Acrobat Reader DC is a widely used software program that allows users to view, print, and annotate PDF (Portable Document Format) files. It has become the industry standard for PDF viewing and is used by millions of people around the world. However, with the rise of alternative PDF readers and concerns about security vulnerabilities, many users are questioning whether they should uninstall Adobe Acrobat Reader DC from their devices. In this article, we will explore what Adobe Acrobat Reader DC is, its features and benefits, potential security risks, and alternative PDF readers that you can consider.
What is Adobe Acrobat Reader DC?
Adobe Acrobat Reader DC, often referred to as simply Adobe Reader, is a free software program developed by Adobe Systems. It is designed to allow users to view, print, and annotate PDF files. PDF files are widely used for sharing documents because they preserve the formatting and layout of the original document, regardless of the software, hardware, or operating system used to view them.
Adobe Acrobat Reader DC offers a range of features that enhance the PDF viewing experience. These include the ability to search for specific words or phrases within a document, zoom in and out, navigate through pages, and add comments and annotations. It also allows users to fill out and sign PDF forms electronically, making it a valuable tool for businesses and individuals who frequently work with digital documents.
Benefits of Adobe Acrobat Reader DC
There are several benefits to using Adobe Acrobat Reader DC:
- Compatibility: Adobe Acrobat Reader DC is compatible with all major operating systems, including Windows, macOS, and Linux. This ensures that you can view PDF files on any device without compatibility issues.
- Feature-rich: Adobe Acrobat Reader DC offers a wide range of features that enhance the PDF viewing experience. From searching for specific words to adding annotations and filling out forms, it provides users with the tools they need to work with PDF files effectively.
- Integration with Adobe Document Cloud: Adobe Acrobat Reader DC seamlessly integrates with Adobe Document Cloud, allowing users to access and store their PDF files in the cloud. This enables easy collaboration and sharing of documents across devices and platforms.
Security Risks of Adobe Acrobat Reader DC
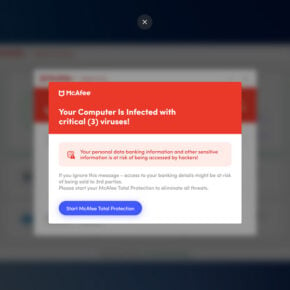
While Adobe Acrobat Reader DC is a powerful and feature-rich PDF viewer, it has been the target of security vulnerabilities in the past. These vulnerabilities can potentially be exploited by hackers to gain unauthorized access to a user’s device or sensitive information. Adobe regularly releases security updates and patches to address these vulnerabilities, but it is important for users to keep their software up to date to ensure they are protected.
If you are concerned about the security risks associated with Adobe Acrobat Reader DC, it is recommended to regularly scan your device for malware. Malwarebytes Free is a reputable and effective malware scanning tool that can help detect and remove any potential threats. You can download Malwarebytes Free from their official website and run a scan to ensure your device is secure. Malwarebytes Free.
Alternative PDF Readers
If you are considering uninstalling Adobe Acrobat Reader DC, there are several alternative PDF readers available that you can consider:
- Foxit Reader: Foxit Reader is a popular PDF reader that offers a range of features, including annotation tools, form filling capabilities, and document signing. It is known for its fast performance and small file size.
- Nitro Reader: Nitro Reader is a feature-rich PDF reader that allows users to view, edit, and create PDF files. It offers a user-friendly interface and a range of tools for working with PDF documents.
- Sumatra PDF: Sumatra PDF is a lightweight and open-source PDF reader that focuses on simplicity and speed. It is designed to be fast and efficient, making it a great choice for users who prioritize performance.
These alternative PDF readers offer similar features to Adobe Acrobat Reader DC and can be viable options if you are looking for alternatives.
Conclusion
Adobe Acrobat Reader DC is a powerful and widely used PDF viewer that offers a range of features and benefits. However, it is important to be aware of the potential security risks associated with the software and take necessary precautions to protect your device and data. Regularly updating Adobe Acrobat Reader DC and scanning your device for malware using tools like Malwarebytes Free can help mitigate these risks.
If you are considering uninstalling Adobe Acrobat Reader DC, there are several alternative PDF readers available that offer similar features and functionality. Foxit Reader, Nitro Reader, and Sumatra PDF are popular options that you can explore.
Ultimately, the decision to uninstall Adobe Acrobat Reader DC depends on your specific needs and concerns. Assess the features, security risks, and alternatives discussed in this article to make an informed decision that best suits your requirements.