- Apr 24, 2013
- 1,200
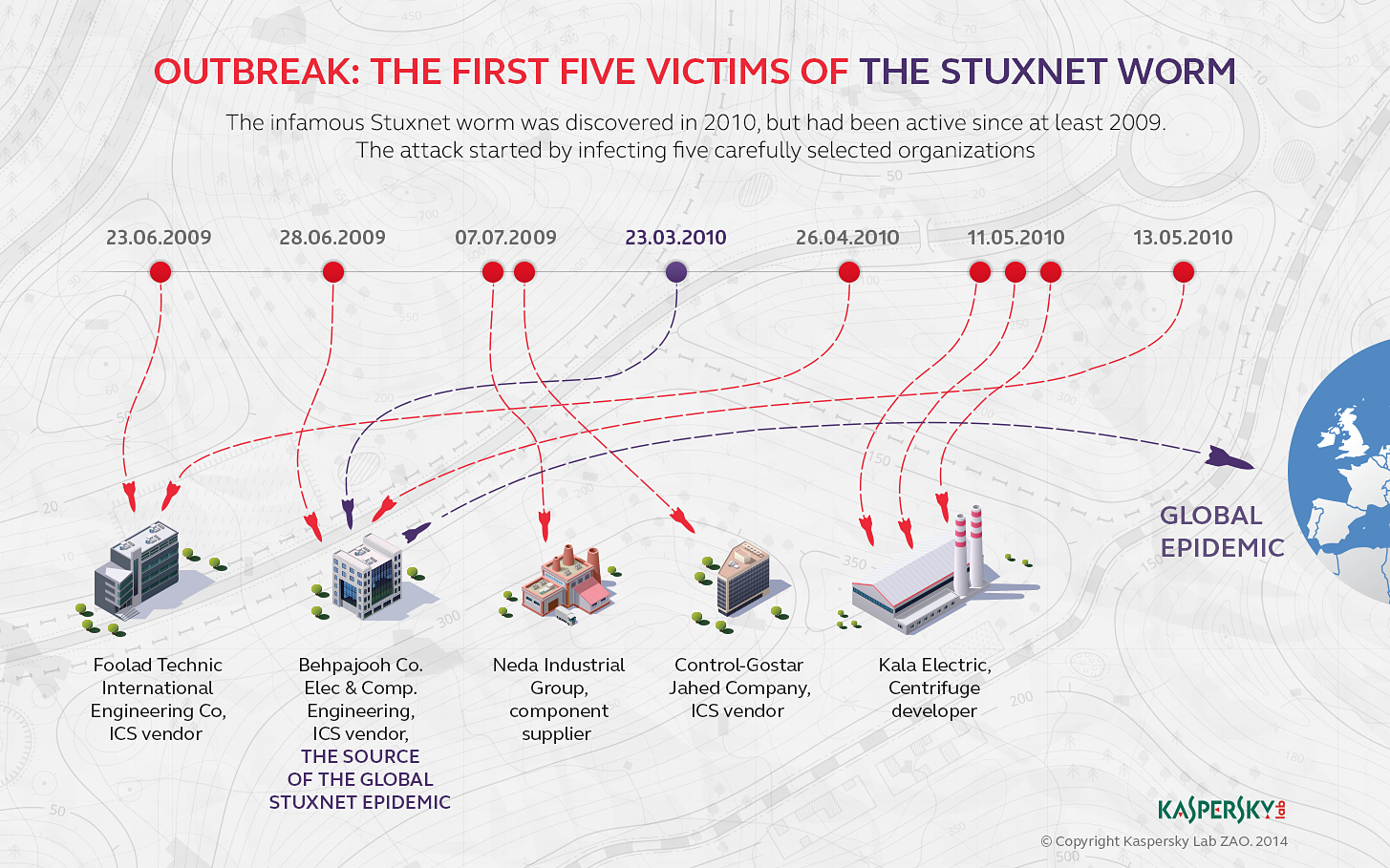
The Stuxnet computer worm that attacked Iran's nuclear development program was first seeded to a handful of carefully selected targets before finally taking hold in uranium enrichment facilities, according to a book published Tuesday.
The new account, included in Countdown to Zero Day: Stuxnet and the Launch of the World's First Digital Weapon by Wired reporter Kim Zetter, is at odds with the now-popular narrative that the malware first penetrated Iran's Natanz enrichment facility and later unexpectedly broke loose to infect hundreds of thousands of other sites across the globe. That earlier account, provided by New York Times journalist David Sanger, characterized the escape outside of Natanz as a programming error that was never intended by engineers in the US and Israel, the two countries Sanger and Zetter said devised and unleashed Stuxnet. According to Zetter, the world's first known cyber weapon first infected Iranian companies with close ties to Iranian nuclear facilities and only later found its way to Natanz.
"To get their weapon into the plant, the attackers launched an offensive against four companies," Zetter wrote. "All of the companies were involved in industrial control processing of some sort, either manufacturing products or assembling components or installing industrial control systems. They were likely chosen because they had some connection to Natanz as contractors and provided a gateway through which to pass Stuxnet to Natanz through infected employees."
Zetter's book, which Wired previewed last week, is the first published account to name the early Stuxnet victims. They were Foolad Technic Engineering Co., an Iranian maker of automated industrial systems used mostly for steel and power; industrial control system developer Behpajooh Co. Elec & Comp. Engineering; Neda Industrial Group, a company accused of supplying military equipment to Iran; and Control Gostar Jahed, another industrial control systems supplier. A blog post published by security firm Kaspersky Lab to coincide with Tuesday's publication of Zetter's book named a fifth likely "Patient Zero" of Stuxnet, Kala Electric, believed to be the main manufacturer of the Iranian uranium enrichment centrifuges.
Kaspersky researchers wrote:
For Stuxnet to be effective and penetrate the highly guarded installations where Iran was developing its nuclear program, the attackers had a tough dilemma to solve: how to sneak the malicious code into a place with no direct internet connections? The targeting of certain "high profile" companies was the solution and it was probably successful.
Unfortunately, due to certain errors or design flaws, Stuxnet started infecting other organizations and propagate [sic] over the internet. The attacks lost control of the worm, which infected hundreds of thousands of computers in addition to its designated targets.
Bread crumb trail
Normally, it's difficult to reconstruct the infection path a piece of malware takes. Stuxnet, however, contained an unusual trait. Each time it executed, it recorded the name, network name, IP address, and date of the machine and embedded the infection chain in an updated executable file. The list of infected machines grew bigger with each affected system.
Rival security firm Symantec also published a blog post Tuesday that concurred with Zetter's account.
"Based on the analysis of the breadcrumb log files, every Stuxnet sample we have ever seen originated outside of Natanz," wrote Liam O'Murchu, manager of operations for Symantec Security Response. "In fact, as Kim Zetter states, every sample can be traced back to specific companies involved in industrial control systems-type work."
There is no bread-crumb trail for Stuxnet 0.5, the predecessor version of Stuxnet with an alternate way of sabotaging Iranian nukes. That means there's no way to know if it was planted inside Natanz and then spread outwards. The evidence for the much more aggressive version 1, however, now seems clear. Stuxnet broke into Natanz from outside, not the other way around.