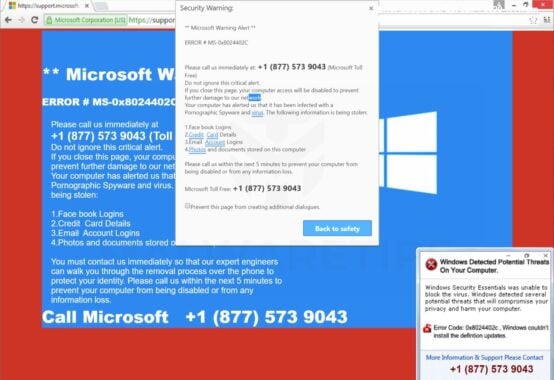
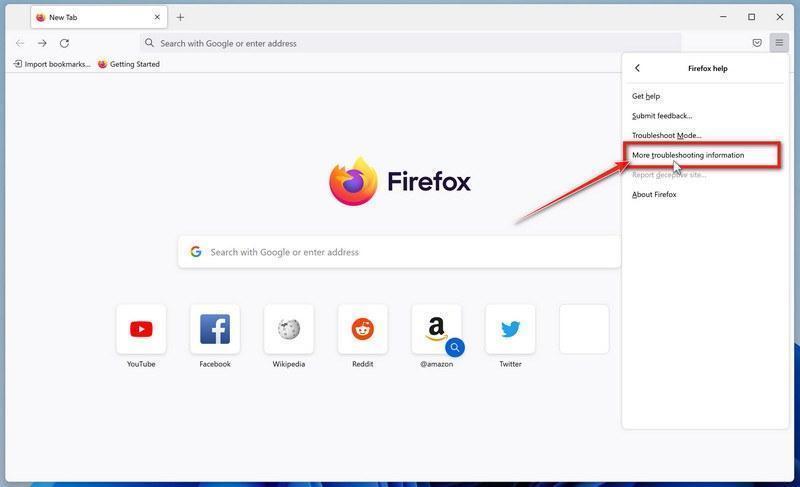
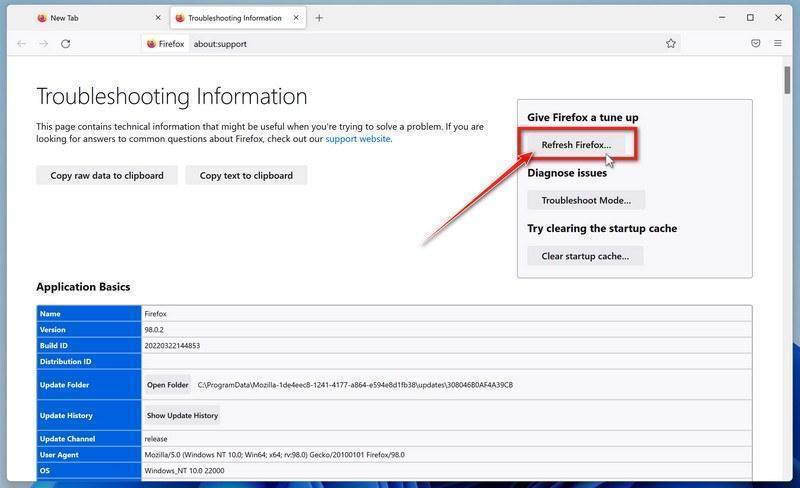
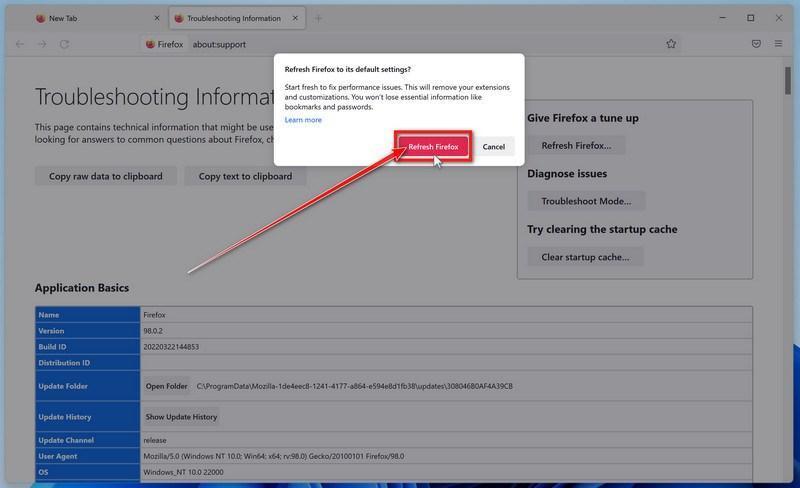
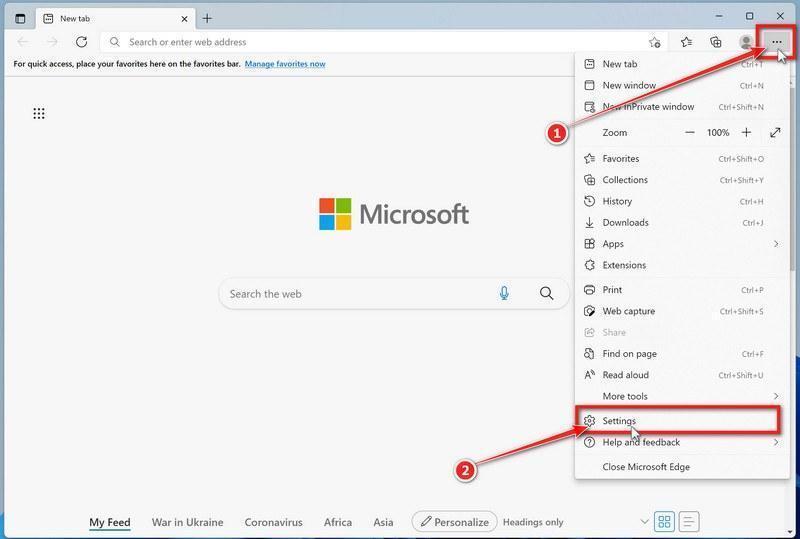
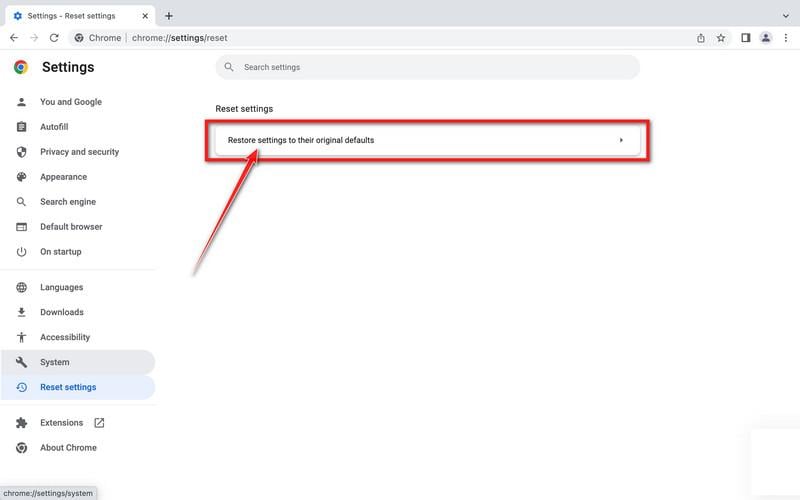
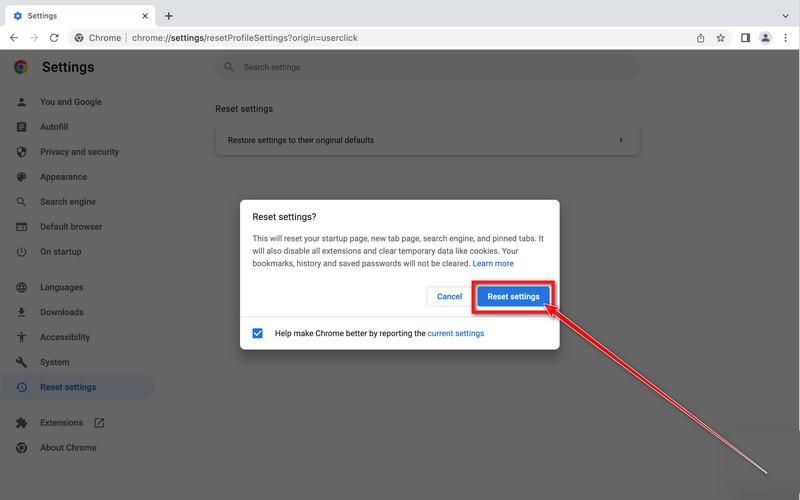
Tech support scams are on the rise globally. Scammers pretend to be from major tech companies like Microsoft or Apple and claim they detected issues on your computer. They say that viruses, malware or hacking was found and you need to call them immediately. But it’s a lie – they just want to trick you into paying for fake services or letting them access your computer to steal data.
This comprehensive guide will provide an overview of tech support scams, explain how they work, provide tips on how to identify them, and give recommendations on what to do if you become the victim of one.
