Imagine opening your inbox one morning to find an email claiming to have footage of you in a compromising situation. The sender threatens to send the video to all your contacts unless you pay a ransom in bitcoin. As terrifying as it sounds, it’s all one big criminal charade.
This is the essence of the “News That’s Not Very Cheerful” sextortion scam that’s been targeting unsuspecting internet users lately. While the email may cause initial shock and distress, it quickly becomes apparent the threats are empty.
In this guide, we’ll break down the devious social engineering tricks used in this scam and provide advice for staying safe. Forewarned is forearmed against such fraudsters. When it comes to defending our digital lives, a little awareness goes a long way.
Overview of the “News That’s Not Very Cheerful” Sextortion Scam
The “News That’s Not Very Cheerful” email scam represents a growing trend of targeted sextortion frauds making the digital rounds. This brazen attempt to extort money relies on the exploitation of human emotions like fear, panic, and embarrassment.
By falsely claiming to have obtained illicit videos of the recipient, the cunning scammers play to our instinctive desire to keep private moments confidential. Their social engineering techniques are designed specifically to override logic and reasoning with raw feeling.
While these criminal emails may appear authentic, their supposed hacked device threats are 100% fabricated. The scammers are leveraging baseless lies in hopes that the victim believes them long enough to process a hasty ransom payment.
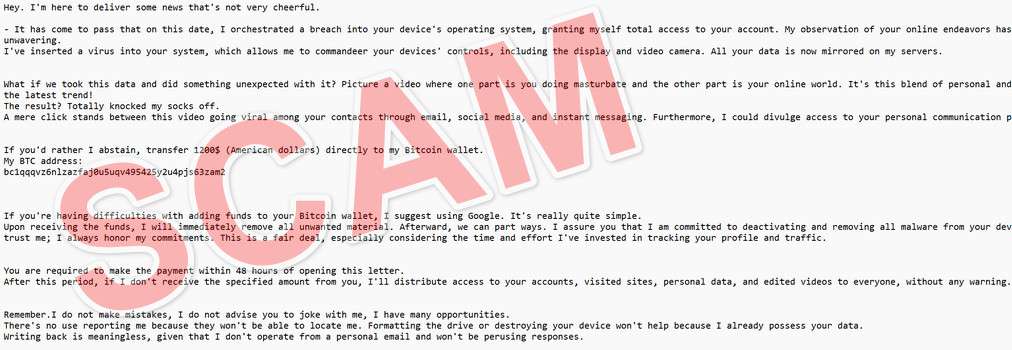
Here is how the “News That’s Not Very Cheerful” email usually looks:
Subject: Access to your “-” device was obtained….
Hey. I’m here to deliver some news that’s not very cheerful.
It has come to pass that on this date, I orchestrated a breach into your device’s operating system, granting myself total access to your account. My observation of your online endeavors has been ongoing and unwavering.
I’ve inserted a virus into your system, which allows me to commandeer your devices’ controls, including the display and video camera. All your data is now mirrored on my servers.
What if we took this data and did something unexpected with it? Picture a video where one part is you doing masturbate and the other part is your online world. It’s this blend of personal and digital that’s the latest trend!
The result? Totally knocked my socks off.
A mere click stands between this video going viral among your contacts through email, social media, and instant messaging. Furthermore, I could divulge access to your personal communication platforms.
If you’d rather I abstain, transfer 1200$ (American dollars) directly to my Bitcoin wallet.
My BTC address:
bc1qqqvz6nlzazfaj0u5uqv495425y2u4pjs63zam2
If you’re having difficulties with adding funds to your Bitcoin wallet, I suggest using Google. It’s really quite simple.
Upon receiving the funds, I will immediately remove all unwanted material. Afterward, we can part ways. I assure you that I am committed to deactivating and removing all malware from your devices. You can trust me; I always honor my commitments. This is a fair deal, especially considering the time and effort I’ve invested in tracking your profile and traffic.
You are required to make the payment within 48 hours of opening this letter.
After this period, if I don’t receive the specified amount from you, I’ll distribute access to your accounts, visited sites, personal data, and edited videos to everyone, without any warning.
Remember.I do not make mistakes, I do not advise you to joke with me, I have many opportunities.
There’s no use reporting me because they won’t be able to locate me. Formatting the drive or destroying your device won’t help because I already possess your data.
Writing back is meaningless, given that I don’t operate from a personal email and won’t be perusing responses.
Good luck, and don’t let this upset you!
P.S. As a word of advice for the future, always follow online safety protocols and refrain from visiting sketchy sites.
