In recent weeks, a new cryptocurrency scam has surfaced under the name HYPSTR Vote Rewards — a convincing imitation of legitimate crypto voting initiatives that has already begun targeting unsuspecting investors. The fraudulent website, most notably hosted at votes-hypester.com, claims that users can earn early rewards by voting in a token allocation proposal. In reality, it’s a crypto-draining operation that steals funds the moment users connect their wallets.
This article unpacks the full story behind the HYPSTR Vote Rewards scam websites — how they work, why they look so real, what happens when you fall victim, and how to safeguard yourself and others.
Scam Overview
The HYPSTR Vote Rewards Scam is a deceptive phishing scheme designed to look like an official governance or voting initiative for the fictional token $HYPSTR. These fraudulent websites mimic the aesthetics and tone of real decentralized finance (DeFi) projects, complete with slick designs, on-chain data displays, and wallet connection prompts.
The most widely reported version of this scam has appeared on votes-hypester.com, but variants of this domain continue to emerge under similar names to evade blacklisting and detection. These sites imitate authentic crypto reward or voting dashboards, luring users with promises of free tokens or early reward allocations.
The Illusion of Legitimacy
When visiting one of these fake pages, users see a clean, professional interface featuring a banner titled “HYPSTR Rewards Update.” The message displayed often reads something like:
“Voters will receive an early $HYPSTR allocation from the Treasury Pool Funds (TPF).”
This phrasing gives the impression of a structured, community-driven initiative — a familiar mechanism in legitimate crypto ecosystems. Below this message, a button labeled “Vote Now” encourages visitors to engage.
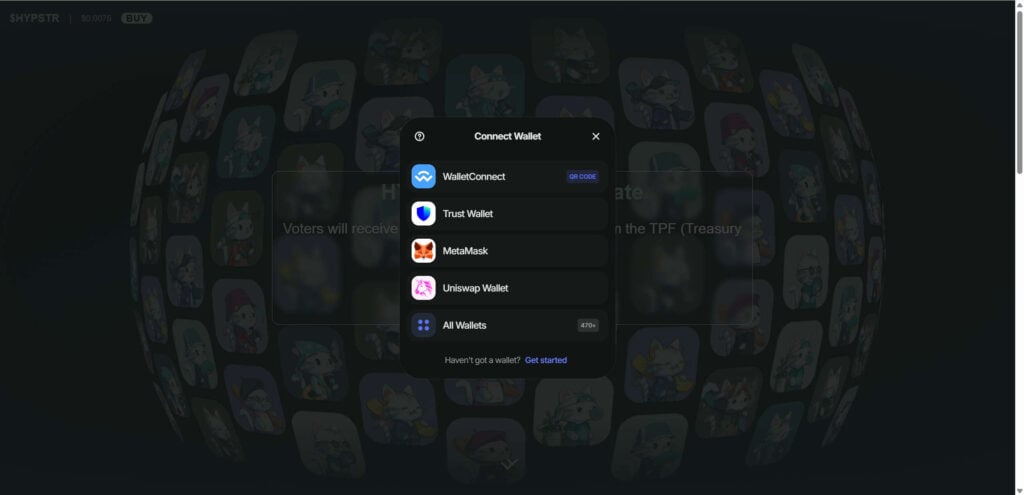
Everything about the layout — from the logo to the price ticker and “Buy” button — is designed to look trustworthy. The scam even includes interactive wallet prompts showing options such as MetaMask, WalletConnect, Trust Wallet, and Uniswap Wallet — all widely recognized by DeFi users.
To an untrained eye, nothing appears amiss.
The Real Purpose: Wallet Draining
Behind this convincing front lies a malicious smart contract designed to execute unauthorized transactions the moment a user connects their crypto wallet.
When a wallet is connected, the site triggers scripts that request token approval permissions. These permissions, if granted, allow the attacker’s contract to transfer tokens directly from the user’s wallet — a process commonly referred to as a crypto drainer.
In short, the user believes they are participating in a legitimate token vote. Instead, they are signing a transaction that effectively hands over control of their assets to the scammer.
How the Scam Gains Traction
These fake HYPSTR sites spread rapidly across:
- Social media platforms like X (formerly Twitter), Telegram, and Discord, where fake accounts impersonate legitimate crypto influencers or projects.
- Paid ads that appear in search results or on crypto news aggregators.
- Community groups, where attackers pose as project moderators sharing “official vote links.”
By combining realistic web design with social engineering, scammers achieve high conversion rates. Many users don’t suspect foul play until their wallets are emptied.
Why This Scam Works So Well
The HYPSTR Vote Rewards Scam exploits three major psychological and technical weaknesses common among crypto investors:
- Trust in Familiar Interfaces
Users are conditioned to trust wallet pop-ups from tools like MetaMask and WalletConnect. Since these legitimate interfaces appear during the scam, victims don’t realize that the back-end contract is malicious. - Fear of Missing Out (FOMO)
The fake campaign’s language emphasizes urgency: “Vote within 24 hours to receive early rewards.” This pressure causes users to act before verifying authenticity. - Brand Deception
The scam copies the look and tone of real DeFi projects. Even the token ticker “$HYPSTR” resembles names from actual blockchain ecosystems, making it appear plausible.
The Broader Pattern
The HYPSTR Vote Rewards Scam follows the same operational blueprint as similar campaigns that have impersonated other DeFi and NFT projects. These include fake “governance vote,” “airdrops,” and “staking reward” pages that promise token incentives in exchange for wallet connections.
