Apple devices and services are used by millions worldwide. This makes Apple users prime targets for cybercriminals running phishing scams aimed at stealing personal data. One common scam is the “Your Apple ID Has Been Suspended” phishing email.
This fraudulent email claims your Apple ID has been suspended to trick you into providing login credentials or sensitive information. If you receive a suspicious email like this, it’s best to ignore it completely. However, you should understand how this scam works so you can stay secure.
Overview of the Apple ID Suspended Scam
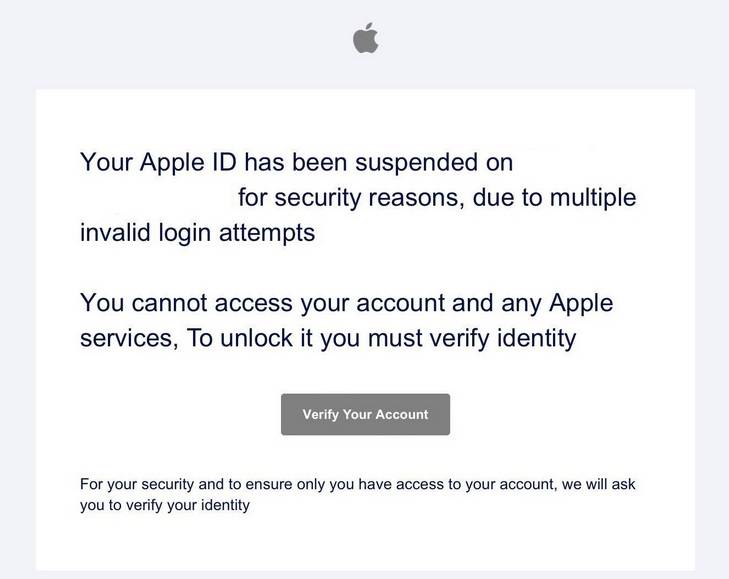
The “Your Apple ID Has Been Suspended” scam uses fake emails pretending to be from Apple Support. The email claims your access has been suspended due to “unusual activity” as a security precaution.
It states you cannot access your account or Apple services until you verify your identity. There is usually a link provided to a fake Apple site asking you to enter your username, password and further personal details to reactivate your account.
In reality, this is a phishing scam to harvest login credentials and personal information. Apple would never suspend your account without notice then send an email asking you to verify your identity using an external link.
The scam email is designed to trick users into urgently providing their Apple ID password and other info to regain access before it is deactivated. If entered on the phishing site, these details are stolen by cybercriminals rather than reaching Apple.
Some red flags indicating the “Apple ID Suspended” email is a scam:
- Apple would never notify you like this over email. Legitimate notices are within your Apple ID account.
- Spelling errors, strange addresses and poor grammar indicate the email is not authentic.
- Random suspension warnings with no prior notification from Apple are suspicious.
- Requests for sensitive information via email should always be treated cautiously.
- Links in unsolicited emails often direct to phishing sites to harvest data.
Understanding phishing techniques used in the “Apple ID Suspended” scam helps identify and avoid this attack to keep your information safe. Scrutinize unsolicited emails supposedly from Apple to protect against fraud.
How the Apple ID Suspended Scam Works
Scammers use deceptive techniques and imitation sites to make the “Apple ID Suspended” phishing scam seem convincing. Knowing how it works helps identify risks and stay secure.
Crafting a Deceptive Phishing Email
The first step in the scam is crafting an email that appears to come from Apple Support. The sender, subject line and content are designed to trick recipients.
The subject will be something like “Your Apple ID Has Been Suspended” to grab attention. The sender email often spoofs an Apple address.
Within the email, the scammer explains your access has been “suspended due to recent unusual activity”. This creates fear of losing account access. A link is provided to immediately “verify your identity” to regain access before deactivation.
These tactics pressure recipients into urgently clicking the link to secure their account without considering the email’s legitimacy. But Apple would only notify you within your Apple ID account, not via external emails.
Directing Victims to Fraudulent Sites
The link in the email directs to a fake Apple account management portal impersonating the real site. The page mimics Apple’s design and account security flows.
You are prompted to enter your Apple ID and password to “reactivate your account”. In reality, this captures your credentials for malicious use rather than restoring your access.
Scammers may even replicate Apple’s identity verification steps to gather more personal information they can use to access your accounts and commit identity fraud.
Stealing Apple ID Credentials and Personal Data
When victims enter their Apple ID password and other personal information, the scammers capture this data. They now possess your username and password.
Accessing your real Apple account allows scammers to view personal information, files, photos, financial data and more. They can steal information, make purchases and access linked services.