What Are Tech Support Scams?
Tech support scams refer to deceptive cybersecurity practices where attackers impersonate technology support representatives from trusted brands like Microsoft, Apple, Norton, or McAfee. These scammers contact victims claiming to have detected malware, viruses, hacking, or other issues on the target’s computer, phone, tablet, or other devices. They then pressure victims into purchasing expensive but useless software, security programs, or technical support services that supposedly will fix the fictional problems.
In the past, these schemes often started with unsolicited phone calls to victims. However, scammers have expanded their tactics and now commonly use fake security alerts on websites to fool targets.
For example, they will place pop-up ads laden with malware on shady streaming sites, torrent repositories, and adult content platforms. These fake ads pretend to be urgent security warnings from Microsoft, Apple, or antivirus vendors stating that the user’s device is compromised. They provide tech support numbers for the victim to call to purportedly remove the non-existent infections.
Scammers also create malicious browser extensions that inject similar bogus virus warnings and tech support numbers when users visit legitimate websites. Spam email campaigns employ this same phishing strategy by telling recipients to call supposed support lines regarding account breaches.
Some tech support scams even build elaborate fake login pages mimicking Windows, iCloud, or other platforms. When victims enter their credentials, instead of signing in, these sites display alarming system alerts pressuring visitors to call scam tech support numbers due to hacking detections.
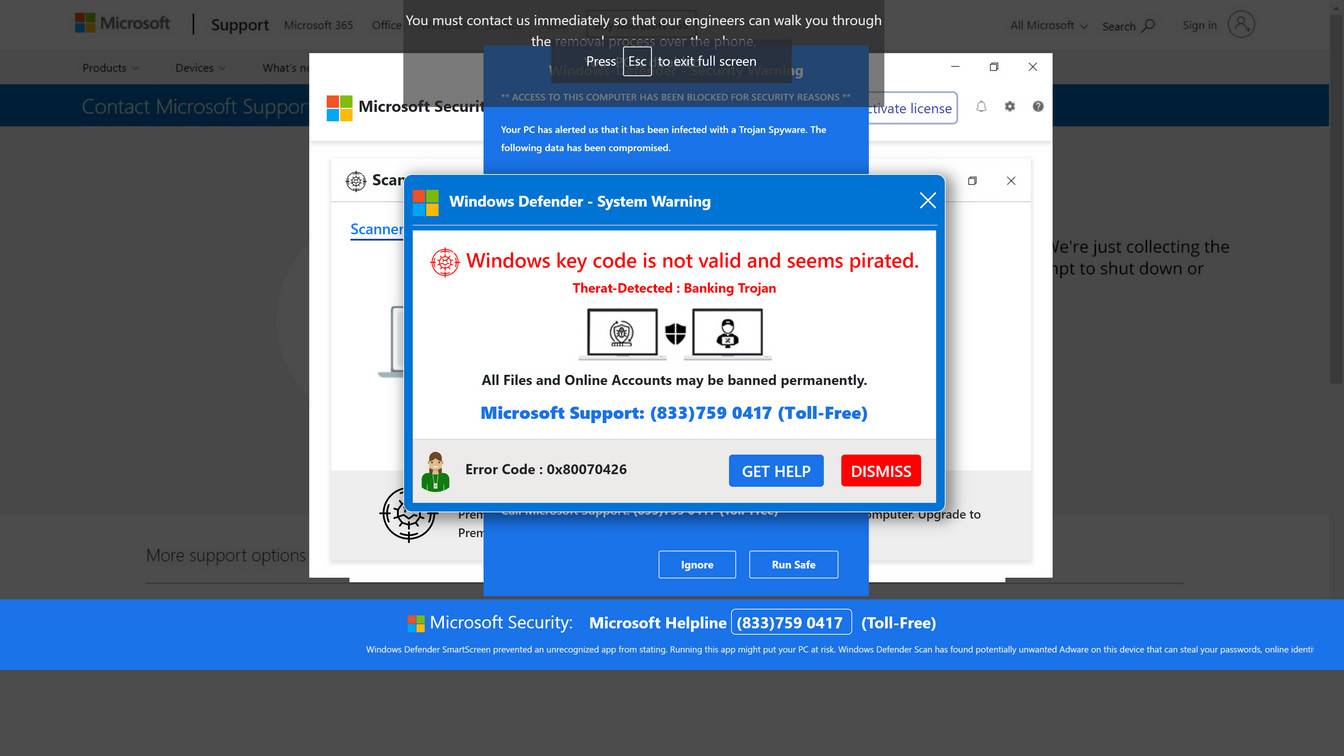
Examples of the fraudulent security alerts shown in these various scams include:
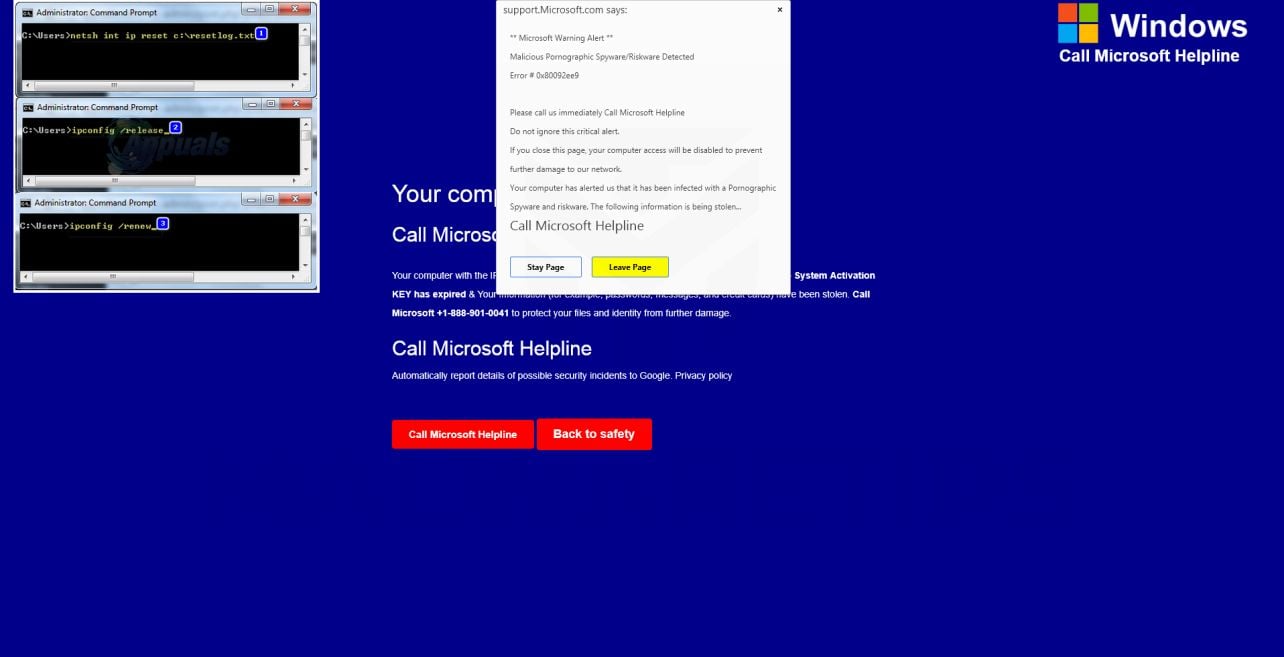
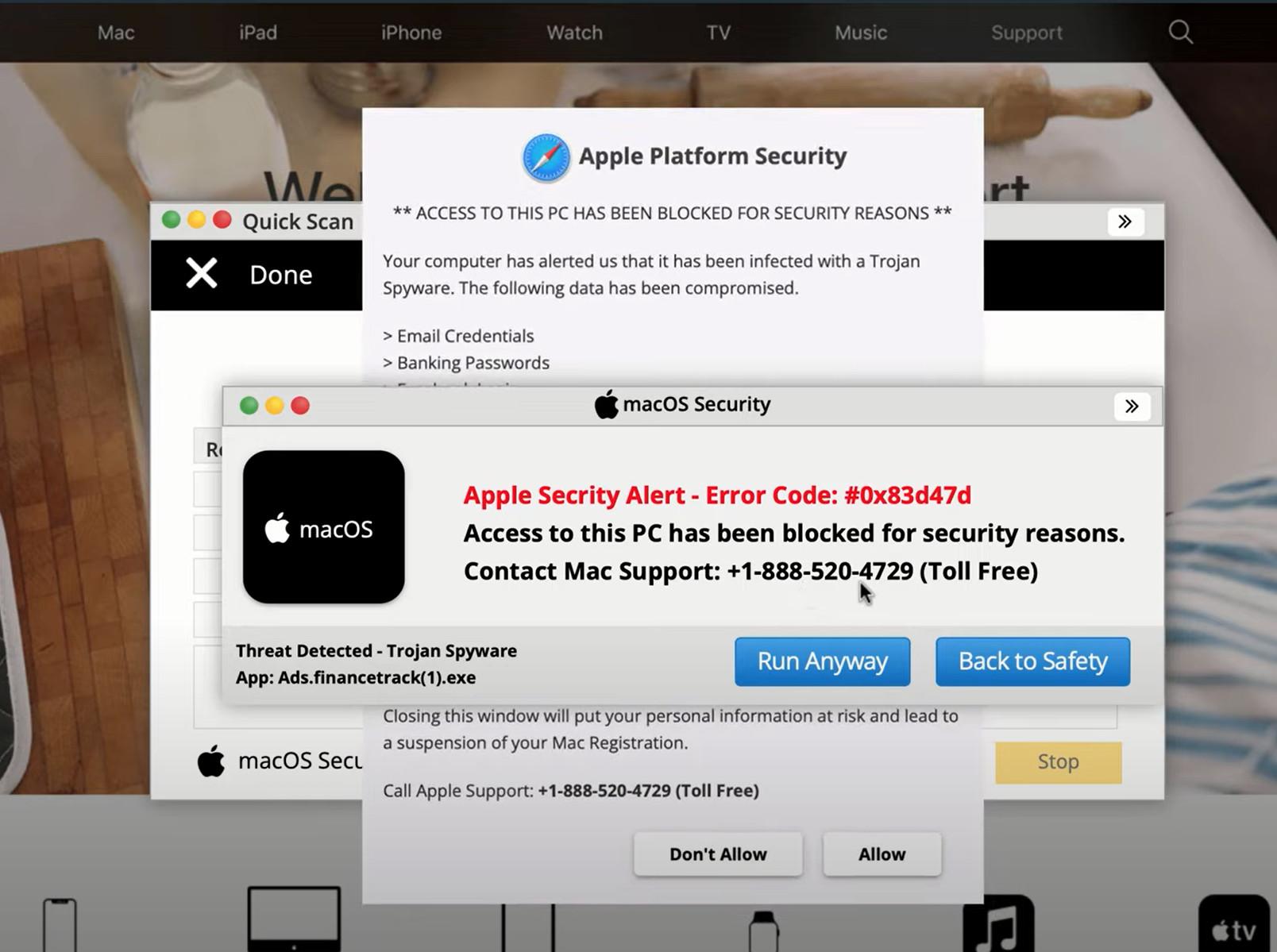
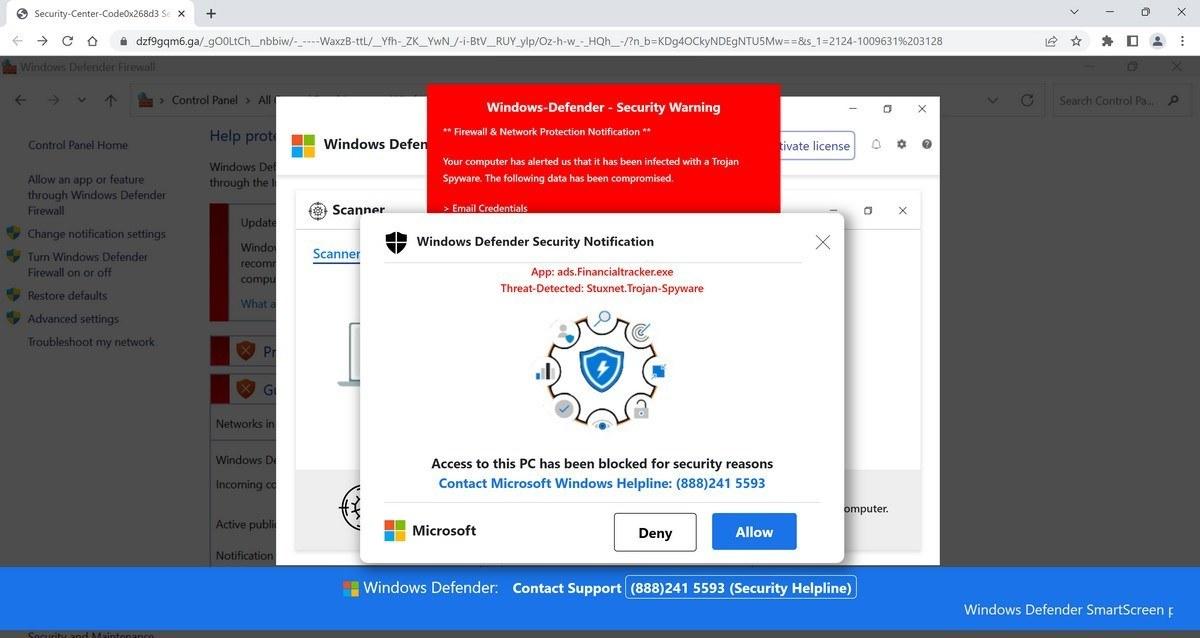
- “Access To This PC Has Been Blocked For Security Reasons”
- “Windows Defender – Threat Detected”
- “Firewall Notification – Credentials Compromised”
- “Call Support Immediately – Computer Disabled”
