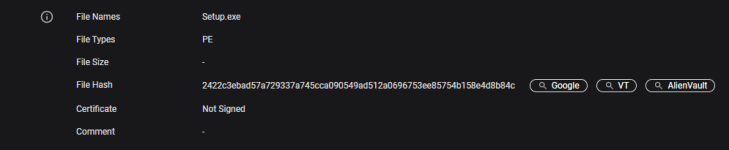
- Feb 7, 2023
- 2,351
Avast, Avira and Bitdefender are fundamentally different engines consisting of more signatures, generic detections and to some extent heuristics. Signatures contain instructions (rules) looking like "from byte x to byte y look for z". Hence they don't need to have a limit at all. Avast uses an arsenal of machine learning and static analysis at runtime as well as on their cloud.How is Avast more suited I take Avast doesn't have size limit?
Norton, Defender, Sophos and many others are engines based primarily on static analysis. Such engines need to have a limit for performance reason. They both have advantages and disadvantages.
They use Sophos locally and have all capabilities of their SDK. In addition, threat emulation can capture passwords for zips in emails and uses a dictionary of passwords that attackers commonly may use. This dictionary includes "infected". Downloading malware from various places results in successful block before you even take the file out of the archive.1. If Sophos engine is capable of handling password-protected zips, can we infer that ZAESNG based on Sophos engine is capable to do the same? Or not necessarily? To be based on a Sophos and Kaspersky engine means to have same capabilities as Sophos and Kasperky engines have?
Kaspersky provides only feeds, once they come across something, they send the hash to ThreatCloud. This is like a more effective and advanced Panda Cloud Antivirus built-in to ZA together with all other technologies.
I always use ZA. Harmony Endpoint is on another system, I am testing it before I become a business customer. These reports are from ZA saved in the directory you mentioned, I go and open from there.2. Here in this thread, are you always using ZAESNG in your tests? Or sometimes you use Harmony EndPoint?
Terminate means the process was suspended immediately together with all connections. But the file wasn't deleted because it is signed. In Harmony Endpoint this can be changed (all files related to an attack can be deleted) but in some cases it can cause issues. For example if you have an abused driver, instead of just suspending the attack, it will delete the driver too. You will have to reinstall it then.What about connections? Sorry to ask, it's not totally clear to me, "terminate" means that the stealer started
For exploits, Harmony and ZA always just end the process without deletion. Meaning if you have vulnerable VLC and a malicious video file, the attack will be suspended but neither the file (you are welcome to delete it manually) nor the VLC player will be deleted (you as admin are welcome to look for updated version).
Last edited: