In the world of cryptocurrency, scams are unfortunately all too common. One such scam that has been preying on victims is a fake cryptocurrency recovery service called CoinTrieve. At first glance, CoinTrieve appears to be a legitimate company that helps victims recover lost or stolen cryptocurrency funds. However, further investigation reveals that CoinTrieve is nothing more than an elaborate ruse designed to steal even more money from unsuspecting victims.
This article will take an in-depth look at how the CoinTrieve scam operates, provide tips on how to avoid falling victim, and give guidance on what to do if you have already been scammed. With cryptocurrency adoption on the rise, it is crucial that crypto users arm themselves with knowledge to detect and resist scams like CoinTrieve.
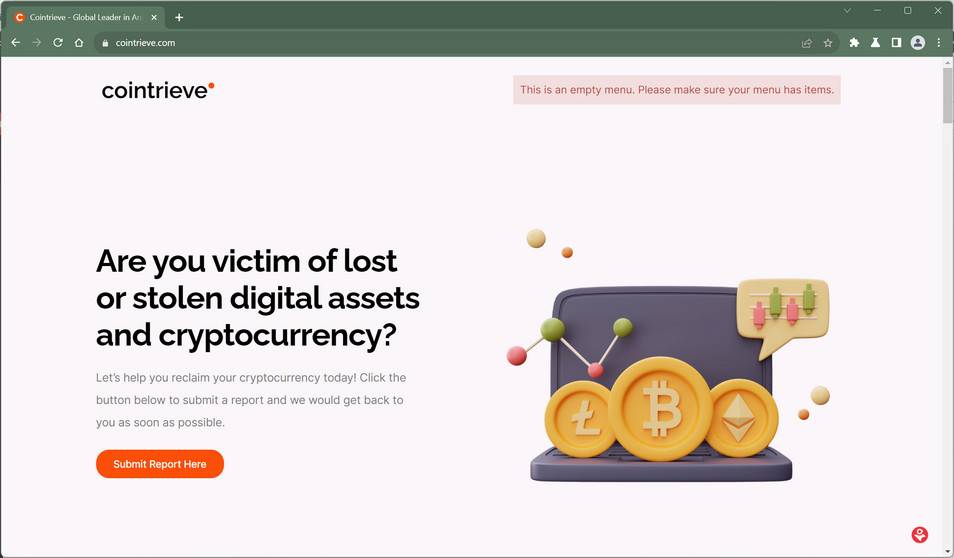
Overview of the CoinTrieve Scam
CoinTrieve masquerades as a cryptocurrency recovery service, claiming to help victims recover funds lost due to theft or security mistakes. Scammers behind CoinTrieve create a professional looking website and market themselves as a legitimate company.
The CoinTrieve website states:
“Are you victim of lost or stolen digital assets and cryptocurrency? Let’s help you reclaim your cryptocurrency today! Click the button below to submit a report and we would get back to you as soon as possible.”
This promise of recovering lost crypto funds is understandably appealing to victims desperate to get their money back. However, CoinTrieve is simply leveraging that desperation to set up an elaborate scam designed to steal even more money.
How the CoinTrieve Scammers Operate
The fraudsters behind CoinTrieve employ clever psychological tactics and socially engineer victims throughout the scam process. This is how the scam typically plays out:
- Initial Contact: Victims will fill out a form on the CoinTrieve website providing details on their lost crypto funds. CoinTrieve then reaches out claiming they can recover the assets.
- Gaining Trust: CoinTrieve will appear professional and eager to help. They ask questions to better understand the victim’s case. This makes the victim believe recovery is possible.
- Payment Request: Once the victim’s trust is gained, CoinTrieve states they’ve “approved the case” but require an upfront fee before starting recovery work. This fee is falsely portrayed as good-faith money that will go towards the investigation and recovery process.
- Stalling Tactics: After receiving the fee, CoinTrieve will reassure the victim they are actively working on the case. But over time, delays and excuses will be given for why the funds can’t be returned yet. The scammers will keep stringing the victim along with false promises.
- Disappearance: When the victim catches on that they are being scammed and tries to recoup the fee paid, CoinTrieve becomes unresponsive. They eventually disappear with the money, leaving the victim with no recovered crypto and now out even more funds.
This sophisticated social engineering is what makes CoinTrieve so dangerous. The scammers are masters at manipulating psychology to slowly build trust before dropping the payment demand. Victims don’t realize it’s a scam until it’s too late.
Red Flags of the CoinTrieve Scam
While cleverly executed, there are red flags that can help uncover the CoinTrieve scam:
- Upfront fees – Legitimate crypto recovery services typically work on contingency, only collecting a percentage after funds are recovered. The upfront fee requirement is a huge red flag.
- Vague recovery promises – CoinTrieve gives vague assurances that lost crypto can be recovered but provides no details on how. Legitimate services clearly explain the recovery process.
