- Dec 15, 2023
- 35
I know this might be newbie question but how do I know or judge whether the file is safe or not?
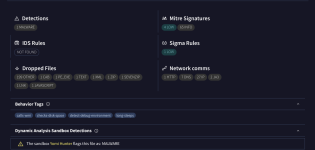
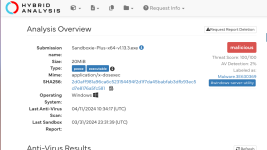
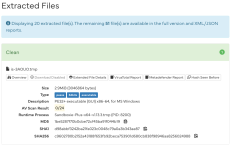
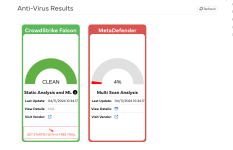
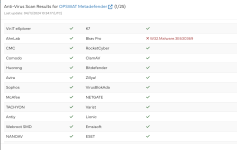
Recently I uploaded Sandboxie-Plus 1.13.3 and PeaZip 9.7.1 setup installer to Virustotal, though both came out 0 detection but under "community" tab some sandbox verdict indicate "likely malicious". And also for PeaZip 9.7.1, under "Relations" or "behavior" had some past detection. Because of that I'm confused about how to judge a file to be safe or not.
verdict indicate "likely malicious". And also for PeaZip 9.7.1, under "Relations" or "behavior" had some past detection. Because of that I'm confused about how to judge a file to be safe or not.
Better be safe than sorry since I don't know these issue had been solved or not Security News - GitHub besieged by millions of malicious repositories in ongoing attack
Furthermore, these can happen to other excutable files whether its downloaded from github or offical website. Can anyone give some advise?
Recently I uploaded Sandboxie-Plus 1.13.3 and PeaZip 9.7.1 setup installer to Virustotal, though both came out 0 detection but under "community" tab some sandbox
Better be safe than sorry since I don't know these issue had been solved or not Security News - GitHub besieged by millions of malicious repositories in ongoing attack
Furthermore, these can happen to other excutable files whether its downloaded from github or offical website. Can anyone give some advise?