Have you ever suddenly been flooded by prompts to reset your Apple ID password out of the blue? You grab your iPhone only to find it useless, overwhelmed by a cascade of system notifications you didn’t initiate. Before you can make sense of what’s happening, your phone rings. The caller ID says “Apple Support,” and they claim to see malicious activity on your account. If you don’t act quickly, your data may be at risk…
This is the opening salvo in an intricate scam that’s leaving Apple device owners scrambling to protect their personal information. By bombarding targets with password reset prompts, the attackers aim to incite panic. Then posing as Apple support, they phish for credentials that grant full access to accounts.
It’s a social engineering scheme requiring patience and technical sophistication. But as data breaches proliferate, scammers now have more of users’ information to leverage in personalized attacks. For Apple customers increasingly reliant on their devices, this scam offers a case study in how vigilance is required to keep our digital lives secure.
Scam Overview
A concerning new phishing scam targeting Apple device users demonstrates the elaborate lengths fraudsters will go to in order to gain access to personal information and accounts. Victims report being bombarded by countless password reset prompts that essentially lock them out of their iPhones and other Apple devices. Unable to use their phones, the targets then receive calls from scammers posing as Apple Support personnel, claiming to have detected suspicious activity on the user’s account.
This social engineering ruse aims to trick users into providing sensitive account details and verification codes, which allows the attackers to seize control of the target’s Apple ID, contacts, photos, and more.
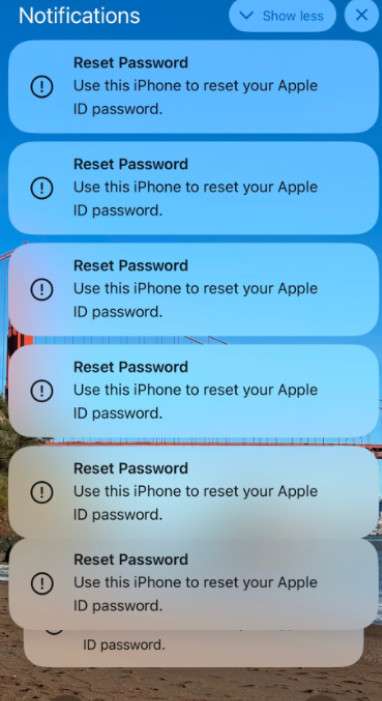
By abusing weaknesses in Apple’s password recovery systems, the fraudsters are able to spam endless password reset confirmations to all of the target’s connected devices. The notifications appear system-generated, lending legitimacy to the scam. Some victims reported receiving over 100 prompts in a short period, overwhelming their iPhones and Apple Watches with popups demanding authentication.
With the user’s devices rendered temporarily useless by the password reset bombardment, the scammers initiate an inbound call while spoofing Apple’s official customer support number. Posing as Apple support reps, they pretend to have identified compromised account activity and claim the target’s data is at risk. This establishes a false sense of urgency and trust, causing the target to be more likely to comply with requests for sensitive information.
In some cases, the fraudsters had acquired personal details about the victim, like an alias or educational background, to further convince targets of their legitimacy during calls. If the user provides a one-time passcode or Apple ID password, the scammers can gain full access to their iCloud account, contacts, photos, messages, and financial information.
Security experts believe the scammers are exploiting weaknesses in Apple’s password recovery protections to spam targets despite security limits. The ability to rapid-fire password reset prompts suggests they have found a way to bypass Apple’s rate-limiting systems, which are designed to prevent such bombardments.
While Apple works to patch any vulnerabilities, users should exercise extreme caution if they receive unsolicited calls appearing to be from Apple Support. Never share one-time passcodes or account passwords over the phone, even if the caller seems to have your personal information. Hang up and contact Apple directly to verify any account security concerns.
Enabling two-factor authentication on your Apple ID also helps protect against phishing attempts. Regularly audit connected devices and installed apps to ensure nothing unfamiliar has been added. And use strong, unique passwords to prevent wider access if credentials are compromised.
No single security precaution is foolproof against increasingly sophisticated phishing tactics. But combining vigilance with protective measures will help Apple users guard against these elaborate social engineering scams aiming to plunder our digital identities.
Inside the Apple ID Password Reset Scam
The Apple password reset scam demonstrates how far attackers will go to convince targets to hand over that one piece of data that unlocks an account. For Apple users, a six-digit verification code can act as a skeleton key to their digital identity.
To phish these codes, the scammers first overload victims with system password change requests. With the target’s Apple devices rendered temporarily useless, the attackers phone them while spoofing Apple’s caller ID. Pretending account security is under threat, they offer to protect the user from this “attack.”
This priming is an act of social engineering that exploits trust in Apple’s systems. The criminals bank on users being so confused by the password spam, a call from “Apple Support” is welcomed. Let’s break down each step of how this scam unravels.
Step 1: Flooding Targets with Password Change Requests
The first phase of the attack involves completely locking users out of their Apple devices. The scammers accomplish this by abusing Apple’s password recovery systems to spam password change approvals.
They start by inputting the target’s Apple ID email address or phone number into Apple’s password reset page. This confirms that account exists, displaying the last two digits of the associated phone number.
After guessing the remaining digits, the attackers can submit repeated password reset requests. Each one generates a system popup on every iPhone, iPad, Mac and Apple Watch linked to the Apple ID.