Beyond just account credentials, further personal information provided to the phishing site equips scammers for identity theft and account recovery. Details like addresses and birthdays have extensive malicious use.
Using Stolen Data in Further Attacks
With your Apple ID credentials and personal information, scammers can launch more extensive attacks beyond your Apple account.
Your email and password may be tested against other popular sites you use, looking to access more accounts. Additional info helps scammers impersonate you and reset account passwords.
Stolen data may also be sold online to other cybercriminals, fueling widespread identity fraud through multiple future attacks. Your information could end up powering extensive cybercrime.
Avoiding engagement with phishing websites stops this dangerous chain reaction where initial data theft enables an expanding sequence of account breaches and identity fraud.
What to Do If You Are a Victim of This Scam
If you suspect you have fallen for the “Apple ID Suspended” or any similar phishing attack, take urgent steps to secure accounts and limit damages.
Step 1: Reset your Apple ID Password
If you entered your Apple password on a phishing site, change it immediately. Reset your password directly through Apple’s portal so scammers can no longer access your account. Create a new, strong password.
Step 2: Review Recently Used Devices
Check your Apple account for any recently used devices you don’t recognize that may indicate scammers accessing your account. Revoke suspicious sessions and logout everywhere to stop misuse.
Step 3: Monitor Account Activity
Look for any unauthorized changes to your Apple account details, files, data, or settings that may signal fraudulent access. Review transaction histories for unknown purchases.
Step 4: Contact Apple Support
Inform Apple you were compromised by phishing so they can secure your account. Apple can implement enhanced security measures and help identify any suspicious account activity.
Step 5: Reset Linked Account Passwords
If your Apple ID links to any other services like iCloud or iTunes, change these account passwords too in case scammers have accessed these. Review thoroughly for any unauthorized activity.
Step 6: Beware Repeat Scams
Be cautious of further phishing scams aimed at you now that scammers know you are vulnerable. Never provide information or account access unless 100% verified as Apple.
Step 7: Monitor for Identity Fraud
Check your credit reports and accounts closely for signs of misuse of stolen personal data. Report any fraudulent activity immediately to limit damages from identity theft.
Acting quickly if you have fallen victim stops your data being misused further and limits the account access scammers have gained. Resetting passwords, contacting Apple and monitoring account use are essential steps.
Apple ID Suspended Frequently Asked Questions
How can I tell if an Apple ID suspended email is legitimate?
Apple will never contact you by email about account suspensions. Any real notices would appear securely within your Apple ID account portal. Emails stating your account is suspended are always phishing scams.
What should I do if I entered my password on the phishing site?
Immediately change your Apple ID password so scammers no longer have access. Review your account activity and contact Apple Support for assistance securing your account and assessing any unauthorized changes.
What damage can scammers do with my Apple ID password?
Scammers can access your account data, files, photos, financial information and make unauthorized purchases. They may also gain access to linked services like iCloud. Promptly changing your password limits the risk.
Are there any valid reasons Apple might suspend my account?
Apple may suspend access to your account if very suspicious activity is detected, like logins from multiple unknown locations. But you would receive notices within your Apple ID first, not via external email.
Should I click the link in the email to verify my identity?
No, the link goes to a fake phishing site to steal your data. Apple would never verify your identity this way. Contact Apple independently to check any account suspension notifications.
How can I improve my Apple ID security after a phishing scam?
Use a unique, complex password and set up two-factor authentication. Be very wary of further phishing attempts asking for account access or personal data. Never provide information without verifying the source.
Who can help me secure my account after falling for this scam?
Contact Apple Support right away. They can help you reset your password, review account activity for unauthorized changes, enhance security measures and minimize damages from any fraudulent access.
Conclusion
The “Apple ID Suspended” scam is a deceptive phishing technique exploiting fear of losing account access to steal personal data. Understanding common phishing tactics allows Apple users to stay secure against this and similar attacks.
Scrutinize the source of all emails regarding account security issues rather than blindly clicking links or providing information. Legitimate Apple notifications will only ever take place within official Apple systems, not via external emails.
If you have fallen victim, take urgent steps like resetting your password, revoking unauthorized access, contacting Apple Support and monitoring for misuse. Quick action is key to limiting damages and preventing extensive identity fraud through your stolen information.
Stay vigilant against phishing ploys targeting your personal data and use unique passwords for all accounts. Never provide information unless 100% sure of the source. Being cautious online helps proactively protect against attacks like the “Apple ID Suspended” scam.


![Remove HomeFindHub.com Redirect [Virus Removal Guide] 10 1 1](https://malwaretips.com/blogs/wp-content/uploads/2023/10/1-1-290x290.jpg)