- Aug 30, 2012
- 6,598

New Configuration of Citadel Trojan Discovered by IBM Trusteer Researchers
In these days of endless breaches, securing user access by enforcing unique, complex passwords and strong authentication is imperative. The onslaught of data breaches in the past year alone, with the majority of the breaches involving compromised credentials, forced users to constantly change their passwords. With many users still trying to use the same passwords over and over, and others struggling to remember their newly created complex ones, a password manager becomes a smart and responsible solution for users – and attackers have taken notice. Always looking for ways to log in as a legitimate user, cybercriminals try to guess, steal or brute force passwords. They try to bypass authentication mechanisms by tampering with user requests and tricking the application into thinking that they’re authenticated.
Secure access plays a critical role in data breach prevention – whether it’s access to personal online services for banking, social networks, e-commerce sites, or corporate applications like webmail, software-as-a-service (SAAS) and platform-as-a-service (PASS) services.
Various solutions have been designed to simplify and streamline secure access. Password managers, for example, relieve the user of the need to remember all the unique and complex passwords that he or she uses to access both personal and work-related applications. Instead, the user need only remember one complex master password, which is much easier. When you provide the master password, these solutions will enable secure access to your applications and services.
Many applications require additional authentication of the user or devices before access is granted. In addition to passwords, which are “something you know,” these authentication processes may require “something you have,” such as a physical device or certificate. Common authentication methods require the use of smart cards, software certificates or digital signatures. The combination of a password you know and an authentication “proof” that you have is powerful. The strength of these solutions is based on the confidence that it is hard to compromise or circumvent something you know or something you have — or moreso, the combination of the two.
However, what happens when cybercriminals use sophisticated malware to steal master passwords and compromise authentication solutions?
New Citadel Trojan Configuration
The Citadel Trojan is not new. It is a massively distributed malware that has already compromised millions of computers worldwide. Once Citadel installs on a machine, it opens communication channels with a command-and-control (C&C) server and registers with it. The malware then receives a configuration file that tells it how it should operate, which targets what to look for, what type of information to capture, which functions to enable and even provides information about alternative C&Cs that allow the attackers to take down an exposed C&C and still operate the malware from a new C&C. As long as the malware is communicating with the C&C, the configuration file can be updated with information about new targets, activities and C&C destinations.
IBM Trusteer research found that an average of 1 in 500 machines worldwide is infected with massively distributed APT malware at any point in time. Massively distributed malware has been discovered by IBM Trusteer’s Service team in practically every customer environment in which they’ve worked. Since millions of machines are already infected with Citadel, it is easy for attackers to take advantage of this malware in new cyberschemes. All attackers need to do is provide a new configuration file to the millions of existing instances and wait for infected machines to access the targets.
It is important to note that Citadel is highly evasive and can bypass most threat detection security systems. It can stay idle on a user’s machine for weeks, months and even years until it is triggered by a user action. This means that many users and organizations do not know that their machines are already infected, and the existing infection can be quickly turned against them.
Compromising Master Passwords and Authentication Solutions
Recently, IBM Trusteer researchers found a new configuration of Citadel that is being used to compromise password management and authentication solutions. It instructs the malware to start keylogging (capturing user keystrokes) when some processes are running.
