Social media is constantly evolving, bringing new trends—and new scams. One recent scheme taking advantage of users’ curiosity is the Abandoned House Facebook scam. Using striking AI images and videos of deserted mansions, castles, and other eerie locations, scammers bait users with hashtags like #abandoned and #abandonedplaces. But behind these captivating posts lies a deceptive ploy designed to exploit engagement and trust.
This article breaks down how the scam works, the warning signs to watch for, and the steps you can take to stay safe. By recognizing the tactics used by scammers, you can protect yourself and others from falling into their trap.
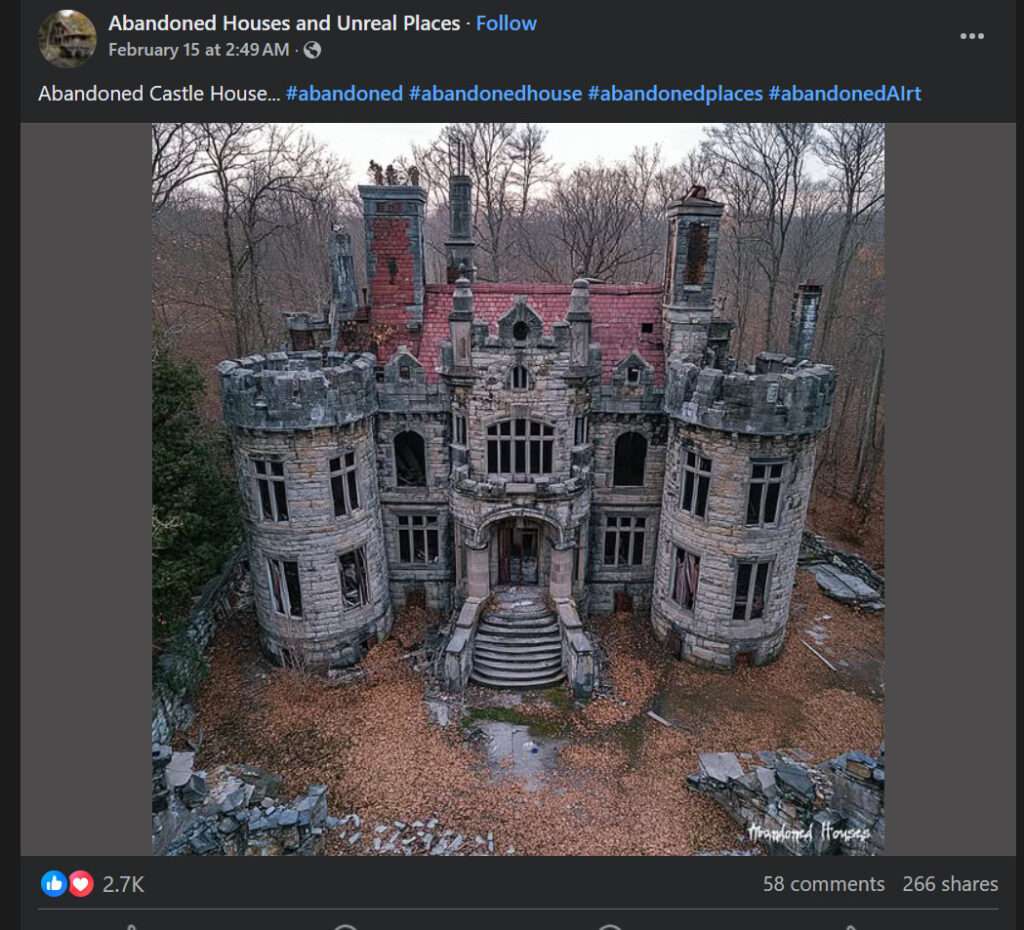
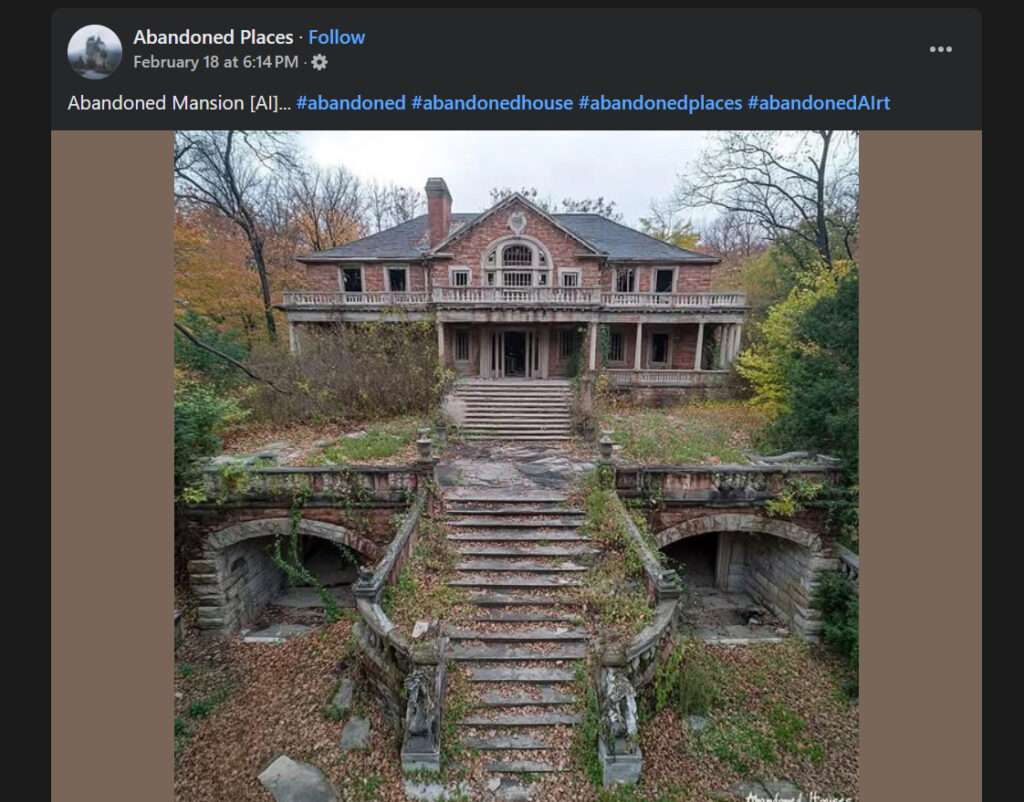
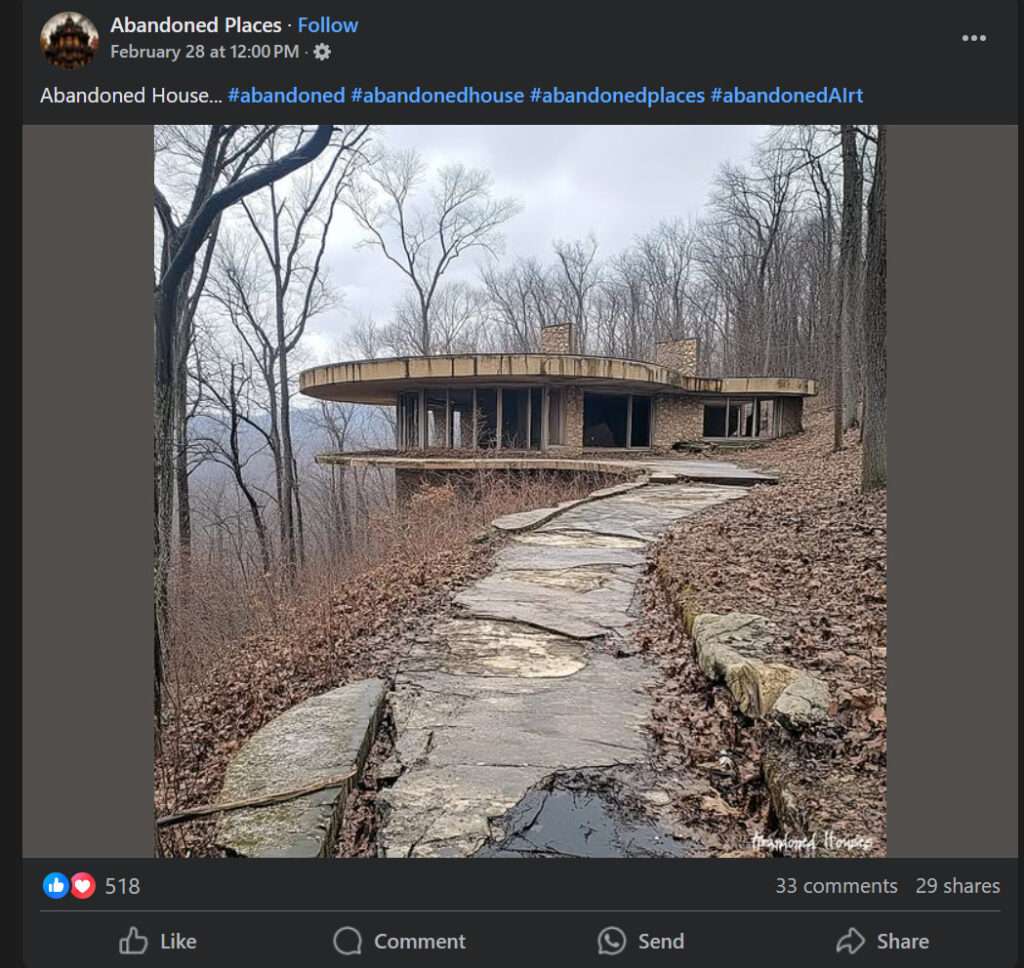
Scam Overview
The Abandoned House Facebook scam is a cunning ploy that exploits our fascination with the mysterious and the unknown. Scammers create compelling posts featuring AI-generated images and videos of purportedly abandoned houses, mansions, and castle houses. These posts are often accompanied by enticing hashtags such as #abandoned, #abandonedhouse, #abandonedplaces, and #abandonedAIrt, designed to pique curiosity and attract attention.
The visuals are carefully crafted using advanced AI technologies, rendering them almost indistinguishable from real photographs. The haunting beauty of these dilapidated structures, overgrown with vegetation and shrouded in an aura of mystery, proves irresistible to many social media users. Little do they know that behind the façade of intrigue lies a sinister motive.
