A dangerous cryptocurrency investment scam has emerged recently targeting social media users and inbox owners across Europe, Canada, Australia and beyond. The fraudsters behind this scam are aggressively promoting a fake platform called Tesla Investments using Elon Musk’s name and image without consent. This article will uncover how this scam works, tactics it uses to deceive, and most importantly, how to spot and avoid becoming another victim.
Overview of the Tesla Investments Scam
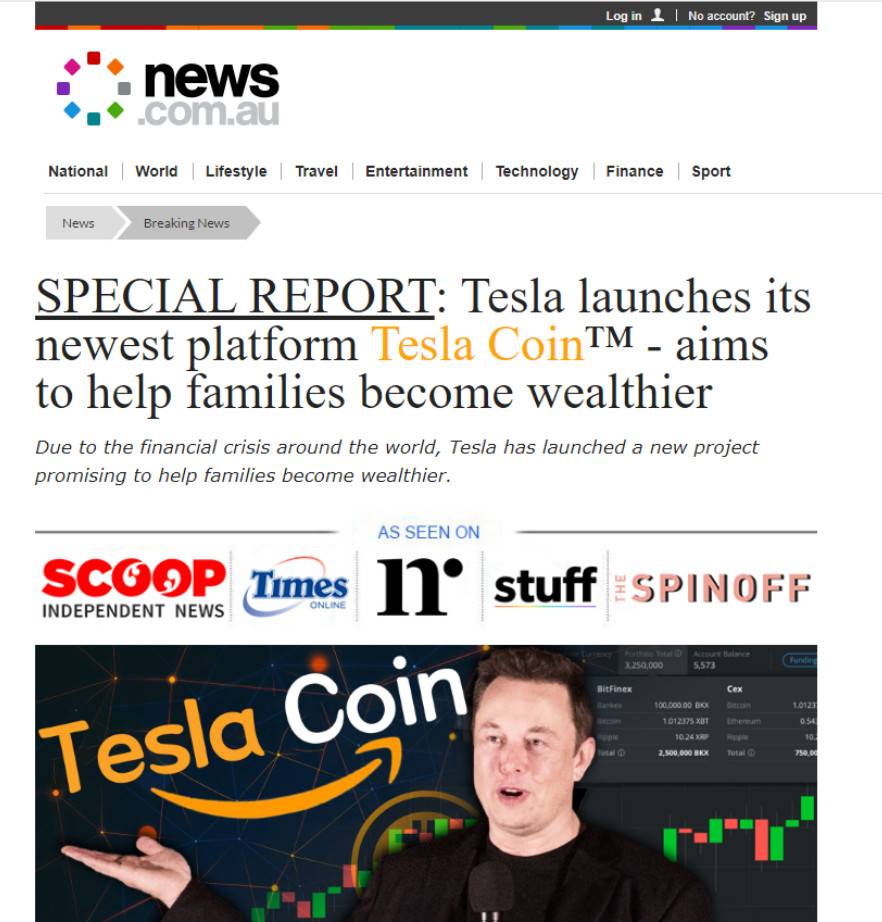
The Tesla Investments scam falsely claims to be a highly profitable AI-powered cryptocurrency platform created by Elon Musk. Scammers promote it via Facebook ads and emails redirecting to fake news pages endorsing the fictitious opportunity. After entering their information, victims are contacted by bots posing as Tesla Investment representatives using manipulative sales tactics to convince victims to deposit funds supposedly to activate trading accounts.
In reality, there is no real Tesla Investments platform, crypto asset, or investment accounts. The criminals behind this scam simply pocket any money sent by victims. The Elon Musk endorsements and materials promoting Tesla Investments are completely fabricated.
How the Tesla Investments Scam Works
The Tesla Investments scam claims to be a highly profitable cryptocurrency created by Elon Musk for Tesla. Scammers promote it by placing Facebook ads and sending emails redirecting to convincing but fake news articles endorsing Tesla Investments.
After entering their information, victims are contacted by bots posing as Tesla Investments representatives. Using manipulative sales tactics, these bots convince victims to deposit at least $250, supposedly to activate trading accounts with massive earning potential.
In reality, there is no real Tesla Investments platform or cryptocurrency. The criminals behind the scam simply steal any funds deposited by victims.
Here is an outline of how this scam operates to defraud victims:
- Scammers pay for Facebook ads and send emails directing to fake news articles promoting Tesla Investments as a lucrative new Elon Musk crypto investment opportunity.
- Victims visit the fraudulent pages and input their personal information into webforms to register interest.
- Bots then contact the victims via email or messaging, posing as Tesla Investment representatives.
- These bots engage in friendly conversations to gain the victims’ trust.
- Eventually, the bots provide payment links urging victims to transfer funds, supposedly to activate their account and earn the huge promised returns.
- Any money sent is stolen by the scammers, as there is no real investment platform or accounts.
- Soon after funds are collected, the bots cease communication, and victims cannot withdraw their non-existent earnings.
This simple but effective process allows the scammers to repeatedly target victims interested in lucrative crypto investments and quickly steal their money.
Avoiding the Tesla Investments Scam
Despite the scam’s initial credibility, several red flags can help identify it:
- Too good to be true – Unrealistic guaranteed profits are a clear warning sign.
- High-pressure tactics – Scammers create false urgency and push for quick payment.
