Cryptocurrency and blockchain technologies have opened up new possibilities for innovation and wealth creation. However, the anonymity and irreversibility of crypto transactions have also enabled scammers to thrive. One common scam making the rounds on social media sites and spam emails is called the “Chainlink Treasury Airdrop” scam. This scam aims to trick victims into forfeiting their crypto funds and has already managed to steal millions of dollars’ worth of cryptocurrencies from unsuspecting internet users.
Overview of the Chainlink Treasury Airdrop Scam
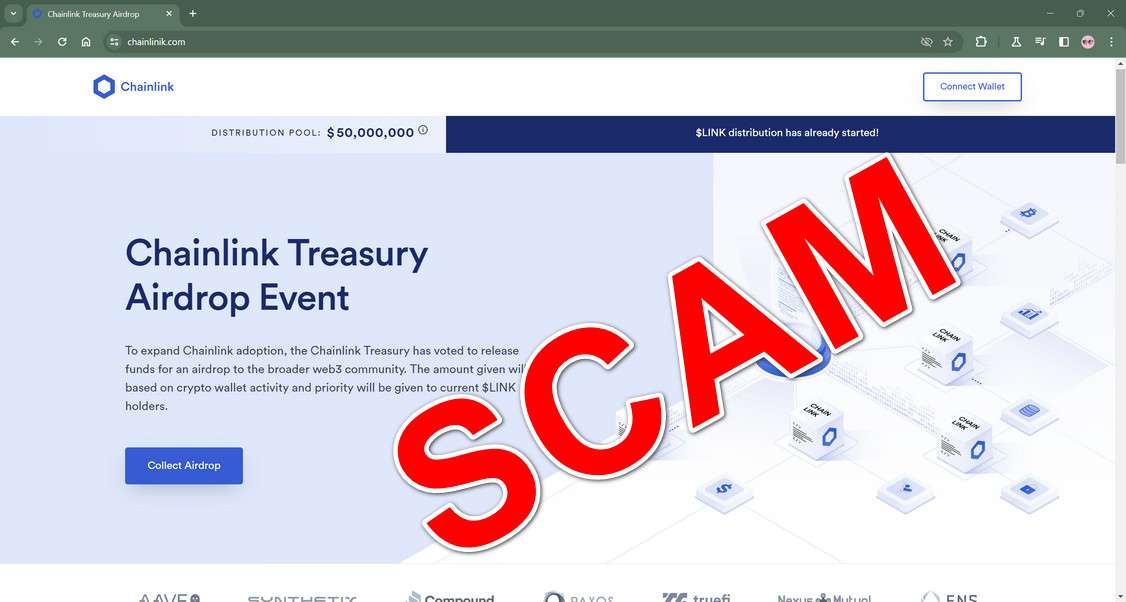
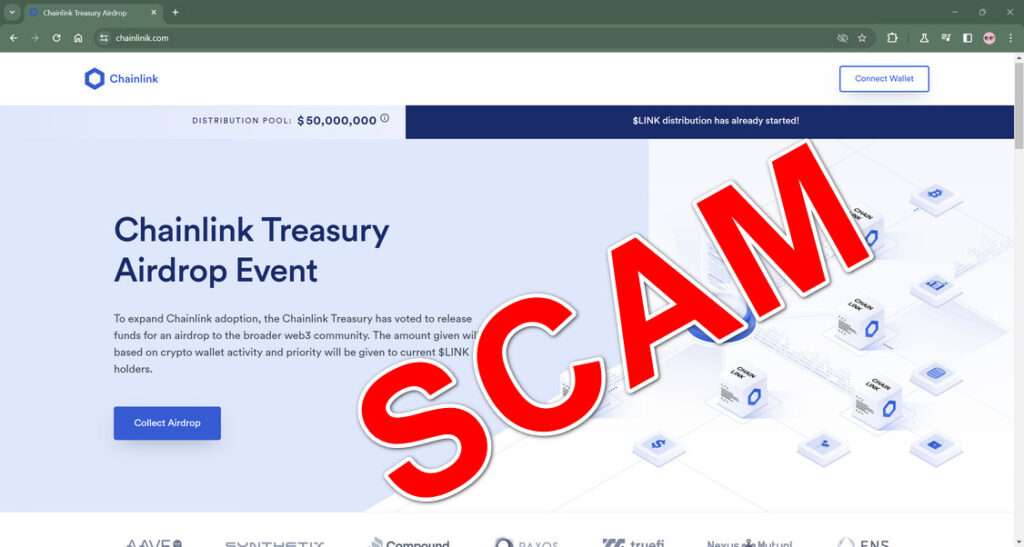
The “Chainlink Treasury Airdrop” scam advertises a fake giveaway of Chainlink’s cryptocurrency Link. It claims that Chainlink is distributing $50 million worth of Link tokens as an incentive to bolster adoption.
