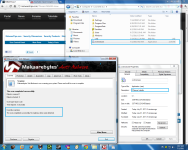
Interesting way of protecting a system.
svchost.exe. is a windows related file so no one will name a file like that unless they want to exploit a system.The important thing that we should note is that this isn't the main way for MBAM to flag a threat.To prove my point I've downloaded the Ccleaner installer and place it in %WINDIR% (C:/) ... I have also renamed Ccleaner to svchost.exe , so now if MBAM was to flag a threat only by looking at his name and path we should have a detection.
[attachment=534]
Code:
Malwarebytes' Anti-Malware 1.51.0.600
www.malwarebytes.org
Database version: 6991
Windows 6.1.7601 Service Pack 1
Internet Explorer 9.0.8112.16421
7/1/2011 9:07:05 AM
mbam-log-2011-07-01 (09-07-05).txt
Scan type: Quick scan
Objects scanned: 1
Time elapsed: 3 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 0
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
(No malicious items detected)
Cyber criminals aren't playing according to the rules so all the vendors should use all the techniques available in order to better defend a system.I'm sure that other vendors use this kind of technique in order to prevent/detect a threat and as long as it's "another way" of detecting malware everything is ok.
The main problem when using this type of detection could be a FP..but I have been using MBAM for 2 years now and I have never seen a FP from MBAM.