The relevant part of the configuration is shown below (in IBM Trusteer’s proprietary format):
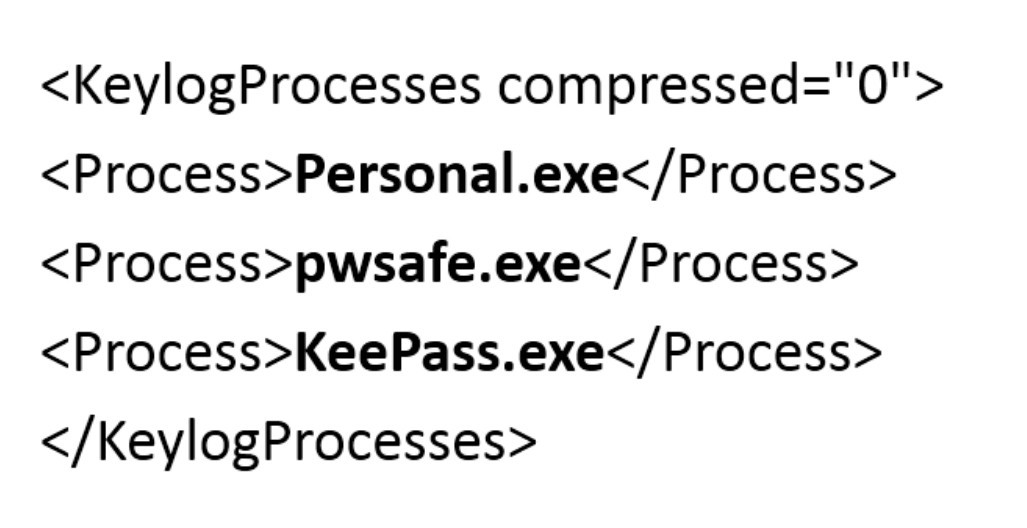
The following are targeted processes:
- Personal.exe: A process that belongs to “neXus Personal Security Client,” an authentication solution that enables users to conduct secure financial transactions, e-commerce and other security-dependent services directly from the desktop. It offers a cryptographic middleware (interlinking piece of software) that enables secure login and the use of common applications. It is used by enterprises as well as online service providers.
- PWsafe.exe: A process that belongs to “Password Safe,” a free, open-source password management solution that allows you to create an encrypted user/password list. According to an article from PCWorld, the original version of its password database was designed by security expert Bruce Schneier, and the current version has been tested and code-inspected by thousands of people — not trivial for a security solution. By using a keylogger, the malware captures the “master password,” which enables the cyberattacker to unlock and access the entire list.
- KeePass.exe: A process that belongs to “KeePass,” another free, open-source, secure password manager. It lets you keep all of your username/password pairs in a securely encrypted database, protected behind a single master password. One of the positive features included with KeePass is a random password generator, so you don’t have to create random passwords on your own. Again, by using a keylogger, the malware can capture the “master password,” which lets cybercriminals unlock and access the entire user/password database.
IBM Trusteer found this new Citadel configuration file on a user machine protected by IBM Trusteer. This machine can be located anywhere in the world and used by any type of user, such as a consumer using Web services, an enterprise employee using corporate systems, a contractor that works with other organizations — we cannot know. The machine was already infected by Citadel when IBM Trusteer Apex was installed on it. Therefore, it is unknown exactly how it became infected. IBM Trusteer Apex identified the infection and mitigated it, sending a sample to the research lab for further analysis.
An analysis of the configuration file shows that the attackers were using a legitimate Web server as the C&C. However, by the time the IBM Trusteer research lab received the configuration file, the C&C files were already removed from the server, so researchers were not able to identify who is behind this configuration.
Because the configuration file instructs the malware to capture keystrokes related to widely used password management and authentication solutions, we can’t know who, exactly, is the target of the attack. It might be an opportunistic attack, where the attackers are trying to see which type of information they can expose through this configuration, or a more targeted attack in which the attackers know that the target is using these specific solutions.
Conclusion
Someday, we might be able to move away from passwords. IBM predicted in 2011 that by 2016, we will not use passwords to access sensitive resources. Instead, our unique biological identity and biometric data such as facial definitions, iris scans, voice files and DNA could be a vital part of keeping personal information safe, replacing the current user ID and password system. However, until then, we must secure our passwords and prevent fraud and exposure from adversaries and cybercriminals.
Password management and authentication programs are important solutions that help secure access to applications and Web services. However, it is important to understand that these solutions can be compromised by malware. If an adversary is able to steal the master password and gain access to the user/password database of a password management solution or compromise an authentication technology, the attacker can gain unfettered access to sensitive systems and information.
Therefore, it is important to ensure access to sensitive systems — whether corporate applications or online services for personal use — is done from malware-free machines. This requires advanced malware protection that is specifically designed to handle highly sophisticated and evasive malware such as Citadel and other massively distributed advanced persistent threat malwares.
Disclosure Note: IBM has made an attempt to contact the vendors in question to allow them to proactively notify their customer base and to provide any product-specific recommendations they may have to enable users to better protect themselves.
