- Aug 23, 2012
- 293
- Content source
- https://twitter.com/apivoid/status/1594365925876125696
We've just found a fake MSI Afterburner website promoted via Google Ads (first result on first page) when you search "msi afterburner" that leads to malware infostealer:
The "Download Afterburner" button points to a Google Drive URL that directly downloads the "MSI Afterburner.zip" file, that contains the malicious "MSI Afterburner.exe" file.
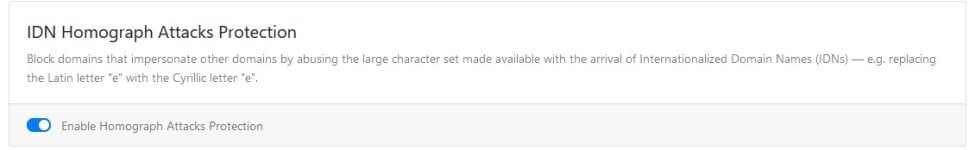
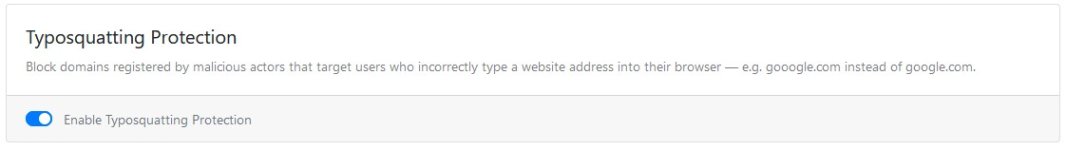
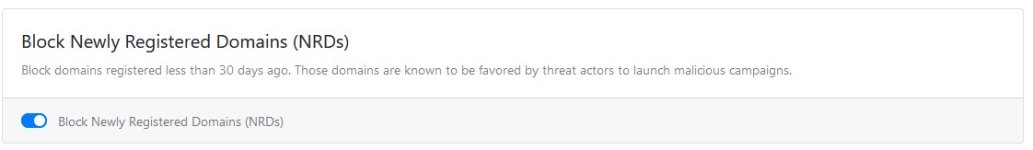
Pay always attention from where you download the software and always check the website domain name that matches exactly the official website.
I thought it would be useful to share it here too.
The "Download Afterburner" button points to a Google Drive URL that directly downloads the "MSI Afterburner.zip" file, that contains the malicious "MSI Afterburner.exe" file.
Pay always attention from where you download the software and always check the website domain name that matches exactly the official website.
I thought it would be useful to share it here too.