Trojans
How to Remove KMSPico Malware [Virus Removal Guide]
Many users—especially those looking for free access to premium software—eventually come across KMSPico. It’s one of the most widely used hack tools for activating Microsoft…

Help Bust Scammers
Your report helps us connect the dots across domains, ads, and messages so the next person doesn’t get tricked.
Protect Your Accounts
Avoid Irreversible Payments
If someone demands payment by gift card, crypto, wire, or “friends and family,” assume it’s a scam. Those methods are popular because they’re hard to reverse and easy to disappear with.
Scams End Here
Remove Ddqatencj.exe *32 virus (Malware Removal Guide)
If your computer is very slow and there are multiple instances of Ddqatencj.exe *32, dllhost.exe or cmmon32.exe process running in…
Remove Hdeppwkv.exe *32 virus (Malware Removal Guide)
If your computer is very slow and there are multiple instances of Hdeppwkv.exe *32, dllhost.exe or cmmon32.exe process running in…
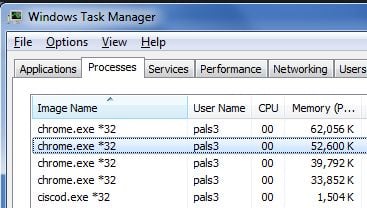
Remove multiple fake Google Chrome virus (Removal Guide)
Google Chrome is a background process used by Chrome web browser, however in a recent attack (Poweliks trojan), cyber criminals have…
Remove e9967a.com virus (Malware Removal Guide)
If your antivirus is constantly blocking e9967a.com, then your computer is infected with Trojan.Poweliks. This is the text of the…

Scam Hunter Mode
Submit the evidence and we’ll verify what we can, then turn it into a practical alert others can act on.


![How to Remove KMSPico Malware [Virus Removal Guide] 6 kmspico malware](https://malwaretips.com/blogs/wp-content/uploads/2023/01/kmspico-malware.jpg)