- Sep 17, 2013
- 1,492
Private Address Ranges
A NAT router typically acts as an intermediary between devices on private address ranges and the rest of the Internet. These private addresses are not routed anywhere on the Internet:
10.0.0.0 - 10.255.255.255 (10.0.0.0/8)
172.16.0.0 - 172.31.255.255 (172.16.0.0/12)
192.168.0.0 - 192.168.255.255 (192.168.0.0/16)
Any site is permitted to use one or more of these address ranges for their own purposes. However, without NAT, devices on these private networks would not be able to access or be accessed by devices on the Internet.
How Can I Tell If I'm Using NAT?
If you can reach sites on the Internet, but you have an address on one of the private address ranges, you're behind a NAT router.
What is NAT?
There are several types of NAT described in the NAT RFC. The most common use is to "hide" an entire network of devices with private addresses behind a single routable address. A NAT router, either a computer or a dedicated hardware "appliance" has connections both to the Internet and to a network with a private address range. As mentioned previously, devices on private networks cannot by themselves access information on the Internet. A NAT acts as an intermediary as follows:
NATs as Firewalls
What would happen if a device on the Internet tried to contact a device on the private network behind a NAT router? It can't contact devices on the private net directly, because no Internet router will forward packets with private network addresses. It could try to send packets to the NAT router, but the NAT router has no way of knowing which device on the private network should receive the information, so the packets are simply dropped. This basically gives NAT routers a firewall functionality with minimal configuration on the user's part.
Because of the relative scarcity of public IPv4 addresses, NATs are being deployed to reuse the IPv4
private address space. In some configurations, there might be multiple levels of NATs between the
client computer and the Internet. Although NATs do allow more clients to connect to the Internet,
they also act as traffic bottlenecks and barriers to some types of communications.
Let’s examine the operation of a NAT to illustrate why network address translation is a nonscalable,
stopgap solution that impairs end-to-end communication.
For example, say that a small business uses the 192.168.0.0/24 private IPv4 address prefix for its intranet and has been assigned the public IPv4 address of 131.107.47.119 by its Internet service provider (ISP). The NAT deployed at the edge of this network maps all private addresses on 192.168.0.0/24 to the public address of 131.107.47.119. The NAT uses dynamically chosen TCP and UDP ports to map internal (intranet) data streams to external (Internet) data streams.
Figure 1-1 shows this example
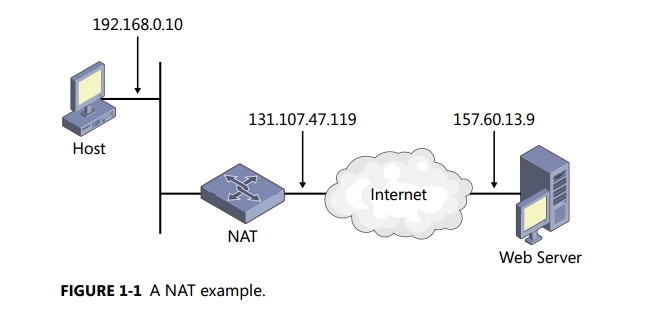
If a private host assigned the private IPv4 address 192.168.0.10 uses a web browser to connect to
the web server at 157.60.13.9, the private host creates an IPv4 packet with the following:
This IPv4 packet is then forwarded to the NAT, which typically translates the source address and source TCP port of the outgoing packet to the following:
The NAT keeps the mapping of {192.168.0.10, TCP 1025} to {131.107.47.119, TCP 5000} in a local
translation table for future reference. The translated IPv4 packet is sent over the Internet. The response is sent back by the web server and received by the NAT. When received, the packet contains the following:
The NAT checks its translation table, locates the entry that was created when the initial packet was
sent, translates the destination address and destination TCP port, and forwards the packet to the host
at 192.168.0.10. The forwarded packet contains the following
For outgoing packets from the NAT, the source IPv4 address (a private address) is mapped to the
ISP-assigned address (a public address), and the source TCP/UDP port numbers are mapped to different TCP/UDP port numbers. For incoming packets to the NAT, the destination IPv4 address (a public
address) is mapped to the original intranet address (a private address), and the destination TCP/UDP
port numbers are mapped back to their original TCP/UDP port numbers.