Some of the key hallmarks of this despicable scam include:
- Preys on perceived helplessness – The email tries to make victims feel powerless, stating that going to police is useless and deleting data won’t help. This aims to deter reporting.
- Threatens ruination of reputation – By claiming they’ll send adult content to the target’s contacts, the scammers threaten public humiliation and destruction of the victim’s good name.
- Limits time to pay – The 48 hour timeframe adds urgency to pay the ransom before the imaginary videos get leaked. This gets targets to act rashly out of fear.
- Tries to avoid email tracking – The message states that responses won’t be read, in an attempt to prevent email tracking tools from uncovering the criminal’s location.
- Appears credible on the surface – The email cites technical details about malware insertion in an effort to sound legit. But a closer look reveals gaping holes.
- Exploits inhospitable nature of cryptocurrency – Demanding payment by bitcoin allows scammers to remain completely anonymous and withdraw funds instantly.
- Takes advantage of the vulnerable – Elderly and mentally ill individuals are often disproportionately targeted, as they may fall for the social engineering tricks more readily.
- Mass targets random victims – These scam emails blast out to millions of addresses at once, with no specific targeting involved. It’s a numbers game for these fraudsters.
- Threatens recurring extortion – Some messages indicate there will be recurring payment demands, trapping victims in endless blackmail cycles if they pay the initial ransom.
- Seeks to avoid skepticism – The concluding message wishes the recipient “good luck” and tells them not to let this upset them, attempting to placate doubts.
The criminals orchestrating this scam are trying to extort money from as many victims as possible. Even if only a small percentage of recipients pay up, it still adds up to huge ill-gotten profits.
Next, let’s examine exactly how this insidious scam works to trick unsuspecting internet users.
Step-by-Step: How the “News That’s Not Very Cheerful” Scam Works
The “News That’s Not Very Cheerful” extortion scam can be broken down into a series of steps:
1. Criminals Obtain Email Addresses
The scammers first need to collect a large cache of potential victims’ email addresses. These are gathered through illegal spamming techniques like:
- Hacking websites and databases to steal email lists
- Scrapping public forums and social media for publicly available emails
- Buying email lists from shady online brokers
- Using specialized bots and crawlers to scour the web and harvest emails
They may obtain millions of addresses at a time to blast out their scam emails en maste. Quantity over quality is the name of the game.
2. Fraudulent Email Template is Created
Next, the scammers craft the “News That’s Not Very Cheerful” email template containing the extortion threat.
The message is made to look convincing, citing technical details about supposed device compromise and malware installation. The criminals exploit fear and shame to coerce victims.
In reality, the email is complete fiction. But it seems real enough to fool some recipients.
3. Scam Emails Blasted Out
Using the compromised email lists obtained in step one, the criminals send out huge volumes of “News That’s Not Very Cheerful” extortion emails.
Millions of messages can be sent per day to random addresses all over the world. The scam is a numbers game, counting on only a small fraction of people paying up.
4. Recipients Open and Read Email
As the scam emails land in inboxes across the web, some recipients inevitably open and read them. If the victim exhibits any vulnerability or gullibility, they may fall for the scam.
Fear of humiliation motivates targets to comply. The criminals leverage social engineering tactics to manipulate emotions.
5. Ransom Demands are Made
The email contains ransom demands, instructing the victim to pay $1200 in bitcoin to the provided wallet address.
Threats of leaking the imaginary videos are made if payment isn’t received within 48 hours. These threats instill fear in the target and pressure them to pay.
6. Some Victims Send Payment
If the scam is successful, the recipient overlooks the email’s dubious claims and pays the ransom demand. This is the scammer’s desired outcome.
Once money is sent, it goes directly into the criminal’s anonymous bitcoin wallet. The victim’s financial loss fuels the cycle of exploitation.
7. Criminals Disappear with the Money
After receiving payment, the scammers simply cut off contact and disappear with the money. Since bitcoin transactions are irreversible, there’s no way for targets to recover their funds.
The criminals then repeat the process, starting the scam cycle anew to seek out fresh victims. Empty extortion threats allow them to pocket easy money.
As we can see, this is a well-oiled extortion operation built on deception. Next, let’s discuss what to do if you’ve fallen prey to this scam.
What to Do If You’ve Fallen Victim to the Scam
The nightmare scenario is paying the “News That’s Not Very Cheerful” ransom demand, only to realize later that it was all a scam. So what should you do if this happens? Here are tips for recovering from the scam:
- Don’t pay any more money – First, cease all communications with the scammers and never pay additional demands. The promises to delete footage are empty lies to trick you into recurring payments.