Scammers exploit social media sites like Facebook, Instagram, and TikTok to promote this fake airdrop, employing a technique known as malvertising. They will pay to promote posts advertising the giveaway and redirecting users to fraudulent sites. Alternatively, spam emails are used to drive traffic to the phishing sites.
The scam sites prompt visitors to connect their crypto wallets and “collect airdrop.” However, by sharing their private keys, victims grant full access and control over their wallets to the scammers, enabling them to siphon off all funds deposited. These sites are often sophisticated copies of legitimate sites (a practice known as “spoofing”), deceiving even veteran crypto users.
Once connected, a malicious smart contract will swiftly drain victims’ wallets and funnel the stolen funds into accounts controlled by the scammers—with no recourse available to recover the funds. Scammers can net millions within hours through just one such fake giveaway site.
As more novices enter the crypto space attracted by promises of wealth, a lack of technical familiarity renders many vulnerable to cons like fake airdrops. Industry safeguards are still maturing, enabling scammers to flourish across various social media services and evade timely interventions to suspend their accounts. Finally, the irreversible nature of crypto transactions presents few options to rectify fraud once funds are lost.
Let’s examine in detail exactly how scammers operate the Chainlink airdrop scam to steal crypto funds through social media and email spam outreach.
How the Chainlink Treasury Airdrop Scam Works
While tactics may vary slightly, the Chainlink airdrop scam generally employs the following blueprint on victims:
Step 1: Spreading Reach Through Spam and Malvertising
The first step for scammers is driving web traffic to their fake Chainlink giveaway sites on a mass scale. This is achieved by:
- Social Media Promotion: Scammers will pay to promote scam site links on Facebook, Instagram, and TikTok. Often these posts feature fake celebrity endorsements to appear credible. For example, a post title might read “Richard Branson Knew It! Chainlink 50 Million Airdrop.”
- Email Spam: Another avenue is bombarding inboxes with fake Chainlink newsletters announcing the airdrop. Given the costs of social promotion, spam provides a cheap method to reach more victims.
Both approaches aim to divert unsuspecting victims toward the phishing site, primed for the airdrop ruse. Promotion splits testing of messages and segments targets for optimization help scammers refine outreach. Automated bots then vastly scale the operation.
Step 2: Duping Victims with Deceptive Sites
Once the scam site receives traffic, the next step involves deceiving visitors into connecting their wallets. These phishing sites implement careful techniques to appear as legitimate giveaway portals. Tactics include:
- Spoofing: Scam sites mimic the branding, web layout and UI of actual Chainlink services to avoid suspicion. The scam wallets visually resemble authentic Chainlink wallets as well.
- Invented Claims: Official-looking language touts the “airdrop” as an “initiative by the Chainlink Treasury” seeking to “expand Chainlink adoption” through token distribution. None of this is factual.
- Scarcity Pressure: Messaging implores visitors to hurry before allocated tokens run out for heightened urgency. Countdown timers suggest dwindling availability even if tokens never existed!
- Social Proof: Fake testimonials with crypto amounts supposedly already claimed by others manufacture credibility. In reality, these are completely fabricated.
With seemingly credible interfaces and claims matched by an artificial sense of scarcity and social proof, even veteran crypto users can be deceived into connecting wallets.
Step 3: Stealing Funds Through Malicious Smart Contracts
The fatal flaw lies in inputting wallet login details. Scam sites utilize malicious smart contracts that trigger the moment a wallet connects.