- No physical location – Check the CoinTrieve website and you won’t find a business address, registration records, or other indicators of physical operations.
- No ties to reputable companies – There are no endorsements or affiliations that link CoinTrieve to larger reputable companies in the crypto recovery space.
Paying attention to these red flags can help avoid being manipulated by the CoinTrieve scam.
How the CoinTrieve Crypto Scam Works
To truly understand the CoinTrieve scam, it’s important to dive deeper into their step-by-step playbook. Being aware of these tactics can prevent you from being ensnared by their clever ruse.
Step 1) Lure Victims on their Website
The CoinTrieve scammers first have to attract potential victims to their website. They achieve this through a mix of aggressive online marketing and exploiting vulnerabilities.
Search Engine Marketing
The scammers behind CoinTrieve heavily invest in search engine marketing and search engine optimization (SEM/SEO). This allows their website to rank high in Google and Bing results for relevant keywords like “cryptocurrency recovery service”.
When victims search for help recovering lost crypto, the CoinTrieve website will prominently appear in results. This tricks victims into thinking they are a legitimate company.
Social Media Marketing
CoinTrieve has accounts across social media including Twitter, Facebook, and Reddit. They use these platforms to promote their services and interact with potential victims.
Reply-guy scams are one tactic they leverage, where automated bots reply to posts about lost crypto with a link to CoinTrieve. This aggressively puts their website in front of victims at their most desperate and vulnerable moments.
Exploiting Vulnerabilities
CoinTrieve scours forums, Reddit, Telegram groups, and other platforms to identify users who recently lost crypto funds. They then directly target those users through email or social media messages offering their recovery services.
This exploitation of vulnerabilities when victims are distraught gives CoinTrieve an opportunity to gain trust through the guise of wanting to help.
Search Hijacking
There are concerning indicators that CoinTrieve may engage in technical exploits like search hijacking/redirects to force their website in front of victims.
For example, some users report typing crypto recovery keywords into Google but instead being instantly redirected to the CoinTrieve website. This demonstrates the deceptive lengths scammers will go to in order to attract victims.
Step 2) Build Trust Through Fake Professionalism
Once a potential victim lands on the CoinTrieve website, the scammers have to build trust quickly to hook them into the scam process. They achieve this through two main methods:
Appearing as a Legitimate Company
The website, branding, language, and claimed credentials are all engineered to make CoinTrieve appear as a professional and reputable company.
This façade of legitimacy is key because it gets victims to lower their guard and believe CoinTrieve can actually help recover their crypto. In reality, the scammers behind CoinTrieve are anonymous fraudsters.
Employing Professional Social Engineers
CoinTrieve has team members dedicated to personally interacting with potential victims once they submit info through the website. These social engineers are experts in building trust through psychology and persuasion.
They will express sympathy, build rapport, ask thoughtful questions, and make promising (but vague) assurances that the crypto can be recovered. This quickly builds strong trust with emotionally vulnerable victims.
Step 3) Make Upfront Payment Demand
Once the scammers have built a rapport with the victim, they move to the pivotal stage of demanding an upfront recovery fee. This is framed in a strategic way to continue manipulating the victim’s trust.
Presenting as “Approval” Milestone
The scammers will contact the victim stating that after an extensive review process, CoinTrieve has officially “approved” taking on their recovery case.
This makes the victim feel a sense of relief and progress. In reality, there is no approval process – they make this fake milestone up to advance the scam.
Justifying the Upfront Fee
Next, CoinTrieve explains that before starting the intensive recovery work, an upfront fee is required to cover “operating costs”. These costs may include investigator expenses, legal fees, hacking services, etc.
The scammers present logical justifications for each supposed cost. This tricks the victim into thinking the fee is legitimate instead of a outright scam.
Offering Discounts & Deals
To further manipulate victims, CoinTrieve often provides discount codes, bonus offers, or other incentives if the fee is paid quickly.
This conveys scarcity and urgency, pressuring victims to pay the “discounted” fee now before the offer expires. In reality, the fee itself simply goes into the scammer’s pockets.
Making Payment Easy
CoinTrieve wants to ensure victims can pay the fee as seamlessly as possible. They accept payment through cryptocurrency, credit cards, wire transfer, PayPal, and other methods.
The easier they can make it to pay, the less chance the victim will hesitate or spot the scam. Friction during payment could break the spell of manipulation.
Step 4) Stall Recovery with Excuses
After securing the upfront fee payment from victims, CoinTrieve needs to stall actual recovery efforts while creating false hope. They utilize every trick imaginable to string victims along in this stage.
Fake Progress Updates
CoinTrieve will provide periodic updates to the victim conveying that good progress is being made. These include claims of contacting exchanges, tracking hacker movements, engaging assets recovery networks, and other faux signs of work being done.
