- Nov 1, 2018
- 47
Thanks for the link.
This really sucks.And LastPass has long been criticized for storing its vault data in a hybrid format where items like passwords are encrypted but other information, like URLs, are not. In this situation, the plaintext URLs in a vault could give attackers an idea of what’s inside and help them to prioritize which vaults to work on cracking first.
That’s bad. It’s not an epic disaster, though.While no customer data was accessed during the August 2022 incident, some source code and technical information were stolen from our development environment and used to target another employee, obtaining credentials and keys which were used to access and decrypt some storage volumes within the cloud-based storage service.
[…]
To date, we have determined that once the cloud storage access key and dual storage container decryption keys were obtained, the threat actor copied information from backup that contained basic customer account information and related metadata including company names, end-user names, billing addresses, email addresses, telephone numbers, and the IP addresses from which customers were accessing the LastPass service.
The threat actor was also able to copy a backup of customer vault data from the encrypted storage container which is stored in a proprietary binary format that contains both unencrypted data, such as website URLs, as well as fully-encrypted sensitive fields such as website usernames and passwords, secure notes, and form-filled data.
So, according to the company, if you chose a strong master password—here’s my advice on how to do it—your passwords are safe. That is, you are secure as long as your password is resilient to a brute-force attack. (That they lost customer data is another story….)These encrypted fields remain secured with 256-bit AES encryption and can only be decrypted with a unique encryption key derived from each user’s master password using our Zero Knowledge architecture. As a reminder, the master password is never known to LastPass and is not stored or maintained by LastPass.
If that’s true, it means that LastPass has some backdoor—possibly unintentional—into the password databases that the hackers are accessing. (Or that @Cryptopathic’s “16 character password using all character types” is something like “P@ssw0rdP@ssw0rd.”)I think the situation at @LastPass may be worse than they are letting on. On Sunday the 18th, four of my wallets were compromised. The losses are not significant. Their seeds were kept, encrypted, in my lastpass vault, behind a 16 character password using all character types.
Previously, we had selected LastPass as our "best paid password manager." However, because of the severity of these incidents, we've decided (as of late December 2022) to temporarily remove LastPass from our list of recommendations, pending a re-review of the service in early 2023. Potential customers and anyone who's uncomfortable with LastPass's continuing security challenges should take a close look at the alternatives presented elsewhere in this story.
I missed this post from Dec 28th but I think it is still worth highlighting here more detail about the failings of Lastpass -
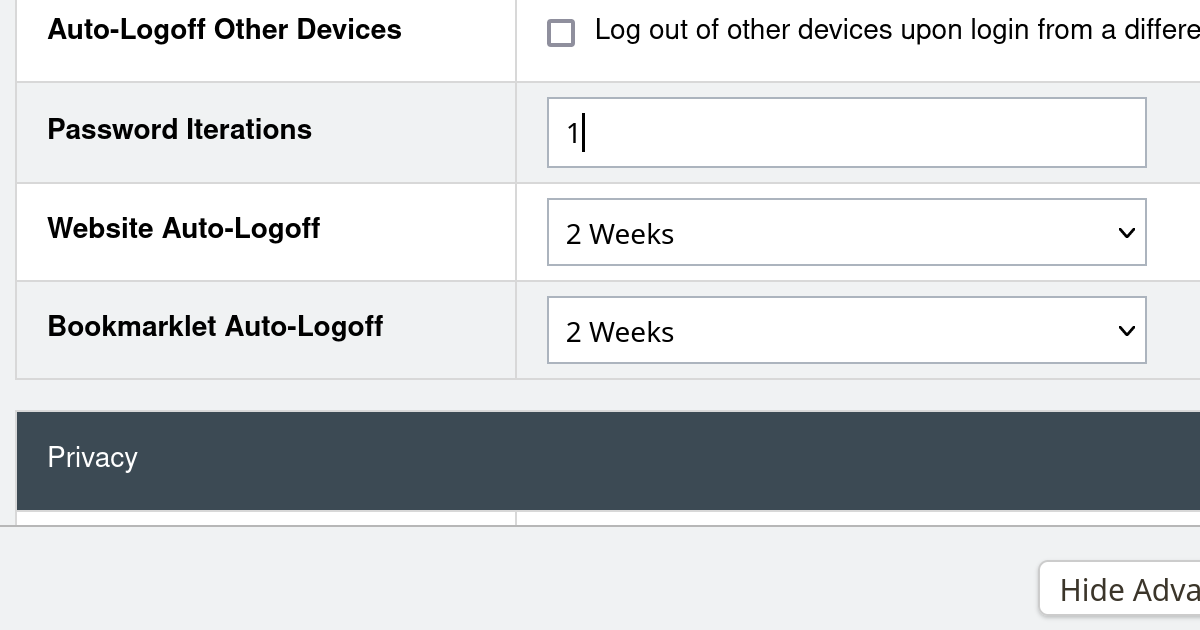
"LastPass has been breached, data has been stolen. I already pointed out that their official statement is misleading. I also explained that decrypting passwords in the stolen data is possible which doesn’t mean however that everybody is at risk now. For assessing whether you are at risk, a fairly hidden setting turned out critical: password iterations.
LastPass provides an instruction to check this setting. One would expect it to be 100,100 (the LastPass default) for almost everyone. But plenty of people report having 5,000 configured there, some 500 and occasionally it’s even 1 (in words: one) iteration.
