A new texting scam preying on drivers is causing panic across the country. Out of the blue, people are receiving messages claiming they missed a toll payment – complete with threats of fees and legal action. But it’s all a fraud to access bank accounts and steal identities.
This article will explore the Toll Violation Notice scam texts infiltrating phones nationwide. You’ll learn how to spot their trap, avoid being fooled, and protect yourself if they hook you. Don’t let these phishing fraudsters cash in on confusion and fear.
Scam Overview: The Anatomy of Fake Toll Violation Texts
The Toll Violation Notice scam preys on drivers through a crafted mix of urgency, official-looking language, and threats of legal consequences. These fraudulent texts aim to trick unsuspecting people into paying “unpaid” toll fees and handing over personal information.
Understanding the typical anatomy of these phishing attempts makes it easier to recognize and avoid falling victim. Common elements include:
Sender Spoofs Local Area Codes and Numbers
The scam texts appear to come from local phone numbers to boost credibility. Scammers use spoofing technology to falsify the sender information transmitted with messages.
The number always matches the recipient’s area code and prefix to simulate coming from a familiar source. For example, someone with a 951-123-4567 number would receive a text pretending to be from 951-123-XXXX.
PDF Attachments and Phishing Links
A defining characteristic of the scam is inclusion of either a PDF file attachment or hyperlink redirecting to a fake website. Both avenues are traps to harvest data and money.
The PDF uses the guise of containing violation details. In reality, it’s embedded with malware to infect devices and steal information if downloaded.
Meanwhile, the link connects to a fraudulent website mimicking a toll authority’s payment portal. This ensnares victims into typing sensitive information that feeds directly to scammers.
Threats for Unpaid Tolls and Short Deadlines
Scammers leverage fear by claiming the recipient drove on a toll road without paying their due fees. The text insists this infraction was caught by cameras and demands immediate payment—typically within 15 days before fines or legal action.
Without evidence, scammers broadly claim the supposed violation happened recently but leave out any specific toll road details. This prevents victims from easily verifying the validity.
Fake Badges, Logos, and Legal References
To bolster credibility, scammers utilize various techniques to make texts appear official, such as:
- Using fictional government agency names like the “State Toll Authority” or “Toll Enforcement Authority”
- Adding logos of real transportation departments or toll road brands
- Mentioning U.S. state and federal traffic regulations
- Referencing civil and legal consequences for not paying
These elements exploit victims’ tendencies to trust authorities and obey laws. But it’s all smoke and mirrors.
Payment and Personal Information Phishing
If recipients take the bait, scammers steer them towards fake toll authority websites via PDFs or links. These sites mimicking legitimate payment portals.
Once on the sites, victims encounter form fields demanding credit card or bank account information to settle the “unpaid tolls.” There are also forms eliciting personal and contact information.
This supplies everything scammers need to drain bank accounts and steal identities. Meanwhile, victims believe they’re simply paying a fee to avoid legal headaches.
By understanding the scheme’s defined structure, individuals can more readily identify attempted Toll Violation Notice scams and avoid being deceived.
How the Toll Violation Notice Text Scam Works
From start to finish, these are the key steps that reveal how the Toll Violation scam unfolds and bilks victims:
1. Scammers Obtain Victims’ Phone Numbers
Toll Violation scammers first need to get their hands on consumers’ cell phone numbers. They gather numbers through various underhanded methods, including:
- Buying phone number lists on the black market
- Harvesting numbers from data breaches
- Using phone number generator apps
- Guessing number combinations randomly
With a database of numbers in hand, scammers are equipped to blast out phishing texts en masse. The wider the net, the more fish they catch.
2. An Official-Looking Violation Notice is Sent
Using the spoofed local numbers described earlier, scammers send text messages alleging unpaid toll road fees.
The contents generally follow the same template outlined in the anatomy section: threats of legal action, urgent payment deadline, official but vague verbiage, and instructions to view a PDF attachment or click a link for more details.
