You open your inbox and find a threatening message: someone claims to be from a cartel and says you wasted an escort’s time, demanding payment or threatening violence. Panic spikes – is it real? Are they watching you?
Short answer: in the vast majority of cases, this is a scam – a form of extortion and sextortion that uses fear and embarrassment to extract money. Scammers impersonate escorts, pimps, or cartel members, combine threats with personal data (often harvested or guessed), and demand payment by cryptocurrency, gift cards, or wire transfers. This article explains the scam in depth and gives practical steps you can use immediately.
Scam Overview
The “escort + cartel” email scam is a frightening variant of extortion that mixes escort scams, sextortion, and cartel-impersonation threats. It typically follows this pattern:
- A victim interacts with an escort ad or a fake profile (on classifieds, dating apps, or messaging platforms).
- Contact is moved off-platform (WhatsApp, Telegram, SMS, email) where scammers can control the conversation.
- The scammer manufactures an episode (you “no-show”, “wasted our time”, etc.) and demands a “fine”.
- To escalate fear they claim affiliation with a violent group (a cartel name such as “CJNG” is often used) and threaten harm to you or your family if you don’t pay immediately.
Why this works: shame, fear, and urgency. Embarrassing subject matter (sex work, escorts, explicit images) makes many victims reluctant to report to police, which is exactly what the scammers count on. Adding “cartel” branding escalates fear – an organized crime group is imagined, with violent capability and reach – increasing the likelihood someone will pay quickly.
Multiple jurisdictions and agencies have repeatedly warned about automated sextortion and extortion campaigns. Law enforcement and public-safety pages emphasize that many of these messages are opportunistic scams: the scammers do not have insight into your private life and often bluff about video evidence or cartel connections. The FBI, state police, and national fraud reporting portals have published guidance describing how sextortion and extortion campaigns work and how to report them.
Real-world reporting and consumer protection blogs show a clear pattern: the “escort + cartel” script arises again and again (often on Reddit and local police alerts), and the underlying mechanism is social engineering plus data harvesting rather than real criminal affiliations. Victim reports and investigative posts repeatedly show the same script lines: threats to visit the victim or family, graphic images, and demands to “pay the fine” via cryptocurrency, gift cards, or money transfer.
Important nuance: while most of these incidents are scams, there are real criminal groups that engage in online fraud and violent intimidation. Law enforcement treats threatening communications seriously; if the message contains clear evidence of surveillance, local police involvement or direct threats to immediate safety should be escalated. The general rule: don’t pay, preserve evidence, and report.
How the Scam Works
This section reconstructs the typical lifecycle of an escort + cartel email scam so you can recognise each stage if it happens to you or someone you help.
Stage 1 – The Hook: Fake Listings, Profiles, and Initial Contact
- Fake profiles and ads: Scammers create escort ads on classifieds, clone real adverts, or use AI/stolen photos to make convincing profiles.
- Move off-platform: They ask to continue the chat on WhatsApp, Telegram, SMS, or email to avoid platform moderation.
- Request “verification”: They might ask for a deposit, selfies, or explicit images – any material that can be weaponized later.
- Data enrichment: When you give a name, phone number, or photo, scammers search social media and data brokers to build a convincing threat narrative.
Stage 2 – The Accusation and Threat
- No-show or “we lost money” narrative: The attacker invents or exaggerates an incident and claims you caused financial harm that must be remedied by payment.
- Cartel branding: The attacker impersonates a cartel member or a violent fixer, using names like CJNG or “pimps” to amplify fear and suggest real violence.
- “Proof” and personalization: They may insert public data or reused photos as fake proof. Reuse indicates a mass scheme rather than targeted surveillance.
Stage 3 – The Demand and Payment
- Preferred payment channels: Cryptocurrency, gift cards, reload cards, or international money transfers – methods hard to reverse or trace.
- Time pressure: Messages include short deadlines and escalating threats to force quick compliance.
- Repeated extortion: Payment rarely ends contact. If someone pays once, scammers often demand more later or sell the victim’s contact to other criminals.
Stage 4 – Follow-up and Aftermath
- Repeat contact: If ignored, the scam may escalate into mass spamming or a new angle (threat to publish images, contact your work, etc.).
- Data resale: Images, names, and payment records may be sold or reused by other scammers.
- Longer-term harms: Emotional trauma, reputational risk, identity theft, and persistent nuisance contact are common consequences.
Red Flags – How to Tell It’s a Scam
Watch for multiple red flags in the same message – together they make the message almost certainly fraudulent:
- Demand for immediate payment via crypto or gift cards.
- Blanket threats that reference a cartel or gang without verifiable evidence.
- Use of the same images or stock photos seen elsewhere (reverse image search can reveal reuse).
- Poor grammar and generic threat scripts that read like templates.
- Requests for “verification photos” or upfront deposits.
- Statements threatening physical violence while using crude or mass-email style language.
