Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,188
Malware Loaders (recent examples).
The last example is uncommon. Most Loaders are digitally signed with fake certificates. Malware with an EV certificate is rare.
Malware loaders (also known as droppers or downloaders) are a popular commodity in the criminal underground. Their primary function is to successfully compromise a machine and deploy one or multiple additional payloads.
A good loader avoids detection and identifies victims as legitimate (i.e. not sandboxes) before pushing other malware. This part is quite critical as the value of a loader is directly tied to the satisfaction of its “customers”.

New Go loader pushes Rhadamanthys stealer
A malicious ad for the popular admin tool PuTTY leads victims to a fake site that downloads malware.www.threatdown.com
Malware loaders are tricky business for SOC teams. Mitigation for one loader may not work for another, even if it loads the same malware. And they’re one of the most common tools for a cyber-threat actor to secure initial access to a network, then help drop payloads (remote-access software and post-exploitation tools are popular choices).
ReliaQuest has uncovered a load of loaders causing havoc for defenders. The seven that we observed the most in customer environments so far this year are shown in Figure 1.
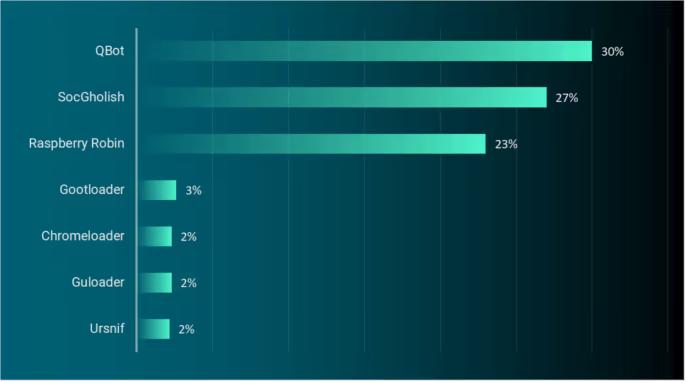

3 Malware Loaders You Can’t (Shouldn't) Ignore - ReliaQuest
Loader malware is working behind the scenes in many organizations' environments, doing the heavy lifting that helps an infection spread. ReliaQuest has picked out the most commonly observed loaders and outlined why SOC analysts should worry about them, plus how to defend against them.www.reliaquest.com
Malware loaders, critical for deploying malware, enable threat actors to deliver and execute malicious payloads, facilitating criminal activities like data theft and ransomware. Utilizing advanced evasion techniques, loaders bypass security measures and exploit various distribution channels for extensive impact, threat groups enhance their ability to download and execute various malware types as demonstrated by Smoke Loader and GuLoader, highlighting their role in extensive malware distribution.
Agent Tesla's New Ride: The Rise of a Novel Loader
Malware loaders enable threat actors to deliver and execute malicious payloads, facilitating criminal activities like data theft and ransomware.www.trustwave.com
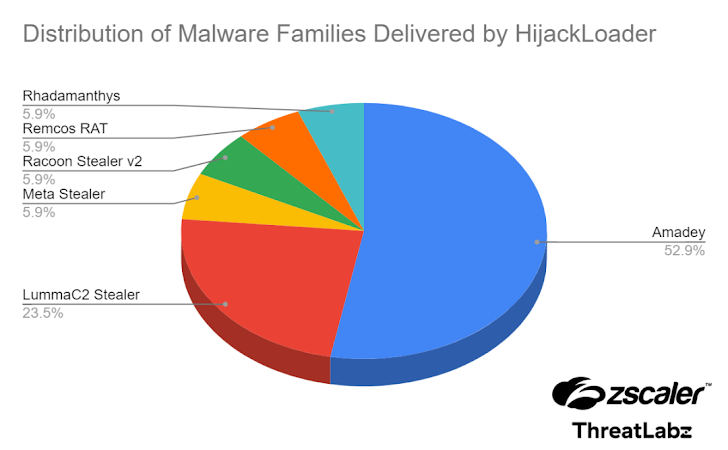