Scammers employ two primary tactics in this scheme. The first involves amassing likes and follows for their pages or accounts. By posting captivating abandoned house content, they rapidly grow their follower base. Once they have garnered a substantial following, they deceptivey change the page name and repurpose it for other nefarious scams, leveraging the trust and engagement they have built.
The second tactic is even more deceptive. Scammers embed links within their posts, promising additional information or exclusive content related to the abandoned houses. However, when unsuspecting users click on these links, they are redirected to surveys, potentially unwanted programs (PUPs), or other scams. These redirects are designed to extract personal information, infect devices with malware, or deceive users into making purchases or subscribing to services they never intended.
This scam has been also investigated by Jordan Liles on his YouTube channel, where he offers a detailed video on the subject. We recommend watching his content for a comprehensive understanding of the scam.
Next, let’s break down exactly how scammers carry out this scam from start to finish.
How the Scam Works
The Abandoned House Facebook scam operates with a level of sophistication that can catch even the most discerning users off guard. Here’s a step-by-step breakdown of how scammers execute this scheme:
Step 1: Creating Compelling Content
Scammers harness the power of AI to generate hyper-realistic images and videos of abandoned houses, mansions, and castle houses. These visuals are meticulously designed to evoke a sense of intrigue and mystery, capturing the imagination of social media users.
Step 2: Crafting Enticing Posts
The AI-generated visuals are then packaged into Facebook posts, accompanied by attention-grabbing captions and relevant hashtags. Scammers strategically use hashtags like #abandoned, #abandonedhouse, #abandonedplaces, and #abandonedAIrt to increase visibility and attract potential victims.
Step 3: Building a Following
As the captivating posts circulate on Facebook, unsuspecting users engage with the content by liking, commenting, and sharing. Scammers actively monitor and respond to comments, fostering a sense of community and trust around their page or account.
Step 4: The Bait and Switch
Once the scammer’s page or account has amassed a significant following, they execute the next phase of their scheme. They abruptly change the name of the page and repurpose it for other scams, leveraging the trust and engagement they have cultivated.
Step 5: The Link Trap
In some cases, scammers include links within their posts, promising additional information or exclusive content related to the abandoned houses. When users click on these links, they are redirected to surveys, PUPs, or other scams designed to extract personal information or deceive them into making unwanted purchases.
What to Do if You Have Fallen Victim to This Scam
If you have inadvertently fallen prey to the Abandoned House Facebook scam, it’s crucial to take immediate action to minimize potential harm. Here are some steps you should follow:
1. Unfollow and report the scammer’s page or account to Facebook.
2. Run a thorough virus scan on your device using reputable antivirus software.
3. Change your passwords for any accounts you suspect may have been compromised.
4. Monitor your financial statements for any unauthorized transactions and report them to your bank immediately.
5. Be cautious of any unsolicited messages or requests you receive, as scammers may attempt to contact you for further exploitation.