Let’s say this up front: this isn’t the account holders’ fault. It rather is a massive failure by LastPass. They have been warned, yet they failed to act. And even now they are failing to warn the users who they know are at risk...."

LastPass breach: The significance of these password iterations
The Password Iterations setting is essential to keep users’ data secure. Yet LastPass failed to keep it up-to-date for many accounts.palant.info

Those two sure know how to keep talking!You guys may be interested in this 2 hour and 3 minute long Security Now podcast with Steve Gibson and Leo Laporte.
Leaving LastPass - How LastPass failed, Steve's next password manager, how to protect yourself
The notes: https://www.grc.com/sn/SN-903-Notes.pdf
You see, I'm not simply recommending that users bail on LastPass because of this latest breach. I'm recommending you run as far way as possible from LastPass due to its long history of incompetence, apathy, and negligence. It's abundantly clear that they do not care about their own security, and much less about your security.
Is the cloud the problem? No. The vast majority of issues LastPass has had have nothing to do with the fact that it is a cloud-based solution. Further, consider the fact that the threat model for a cloud-based password management solution should *start* with the vault being compromised. In fact, if password management is done correctly, I should be able to host my vault anywhere, even openly downloadable (open S3 bucket, unauthenticated HTTPS, etc.) without concern. I wouldn't do that, of course, but the point is the vault should be just that -- a vault, not a lockbox.
1Password saves the master password inside the vault, which can be deleted should the user wishes.or even opt in to save it and have it entered for them ….then there is no point of using a password manager no matter how secure it is.
reddit user:
I'm not sure why you're worried?
The 1Password entry is created inside a locked vault. It's like keeping a spare set of keys inside your house; it's not a security issue.
Leaving a password manager unlocked in public is a user behaviour issue that no password manager can guard against. If you leave your password manager unlocked and unattended in public, anyone could just use the export feature to export all your passwords. Or create themselves a copy of the emergency kit and steal it. Or simply use your password manager to log into your accounts and reset all your passwords and lock you out of your own accounts.
In other words, a password manager isn't designed to protect you if you leave it unlocked where anyone could access its contents. So don't do that.
1Password Security Team:
This is a great answer.
Keep in mind that using that Starter Kit item to fill your data into 1Password on the web actually has a security benefit: avoiding phishing attempts. 1Password will only fill your credentials into a genuine copy of 1Password on the web, at the exact correct URL. Humans may not be as good at detecting if they’ve come across a fake or imitation. In this sense, keeping your credentials within 1Password for use is safer than not doing so.
And the flow of bad news has no end - What’s at stake for 33M compromised LastPass users?
Instead of running the math to determine how complex your password would be to crack with modern equipment, it’s best to go ahead and do some credential hygiene.”
Calling yourself stupid for you trusted a password manager is not right. Lastpass is one of the best PMs functionality wise. I feel sorry for them because it seems their end is inevitable now.@Divine_Barakah I began changing passwords to my most critical websites as soon as I read of the breach on the morning of Dec 22/23 and fully migrated to 1PW and Bitwarden. After taking a backup, my LP account and that of my family members were deleted an active family subscription notwithstanding.
I've been a Bitwarden subscriber since 2017 all thanks to the good folks here at MalwareTips. Happened 2-3 months after I signed up at this forum in Aug '17 (subbed to BW in Nov '17 IIRC) . And of course I thought I'd give a new startup based offering an open source PM a chance. I am so glad I did.
I've used and/or subscribed to nearly every PM out there starting with the granndaddy of 'em all Roboform which was a good app but and LP quickly became my favourite. Yes, stupid of me not to see the writing on the wall years ago when the hack attacks began.
Anyway, I've changed passwords to nearly all the several hundred sites I had in LP, disabled renabled 2FA on the critical ones to generate new tokens, regenerated new backup recovery codes. Ditto for my family members' accounts.
It has been a very painful and tedious job over the past 2+ weeks and still continues for minor sites. Unfortunately there's nothing I can do about the safe/secure notes but cross my fingers & hope they're not decrypted as they contain a lot of personal and other data. I am so darned angry with LP!!
Calling yourself stupid for you trusted a password manager is not right. Lastpass is one of the best PMs functionality wise. I feel sorry for them because it seems their end is inevitable now.
So glad that you migrated to BW. Regarding your safe memos, I am going to say one thing. Please do not put all your eggs in one basket. One more thing, it is wise to not sync your private data to the cloud to avoid situations such as lastpass’s. I do know it is a little inconvenient, but is it worth the risk?
I do not want to spread paranoia, but believe me BW can suffer the same as LP. Unfortunately, self-hosting Bw is not an easy task. Thus, it is up to you if you want to keep your data synced to the cloud or migrate to another offline PM.
Cryptomator a nice piece of software. I can’t imagine my life without it.Well, I am quite clued into the IT industry having worked in it for decades on both desktop & enterprise applications so I blame myself for not having seen the writing on the wall.
You're right about the 'eggs in one basket' bit - all my new recovery codes are now downloaded to my PC, stored on a NAS and USB hard drive and copies encrypted using good ol' Ccryptomator and stored on multiple cloud drives. Never again will I begin using my PM to store personal data.
And you're absolutely 100% right, what happened to LP could happen to any cloud based PM service so we have to make our choices. Though I have Sticky Password and Enpass + use Keepass as an archiver, BW, 1PW and Dashlane have that ease of use that makes them so enjoyable to use especially for non geeks like my wife and other family members. There would be howls of protest if were ever to push Keepass or similar as a solution. LOL!