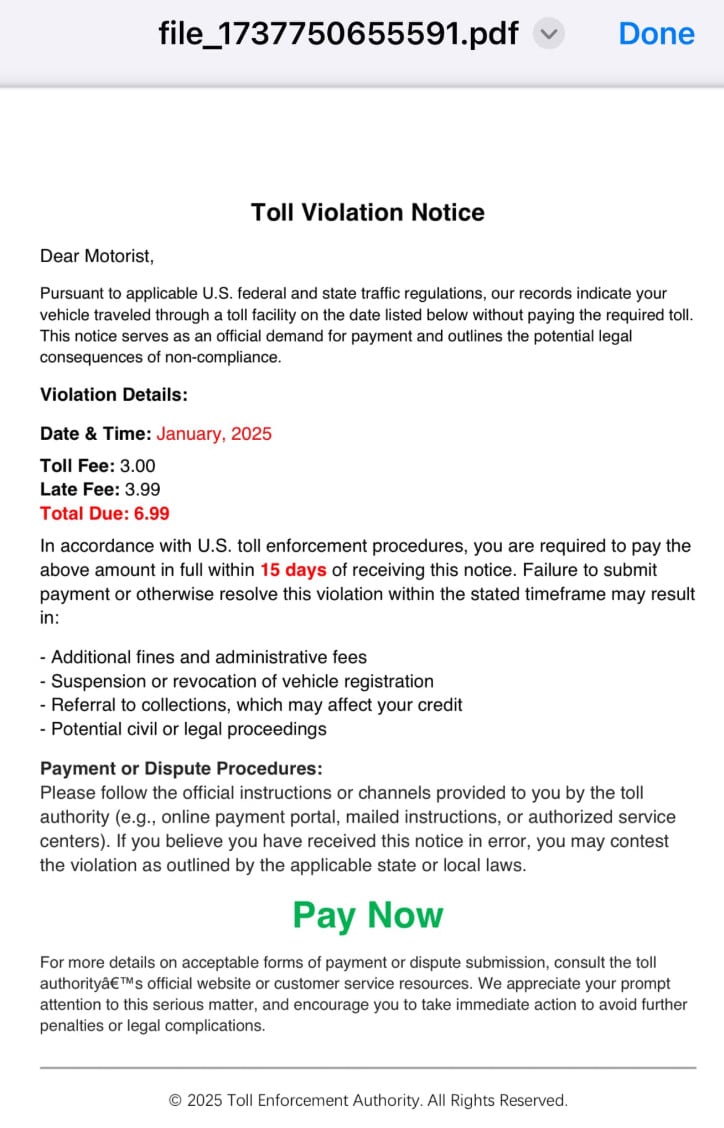
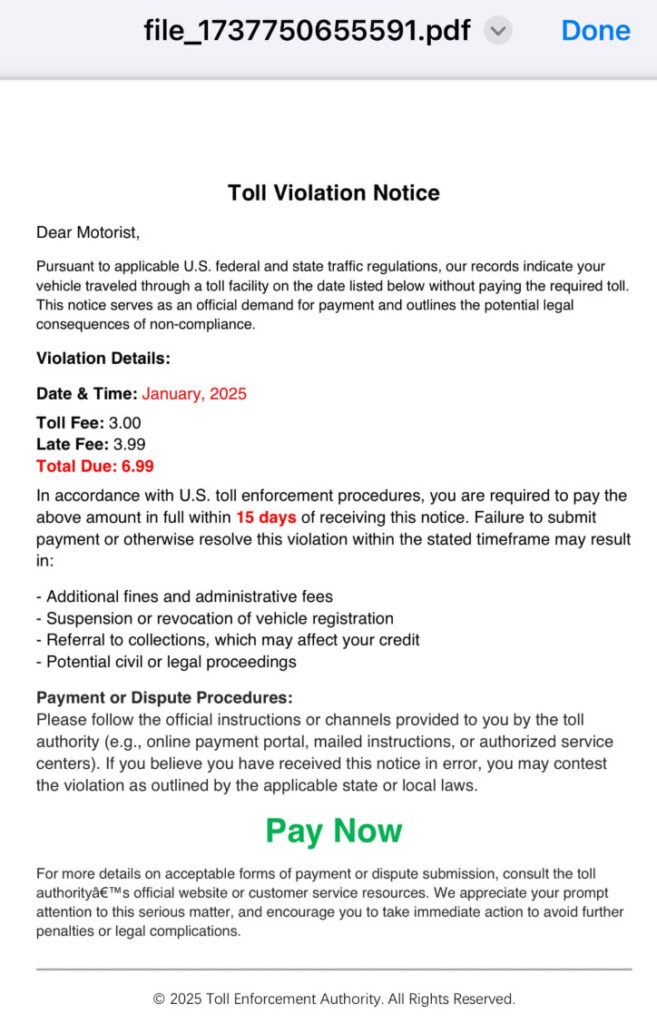
Here is what the PDF might say:
Toll Violation Notice
Dear Motorist,
Pursuant to applicable U.S. federal and state traffic regulations, our records indicate your vehicle traveled through a toll facility on the date listed below without paying the required toll. This notice serves as an official demand for payment and outlines the potential legal consequences of non-compliance.
