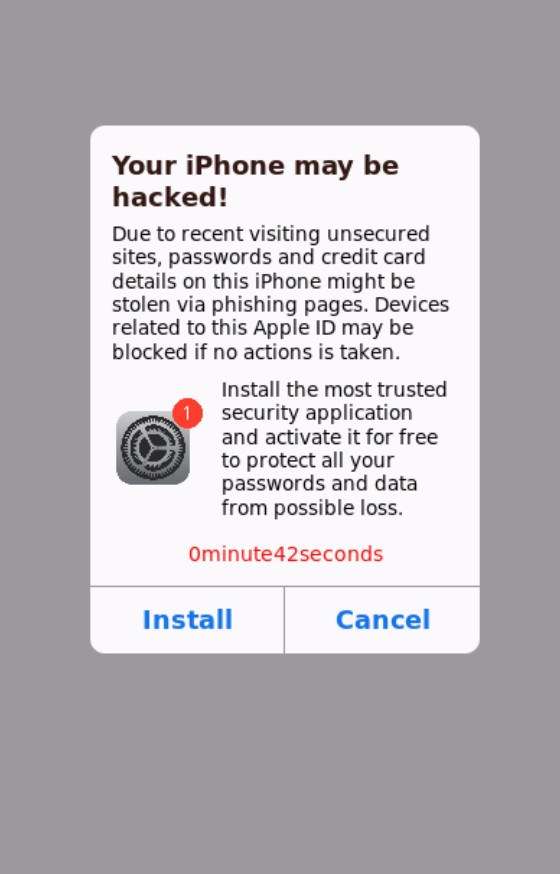
Pop-up warnings can appear convincing, but many are scare tactics used by scammers. One such scam claims “iPhone Severely Damaged by 19 Viruses!” to trick users into installing unwanted apps and sharing sensitive information. Learn how this scam operates and how to protect yourself.
Scam Overview: “iPhone Severely Damaged by 19 Viruses”
The scam starts with an alarming pop-up triggering fears of mobile malware infections. Here’s a sample message shown on iPhone devices:
“iPhone severely damaged by 19 viruses! We have detected that your Browser is (59%) DAMAGED by BROWSER TROJAN VIRUS picked up while surfing recent corrupted sites. Immediately install mobile security application or sensitive data like your Facebook account, Whatsapp messages, photos and provate application will be infected and stolen.”
This intends to convince victims to hastily download apps, call scam support numbers, and share personal information to stop the supposed viruses. In reality, it is completely fabricated to take advantage of public iOS security concerns.
Scare Tactics Used
The scam leverages various psychological triggers and fears to spur user action, including:
- Threat severity – Claims an excessive 19 viruses to sound highly dangerous
- Data loss – Warns personal data will be “infected and stolen”
- Time limit – A visible timer pressures quick action before damage worsens
- Reciprocity – Offers a free “fix” after warning of issues, triggering feelings of obligation
Combined, these make victims feel an urgent need to mitigate threats by accepting the scam’s “help”. But all these warnings are outright deceptions.
Scam Goals
The end goals of this scam include:
- Installing malware – By disguising malware as security software or OS updates. Once installed, attackers gain device access.
- Phishing credentials – Direct victims to fake login pages to harvest Apple, iCloud, Facebook, Gmail and other account details.
- Hijacking accounts – Leverage phished credentials to login and takeover compromised accounts.
- Charging fraudulent fees – Trick users into unnecessary premium account subscriptions or fake support services.
In summary, the scam aims to fully compromise devices, accounts, and finances by exploiting fear around iOS malware threats.
Step-by-Step Scam Process
While specifics vary across campaigns, the “iPhone Severely Damaged” scam generally unfolds as follows:
Step 1: Victim Visits Scam Site
The scam begins by the pop-up loading on an infected website visited on an iPhone. Scammers infiltrate sites via:
- Exploiting vulnerabilities in outdated platforms like WordPress or vBulletin
- Cracking site admin accounts with brute force or credential stuffing
- Purchasing ad inventory often via real-time bidding platforms
Once site access is gained, the scam code is added to serve the fake virus pop-up to site visitors.
Step 2: Pop-up Triggers Action
The alarming pop-up appearing surprises users as they browse. iOS malware is rare, so seeing claims of viruses catching many off guard.
Fear of account theft or permanent data loss pushes victims into hastily contacting the scam number shown or clicking install buttons.
Step 3: Fake Mobile Support Answers
When phoning the number, scammers posing as Apple support or mobile security experts answer. They confirm the supposed threats and claim only they can fix the viruses.
Call environments mimic real support centers, with hold music and transfers giving an added air of legitimacy.
Step 4: Support Instructs Malware Download
Scammers direct victims to a website and have them download an app portrayed as anti-virus software or an iOS update needed to remove the viruses.
In reality, this app is malware that gives scammers remote access once installed. They persuade victims the download is from the official App Store and safe.
Step 5: Directing Users to Phishing Sites
Alternatively, scammers direct victims to fake Apple ID, iCloud, or App Store login pages to harvest credentials. The sites mimic Apple’s design and branding.
Any data entered is captured by scammers, giving them account access to compromise sensitive user info, files, and device data.
Step 6: Account and Device Takeover
With malware installed or credentials phished, scammers can fully takeover accounts and devices.
Actions include plundering bank/iCloud data, activating services in victims’ names, snooping on device files and location history, accessing onboard cameras, and reselling account access.