Hijack Loader Malware Employs Process Hollowing, UAC Bypass in Latest Version
A newer version of the Hijack Loader malware has been observed with updated anti-analysis techniques to evade detection.thehackernews.com
The new Rugmi malware loader is also known as Win/TrojanDownloader.Rugmi is gaining notoriety among numerous hackers for its role in delivering various information stealers. Some confirmed infostealers that benefited from this new malicious tool are the Lumma Stealer, Vidar, RecordBreaker, and Rescoms.
Moreover, Rugmi is a loader that has three distinct components. The first one is a downloader that fetches an encrypted payload. The next one is a loader that runs the payload from internal resources, and the last one is a loader that runs the payload from an external file on the disk. This intricate structure of this new tool allows the malware to operate with a high degree of sophistication.
The Impact of GuLoader
GuLoader is available as a service for a relatively low price, can be easily found in the clearnet, and comes with easy-to-follow instructions. No wonder, then, that creators claim they already have over 5000 clients. Thanks to the combination of advanced anti-evasion tricks and ease of use, we expect its popularity to continue to grow.
The contribution made by malware loaders, often referred to as “crypters,” is of great significance in the propagation of Remote Administration Tools (RATs) and data-stealing malwares that target individual user information. The pilfered Personal Identifiable Information (PII) sourced from compromised endpoints is predominantly gathered and directed towards various underground data marketplaces for sale. This phenomenon has a cascading impact on enterprises, as critical authentication-related data is leaked from users’ personal devices, consequently granting unauthorized access to corporate networks.
GuLoader is extensively utilized within large-scale malware campaigns to infiltrate users’ systems with prevalent data-stealing malwares like Raccoon, Vidar, and Redline. Additionally, these campaign activities are also responsible for disseminating commodity RATs like Remcos.
GuLoader Downloaded: A Look at the Latest Iteration
GuLoader stands out as a prominent downloader founded on shellcode that has been used in many attacks. We delve into its delivery methods and impact.cyberint.com
In March 2024, eSentire's Threat Response Unit (TRU) discovered multiple instances of D3F@ck Loader infections being propagated via Google Ads. This new loader, which debuted on hacking forums in January 2024 (Figure 1), can allegedly bypass several key security features such as Google Chrome, Edge, Windows Defender alerts, and SmartScreen.
The initial pricing was $70 per day and $490 for a week of access. TRU has observed the loader dropping Raccoon Stealer and Danabot for two separate infection cases.
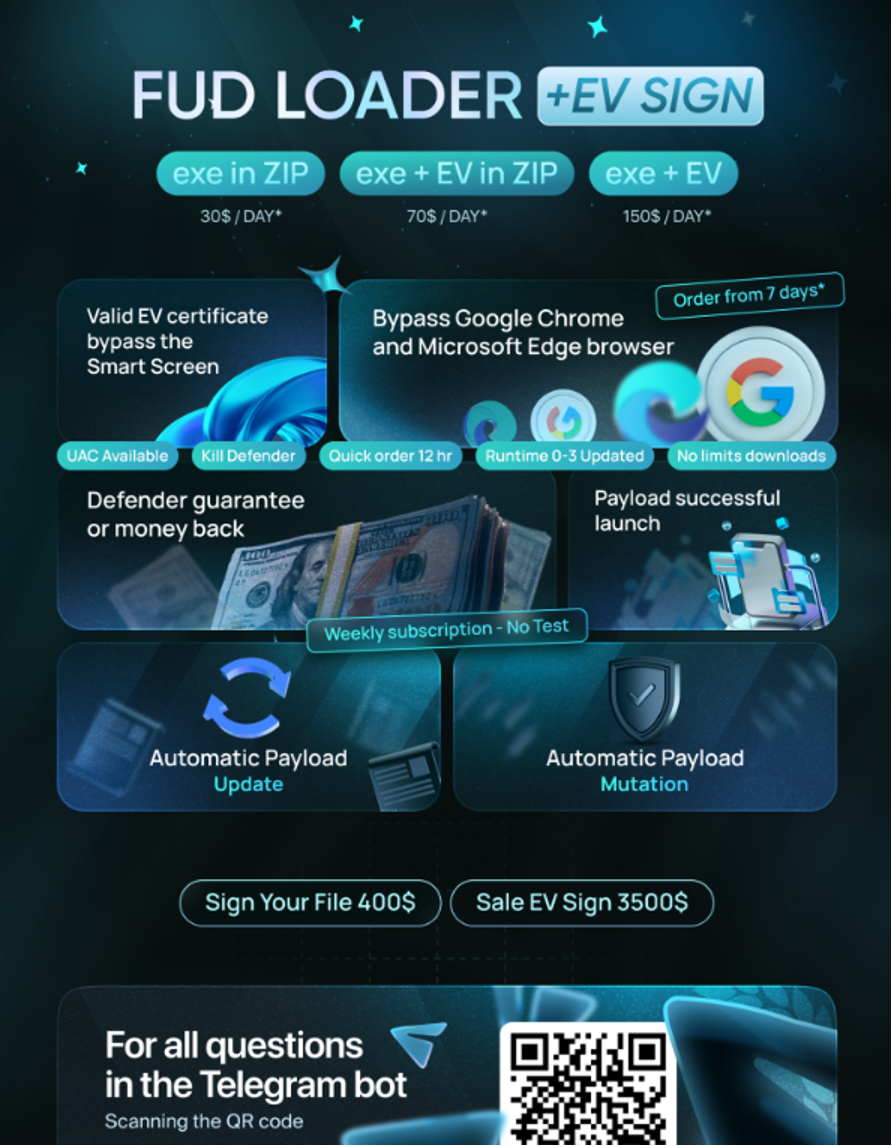

D3F@ck Loader, the New MaaS Loader
Learn more about the D3F@ck Loader malware and get security recommendations from our Threat Response Unit (TRU) to protect your business from this cyber…www.esentire.com
The last example is uncommon. Most Loaders are digitally signed with fake certificates. Malware with an EV certificate is rare.