Violation Details:
Date & Time: January, 2025
Toll Fee: 3.00
Late Fee: 3.99
Total Due: 6.99
In accordance with U.S. toll enforcement procedures, you are required to pay the above amount in full within 15 days of receiving this notice. Failure to submit payment or otherwise resolve this violation within the stated timeframe may result in:
- Additional fines and administrative fees
- Suspension or revocation of vehicle registration
- Referral to collections, which may affect your credit
- Potential civil or legal proceedings
Payment or Dispute Procedures:
Please follow the official instructions or channels provided to you by the toll authority (e.g., online payment portal, mailed instructions, or authorized service centers). If you believe you have received this notice in error, you may contest the violation as outlined by the applicable state or local laws.
Pay Now
For more details on acceptable forms of payment or dispute submission, consult the toll authority’s official website or customer service resources. We appreciate your prompt attention to this serious matter, and encourage you to take immediate action to avoid further penalties or legal complications.
This is where the scam hinges on fear and confusion to get recipients to let their guard down.
3. Victims Open the PDF or Click the Link
If the initial text achieves its goal, worried recipients will either open the attached PDF or follow the link for more information. But this delivers victims right into the scammer’s hands.
The PDF attachment or phishing link connects to a fraudulent website masquerading as a legitimate toll authority. Its sole purpose is stealing personal and financial data.
4. Scammers Collect Payment and Personal Information
Once on the phishing site, victims see elaborately crafted graphics and messaging reinforcing the supposed violation and directing them to pay immediately.
Various psychological tricks pressure people into entering their credit card or bank account information, including:
- Countdown timer
- Threats of financial or legal consequences
- Fake customer support chatbox
Beyond payment info, scammers also have victims complete forms with personal and contact information. This supplies data for identity theft down the road.
5. Scammers Disappear with the Money and Information
Victims expect their payment to settle the phony violation. But in reality, scammers pocket the money and use any collected information for future frauds or sell it on the dark web.
Meanwhile, recipients receive no confirmation or updates from the “toll authority.” The scammers simply disappear without a trace.
By the time victims realize it was a scam, the damage is done. Scammers have drained bank accounts and acquired the means to steal identities. They are long gone before victims can attempt to recover lost funds or compromised information.
What to Do If You’ve Fallen Victim to the Toll Violation Notice Scam
Discovering you’ve fallen prey to the Toll Violation Notice scam is unsettling but don’t panic. Here are the key steps to start addressing the situation:
Act Quickly to Contain the Damage
- Notify banks/credit card companies: Alert your financial institutions to reversed any fraudulent charges and monitor for suspicious activity. Cancel cards used on scam sites.
- Place fraud alert: Contact one of the three credit bureaus to place an initial 90-day fraud alert on your credit file. This requires creditors to verify your identity before opening new accounts.
- Enroll in credit monitoring: Sign up for credit monitoring services to stay on top of your credit reports and catch any signs of identity theft early. Many companies offer victims free monitoring for 12 months.
- Change passwords: Update passwords, security questions, and PINs for any compromised accounts. Make them strong and unique for different accounts. Enable two-factor authentication when possible.
Report the Scam Activity
- Contact local authorities: File reports with your local police department and state attorney general’s office. Provide details on how the scam occurred and any losses incurred.
- Report to the FTC: Submit a complaint with the FTC (Federal Trade Commission) on their website or by calling 1-877-FTC-HELP. The FTC aggregates scam reports to aid law enforcement.
- Inform the toll road authority: If scammers used the name of a legitimate toll authority, notify them of the scam so they can warn customers. Provide details that may help identify the fraudsters.
- Warn contacts: Let close contacts know about the scam messages in case they receive them too. Reporting helps raise awareness before more people fall victim.
