Privacy theater. It’s trivial for Google, Microsoft, or anyone else to compute the hashes of every site in the Alexa Top 10 Million. If you don’t trust the server, hashing the the URLs of the sites you visit won’t change anything.
Not quite. Here's why.
Yes, you can decrypt simple domain names without any issue. Example;
www.google.com is
191347bfe55d0ca9a574db77bc8648275ce258461450e793528e0cc6d2dcf8f5 hashed by SHA-256. Now, if we change from that to
www.Google.com (yes, just uppercase letter G) the entire SHA-256 hash changes and is now
fb0d6fbb3fff0090731e98c9d3088f9b0dcbcbd45d42b32ba6ea5b07ffd4840a.
While you could easily decrypt the first hash, unless you know what change was made to generate the new SHA-256 hash, there is no way to decrypt it. Don't believe me?
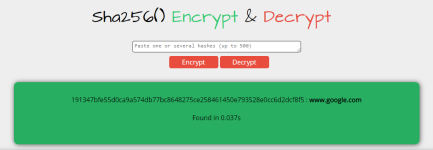
Here's the website that tries to decrypt the SHA-256. If you enter first hash, you get the result as
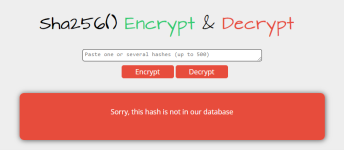
www.google.com; but when you enter the second hash, it says that match isn't found in their database so they can't show the result.
Now, if you can't decrypt that simple change. How could you decrypt the entire URL? You can't. That's why Google's implementation is much, much better than SmartScreen is. In fact, Chrome will only send hash if you came across malicious website; if not, it won't send anything because all other checks are done locally, on your device. Meanwhile, at Microsoft, they don't have to go through all that trouble because full URLs are sent in plain text to Microsoft's servers via HTTPS. That HTTPS means nothing when rogue SSL certificate is found on user's computer. MITM attack could easily decrypt what was sent to SmartScreen's servers.
One more thing. Do you know why security experts recommend setting a strong and different password for each user account? This is the reason why. Once hackers get their hands on user account database, they'll get e-mail addresses in plain text and passwords in hashed format. If password is really popular and not unique, they could just put the hash into decrypter like I did and get the result fast. If you made unique and strong password with different symbols, chances their decrypt tool will give them your password are non-existent, as to this day, SHA-256 hasn't been cracked.




