- Mar 10, 2024
- 366
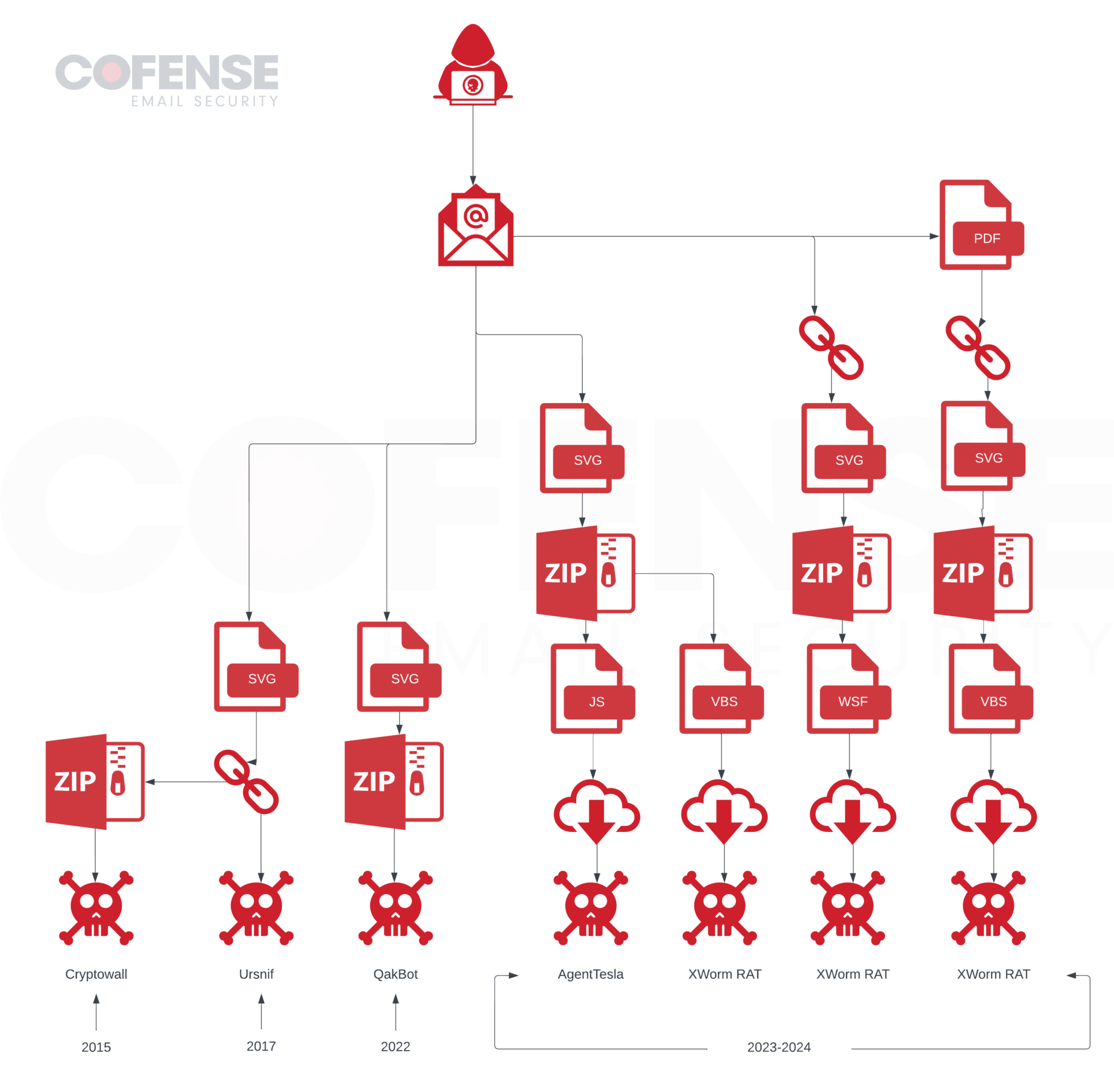
Cybersecurity researchers have discovered an intricate multi-stage attack that leverages invoice-themed phishing decoys to deliver a wide range of malware such as Venom RAT, Remcos RAT, XWorm, NanoCore RAT, and a stealer that targets crypto wallets.
The email messages come with Scalable Vector Graphics (SVG) file attachments that, when clicked, activate the infection sequence, Fortinet FortiGuard Labs said in a technical report.
The modus operandi is notable for the use of the BatCloak malware obfuscation engine and ScrubCrypt to deliver the malware in the form of obfuscated batch scripts.

Attackers Using Obfuscation Tools to Deliver Multi-Stage Malware via Invoice Phishing
Cybersecurity experts uncover a sophisticated multi-stage attack! 🛡️ Malware including Venom RAT, Remcos RAT, and more deployed via invoice-themed ph
 thehackernews.com
thehackernews.com