Of course, these threatening notifications are only designed to frighten users into calling the fake support numbers provided. The scammers on the other end of the lines pretend to be from Microsoft, Apple, or security vendors and claim they must access the victim’s computer remotely in order to diagnose and remove the so-called viruses. This simply allows them to covertly steal data and install actual malware instead.
If you encounter any pop-up, email, or webpage telling you to call tech support for supposed security issues, it is always a scam. Legitimate warnings never ask you to phone unknown numbers or enable remote access in this manner. Close out these scam tabs immediately and avoid calling the fraudulent support lines listed. The scammers will only leverage social engineering and remote control to infiltrate your personal information and accounts
Common Tech Support Scams
There are several variants of tech support scams. Here are some of the most prevalent types:
1. Fake Security Alerts
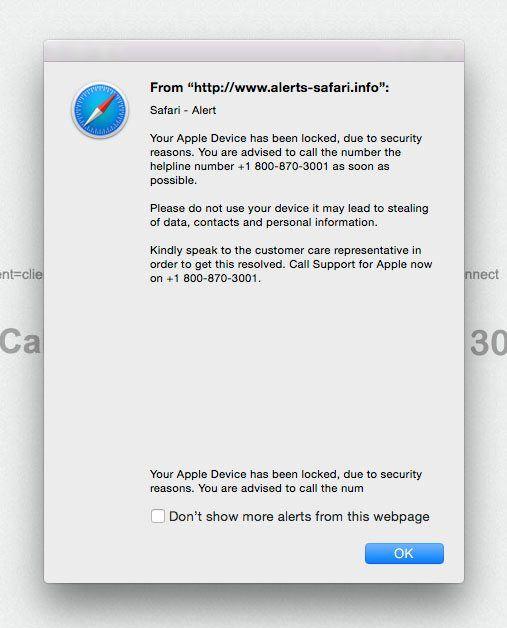
This is the most common tech support scam tactic and involves fake security alerts generated through pop-up ads placed on shady streaming sites, torrent repositories, and adult content pages. The malicious ads pretend to be urgent security warnings from Microsoft, Apple, or antivirus vendors. They claim the user’s device is infected, hacked, or otherwise compromised and provide a tech support number to call.
Similarly, scammers create malicious browser extensions that inject fake “virus detected” warning pages when users visit legitimate sites. They scare users into calling the number to remove the non-existent infection.
Some examples of the alarming fake security alerts shown through these tactics include:
- “Access To This PC Has Been Blocked For Security Reasons”
- “Windows Defender Security Notification – Threat Detected”
- “Firewall & Network Protection Notification – Credentials Compromised”
- “Windows Security Warning – Computer Disabled – Call Support”
- “Major Security Issue Detected – Information at Risk”
The notifications list phone numbers with area codes like 844, 833, 888, and 855. They sometimes claim to be Microsoft, Apple, Norton, or McAfee support.