- Requests for upfront payment – Legitimate platforms never require an upfront fee just to open an account.
- Unsolicited contacts – Real investment firms won’t cold contact you demanding immediate action.
- Grammatical/spelling errors – Communications often contain obvious mistakes.
- No verified registration – Tesla Investments lacks any valid business registration or trading license.
- No announcement from Tesla – Tesla has never announced plans to launch a cryptocurrency.
Critical thinking reveals this “opportunity” is clearly a scam.
What to Do if You Lost Money in the Scam
If you made a purchase or entered personal information this website, acting quickly can help you minimize financial loss, secure your accounts, and prevent further misuse of your data. Follow these steps carefully:
- Contact your bank or payment provider immediately
If you paid with a credit or debit card, call your bank’s customer service line and explain that you placed an order on a website that may be fraudulent. Request to dispute the transaction or initiate a chargeback.
If you used PayPal or another payment processor, file a dispute through their resolution center and provide order confirmations, emails, or screenshots as supporting evidence.
Fast action gives you the best chance of recovering your money and preventing additional unauthorized charges. - Freeze or replace your payment method
If your card or account details were entered on this website, it’s safest to have your bank or provider issue a replacement card. This prevents future unauthorized transactions and protects your financial accounts.
Some banks may also offer temporary holds or fraud alerts, ensuring no additional transactions can be made without your consent. - Run a personal data removal scan
Fraudulent websites often collect personal information such as names, phone numbers, addresses, and emails. This data may be shared with third parties or added to marketing and phishing lists.
A trusted service such as Malwarebytes Personal Data Remover can identify where your information is listed across data broker networks and help you request its removal. - Check your digital footprint
Even if you didn’t lose money, your personal data could already be circulating online. Running a digital footprint scan can help reveal whether your email address, phone number, or other personal information is present in leaks or broker databases.
This allows you to take proactive measures such as changing credentials, monitoring accounts, or setting up alerts before your data is misused. - Change your passwords and enable 2FA
If the same email or password used during checkout is also used on other websites or services, update those credentials immediately.
Choose strong, unique passwords and enable two-factor authentication (2FA) on all important accounts, especially your primary email, banking apps, and social media. This extra security layer makes unauthorized access significantly harder. - Scan your device for potential threats
Many fraudulent sites contain hidden tracking scripts, phishing pop-ups, or files designed to compromise your security.
Run a full system scan using a trusted security solution such as Malwarebytes Free or ESET Online Scanner to make sure your device hasn’t been exposed to malware or spyware during the visit.
If any suspicious files are found, remove them and restart your device. - Check your accounts and statements regularly
Monitor your bank and credit card statements closely for any unauthorized activity. Look for unfamiliar charges, subscription renewals, or repeated small test transactions.
Also review your email inbox and online accounts for password reset notices or sign-in alerts you didn’t initiate. Report anything unusual to your bank or account provider immediately. - Report the incident to the appropriate authorities
Reporting helps law enforcement track fraudulent websites and can support your claim if needed.- In the U.S., file a report with FTC ReportFraud.ftc.gov.
- In the EU, contact Europol or your national cybercrime unit.
- Globally, you can also submit the site to ScamAdviser to help warn other consumers.
Providing the website URL, order details, and communications increases the impact of your report.
- Save all evidence and communication
Keep copies of order confirmations, emails, payment records, chat logs, and screenshots of the website. This documentation can be crucial for supporting your chargeback request, reporting the case, or pursuing legal remedies if needed.
Store everything in one secure folder so you can easily provide it to your bank or relevant agencies. - Be cautious of follow-up contact
After incidents like this, affected individuals may receive fake refund messages, phishing emails, or phone calls pretending to offer “assistance.”
Do not click on unsolicited links, download attachments, or provide additional personal information. If you receive any message related to this website, verify its authenticity directly through your bank or official payment provider channels.
Conclusion
The Tesla Investments scam demonstrates how easily scammers can now execute cryptocurrency fraud by impersonating brands like Tesla and fabricating false endorsements. As such elaborate cons proliferate, we must stay alert and think critically before engaging with any unsolicited investment opportunity online. Never send money or personal information to strangers who contact you first. Spotting obvious warning signs can help avoid compelling but fraudulent scams leveraging platforms like Facebook and email to lure their victims.
FAQ About the Tesla Investments Scam
Is Tesla Investments a real cryptocurrency created by Tesla/Elon Musk?
No, Tesla Investments is completely fake. It has no association with Tesla or Elon Musk in any way.
Can I really earn $600+ daily in profits from Tesla Investments?
No, there are no actual profits to be earned. Any claims of guaranteed returns are false promises from scammers aimed to defraud victims.
Why do the bots contacting me seem so friendly and helpful at first?
The bots build trust through friendly conversation so victims feel comfortable providing payment details when asked later. It’s a manipulation tactic.
Are the news articles and ads endorsing Tesla Investments real?
No, any articles or ads promoting Tesla Investments are fabricated by the scammers to lend credibility to the fake opportunity.
Why can’t I withdraw funds after investing in Tesla Investments?
Because there is no real platform, any money you send goes straight into the scammers’ pockets. The investment is 100% fiction.
How can I recover money lost in the Tesla Investments scam?
Unfortunately, recovery of funds is very unlikely since the scammers are anonymous. Reporting the scam promptly can potentially limit damage.