Seek Reimbursement for Losses
- Dispute unauthorized charges: Work with your bank and credit card issuer to dispute any unauthorized charges from the scam. Under federal law, you have protections against fraudulent charges.
- Review reimbursement options: Depending on details, you may be eligible for reimbursement for losses through banks, credit cards, or victim assistance programs. Contact them regarding claim procedures.
- Consult professionals if needed: For significant identity theft or complex cases, consulting a lawyer or cybersecurity expert may help strengthen claims and maximize reimbursements. But this route requires weighing the costs versus potential recovered funds.
With vigilance and swift action, you can minimize the fallout from the Toll Violation Notice scam. Don’t let embarrassment or pride prevent you from taking the necessary steps to protect yourself after being deceived.
Frequently Asked Questions About Toll Violation Notice Scam Texts
1. How do scammers get your phone number?
Scammers obtain victim phone numbers through various underhanded tactics, including buying number lists on the black market, harvesting from data breaches, using number generator apps, and random number guessing. With a database of numbers, they can blast out phishing texts en masse.
2. What tricks do scammers use in the Toll Violation Notice phishing texts?
These Toll Violation Notice scam texts use various tricks to appear legitimate, such as spoofing local area codes/numbers, making threats and short payment deadlines, mentioning fake legal authorities, and including fraudulent PDF attachments or links to phishing websites.
3. What happens if you click the link or open the PDF?
The PDF attachment often contains malware to infect your device and steal personal data. The phishing link goes to a fake website impersonating a toll authority to get you to enter personal and financial information that feeds directly to the scammers.
4. How do you avoid falling for the Toll Violation Notice phishing texts?
Do not open attachments or click embedded links. Instead, look up the official toll authority contact information and call them directly to verify any payment notices. Check for scam indicators like threats, typos, and requests for immediate payment via text.
5. What should you do if you shared personal information?
If you entered personal or financial data, immediately call banks/credit companies to reverse charges and monitor for fraudulent activity. Place fraud alerts, enroll in credit monitoring, change account passwords and security questions, and contact authorities to report the incident.
6. How can you report the phishing texts?
Forward scam texts to 7726 to report them to your cell provider. File complaints with the FTC and your state attorney general’s office. Contact the legitimate toll authority being impersonated to alert them.
7. Will you have to pay actual tolls if scammed?
No, the toll violation claims are completely fabricated. You will not owe anything to legitimate toll authorities. The scammers keep all ill-gotten payments and disappear. But you remain responsible for any real unpaid toll fees.
8. How can you avoid Toll Violation Notice scam texts?
Be cautious of texts claiming you owe fees, ignore demands for immediate payment over text, manually look up official contact info, and never provide info without verifying the requester’s identity. Getting educated on common tactics these scams use is key to staying protected.
9. What recourse do you have if scammed out of money?
Report unauthorized charges to your bank/credit company to dispute them and get reimbursement under fraud protections. You may also have reimbursement options through cards or victim assistance programs depending on specific details.
10. How can you help stop these phishing scams?
Be vigilant in reporting scam texts to all appropriate authorities. Share knowledge of these scams with others to spread awareness. Data from victim reports helps law enforcement shut down scam operations and nab fraudsters.
The Bottom Line: Stay Vigilant Against Toll Violation Scam Texts
Don’t let sneaky Toll Violation Notice scammers fool you into handing over your hard-earned money or personal information. With the right knowledge, you can evade these phishing texts and warn others.
Follow these tips to protect yourself:
- Be skeptical of any texts demanding urgent toll payments and threatening consequences. Legit notices come via mail with time to address.
- Call the supposed toll agency directly using official contact info to validate notices before taking any action demanded over text.
- Never open attachments or click links within unsolicited messages. Go straight to the toll road’s website through your browser if you need to manage payments or violations.
- Watch for phishing indicators like odd numbers, grammatical errors, threats, and pressure for immediate payment. These are telltale signs of scams.
- Look up and save the official contact info for toll roads you use so you can easily verify any notices received. Don’t rely on what texts provide.
- Report scam texts to authorities and warn contacts who may also receive them. Spreading awareness helps cut down on victimization.
You now have the knowledge to recognize deceitful Toll Violation texts and take simple steps to avoid being scammed. Don’t leave yourself vulnerable by ignoring this threat. Instead, use these tips to confidently dodge scammers aiming to profit off confusion and urgency. Stay vigilant!