6. Educate yourself and others about the tactics used in this scam to prevent future victimization.
Frequently Asked Questions (FAQs) About the Abandoned House Facebook Scam
Q1: What is the Abandoned House Facebook scam?
A: The Abandoned House Facebook scam is a deceptive scheme where scammers use AI-generated images and videos of supposedly abandoned houses, mansions, or castle houses to lure users into engaging with their content. The scammers’ ultimate goal is to gather likes and follows for their pages or accounts, which they later repurpose for other scams, or to redirect users to surveys, potentially unwanted programs (PUPs), or other fraudulent schemes.
Q2: How can I identify an Abandoned House scam post on Facebook?
A: Scam posts often feature captivating visuals of abandoned structures accompanied by hashtags such as #abandoned, #abandonedhouse, #abandonedplaces, and #abandonedAIrt. Be wary of posts that include links promising additional information or exclusive content, as these may lead to malicious websites or scams.
Q3: What should I do if I suspect a Facebook page is involved in the Abandoned House scam?
A: If you come across a suspicious Facebook page or post related to the Abandoned House scam, refrain from engaging with the content. Do not like, comment, or share the post, and avoid clicking on any links provided. Instead, report the page or post to Facebook and spread awareness to help others avoid falling victim to the scam.
Q4: Can clicking on links in Abandoned House scam posts harm my device?
A: Yes, clicking on links provided in Abandoned House scam posts can potentially expose your device to malware, viruses, or other malicious software. These links may redirect you to websites designed to extract personal information or trick you into downloading harmful programs. Always exercise caution and avoid clicking on suspicious links.
Q5: What should I do if I have already engaged with an Abandoned House scam post or page?
A: If you have inadvertently engaged with a scam post or page, take immediate action to protect yourself. Unfollow and report the page to Facebook, run a thorough virus scan on your device using reliable antivirus software, and change passwords for any accounts you suspect may have been compromised. Monitor your financial statements for unauthorized transactions and be cautious of any unsolicited messages or requests you receive.
Q6: How can I protect myself from falling victim to the Abandoned House Facebook scam?
A: To safeguard yourself against the Abandoned House Facebook scam, be vigilant when encountering posts featuring abandoned structures. Verify the authenticity of the content and the credibility of the source before engaging. Avoid clicking on links from unfamiliar pages or accounts, and keep your antivirus software up to date. Educate yourself about the tactics used by scammers and share your knowledge with others to help prevent the spread of this scam.
Q7: Are all posts about abandoned houses on Facebook scams?
A: Not all posts featuring abandoned houses on Facebook are scams. Legitimate urban exploration enthusiasts and photographers may share genuine content related to abandoned structures. However, it’s essential to approach such posts with caution and verify the credibility of the source before engaging or clicking on any links.
Q8: What should I do if I have shared personal information or made purchases as a result of the Abandoned House scam?
A: If you have shared personal information or made purchases due to the Abandoned House scam, take immediate steps to mitigate potential damage. Contact your bank or credit card company to report any unauthorized transactions and request a new card if necessary. If you have provided login credentials, change your passwords immediately. Consider placing a fraud alert or credit freeze on your credit report to prevent identity theft. Stay vigilant and monitor your accounts closely for any suspicious activity.
By being aware of the tactics used in the Abandoned House Facebook scam and taking proactive measures to protect yourself, you can safely navigate the social media landscape and avoid falling victim to this deceptive scheme.
The Bottom Line
The Abandoned House Facebook scam is a stark reminder of the importance of vigilance and critical thinking in the digital age. While the allure of mysterious, forgotten structures may be tempting, it’s crucial to approach such content with a discerning eye. By understanding the tactics employed by scammers and taking proactive measures to protect ourselves, we can navigate the social media landscape with greater safety and confidence.
Remember, if something seems too good to be true or arouses suspicion, trust your instincts. Engage with content from trusted sources and be cautious of unfamiliar pages or accounts. By staying informed and alert, we can collectively combat the spread of these deceptive scams and create a safer online environment for all.