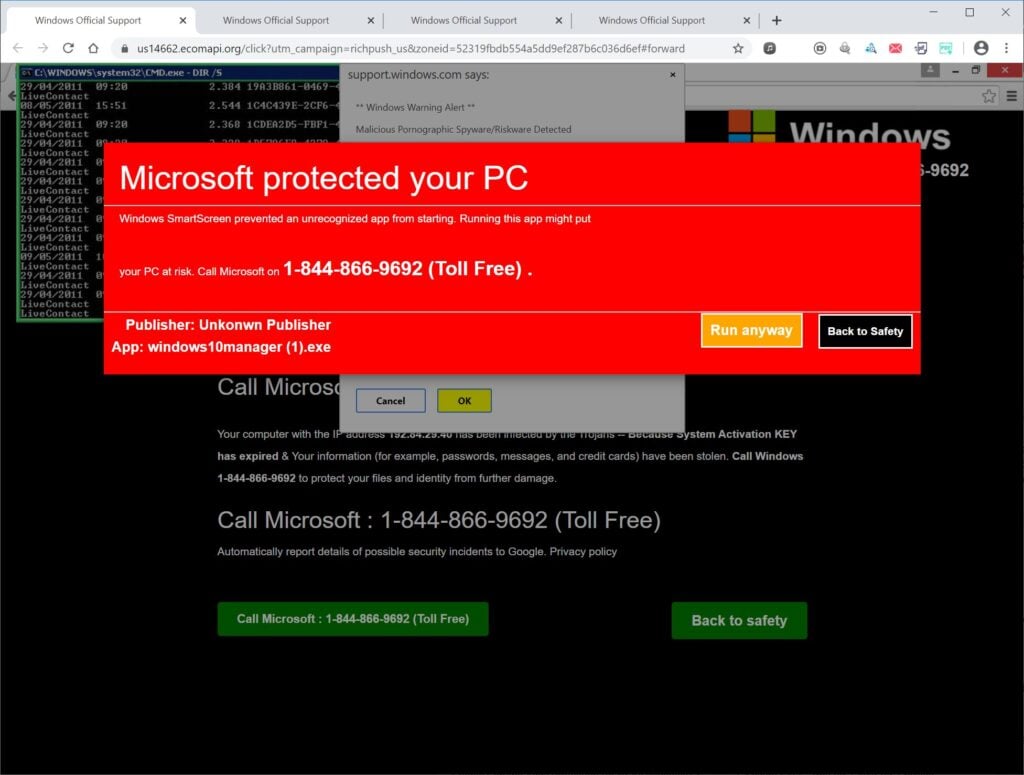
Of course these alarming warning pages are only designed to get users to call the fake support lines listed. The scammers on the other end will claim they need to connect to the victim’s computer remotely in order to diagnose and remove the supposed viruses. This allows them to covertly install malware and steal data.
If you see any type of pop-up or web page telling you to call tech support, it is always a scam. Real security software never operates this way. Close the tabs immediately using Task Manager if needed. Never call the numbers listed or provide any information. The scammers will leverage social engineering over the phone to gain remote access, install malware, and steal personal data.
2. Cold Calls
Unexpected phone calls from scammers claiming to be Microsoft, Apple, or other tech support reps are also common. The scammers will say they’ve detected security problems on the victim’s computer and offer to fix them for a fee. But it’s simply a lie aimed at scaring victims into paying.
3. Fake Refund Calls
Scammers may also call posing as tech company refund departments. They claim the victim is owed money for past services or subscriptions and try to gain remote access to process the supposed refund. In reality, they just use this as a ploy for remote access in order to steal data and money.
4. Fake Activation Messages
Some scams involve pop-ups with messages saying the victim’s software license key has expired. The message demands that the victim calls the number provided to reactivate their license key. This is always a scam, as real software does not work this way.
5. Bogus Billing Emails
Scammers may send spam emails claiming unrecognized charges were made on the victim’s account for antivirus subscriptions. They claim that the victim must call a phone number if they don’t recognize the charge. This is entirely fake and just a scam for remote access.
The End Goal – Stealing Money and Information
These fake security alerts and tech support calls have nothing to do with real warnings from Microsoft, Apple, Google or any other legitimate company. The scammers’ end goal is solely to extort money from victims or outright steal financial information.
If you call the phone numbers listed in these fraudulent pop-ups and alerts, you will be connected to elaborate fake support centers set up by scammers. When speaking to you, the scammers will claim they detected viruses, malware, or hacking activity on your device.
They will then pressure you to allow them remote access to your computer by having you download screensharing software like AnyDesk. The scammers claim this is so they can diagnose and remove the infection.
However, once connected remotely, the scammers will instead install malware, ransomware, or spyware without your knowledge. This allows them to steal passwords, financial information, personal files, photos, and more from your system.
The scammers may even try to directly access your online banking accounts and transfer funds if they can operate your computer remotely. They will also likely pressure you to pay exorbitant fees for unnecessary anti-virus software or fake technical support services to “fix” problems that don’t exist.
In extreme cases, the scammers will demand payment via untraceable gift cards and have you read them the redemption code over the phone. This allows them to quickly steal the gift card balance you loaded.
In summary, the fake pop-ups are simply to scare you and get you to call the number provided. Everything the scammers claim after that point is a complete lie. They just want to access your computer remotely to infiltrate your personal information and accounts for theft and fraud. Never call the tech support numbers in suspicious pop-ups or alerts.
Who Do Tech Support Scams Target?
Tech support scams can target both individual consumers and businesses. However, some common targets include:
- Elderly computer users who may be less tech-savvy. Scammers assume they will be more easily convinced of the scams.
- Small businesses without dedicated IT support. Scammers pretend the business’ devices are critically infected to get paid for fake remediation services.
- New computer owners who are less familiar with standard processes. Scammers exploit their lack of knowledge about normal security alerts.
- English speakers in western countries like the US, Canada, UK, and Australia. Scam operations focus heavily on English speakers in these prosperous nations.
- Any user experiencing legitimate computer issues. Scammers use opportunities like real crashes or slowness to exaggerate problems in their scam pitch.
How Do Scammers Carry Out Tech Support Scams?
Tech support scammers are highly skilled at psychological manipulation and social engineering. They will use a variety of deceptive tactics to carry out their scams seamlessly.
1. High Pressure and Threats
Scammers leverage fear, uncertainty, and doubt in their social engineering tactics. They will use threats and high-pressure language insisting that the victim’s computer is at grave risk if they do not act quickly. This is aimed at scaring victims into complying.
2. Fake Remoting Software
Scammers often urge victims to install remote access programs like AnyDesk so they can “diagnose” the issue. In reality, this allows them to take control of the computer silently for malware installation and data theft. Legitimate tech companies do not need customers to install sketchy remote software.
3. Scripts and Teams
Tech support scam operations usually have teams working off scripts and call sheets. They sound legitimate by posing as authorized tech reps and referring to real software and companies like Microsoft, Norton, and Apple.
4. Exaggerated Diagnostics
Once scammers gain remote access, they use built-in Windows tools like Event Viewer to generate exaggerated diagnostic reports to trick victims into thinking their computers have serious issues.
5. Bundling Malware
Some scammers bundle malware like keyloggers with free software offered from their scam sites. Once installed, they call victims posing as Microsoft and pretend to detect the malware they covertly installed earlier.
6. Fake Refunds
Scammers may promise refunds for the price of the useless services and software they sell to victims initially. But they will just use this as another opportunity to steal financial information. Legit companies do not need remote access just to process refunds.
Signs of a Tech Support Scam: How to Identify Them
While scammers are constantly evolving their tactics, there are some common signs that can help identify tech support scams:
1. They Contact You First
Legitimate tech help will never call or message you unsolicited. Microsoft, Apple, and other vendors do not make calls about devices or accounts unless you contact them first.
2. High-Pressure Threats and Fear Tactics
Scammers use threats, like claiming your computer will crash immediately if you do not comply, to pressure you into acting fast. A real tech rep will never make outrageous threats like this.
3. Asking for Remote Access
Remote access tools are only needed for advanced troubleshooting. Scammers leverage remote access to covertly install malware and steal data. Real tech support will suggest much simpler steps first before remote access.
4. Vague Claims of Problems
Scammers cannot provide details on the supposed issues because they made them up. Ask for specifics on the viruses, malware, or problems they claim to detect. A real tech rep could provide detailed reports.
5. Asking for Advanced Payment
Legitimate tech reps will not ask for payment before performing any work or diagnostics. Only scammers demand upfront payments from victims.
6. No Caller ID or Fake Caller ID
Scammers often use internet calling services or spoofed numbers to display fake, missing, or unverifiable caller IDs. Check the number if one appears and be wary of unidentified callers.
7. Ordering You Not To Act
Scammers may tell victims not to take common-sense precautions like contacting their security software company or checking with their IT department. Real tech reps will suggest getting second opinions.
8. Threats of Account Termination
Scammers may threaten to disable or delete your online accounts if you do not comply with their demands. Real tech companies just do not behave this way under any circumstances.
What to Do If You Get a Tech Support Call
If you receive an unsolicited tech support call, here are some tips on how to handle it:
- Don’t panic – Remain calm and don’t act hastily, even if the scammer uses threats and urgency to pressure you.
- Ask detailed questions – Probe the caller for information like employee name/ID, company department and location. Scammers typically cannot provide specifics.
- Verify the number – Look up the company’s official contact info independently and call back to confirm if the call was legitimate.
- Don’t provide info – Never give personal or financial information to an unverified caller claiming to be tech support.
- Hang up – If the call seems suspicious, hang up. You can always call the company directly later to check if the call was legitimate.
- Report scam calls – Notify the FTC and local authorities about scam callers to help warn others.
- Add numbers to block list – After reporting scam calls, add the numbers to your block lists to filter future calls automatically.
What to Do If You Already Paid a Tech Support Scammer
If you already fell victim to a scam and paid money, take these steps immediately:
- Call bank/credit card companies – Notify your bank and credit card providers to dispute the charges and have them reversed. Cancel any recurring payments or subscriptions.
- Secure accounts – Change online account passwords that the scammers may have accessed during remote control sessions. Enable two-factor authentication if possible.
- Scan for malware – Download legitimate antivirus software like Malwarebytes to scan your computer for any malware, spyware or remote access tools the scammers may have installed. Remove anything suspicious.