Request for More Information
Scammers will say they require additional details from victims to aid the recovery process. This may include receipts, transaction records, photos, or extensive backstory. The more they can string this along, the longer they stall.
Cite Unexpected Complications
When victims start questioning the delays, CoinTrieve will blame unexpected complications like difficulty pinpointing hacker locations, exchange legal red tape, or blockchain congestion slowing fund tracing.
These complications both buy more time and reinforce that real work is happening.
Leverage Hacker Fears
CoinTrieve will claim that hackers are actively fighting back against the recovery efforts, justifying the need for even more time. Scaring victims with this notion distracts from the fact they are the real scammers.
Appeal to Hope & Fear
By keeping updates just promising enough, CoinTrieve fuels victims’ hope that recovery could happen soon. Victims are also made to fear losing all progress if they stop engaging with CoinTrieve. This psychological trap keeps them obediently waiting.
Step 5) Disappear and Retain Money
After stalling as long as possible, eventually victims will catch on that it’s a scam as no funds are ever recovered. At this point, CoinTrieve will disappear with the money.
Ghost Victims
Once victims start demanding their money back too assertively, CoinTrieve will simply stop responding to all contact attempts. Emails, calls, and social media outreach will all be ignored.
Remove Online Presence
To avoid victim backlash, CoinTrieve will take down their website, delete social media accounts, and scrub all traces of their online presence. This makes it extremely difficult for authorities to pursue them.
Open Under New Entity
After letting some time pass, the scammers will simply re-emerge under a new company name and repeat the entire scam process with new victims. Rinse and repeat.
By understanding this deceptive 5-step playbook, potential victims can hopefully identify CoinTrieve as a scam before getting ensnared by their manipulative tactics.
What to do if you have Fallen Victim to CoinTrieve
For those unfortunate souls who have already been swindled by the CoinTrieve scam, all hope is not lost. While recovery will be difficult, here are important steps to take to report CoinTrieve and regain some of what was stolen:
Step 1) Cut off All Contact
It can be tempting to keep engaging with CoinTrieve on the tiny chance your money is returned. But ceasing all contact is crucial, as any additional engagement just enables them to string you along and steal even more funds.
Delete any email addresses, phone numbers, social media connections etc. you have for them. End the scam cycle immediately.
Step 2) Report Them to Authorities
Alerting authorities about CoinTrieve helps ensure they are on the radar for investigation, disrupting their ability to keep scamming.
File detailed reports about your experience with the following agencies:
- FBI Internet Crime Complaint Center (IC3)
- Federal Trade Commission
- State Attorney General’s Office
- Local police cybercrime division
Preserve all written, audio, and visual communications you have with CoinTrieve to aid the investigations.
Step 3) Warn Others of the Scam
The more public awareness there is surrounding CoinTrieve’s scam tactics, the harder it will be for them to find new victims.
Post about your experience on social media, crypto forums, Reddit, and anywhere else it may have visibility. Submit bad reviews of CoinTrieve on sites like TrustPilot to dissuade new victims.
Contact any organizations you see promoting CoinTrieve to ensure they are aware it is a scam targeting their members who have lost crypto.
Step 4) Consult an Attorney
A lawyer experienced in recovering stolen funds will know the legal strategies that could help wrestle back some of what CoinTrieve took.
An attorney can also facilitate the process of reporting CoinTrieve to authorities and assist with any potential civil action against them. Their expertise significantly improves the odds of reclaiming lost money.
Step 5) Seek Emotional Support
The betrayal and loss of being scammed can be emotionally traumatic. Seeking counseling or joining support groups with other scam victims can help process these difficult feelings.
Do not isolate yourself – you are not to blame for the calculated deception tactics CoinTrieve uses. Seek strength through shared experiences.
While the CoinTrieve scam can certainly do damage, following these steps helps limit their power and starts you on a path to potential recovery.
Conclusion
In conclusion, the cryptocurrency recovery service CoinTrieve is a complete scam designed to trick victims into paying an upfront fee with the false promise of helping recover lost crypto funds. In reality, CoinTrieve utilizes clever psychological tactics and stalling methods to extract as much money as possible before disappearing without ever actually regaining victims’ assets.
The best way to avoid this scam is to identify the multiple red flags indicating their illegitimacy. An absence of physical operations, upfront fees, vague details, and lack of industry ties are all warning signs of the CoinTrieve fraud.
If you have already fallen victim to CoinTrieve, immediately cease contact and report them to as many authorities as possible. Widespread awareness of this scam is crucial to disrupting their ability to keep stealing funds. While challenging, legal consultation and emotional support give victims the best chance of reclaiming some of what was taken.
Cryptocurrency scams like CoinTrieve unfortunately thrive on exploiting vulnerable situations. But combined vigilance and education within the crypto community can help curb these predatory practices, creating a safer and more trustworthy ecosystem for all.