- Report the email – Forward the scam email to your email provider’s abuse department so they can investigate the senders. Also file a report with the FBI’s Internet Crime Complaint Center.
- Contact your contacts – If you paid the ransom, the scammers may send out video threats to your contact list anyway. Get ahead of this by informing your friends, family, and coworkers that it’s a scam.
- Beef up security – Change passwords on your email and other online accounts in case of any account compromise. Enable strong two-factor authentication wherever possible.
- Monitor accounts – Keep an eagle eye on your financial statements and online accounts for any signs of misuse stemming from a potential email account breach by the scammers.
- Seek help for emotional distress – Being victimized by cyber extortion can take a psychological toll. Don’t keep silent. Talk to a professional counselor if you need help coping with fear, anxiety or shame.
- Consider law enforcement – If funds were paid, file a report with local police and the FBI. They may be able to trace bitcoin payments to identify and prosecute the criminals. But chances of recovering money are very slim.
With vigilance and proper reporting, you can limit the damage from this scam. Don’t let fear of humiliation prevent you from seeking help.
Frequently Asked Questions About the “News That’s Not Very Cheerful” Scam
1. How does the “News That’s Not Very Cheerful” scam work?
This scam begins with an email sent to the victim claiming their device was hacked and compromising videos were recorded. The email threatens to send the videos to the victim’s contacts unless a ransom is paid in bitcoin. This is a complete fabrication intended to extort money through deception and emotional manipulation.
2. What are some key details in the scam email?
- Claims device was hacked on a specific date to sound credible
- Says videos were recorded of the victim doing adult activities
- Threatens to mix the videos with personal data and send to all contacts
- Demands payment of $1200 in bitcoin within 48 hours
- States that responding to the email is useless
- Uses technical jargon about malware installation to seem legitimate
3. What are some tactics used in the scam email?
- Exploits fear, panic, and embarrassment
- Pressures victims to act quickly before videos are leaked
- Makes targets feel powerless to stop the threats
- Attempts to avoid email tracking to hide scammers’ location
- Tries to prevent victims from thinking rationally or seeking help
4. What type of personal information is compromised?
No personal data is actually compromised. The claims of videos depicting the victim are completely fabricated to extort money. The scammers do not have any sensitive personal information.
5. Does paying the ransom help?
No, paying only enables the scammers and funds their criminal operations. There are no videos to delete, so paying provides no benefit. The scammers typically cut off contact after receiving ransom payments.
6. What happens if I don’t pay the ransom?
Nothing happens if the ransom is not paid, as the scammers have no compromising footage to distribute. They are merely using empty threats in hopes of tricking victims into paying. Not paying is the recommended action.
7. Should I report the scam email?
Yes, report the scam email to your email provider and the FBI’s Internet Crime Complaint Center. This helps authorities track and shut down these fraudsters. Also warn your contacts about the scam in case they receive video threats.
8. How can I recover if I already paid the ransom?
If you paid, immediately contact your bank and police. Monitor accounts closely for signs of misuse. Enable two-factor authentication and change passwords. Seek counseling if needed to cope with the stress. But the likelihood of recovering funds is very low.
9. How can I boost security after receiving the scam email?
Scan devices for malware, change passwords, enable two-factor authentication, monitor accounts closely, and be wary of any further contact attempts by the scammers. Also be vigilant of other scams targeting the same email address.
10. How can I avoid becoming a victim of this scam?
Be skeptical of threat emails demanding untraceable payments. Look for signs like technical jargon, threats, limited timeframes, and requests for secrecy as red flags. Stay calm and think critically before taking any action. When in doubt, seek help.
The Bottom Line
The rise of the “News That’s Not Very Cheerful” sextortion scam makes one thing abundantly clear – scammers will stop at nothing to pocket easy money.
This guide has provided an in-depth look at how this devious scam operates, exploiting fear and embarrassment through social engineering techniques. The criminals may be heartless, but knowledge is power.
Remember, anytime an email threatens you and demands untraceable payment, it’s almost surely a scam. The supposed hacked device, incriminating videos, and contact list threats are all bluffing to coerce payment.
No matter how convinced the scammers sound, they cannot actually access devices or leak footage they don’t have. These fraudsters will say anything for a quick buck.
With awareness of this scam, internet users can confidently spot the telltale signs and delete these criminal emails where they belong – the trash folder. Don’t become another statistic. Instead, arm yourself with the information needed to protect your reputation, finances and mental wellbeing from these scoundrels.