- Alert authorities – File detailed fraud reports with the FTC, FBI IC3, and local law enforcement. Provide them with the scammer’s phone numbers, names used, and any other details.
- Warn others – Post about your experience on social media or tech forums to make others aware of new scam tactics. Report fake websites or ads used for scams to site admins.
- Be more vigilant – Learn from this experience moving forward. Never give info or access to unsolicited callers. Verify things independently if you have any doubts.
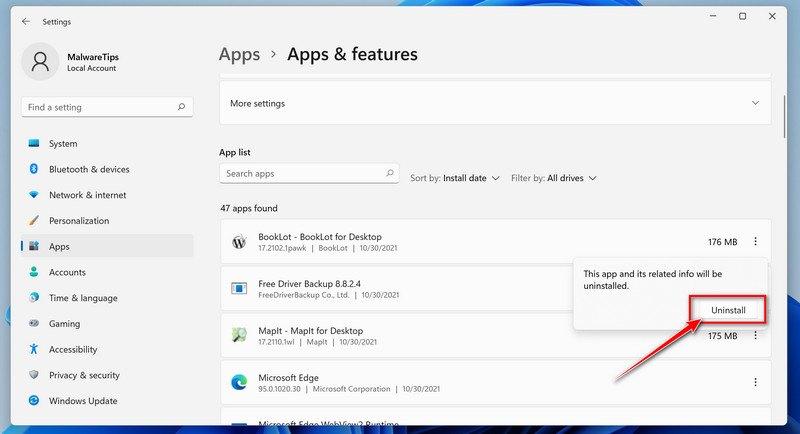
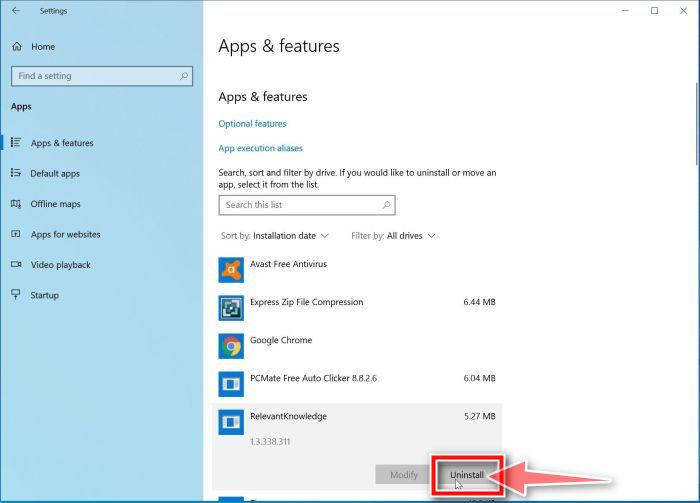
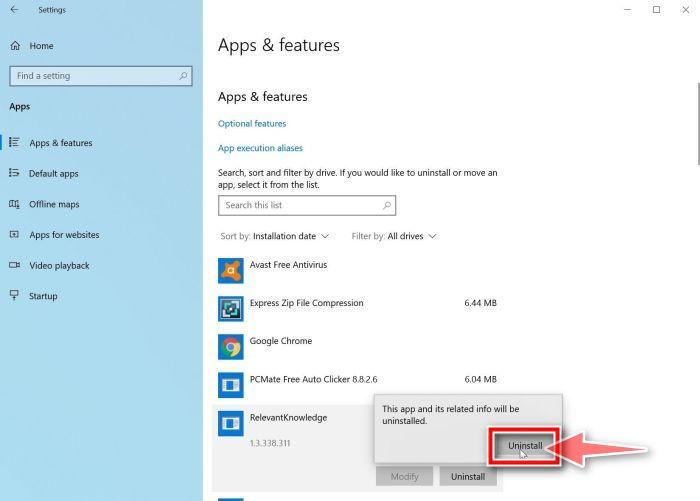
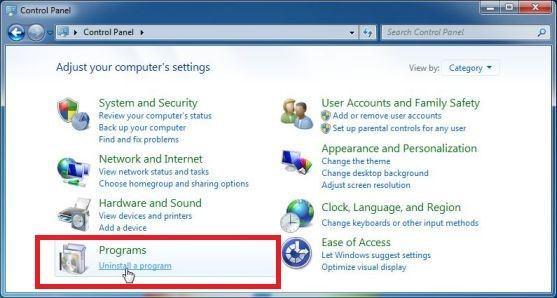
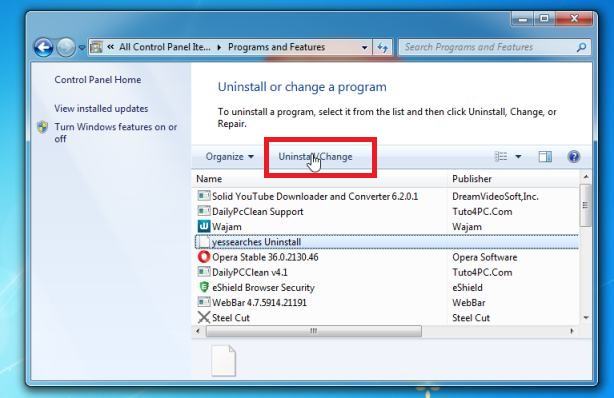
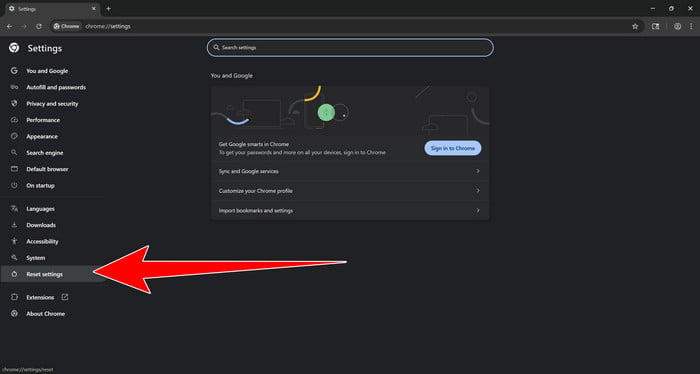
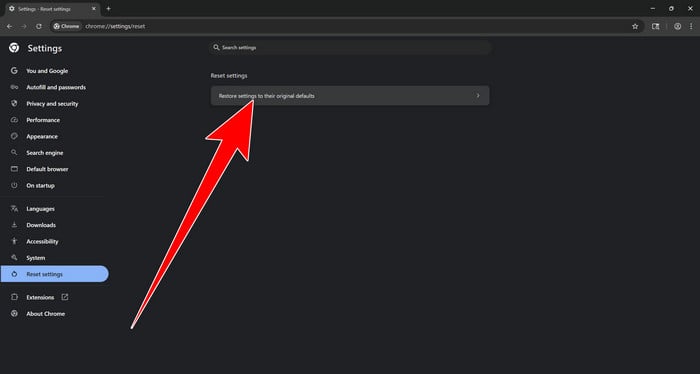
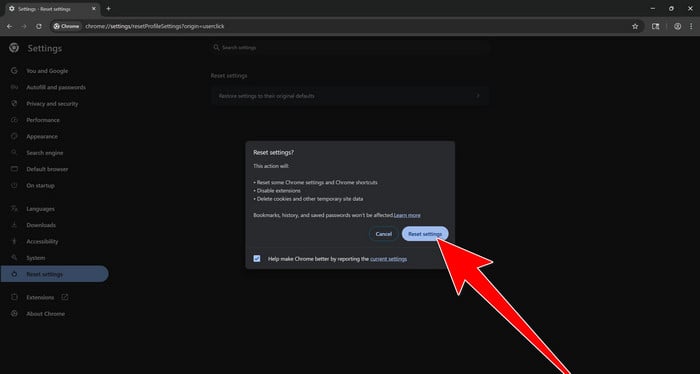
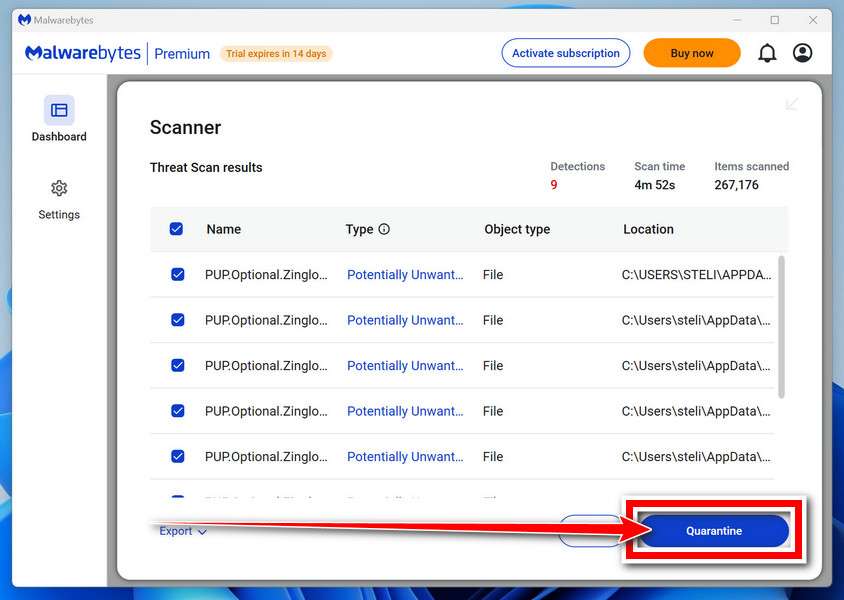
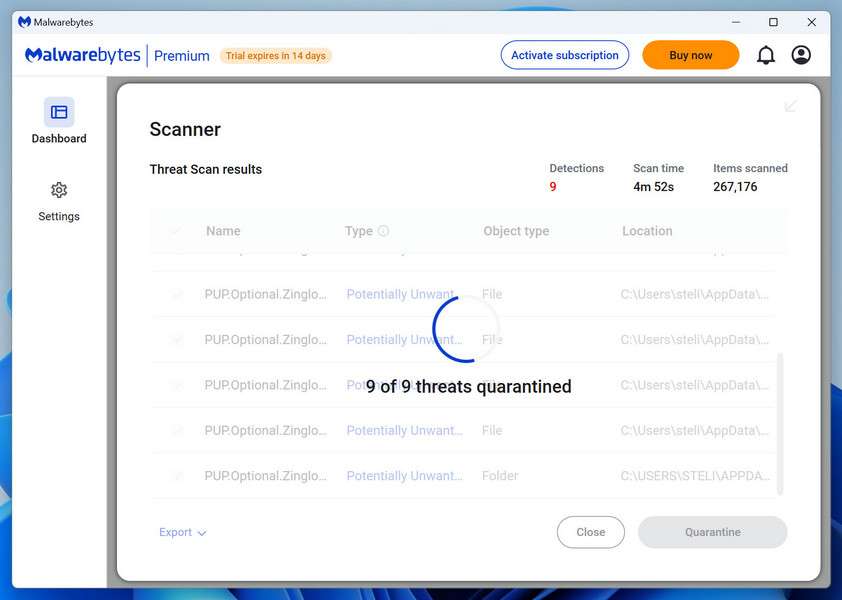
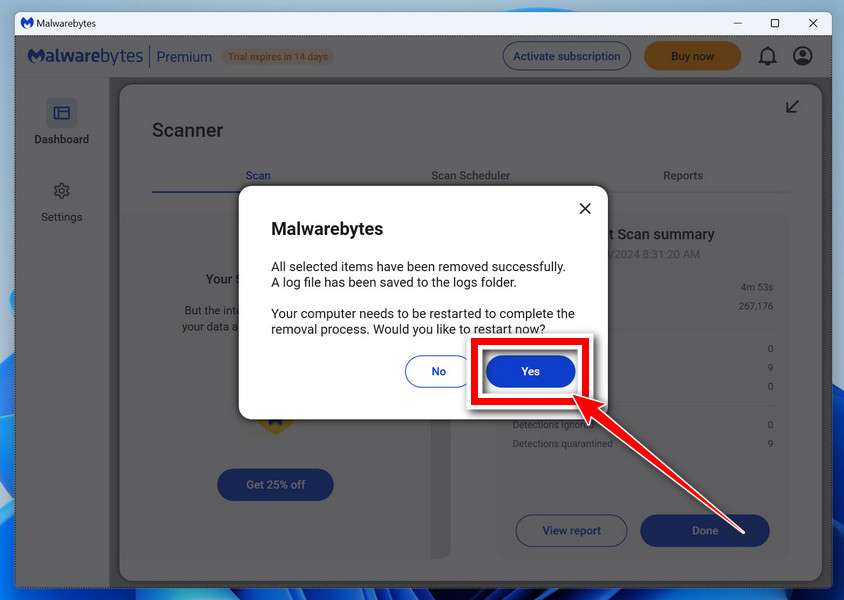
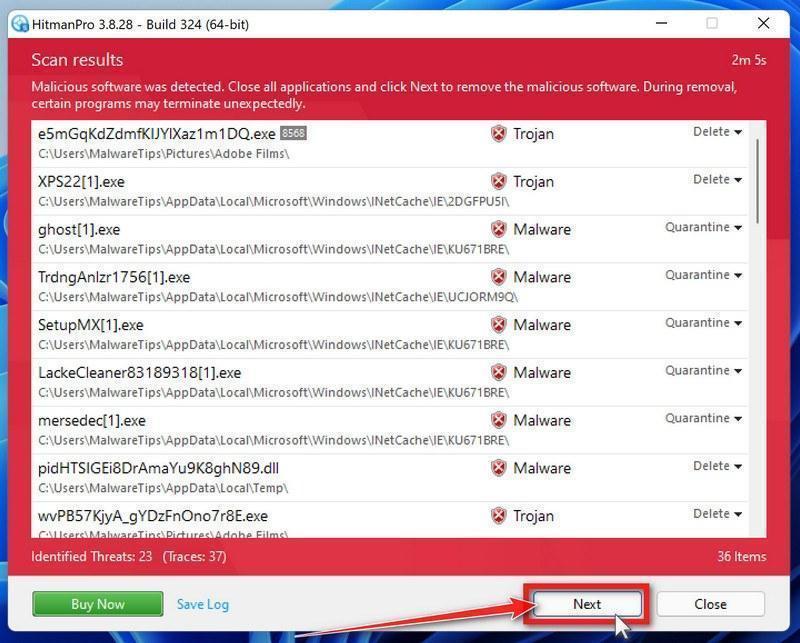
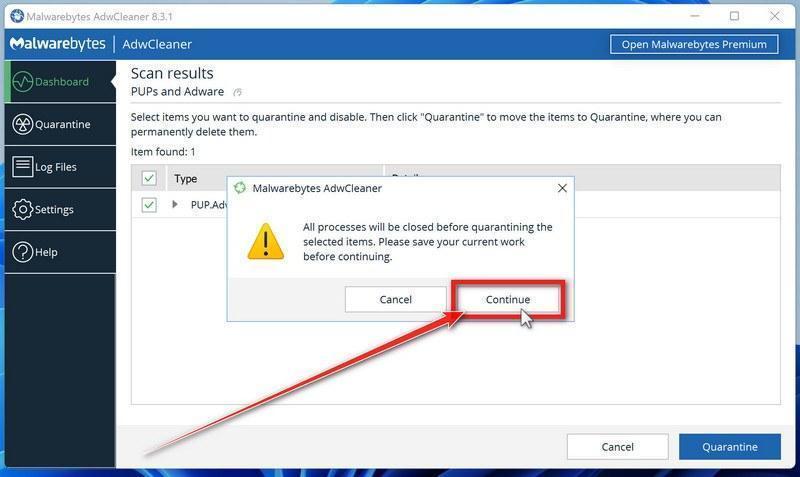
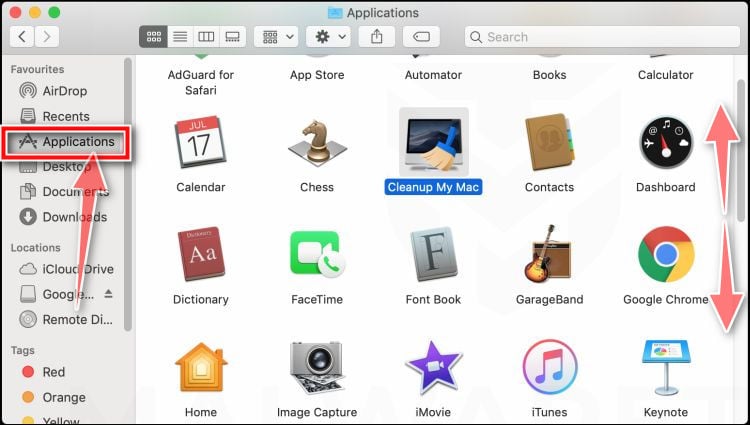
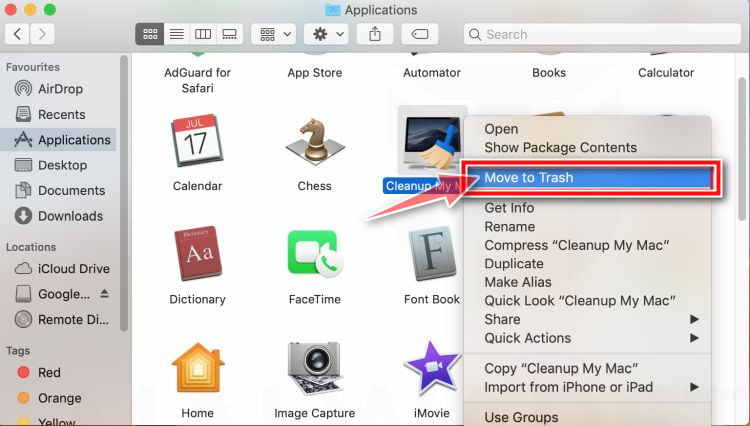
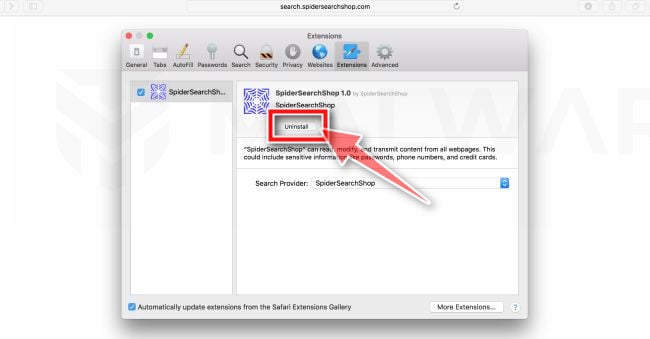
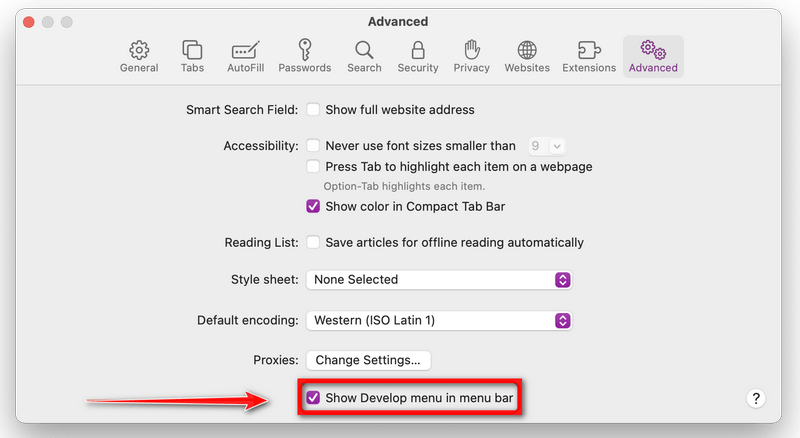
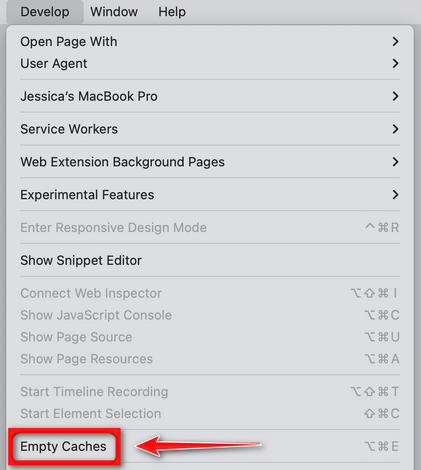
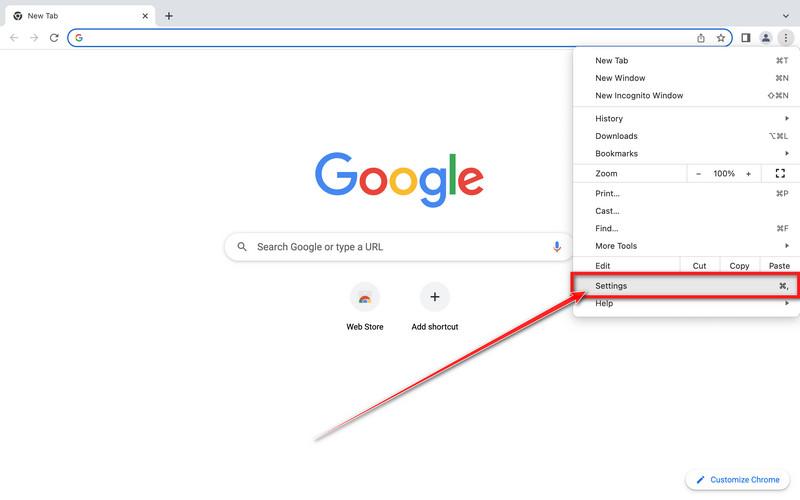
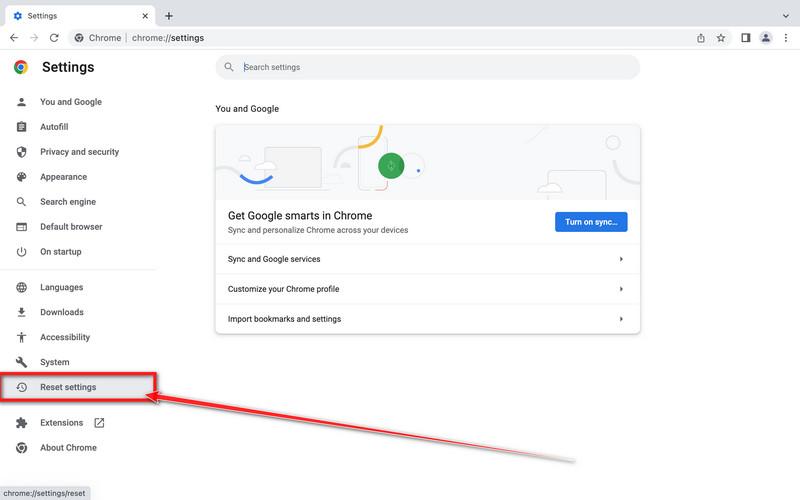
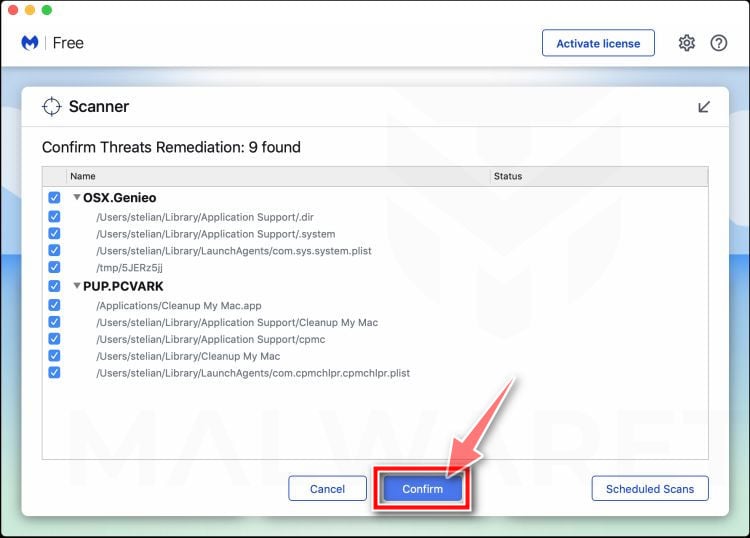
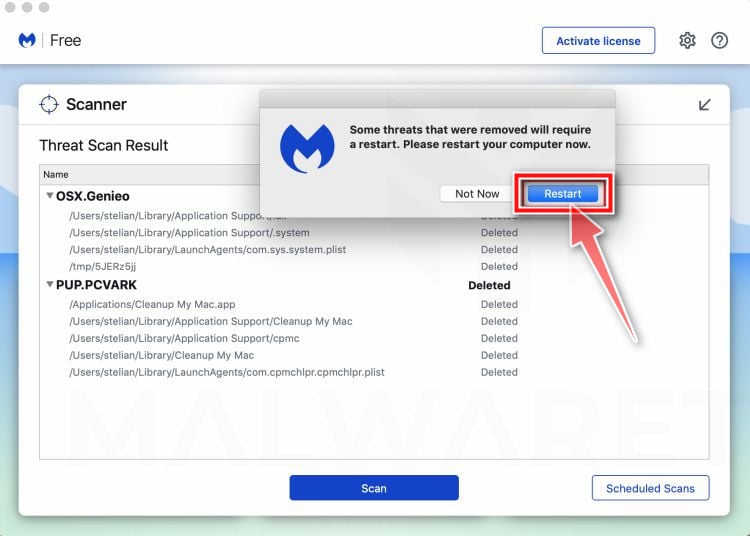
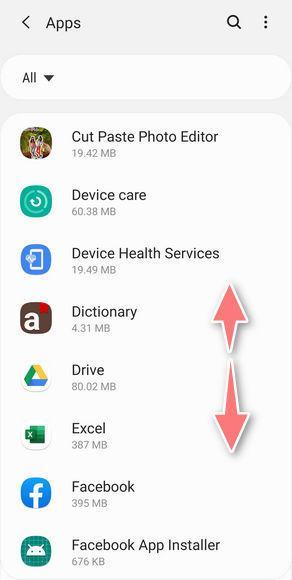
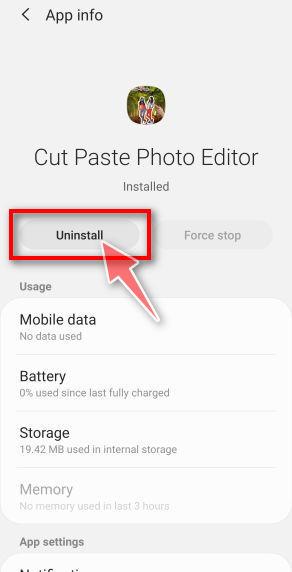
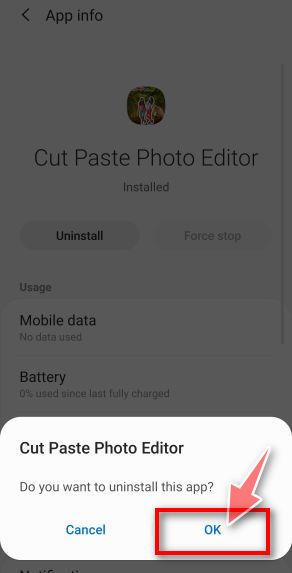
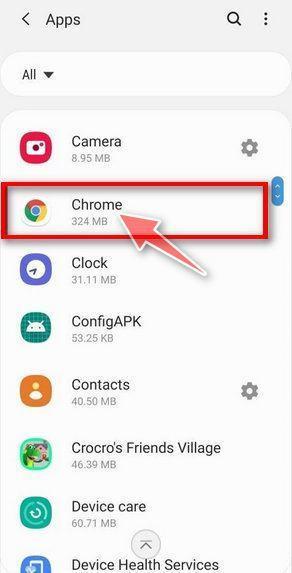
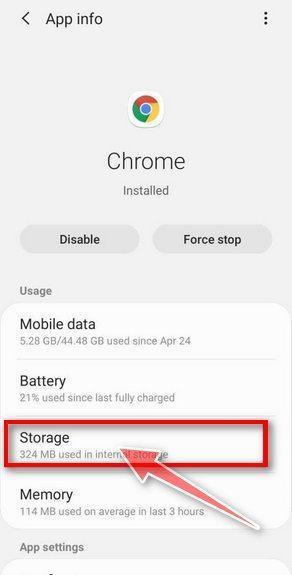
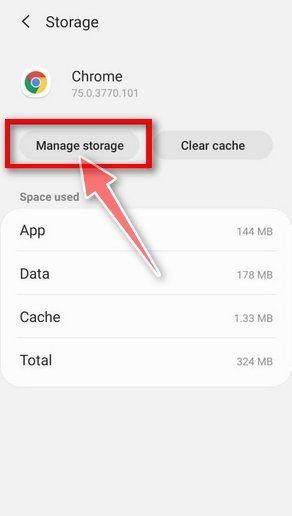
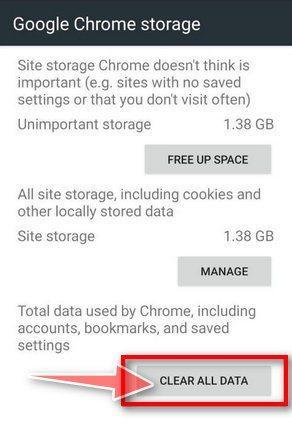
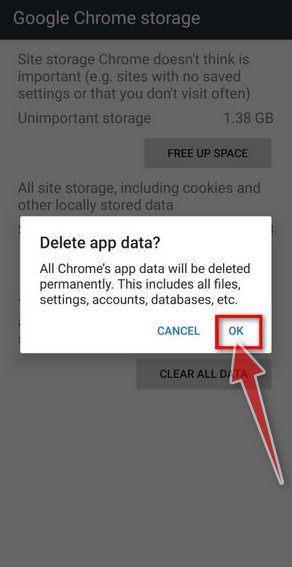
How to Remove Unwanted Apps and Malware
If you have accidentally downloaded unwanted programs or malware from a pop-up scam, you can find below a full malware removal guide.
Please perform all the steps in the correct order. If you have any questions or doubts at any point, stop and ask for our assistance.
 Remove Unwanted Apps and Malware from Windows
Remove Unwanted Apps and Malware from Windows-
 Remove Unwanted Apps and Malware from Mac
Remove Unwanted Apps and Malware from Mac  Remove Unwanted Apps and Malware from Android