Normal network address translation relies on the following:
Address and port translation lowers the forwarding performance of the NAT because of the additional operations that must be performed on each packet. As a result, NATs are typically not deployed
in large-scale environments. However, recent development of standards such as carrier-grade NATs
(CGNs) promise to scale NAT to enterprises and large ISPs.
To make modifications to the IPv4 packet beyond address or port translation requires additional
processing and software components on the NAT called NAT editors. HyperText Transfer Protocol
(HTTP) traffic on the World Wide Web does not require a NAT editor because all HTTP traffic requires
only address and TCP port translation. However, NAT editors are required in the following situations:
Most traffic can traverse a NAT because either the packets require only address or port translation
or a NAT editor is present to modify the payload appropriately. However, some traffic cannot traverse
a NAT. If the data requiring translation is in an encrypted part of the packet, translation is not possible. For IPsec-protected packets, address and port translation can invalidate the packet’s integrity.
IPsec NAT-Traversal (NAT-T) is a recent Internet standard that allows some types of IPsec-protected
packets to be translated by a NAT.
An additional problem with NATs is their effect on peer-to-peer applications. In the peer-to-peer
communication model, peers can act as either the client or the server and initiate communications to
each other. If a peer is behind a NAT, two addresses are associated with it, one that is known to the
peer behind the NAT (the private address) and one that is known in front of the NAT (the public address).
Let’s examine a simple configuration in which NATs can cause problems for peer-to-peer applications. Figure 1-2 shows an intranet with a NAT at its edge.
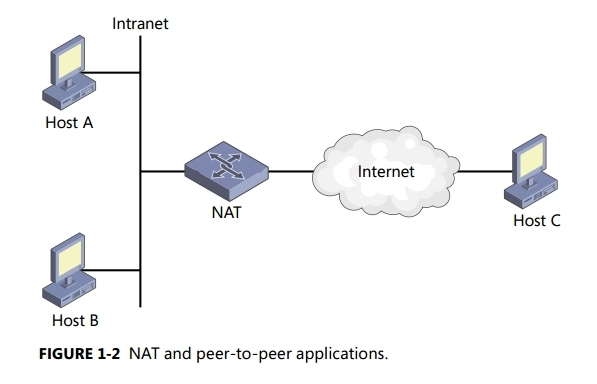
For a peer-to-peer application running on all hosts, Host A can initiate a session with Host B
(directly reachable on its link) and with Host C. However, Host A cannot inform Host C of the public
address and port number of Host B because Host A does not know it. Also, Host C cannot initiate
a session with either Host A or Host B without an existing translation table entry to translate the
inbound connection-request packets to Host A’s private address and port. Even with the table entry,
Host C might not be able to initiate a session with both Host A and Host B because both hosts are
known by the same public IPv4 address.
To make matters worse, it is a more common situation to have each Internet peer behind a NAT.
To solve these problems, the peer-to-peer or multiple-party applications must be modified to be
NAT-aware or use a NAT traversal technology, resulting in additional complexity. Also, some NAT aware applications use an echo server to automatically discover their public address and port number,
which adds costs for independent software vendors (ISVs) to deploy and maintain echo servers on the
Internet.
NATs are a makeshift measure to extend the life of the IPv4 public address space, and they are not
a solution to the IPv4 public address space problem. NATs work best for reusing the private address
space for client computers and client/server-based communication when the client behind the NAT
initiates the communication. Most server computers still need unambiguous public addresses.