What to Do If You’ve Been Targeted
Do NOT pay before following these steps. Paying usually makes things worse. Follow this checklist precisely:
- Do not panic – do not pay. Paying extortionists rarely resolves the issue and often encourages more demands.
- Preserve all evidence. Save raw email headers (in Gmail: “Show original”), full message text, attachments, screenshots, phone numbers, and any payment receipts. Do not edit the evidence file names or message contents.
- Reverse image search any attachments. Use Google Images or TinEye to see whether images are stock or previously circulated; reuse suggests a mass scam.
- Secure your accounts immediately. Change passwords for email and social media, enable two-factor authentication (2FA), and review account login history for unauthorized access.
- Scan for malware. If you clicked links or opened attachments, run a full antimalware scan with up-to-date signatures. Consider a second opinion scanner or a factory reset if compromise seems likely.
- Contact local law enforcement if you feel threatened. Provide them with all preserved evidence. If you are in imminent danger, call your emergency services number.
- File a report with the central cybercrime authority in your country. In the U.S., use the FBI IC3 portal; other countries have equivalent cybercrime reporting bodies. Filing a report helps authorities track and combat these campaigns.
- Report the offending profile to the platform used for contact. If the initial contact was on a dating app, classifieds site, social network, or messaging service, report the profile and attach screenshots and message text.
- Don’t respond or negotiate emotionally. Avoid threats, pleading, or attempts to trick the scammer. Engagement can reveal more information to them or encourage escalation.
- If you already paid, preserve payment records. Keep receipts, transaction IDs, wallet addresses, or gift card photos and provide these to law enforcement and your bank where possible.
- Notify affected third parties. If family members or colleagues are referenced, inform them so they can be alert to related fraud or harassment.
- Consider legal or privacy assistance. If explicit images were shared, consult an attorney or takedown/reputation service about removal strategies and legal options for non-consensual image distribution.
- Share a redacted warning. If you are comfortable, share a redacted version of the scam message in community groups to warn others and reduce the pool of future victims.
Ready-to-use Police / IC3 Report Template
Copy the template below, fill in your details, attach raw headers and screenshots, and submit to local police or the IC3 portal.
Police/IC3 Report - Escorts + Cartel Email / Sextortion
Contact info:
Full name: ______________________
Email(s) used by victim: ______________________
Phone: ______________________
City & Country: ______________________
Date / Time Received:
______________________ (include timezone)
Message origin:
From (email/SMS/username): ______________________
Any reply messages sent? Yes / No - if yes, include date/time and text.
Full message text (copy/paste verbatim):
__________________________________________________________________
__________________________________________________________________
(Attach screenshots and raw email source/header)
Attachments (list file names):
1) ______________________
2) ______________________
Payment request details:
Amount requested: ______________________
Currency: ______________________
Payment method (e.g., Bitcoin address, gift card type, wiring instructions): ______________________
Any interactions or payments made:
(Yes / No) - if yes, provide receipts, transaction IDs, wallet address, dates, and copy of bank/gift card transaction.
Potential personal data exposed or used by scammer:
(Names of family members, workplace, address references, social profiles, photos sent by victim)
__________________________________________________________________
Other evidence collected:
- Raw email header file (attached)
- Screenshots (attached)
- Reverse image search results (attached)
- Chat logs (attached)
Requested action:
Please investigate the extortion attempt and advise on protection steps for myself and my family. I am available to provide additional evidence or to give testimony if needed.
Signature: ______________________
Date: ______________________
Prevention – How to Reduce Risk
Practical steps to avoid becoming a victim:
- Avoid sharing explicit images or compromising personal data with strangers.
- Use burner emails and numbers for classified ads or escort services, never your main accounts.
- Enable 2FA and unique passwords for critical accounts.
- Use reverse image search before trusting profiles that contact you.
- Limit publicly visible profile information on social networks.
- Do not click attachments or links from unknown senders; scan attachments with antimalware tools first.
- If you must interact with potentially risky services, use payment methods that minimise personal exposure and never send gift cards/crypto in response to threats.
Frequently Asked Questions (FAQ)
What is the Escorts and Cartel Email Scam?
The Escorts and Cartel Email Scam is a fear-based extortion scheme where scammers claim to be part of a dangerous criminal group, often mentioning names like the “Jalisco New Generation Cartel (CJNG).” Victims typically receive threatening messages accusing them of wasting an escort’s time and demanding a “fine” to avoid harm to themselves or their family. These threats are designed to create panic and force quick payment through untraceable methods such as cryptocurrency, gift cards, or wire transfers. In reality, most of these threats are scams – they are mass or semi-automated campaigns sent to many people at once.Why are these scams so effective?