The smart contract quickly scans the balance across any linked accounts like metamasks. Then in seconds it siphons off the entire sum to the scammer’s wallet. Even if the site crashes or is taken down, the theft smart contract persists on the blockchain facilitating continued drainage.
With hundreds connecting wallets daily, scammers easily net 7-figure hauls rapidly through this method. Theft amounts become limited only by the number of victims successfully deceived.
Moreover, due to crypto transaction irreversibility, victims have no path to recovery once scammed this way. Nor do law agencies possess effective legal recourse in most cases. This makes the approach incredibly lucrative for scammers.
Step 4: Cashing Out & Creating New Scams
After amassing vast sums in crypto from their scam, the final step for scammers involves cashing out into fiat currency while evading authorities. OTC brokers, offshore exchanges, money mules, and mixer services enable difficult-to-trace liquidation.
A portion of net proceeds invariably gets invested into new scams; improving technical sophistication, outreach capacity through bots/spam services, and laundering mechanisms. This enables the cycle to perpetuate diverting funds from victims to offenders.
How to Identify Fake Chainlink Airdrop Websites
With sophisticated spoofing tactics making phishing sites appear legitimate, avoiding wallet drainage requires proactive scam detection. Here are key red flags to analyze before connecting your crypto wallet anywhere:
Inspect the Website URL Carefully
Fake sites rely on typosquatting and suggestive names to ensnare victims. However, lookalike URLs give them away on close inspection:
✘ http://chainlink-airdr0p.com/
✘ http://get-chainlink.org/airdrop
✘ http://chainlinik.com
✔️ Real Chainlink Domain: https://chain.link/
The lack of the actual “chain.link” domain signals fraud. Other signs are subtle misspellings, prefixes/suffixes, and top-level domain swaps. Verify site authenticity through Chainlink’s official social media channels rather than web searches.
Compare Interface Elements Carefully
While scam sites lift the look and feel of legitimate platforms through spoofing, inconsistencies become visible on close interface comparisons:
✘ Wrong company name
✘ Different logo design/colors
✘ Different site branding style
✘ Different product photos
Cross-verify UI elements like official branding assets, colors, and imagery against Chainlink’s websites and social media profiles. For example, finding “Link Labs” referenced instead of “Chainlink” indicates a scam operation.
Check for Credible Terms of Service & Privacy Policies
Authentic services post valid legal pages to operate legally. In contrast, scams ignore this aspect:
✘ No Terms of Service document
✘ No Privacy Policy published
✘ No company address/email included
Real services link legal policies with contact details. The lack thereof signals fraudulent intent to steal funds anonymously without recourse.
Test Site Responsiveness
Professional sites offer quick customer assistance. Phishing links instead lead to:
✘ Non-working contact email
✘ Non-working contact form
✘ No social media traces
Verify site legitimacy by actually testing response channels. Unresponsive sites clearly aim only to grab your wallet keys rather than provide real services.
Staying vigilant requires going beyond cursory glance waves. Analyze each site systematically before connecting wallets anywhere online. Cross-verifying URLs, UI elements, policies, addresses, and responsiveness offers the best defense against deceptive spoofing tactics. Apply these scam detection steps routinely to avoid surprise wallet drainage!
How to Identify the Scam on Social Media
A core tactic scammers use to promote the fraudulent Chainlink airdrop links involves social media marketing. By studying their patterns on platforms like Facebook, Instagram, and TikTok, we can avoid falling into wallet drainage traps.
Spotting Scam Posts on Facebook
Facebook’s enormous user base and ad targeting presents a lucrative avenue for scammers. Some signals to recognize their scam clicks:
- Sponsored Posts: Look for posts labeled as “Sponsored” promoting improbable giveaways or urging urgent action
- Sensational Celebrity Images: Posts featuring celeb photos/logos promising free crypto are attention-grabs steering users towards phishing links
- Suspicious or Generic Page Profiles: Scam ads originate from shady pages unrelated to crypto lacking credentials
- Link Previews to Unverifiable Sites: Hover over post links to preview destination sites. Unrecognizable non-Chainlink domains should raise red flags
- Repetitive Messaging Across Pages: Similar phrasing on free Link tokens suggest copy-pasted scam bots rather than unique posts
Apply vigilance around sponsored crypto giveaways employing these types of suspicious signals. Verify poster legitimacy before clicking advertised links.