Although a server can be placed behind a NAT, the NAT must be configured manually with a static
translation table entry to translate the inbound packets to the server’s private address and port. In
peer-to-peer communications, each end acts as both client and server and, therefore, peers separated
by NATs might not operate correctly and must be modified for NAT awareness.
Advantages of NAT
NAT is one of those technologies that has a long list of both advantages and disadvantages. This means it can be extremely useful in a variety of scenarios, but also problematic in others. The main advantages are:
Disadvantages of NAT
Further reading
http://www.tcpipguide.com/free/t_IPNetworkAddressTranslationNATProtocol.htm
en.wikipedia.org/wiki/Network_address_translation
http://www.vicomsoft.com/learning-center/network-address-translation/
http://docs.oracle.com/cd/E19062-01/sun.mgmt.ctr36/819-5418/nat-1/index.html
http://linux-ip.net/html/nat-overview.html
A NAT router typically acts as an intermediary between devices on private address ranges and the rest of the Internet. These private addresses are not routed anywhere on the Internet:
10.0.0.0 - 10.255.255.255 (10.0.0.0/8)
172.16.0.0 - 172.31.255.255 (172.16.0.0/12)
192.168.0.0 - 192.168.255.255 (192.168.0.0/16)
Any site is permitted to use one or more of these address ranges for their own purposes. However, without NAT, devices on these private networks would not be able to access or be accessed by devices on the Internet.
How Can I Tell If I'm Using NAT?
If you can reach sites on the Internet, but you have an address on one of the private address ranges, you're behind a NAT router.
What is NAT?
There are several types of NAT described in the NAT RFC. The most common use is to "hide" an entire network of devices with private addresses behind a single routable address. A NAT router, either a computer or a dedicated hardware "appliance" has connections both to the Internet and to a network with a private address range. As mentioned previously, devices on private networks cannot by themselves access information on the Internet. A NAT acts as an intermediary as follows:
- A device on the private network makes a request for information on the Internet.
- Packets travel to the NAT router, which rewrites the packet header so that it appears that the packets are coming from the router's public address.
- The NAT router maintains a session table, so that replies can be forwarded back to the originator on the private network.
NATs as Firewalls
What would happen if a device on the Internet tried to contact a device on the private network behind a NAT router? It can't contact devices on the private net directly, because no Internet router will forward packets with private network addresses. It could try to send packets to the NAT router, but the NAT router has no way of knowing which device on the private network should receive the information, so the packets are simply dropped. This basically gives NAT routers a firewall functionality with minimal configuration on the user's part.
Because of the relative scarcity of public IPv4 addresses, NATs are being deployed to reuse the IPv4
private address space. In some configurations, there might be multiple levels of NATs between the
client computer and the Internet. Although NATs do allow more clients to connect to the Internet,
they also act as traffic bottlenecks and barriers to some types of communications.
Let’s examine the operation of a NAT to illustrate why network address translation is a nonscalable,
stopgap solution that impairs end-to-end communication.
For example, say that a small business uses the 192.168.0.0/24 private IPv4 address prefix for its intranet and has been assigned the public IPv4 address of 131.107.47.119 by its Internet service provider (ISP). The NAT deployed at the edge of this network maps all private addresses on 192.168.0.0/24 to the public address of 131.107.47.119. The NAT uses dynamically chosen TCP and UDP ports to map internal (intranet) data streams to external (Internet) data streams.