Remove Unwanted Apps and Malware from Android-
 Remove Unwanted Apps and Malware from iPhone and iPad
Remove Unwanted Apps and Malware from iPhone and iPad
How to Protect Yourself from Tech Support Scams
Here are some key tips to avoid becoming the victim of a tech support scam:
Never Give Remote Access Unless You Initiated Contact
Only allow remote software installation if you contacted a verified tech support provider directly. Never grant access just because a cold caller claims it’s needed.
Don’t Rely on Caller ID
Scammers spoof legitimate business numbers easily. Independently look up and call back the company yourself for verification.
Keep Software Updated
Always apply the latest security patches and software updates. Scammers exploit outdated, vulnerable systems. Keeping software updated eliminates many of these vulnerabilities.
Use Robust Antivirus and Firewall Software
Use reputable endpoint security software like Avast, Malwarebytes, and Windows Defender to block and detect malware, spyware, and other malicious tools used by scammers.
Back Up Your Data
Maintain backups of critical data either locally or in the cloud. This gives you leverage if a scammer encrypts files for ransom. You can restore from accessible backups rather than paying the ransom.
Don’t Install Software from Unknown Sites
Get programs directly from official developer sites only. Bundled malware from unofficial sites leads to many scam calls.
Secure All Accounts with Strong Passwords
Use strong, unique passwords for all accounts. This prevents scammers that have remote accessed your device from compromising your online accounts easily.
Beware of Cold Calls, Pop-ups and Unsolicited Emails
Disconnect from any unsolicited call. Close out pop-ups using Task Manager, not the built-in close buttons. Avoid clicking links in suspicious emails.
Trust Your Instincts
If something seems suspicious, it probably is. Stick to your gut feeling and never provide info or access to unverified individuals that contact you first.
Frequently Asked Questions About Tech Support Scams
Tech support scams are on the rise globally, tricking unsuspecting victims into paying for useless services or software. Read on for answers to commonly asked questions about identifying and avoiding these fraudulent schemes.