With some users reporting over 100 notifications, this bombardment essentially renders the target’s devices unusable. They cannot be accessed until each alert is dismissed individually.
Step 2: Calling While Spoofing Apple Support
With the target scrambling to understand the notifications flooding their devices, the scammers initiate the next phase of psychological manipulation.
The attackers call the target from a spoofed number appearing as Apple support. They pretend to have detected compromised account activity, and claim to be helping the user resolve this “attack.”
This establishes a sense of urgency and trust, priming the target to comply with the fake support rep’s instructions. If they believe Apple is calling, they’ll be more likely to hand over sensitive information.
Step 3: Phishing for the Target’s Credentials
With the target now receptive to the call, the scammers pivot to phishing for account credentials or a one-time passcode. Providing either would grant the attackers full access to the victim’s iCloud account.
The fake support rep may claim they’ll use the code to verify the target’s identity as the account owner. Or insist Apple can remotely reset the account password if given the code.
But one-time passcodes should never be shared with anyone. And Apple would never proactively call a user to resolve account issues. Yet the target may be so overwhelmed by the password spam, they provide the scammer exactly what they’re phishing for.
The Aftermath: Ransacking Apple Accounts & Devices
Once armed with the target’s credentials or passcode, the scammers can access and plunder the victim’s Apple ID at will. Any iPhone, iPad or Mac linked to the account is now vulnerable.
The attackers can reset the account password, removing the target’s access. They can harvest personal data from iCloud like contacts, photos, email and documents. Financial info linked to the account, like stored credit cards, is also exposed.
With control of the target’s messages, email and camera roll, the potential for further extortion through sextortion emerges. The scammers can also remotely wipe devices, holding them hostage until the target pays a ransom.
What to Do if You’re Targeted by the Apple Password Reset Scam
Finding yourself suddenly locked out of your Apple account can induce panic. But there are concrete actions you can take to secure your account and devices. Here are tips if you fall prey to this scam:
- Do not provide any information to the callers. One-time passcodes should never be given out.
- Hang up and call Apple support directly. Use Apple’s official support line to discuss account lockouts.
- Change your iCloud password immediately. Do this from a trusted device if possible. Enable two-factor authentication.
- Review recent sign-in activity. Check for any unauthorized access attempts on your Apple ID account page.
- Audit connected apps and services. Look for unfamiliar apps linked to your account that may be compromised. Revoke their access.
- Enable secondary authentication methods. Add extra login verification like device-based 2FA or security keys to prevent future attacks.
- Scrutinize payment info. Remove any stored credit cards on your Apple ID that may be compromised. Watch for fraudulent charges.
- Change passwords on other accounts. If you reuse passwords, update them everywhere to block wider access.
- Contact institutions about potential identity theft. Alert credit bureaus and monitor your reports if personal information was exposed.
- Report the scam call to authorities. File a complaint with the FCC and your local law enforcement to aid investigations.
By taking quick action if your Apple account is compromised, you can limit the damage and prevent further abuse of your information. But awareness of common tactics is key to avoid becoming a victim in the first place.
How to Spot Apple Password Reset Scam Calls
Looking out for a few red flags can help Apple users identify and avoid scam callers posing as Apple support. Here are signs you may be targeted by an Apple ID password reset scam:
- You receive an onslaught of password change prompts that lock your devices.
- The caller ID seems to be from an Apple support number.
- They reference suspicious logins you haven’t noticed yourself.
- They ask for personal information like account passwords or one-time codes.
- They pressure you to act quickly or urgently provide access.
- The call originates from an overseas number if examined closely.
- You cannot call them back via an official Apple support channel.
Any unsolicited call claiming your account is under attack warrants skepticism. Remember that Apple will never proactively reach out requesting personal information or codes. When in doubt, hang up and contact Apple directly to verify any account issues.
How Apple Users Can Protect Against Password Reset Scams
While Apple cracks down on abuse of its password recovery systems, users should take measures to harden their accounts:
- Use strong, unique passwords on all accounts. Never reuse passwords.
- Enable two-factor authentication and use auto-generated app passwords.
- Limit personal info shared online or with services.
- Beware phone calls from unverified numbers. Never provide codes or account access.
- Avoid clicking password reset links in emails. Go directly to Apple’s site.
- Monitor account activity and devices for unauthorized changes.
- Update devices and apps to close security loopholes.
- Report scam calls and phishing attempts to warn others.
No single precaution is foolproof. But combining vigilance with protective measures will make you a much harder target for Apple ID scammers.
The Bottom Line
The elaborate Apple password reset scam reveals just how far social engineers will go to manipulate targets. By flooding users with system messages and posing as support reps, the attackers play on confusion and trust.
But understanding the scam blueprint enables Apple customers to spot fraudulent calls. Never provide information or verification codes over the phone, no matter how legitimate the request seems.
With our digital and device security increasingly interconnected, a single account takeover can have cascading implications. For Apple users, protecting your Apple ID should be a top priority, only rivaled by awareness of the ever-evolving tactics targeting it.
While scammers achieve success through dramatic stories, you write your own story by being an informed user. We all have a role to play in ending these attack cycles. Spreading awareness so fewer fall victim is perhaps the most meaningful action Apple customers can take today.