These scams work because they exploit two powerful psychological triggers: embarrassment and fear. The escort element makes victims hesitant to report the scam to authorities due to stigma or privacy concerns, while the cartel element adds a layer of fear and urgency. Scammers count on victims reacting emotionally instead of rationally, leading them to pay quickly. They often use aggressive language, fake cartel names, and threatening images to appear more convincing.Is the CJNG Cartel really behind these emails?
Almost certainly not. Law enforcement and cybersecurity experts have repeatedly confirmed that the vast majority of cartel-themed extortion emails are scams, not actual threats from organized crime. Real criminal groups do not typically send poorly written mass emails demanding small payments. These scammers simply use cartel names to create fear and make their threats sound more dangerous. If the message includes only vague personal details or recycled images, it’s almost certainly fake.What should I do if I receive one of these emails?
If you receive a threatening email like this, do not panic and do not pay. Save the entire email including the header information, take screenshots of any attachments, and report it to the appropriate authorities (such as the FBI’s IC3 in the U.S. or your local cybercrime unit). Reverse image search any attachments to check if they are stock or reused images. Secure your accounts, enable two-factor authentication, and avoid any further communication with the scammer.Will the scammers come after me or my family if I ignore the message?
In nearly all cases, no. These scammers typically do not have any real-world connection to the victim. They rely on fear to make you pay voluntarily. Once they realize you won’t respond or pay, they often move on to easier targets. However, if a message includes credible, specific threats (e.g., real-time location data), you should immediately contact local law enforcement for protection and investigation. But statistically, most of these threats are empty.What if I already paid the “fine” they demanded?
If you have already paid, gather all payment records, wallet addresses, receipts, and any other evidence you have. Report the incident to the police and to your financial institution if applicable. While recovering the money may be difficult, filing a report increases the chances of tracing or linking the payment to other cases. Also, secure your personal accounts and stay alert for follow-up scams, as scammers often target people who have already paid once.Why do scammers use cryptocurrency or gift cards for payment?
Scammers prefer payment methods that are fast, anonymous, and hard to trace. Cryptocurrency like Bitcoin allows them to receive money without revealing their identity. Gift cards and reload cards are also commonly used because once the codes are sent, the money is nearly impossible to recover. Any demand for these payment types should be treated as an immediate red flag for fraud.Can scammers really access my personal data?
Most scammers don’t have deep personal information about you. They often use your email address, phone number, or details you may have shared earlier to make their threats sound more personal. In some cases, they might reference public information or breached data. That’s why it’s crucial not to share sensitive information, photos, or IDs with strangers online, and to use separate accounts for potentially risky interactions.What should I include when reporting the scam?
When reporting, include the full text of the email, the raw email headers, any attachments, payment details if applicable, and a timeline of interactions. Provide screenshots and the email address or phone number used by the scammer. The more information you provide, the better the chances that law enforcement can track the campaign and link it to other victims. Reporting is important even if you didn’t pay – it helps protect others.Analysis of the Example Message
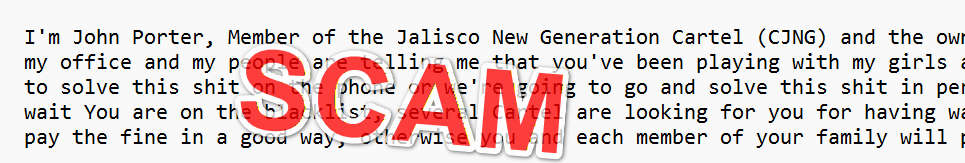
You included this message as an example (verbatim):
“I’m John Porter, Member of the Jalisco New Generation Cartel (CJNG) and the owner of the business where you wanted to hire one of my escorts, so arrived at my office and my people are telling me that you’ve been playing with my girls and wasting their time and making my business lose money, so we have two ways to solve this shit on the phone or we’re going to go and solve this shit in person with you or with your whole family, so come back to me if you don’t just wait You are on the blacklist, several Cartel are looking for you for having wasted the girls’ time. The best thing is that you contact me immediately and pay the fine in a good way, otherwise you and each member of your family will pay the consequences.”
Why this is almost certainly a scam:
- Template language and reuse: The phrasing and structure match widely reported extortion templates used in mass campaigns.
- Inconsistency with real criminal behaviour: Real organized-crime intimidation tends to use local intermediaries and different channels; a crude mass email in broken phrasing is an inefficient tool for real cartels.
- Monetization pattern: Immediate demand for a “fine” indicates financial motive typical of scammers, not legitimate reprisals.
- Lack of verifiable identifiers: There’s no local contact, invoice, legal channel, or traceable identifier – all hallmarks of a scam.
The Bottom Line
Escort + cartel email scams are a terrifying but common extortion technique based on social engineering and mass messaging. In most documented cases the messages are scams – mass or semi-automated campaigns that rely on shame and fear. The recommended course of action is consistent: don’t pay, preserve evidence, secure your accounts, and report to law enforcement and relevant cybercrime portals. Early reporting and evidence preservation help protect you and others.