Recognizing Instagram Scam Accounts
On Instagram, fake airdrop promotions harness influencer aesthetics for credibility. Warning signs include:
- No Historical Crypto Context: Accounts suddenly pivoting to promote Link giveaways despite no prior crypto content
- Suspicious Engagement Patterns: Near-zero comments or likes on posts despite thousands of followers signals inauthentic bots or purchased accounts
- Redirecting Links in Profile: Linktree or shortly.io profile links route visitors away from Instagram onto external phishing sites
- Reposting Memes Across Accounts: Same free Link token meme reposted widely indicates coordinated scam bots rather than crypto enthusiasts
Contextless crypto giveaways from shady accounts should always warrant extra scrutiny on Instagram. Dig deeper before tapping advertised links.
Avoiding Hijacked Accounts on TikTok
On TikTok, scammers compromise legitimate profiles to broadcast scam links. Be wary if:
- Irrelevant Crypto Content Sudden Appears: Video topics pivot inexplicably from past interests like sports or fashion to crypto freebies
- Profile Behavior Shifts Abnormally: Previously consistently active accounts begin reposting randomness including phishing links
- Bio Links Get Replaced: Profile URLs get swapped subtly not directing elsewhere instead of the account’s feed
Report suspicious behavioral flip-flops signalling potential account takeovers. Avoid unfamiliar links even from known profiles until verifying intent.
The Common Scamming Playbook
While platforms and tactics vary, scam promotions follow the same formula:
- Manufactured Urgency: Impossibly large free crypto offers tied to short time windows pressure quick actions
- Social Proof: Fake comments and stats showing enormous payouts already claimed build credibility
- Clickbait: Shocking celebrity images, oversized fonts and video thumbnails capture user attention
- Masked Destinations: Shortened or redirecting links prevent vetting landing sites
Learn to recognize these manipulative patterns across any social media crypto promotion. Contextless urgency and unbelievable giveaways invariably steer towards phishing endgoals. Stay cautious sharing data or clicking such links.
What To Do If You Have Fallen Victim to the Scam
If you connected your crypto wallet and then witnessed funds suddenly disappearing, you have likely fallen prey to the Chainlink airdrop scam. Unfortunately, given the irreversible nature of blockchain transactions, recovery chances remain extremely slim. But certain measures should still be undertaken right away:
Step 1: Notify Relevant Parties Immediately
- Wallet Provider: Inform your wallet provider like Metamask right away about unauthorized account access. They likely cannot reverse transactions but can freeze the account to prevent further compromise.
- Exchange: If you held funds on a centralized exchange, notify their fraud team citing unauthorized access leading to asset theft. Exchanges can potentially trace, flag or freeze transfers.
- Bank: Alert your bank if any linking exists between your wallet or exchange account to initiate fraud protocols on associated card or bank account transactions.
- Law Agencies: File reports with cybercrime authorities in your jurisdiction like the FBI’s Internet Crime Complaint Center detailing scam specifics. Global cooperation traces funds or issues warnings on larger scams.
Step 2: Gather Evidence on the Scam Approach Deployed
Collecting scam details aids reporting and investigations:
- Website: Record the fake site URL accessed along with screenshots evidencing specifics like branding, messaging and wallet connection prompts.
- Promotion: Save copies of social media posts, YouTube videos or spam emails that led to their site. Details like dates, accounts, content and CTAs provide useful indicators.
- Wallet Logs: Check wallet logs that trace transaction timestamps, wallet IDs and cryptocurrency amounts stolen. Flag these with law agencies.
- Smart Contract: The address of the theft enabling smart contract can indicate larger scam operations for authorities. On Ethereum chains this is traceable on blockchain explorers by connecting the dots.