Scammers may also enroll compromised iOS devices into botnets to conduct DDoS attacks.
Step 7: Ongoing Extortion
Victims may be blackmailed with sensitive or embarrassing data found on devices. Scammers can threaten sharing photos or browsing history publicly unless ransom demands are met.
Scammers also interrogate victims on what other accounts and financial assets they have to target next. Savings, retirement, and investment accounts can be drained.
What To Do If You Encountered This Scam
If you suspect you interacted with the virus pop-up scam, stay calm and take these steps:
Step 1: Disconnect from WiFi/Cellular
If you installed any suspicious apps, cut the device’s internet access immediately. This prevents scammers from retaining access.
On an iPhone, toggle Airplane Mode on, then toggle WiFi and Cellular Data off while in Airplane Mode to block all connections.
Step 2: Remove Downloaded Apps
Go into Settings > General > iPhone/Device Storage. Look for any apps you don’t remember downloading or any with generic names like “Security”, “Antivirus” or “iOS Update”.
Delete all such suspicious apps. This removes any lurking malware.
Step 3: Reset Apple ID Password
If you entered Apple credentials into any third-party sites, reset your Apple ID password immediately at appleid.apple.com. Enable two-factor authentication as well for added security.
Step 4: Scan for Malware
Install trusted antivirus apps like Malwarebytes to scan for any lingering infections or malicious activity on your iOS device. Let it remove anything harmful it detects.
Step 5: Contact Banks/Accounts
If any financial accounts were compromised, contact institutions to freeze accounts, dispute charges, and reset online account passwords.
Monitor account activity closely for fraudulent charges or password changes.
Step 6: Report the Scam
Notify the FBI’s Internet Crime Complaint Center with all details on the pop-up scam, phone numbers, site visited, losses incurred to aid investigations. Local police are another option.
Step 7: Leave App Store Reviews
Look up any downloaded apps in the App Store and leave 1 star ratings warning others of malware or scam risks to protect victims.
How to Avoid Falling Victim
While no one is immune to mobile scams, following best practices safeguards against threats:
Install an Antivirus
Reputable antivirus apps like Malwarebytes provide real-time website scanning to block known malicious pages before they can display virus pop-ups.
Update Devices Regularly
Always keep iOS devices updated to the latest OS version. Updates patch vulnerabilities that scammers exploit to distribute malware or phishing pages.
Avoid Unknown Sites
Be cautious when visiting new, unknown sites that haven’t earned reputations for safety. Only install apps from the official App Store, not third-parties.
Don’t Call Random Numbers
Never phone random numbers seen in pop-ups making security claims or requesting support. Independently find official contact info and verify the issue.
Monitor App Permissions
Check what contacts, data, and device access any newly installed apps request. Malware often asks for excessive permissions. Avoid installing such apps.
Use Strong Passwords
Create unique, complex passwords for all accounts to make successful credential stuffing attacks more difficult. Enable two-factor authentication as well.
Keep Software Updated
Always update browsers and other apps used to visit websites. Updates patch security flaws that scammers leverage to distribute pop-up malware.
Frequently Asked Questions
What is the “iPhone Severely Damaged by 19 Viruses” scam?
This scam shows a fake pop-up claiming your iPhone has 19 dangerous viruses. It urges you to call a number or install apps to remove the non-existent threats, but it is a ploy to distribute malware or steal Apple credentials.
What does the scam pop-up say?
The pop-up says “iPhone severely damaged by 19 viruses!… Immediately install mobile security application or sensitive data like your Facebook account, Whatsapp messages, photos and private application will be infected and stolen.”
What is the scammer’s goal?
Goals include tricking you into downloading malware, capturing Apple ID/iCloud credentials via phishing, hijacking accounts, encrypting data for ransom, and enrollment in botnets for DDoS attacks.
What techniques do scammers use?
Tactics include false claims of severe virus infections, threats of permanent data loss, visible timers showing imminent danger, and offering free “protection” to trigger reciprocity and urgency.
How can I avoid this iPhone virus scam?
Use antivirus apps, update devices regularly, avoid unknown sites, don’t call random numbers, monitor app permissions, use strong passwords, and keep software updated.
What should I do if I encountered this scam?
Disconnect from the internet, delete any downloaded apps, reset Apple ID password, run antivirus scans, contact banks about account security, report the scam to authorities, and leave App Store warnings about malware.
Who typically falls victim to this scam?
Anyone using an iPhone or iPad could encounter this scam. It exploits general fears around mobile malware. Elderly and those less tech-savvy may be more prone to fall for the claims and urgent threats though.
Can this scam affect other devices like Androids?
Yes, similar fake virus pop-ups are used to target Android devices as well. The scam tactics remain largely the same.
How can I report this scam?
Report details like scam sites, pop-up content, phone numbers, and losses to the FBI Internet Crime Complaint Center or your local police department.
How can I recover losses from this scam?
If you paid scammers via credit card you can request a chargeback citing fraudulent charges. Unfortunately, other methods like gift cards or crypto may not be recoverable.
Conclusion
Cybercriminals are working relentlessly to craft increasingly convincing scams targeting mobile users. But knowledge of their tactics makes it possible to evade schemes like the phony “iPhone Severely Damaged by 19 Viruses” campaign.
Bookmark trusted sites, leverage security tools, install apps selectively, and think critically before providing any sensitive information. Together we can outsmart scammers aiming to exploit public technology fears and regain peace of mind while on the go.