What is a tech support scam?
A tech support scam refers to an unethical scheme where scammers contact victims while impersonating technology support teams from Microsoft, Apple or other major brands. The scammers will falsely claim that the target’s computer is infected with malware, viruses or other security issues. They then pressure the victim to pay for expensive but useless services or software by the scammers that supposedly will fix the made-up problems.
How do tech support scams work?
These scams typically start with a phone call, pop-up ad or email to the victim from scammers posing as support staff from a trusted tech company. The scammers will say they detected compromised files, malware infections or other falsified issues on the target’s computer or device. They leverage urgency, doubt and fear to fool victims into purchasing their useless repair services or overpriced antivirus software.
What are examples of issues scammers claim to find?
Common fake issues cited by scammers include malware infection, ransomware activity, suspicious IP addresses, system file corruption, blacklisted license keys, hacking tools, and expired security suite licenses. The scammers make up elaborate stories citing technical details to sound more convincing.
What is the scammer’s end goal?
The scammer’s sole goal is to get victims to pay exorbitant fees for unnecessary technical support services, phony diagnostic tests or overpriced security software that will supposedly fix the non-existent issues they claimed to uncover.
Do tech support scammers ever install real malware?
In some cases, yes. If scammers gain remote access to a victim’s computer, they may covertly install genuine hacking tools, malware or other malicious software. This allows them to then call back citing even more severe infections that command even higher service fees.
What are signs of a tech support scam?
Clues include unsolicited calls, exaggerate claims of compromise, urgent high-pressure tactics, requests for remote access, demands for upfront payment, refusing other opinions, spoofing legitimate company numbers, or refusing to provide detailed contact info.