Step 3: Educate Yourself and Others on Avoiding Future Crypto Scams
While tragic, victimization often spurs learning to identify the scam red flags for the future. Study legitimate crypto project communications to distinguish credible giveaways from cunning fakes. Enable protective measures on wallet apps like login request alerts. Report and flag suspicious posts seen on social media to the platforms. Spread awareness among friends and communities vulnerable to crypto fraud. Let your experience protect fellow users, even if unable to recover own funds.
Frequently Asked Questions on the Chainlink Scam
As crypto scams evolve in complexity, many newcomers to the web3 space understandably have pressing questions. This FAQ covers key aspects of the “Chainlink Treasury Airdrop” phishing scam to aid awareness and prevention across the crypto community.
What is the Fake Chainlink Airdrop Scam?
The Chainlink airdrop scam promotes a fake cryptocurrency giveaway of Chainlink’s LINK tokens worth $50 million. By advertising this on social media and emails, scammers direct victims to fraudulent sites prompting wallet connections to “claim airdrop”. Upon inputting private keys, malicious smart contracts instantly drain victims’ crypto funds, stealing millions overall.
How Do Scammers Spread the Fake Airdrop Links?
Scammers rely on two primary outreach vectors to promote the scam sites:
- Social media posts on Facebook, Instagram and TikTok employing fake celebrity images and endorsements. These aim to boost site traffic rapidly through paid promotion.
- Spam email campaigns pretending official Chainlink newsletters announcing the airdrop initiative. Mass blasts help spread the scam website URLs cheaper.
For both channels extensive use of bots, segments targeting and splits testing optimization expands exposure to potential victims.
How Can One Identify the Phishing Sites as Fake?
While scam sites employ clever spoofing of Chainlink’s visual identity through branding, UI and content, key red flags signal their illegitimacy:
- Incorrect domain names with typos or suffix/prefix augmentations
- User interface discrepancies in logos, color schemes and product photos
- Lack of terms, privacy, addresses signaling fraudulent intent
- Non-responsiveness to email contacts and info requests
See the guide on identifying fake Chainlink sites for more scam detection tips.
What Should I Do If I Shared Wallet Keys on the Scam Site?
If you connected your wallet and witnessed unauthorized drainage of crypto assets, take these steps immediately:
- Notify your wallet provider, crypto exchange, bank and law agencies on the fraud incident
- Gather scam site specifics like screenshots and promotion material as investigation evidence
- Study legitimate project communications to avoid future deception
- Spread warnings in crypto communities to protect other newcomers
Unfortunately fund recovery remains very unlikely due to blockchain transaction irreversibility.
How Can the Crypto Space Combat Such Scams at Scale?
With crypto adoption surging globally, user education represents the first line of defense against phishing threats today. But maturing institutional safeguards should also bolster protections:
- Tighter regulation policies governing crypto promotion channels
- Faster response protocols by social media platforms
- Blockchain surveillance mechanisms by exchanges
- Mandatory wallet security features like transaction validation
- International collaboration in investigating fraud networks
With prudent vigilance and steadily improving security infrastructure, the crypto ecosystem can structurally minimize scam risks for all users in the coming years.
Stay alert and inform yourself on common crypto phishing techniques. This offers the best guard against cunning social engineering exploits seeking to capitalize on blockchain anonymity today. Verify every site and offer carefully before interacting with your wallet online.
The Bottom Line
The “Chainlink Treasury Airdrop” scam offers a cautionary tale on the prevalence and scale of crypto fraud exploiting decentralization anonymity. Positing as a promotional crypto giveaway, clever social engineering dupes even experienced investors into forfeiting wallet access. A subsequent complex cascade drains linked accounts rapidly.
If complacent, anyone can fall prey, by overlooking seemingly minor website discrepancies that betray sophisticated scam operations. The irreversible crypto transaction model further compounds issues by preventing recovery and limiting legal remedies. For the unwary, such scams continue inflicting heavy monetary losses.
Yet with prudent awareness and safety measures individuals can equip themselves to sidestep such crypto scams. Caution against unbelievable offers, extensive wallet protections, social media literacy and smart contract scrutiny remain vital. As crypto adoption spreads, users must inform themselves on scam techniques rather than rely solely on maturing institutional safeguards. Staying vigilant and skeptical offers the best protection today against fraud in the decentralized finance realm.