Figure 1-1 shows this example
If a private host assigned the private IPv4 address 192.168.0.10 uses a web browser to connect to
the web server at 157.60.13.9, the private host creates an IPv4 packet with the following:
- Destination address: 157.60.13.9
- Source address: 192.168.0.10
- Destination TCP port: 80
- Source TCP port: 1025
This IPv4 packet is then forwarded to the NAT, which typically translates the source address and source TCP port of the outgoing packet to the following:
- Destination address: 157.60.13.9
- Source address: 131.107.47.119
- Destination TCP port: 80
- Source TCP port: 5000
The NAT keeps the mapping of {192.168.0.10, TCP 1025} to {131.107.47.119, TCP 5000} in a local
translation table for future reference. The translated IPv4 packet is sent over the Internet. The response is sent back by the web server and received by the NAT. When received, the packet contains the following:
- Destination address: 131.107.47.119
- Source address: 157.60.13.9
- Destination TCP port: 5000
- Source TCP port: 80
The NAT checks its translation table, locates the entry that was created when the initial packet was
sent, translates the destination address and destination TCP port, and forwards the packet to the host
at 192.168.0.10. The forwarded packet contains the following
- Destination address: 192.168.0.10
- Source address: 157.60.13.9
- Destination TCP port: 1025
- Source TCP port: 80
For outgoing packets from the NAT, the source IPv4 address (a private address) is mapped to the
ISP-assigned address (a public address), and the source TCP/UDP port numbers are mapped to different TCP/UDP port numbers. For incoming packets to the NAT, the destination IPv4 address (a public
address) is mapped to the original intranet address (a private address), and the destination TCP/UDP
port numbers are mapped back to their original TCP/UDP port numbers.
Normal network address translation relies on the following:
- Address translation Translation of the IPv4 addresses in the IPv4 header
- Port translation Translation of the TCP port numbers in the TCP header or of the UDP port numbers in the UDP header
Address and port translation lowers the forwarding performance of the NAT because of the additional operations that must be performed on each packet. As a result, NATs are typically not deployed
in large-scale environments. However, recent development of standards such as carrier-grade NATs
(CGNs) promise to scale NAT to enterprises and large ISPs.
To make modifications to the IPv4 packet beyond address or port translation requires additional
processing and software components on the NAT called NAT editors. HyperText Transfer Protocol
(HTTP) traffic on the World Wide Web does not require a NAT editor because all HTTP traffic requires
only address and TCP port translation. However, NAT editors are required in the following situations:
- An IPv4 address, TCP port, or UDP port is stored elsewhere in the payload. For example, File Transfer Protocol (FTP) stores the dotted decimal representation of IPv4 addresses in the FTP header for the FTP PORT command. If the NAT does not properly translate the IPv4 address within the FTP header for the FTP PORT command and adjust the TCP sequence numbers in the data stream, connectivity and data transfer problems will occur.
- TCP or UDP is not used to identify the data stream. For example, Point-to-Point Tunneling Protocol (PPTP) tunneled data does not use a TCP or UDP header. Instead, PPTP uses a Generic Routing Encapsulation (GRE) header and the Call ID field of the GRE header to identify the data stream. If the NAT does not properly translate the Call ID field within the GRE header, connectivity problems will occur.
Most traffic can traverse a NAT because either the packets require only address or port translation
or a NAT editor is present to modify the payload appropriately. However, some traffic cannot traverse
a NAT. If the data requiring translation is in an encrypted part of the packet, translation is not possible. For IPsec-protected packets, address and port translation can invalidate the packet’s integrity.
IPsec NAT-Traversal (NAT-T) is a recent Internet standard that allows some types of IPsec-protected
packets to be translated by a NAT.
An additional problem with NATs is their effect on peer-to-peer applications. In the peer-to-peer
communication model, peers can act as either the client or the server and initiate communications to
each other. If a peer is behind a NAT, two addresses are associated with it, one that is known to the
peer behind the NAT (the private address) and one that is known in front of the NAT (the public address).
Let’s examine a simple configuration in which NATs can cause problems for peer-to-peer applications. Figure 1-2 shows an intranet with a NAT at its edge.
For a peer-to-peer application running on all hosts, Host A can initiate a session with Host B
(directly reachable on its link) and with Host C. However, Host A cannot inform Host C of the public
address and port number of Host B because Host A does not know it. Also, Host C cannot initiate
a session with either Host A or Host B without an existing translation table entry to translate the
inbound connection-request packets to Host A’s private address and port. Even with the table entry,
Host C might not be able to initiate a session with both Host A and Host B because both hosts are
known by the same public IPv4 address.