What should I do if I receive a tech support call?
Hang up immediately if the call seems suspicious. Look up the company’s number independently and call back to verify if needed. Never provide personal information or payments to unsolicited callers.
What should I do if I already paid a scammer?
Contact your bank or credit card company to halt payments or reverse charges if possible. Change all account passwords accessed during the scam. Scan your computer for malware using legitimate antivirus software like Malwarebytes or Windows Defender. File detailed fraud reports with authorities.
How can I avoid tech support scams in the future?
Block suspicious numbers, never give remote access to unverified callers, use strong passwords, keep software updated, use secure browsers, learn to identify social engineering tactics, and don’t trust unsolicited contacts claiming you have compromises or viruses.
What happens if I ignore the scammer’s call?
Nothing. The scammers cannot do anything to you or your device if you hang up and block their number. All their claims are outright lies simply meant to scare and manipulate you. Your device is likely perfectly safe.
This covers the key questions and answers regarding the nature of tech support scams, how to identify them, and steps to take to avoid falling victim. Remember to remain vigilant of these scammers and their constantly evolving fraudulent tactics targeting unsuspecting users.
The Bottom Line
Tech support scams rely on trickery and deception to extort money from unsuspecting victims. But armed with the right knowledge, these scams can be easily identified and avoided. Remember to never trust unsolicited calls or messages, verify things independently, avoid enabling remote access for cold callers, and keep software secured and updated.
Do not engage with suspicious callers or assume they are telling the truth if you did not contact them first. Take preventative measures like stronger passwords and updated software. Finally, spread awareness about the latest scam tactics you encounter to help protect others from falling victim. Staying vigilant, securing your systems properly, and not trusting unverified calls are the keys to avoiding tech support scams entirely.