- May 3, 2011
- 3,893
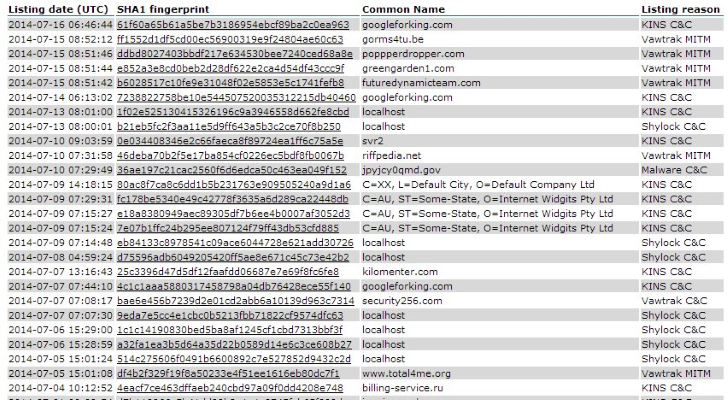
 - Blacklisted SSL certificates on abuse.ch
- Blacklisted SSL certificates on abuse.chA new project has been deployed, aiming at presenting a collection of SSL certificates employed by threat actors to secure communication between the infected machines and the servers under their control.
Cryptographic protocols have been implemented as a safe way for a computer user to navigate to certain web pages giving access to sensitive information, without third-parties to be able to intercept the messages.
However, cybercriminals also started to adopt this method for exchanging messages with compromised computers in a botnet. The reason behind this is to avoid being spotted by intrusion detection/prevention systems (IDS/IPS).
Security researchers at Abuse.ch from Switzerland, initiated a project (SSLBL) that publishes a SSL blacklist with the SHA1 cryptographic fingerprints of the SSL/TLS certificates employed in malicious activities, such as communication between command and control servers and the systems in a botnet.
“The goal of SSLBL is to provide a list of bad SHA1 fingerprints of SSL certificates that are associated with malware and botnet activities,” say the maintainers of the SSLBL in a blog post.
The idea of the project came when working with Suricata, an open-source IDS, IPS and Network Secure Monitoring (NSM) tool, which integrates a SSL/TLS module that can fingerprint the secure certificates.
The Swiss researcher is known for tracking high-profile banking Trojan families and botnets, and their portfolio includes malicious software, like as Zeus, SpyEye, Palevo and Feodo.
As such, starting SSLBL is a continuation of their fight against the threat actors attempting to steal financial information from computer users around the world.
At the moment, the list includes a number of 127 digital certificates associated with different malware campaigns. Some of them have been generated by the cybercriminals themselves, while others have been bought from trusted certificate authorities (CA).
“The goal of SSLBL is to provide a list of bad SHA1 fingerprints of SSL certificates that are associated with malware and botnet activities. Currently, SSLBL provides an IP based and a SHA1 fingerprint based blacklist in CSV and Suricata rule format,” says the researcher.
The list is useful for detecting command and control traffic relying on SSL and it contains important details, such as the MD5 hash of the malware binary, the destination address, and the SSL version used.
So far, the entries show the fingerprints for certificates used by KINS, Vawtrack and Shylock; however, the database is likely to grow and add more malware families, considering the general communication encryption trend used by cybercrooks.
Source