To make matters worse, it is a more common situation to have each Internet peer behind a NAT.
To solve these problems, the peer-to-peer or multiple-party applications must be modified to be
NAT-aware or use a NAT traversal technology, resulting in additional complexity. Also, some NAT aware applications use an echo server to automatically discover their public address and port number,
which adds costs for independent software vendors (ISVs) to deploy and maintain echo servers on the
Internet.
NATs are a makeshift measure to extend the life of the IPv4 public address space, and they are not
a solution to the IPv4 public address space problem. NATs work best for reusing the private address
space for client computers and client/server-based communication when the client behind the NAT
initiates the communication. Most server computers still need unambiguous public addresses.
Although a server can be placed behind a NAT, the NAT must be configured manually with a static
translation table entry to translate the inbound packets to the server’s private address and port. In
peer-to-peer communications, each end acts as both client and server and, therefore, peers separated
by NATs might not operate correctly and must be modified for NAT awareness.
Advantages of NAT
NAT is one of those technologies that has a long list of both advantages and disadvantages. This means it can be extremely useful in a variety of scenarios, but also problematic in others. The main advantages are:
- Public IP Address Sharing: A large number of hosts can share a small number of public IP addresses. This saves money and also conserves IP address space.
- Easier Expansion: Since local network devices are privately addressed and a public IP address isn't needed for each one, it is easy to add new clients to the local network.
- Greater Local Control: Administrators get all the benefits of control that come with a private network, but can still connect to the Internet.
- Greater Flexibility In ISP Service: Changing the organization's Internet Service Provider (ISP) is easier because only the public addresses change. It isn't necessary to renumber all the client machines on the network.
- Increased Security: The NAT translation represents a level of indirection. Thus, it automatically creates a type of firewall between the organization's network and the public Internet. It is more difficult for any client devices to be accessed directly by someone malicious because the clients don't have publicly-known IP addresses.
- (Mostly) Transparent: NAT implementation is mostly transparent, because the changes take place in one or perhaps a few routers. The dozens or hundreds of hosts themselves don't need to be changed.
Disadvantages of NAT
- Complexity: NAT represents one more complexity in setting up and managing the network. It also makes troubleshooting more confusing due to address substitutions.
- Problems Due to Lack of Public Addresses: Certain functions won't work properly due to lack of a “real” IP address in the client host machines.
- Compatibility Problems With Certain Applications: I said above that NAT was only mostly transparent. There are in fact compatibility issues with certain applications that arise because NAT “tinkers” with the IP header fields in datagrams but not in the application data. This means tools like FTP, which pass IP addresses and port numbers in commands, must be specially handled, and some applications may not work.
- Problems With Security Protocols: Protocols like IPSec are designed to detect modifications to headers and commonly balk at the changes that NAT makes, since they cannot differentiate those changes from malicious datagram “hacking”. It is still possible to combine NAT and IPSec, but this becomes more complicated.
- Poor Support for Client Access: The lack of a public IP address for each client is a double-edged sword; it protects against hackers trying to access a host but also makes it difficult for legitimate access to clients on the local network. “Peer-to-peer” applications are harder to set up, and something like an organizational web site (accessed from the Internet as a whole) usually needs to be set up without NAT.
- Performance Reduction: Each time a datagram transitions between the private network and the Internet, an address translation is required. In addition, other work must be done as well, such as recalculating header checksums. Each individual translation takes little effort but when you add it up, you are giving up some performance.
Further reading
http://www.tcpipguide.com/free/t_IPNetworkAddressTranslationNATProtocol.htm
en.wikipedia.org/wiki/Network_address_translation
http://www.vicomsoft.com/learning-center/network-address-translation/
http://docs.oracle.com/cd/E19062-01/sun.mgmt.ctr36/819-5418/nat-1/index.html
http://linux-ip.net/html/nat-overview.html