In essence, scammers exploit the decentralized nature of blockchain — where wallet authentication replaces traditional passwords — to deceive users into authorizing theft.
How the Scam Works
To understand why this scam is so effective, it’s important to look at its technical and psychological structure in detail. Here’s a full breakdown of how the HYPSTR Vote Rewards Scam typically unfolds.
Step 1: Creating the Fake Website
The attackers start by cloning an existing crypto project site. Using modern web scraping tools, they replicate page layouts, color palettes, and fonts to create a visually identical clone.
They then register a lookalike domain, such as:
- votes-hypester.com
- hypstrrewards.net
- hypstr-vote.org
- hypstr-tokenreward.app
These names are deliberately similar to authentic project domains. The use of SSL certificates (which show the padlock icon in browsers) gives a false sense of legitimacy.
Step 2: Social Media Distribution
Once the fake site is live, the scammers promote it aggressively. Fake announcements appear on X, Discord, Telegram, and Reddit, often written to look like official project updates.
Typical messages include:
“Governance voting for $HYPSTR Rewards is now live. Vote within 24 hours to receive early TPF allocation!”
These are often accompanied by graphics stolen from real crypto marketing materials to add credibility.
Step 3: The Wallet Connection Trap
When users click “Vote Now,” they’re presented with a wallet connection pop-up. The interface lists familiar options: MetaMask, WalletConnect, Trust Wallet, and Uniswap Wallet.
Once the user selects one, the site requests a signature — supposedly to “confirm the vote.” This is where the actual attack occurs.
Step 4: The Malicious Contract Execution
Behind the front-end interface, the scam website interacts with a hidden smart contract deployed on a public blockchain. When users sign the transaction, they unknowingly authorize this contract to move tokens or assets from their wallet.
The code typically performs the following functions:
- Executes an
approve()command to grant spending permissions. - Reads the wallet’s token balances and asset types.
- Prioritizes high-value assets such as ETH, USDT, USDC, or popular NFTs.
- Uses
transferFrom()commands to move those assets to the attacker’s wallet address.
This process can be instantaneous, draining the wallet completely within seconds.
Step 5: Draining and Obfuscating Funds
Once the tokens are stolen, the scammer’s network begins laundering them through various means:
- Swapping assets on decentralized exchanges (DEXs) to convert to other tokens.
- Bridging across blockchains to make tracing harder.
- Using privacy tools and mixers like Tornado Cash alternatives to obfuscate origins.
- Transferring to multiple intermediate wallets before cashing out via exchanges.
Because these transactions occur on decentralized platforms without intermediaries, reversing them is practically impossible.
Step 6: Domain Rotation and Continuation
Once enough users report the domain or flag it on social media, scammers abandon it and launch a new clone site. The entire process is automated through scripts that can deploy replicas in minutes, ensuring continuous operation.
Cybersecurity analysts have observed that some operations run hundreds of these domains at once, cycling them to stay ahead of takedown efforts.
Step 7: Manipulating Victims Post-Theft
In some cases, scammers reach out to victims pretending to be “support agents” from the project, offering “recovery services.” These follow-up scams ask victims to pay “gas fees” or provide seed phrases, resulting in further losses.
This secondary manipulation adds another layer to the deception and highlights the need for users to avoid engaging with any recovery offers unless verified by official project representatives.
What To Do If You Have Fallen Victim to This Scam
If you interacted with votes-hypester.com or any similar site and connected your wallet, it’s critical to act immediately. Here are the essential steps to limit damage and secure your remaining assets.
1. Disconnect Your Wallet from the Scam Website
- Open your wallet extension or app (e.g., MetaMask, Trust Wallet).
- Navigate to Settings > Connected Sites.
- Remove or disconnect any unfamiliar or suspicious domains.
This prevents the malicious site from initiating further actions.
2. Revoke Token Approvals
- Visit trusted platforms like Revoke.cash or Etherscan’s Token Approval Checker.
- Connect your wallet and review all active token approvals.
- Revoke any permissions granted to unknown or suspicious addresses.
This step is crucial because it stops the scam contract from continuing to spend your tokens.
3. Transfer Remaining Assets to a New Wallet
If funds remain, move them immediately to a new wallet.
- Create a new address using a fresh seed phrase.
- Transfer all unaffected assets.
- Do not reuse the compromised wallet for future transactions.
4. Report the Scam
Notify the following entities:
- Official HYPSTR or Hyperliquid communities (if you were led there).
- Cybersecurity platforms like CertiK, Chainalysis, or SlowMist.
- Your local cybercrime or fraud reporting agency.
Include as much detail as possible: URLs, transaction hashes, and screenshots.
5. Monitor Your Wallet and Transactions
Keep checking your compromised wallet using a blockchain explorer. Watch for any unauthorized outgoing transactions or approvals that reappear.
6. Warn Others
Share your experience publicly to help prevent further victims. Post in crypto forums, Discord groups, and Reddit communities with verified project moderators.
7. Strengthen Your Security Habits
After dealing with the immediate crisis, review and upgrade your security practices:
- Use hardware wallets for large holdings.
- Verify every URL before connecting.
- Bookmark official sites.
- Enable phishing alerts in your browser.
- Stay updated through verified sources only.
The Bottom Line
The HYPSTR Vote Rewards Scam Websites, including votes-hypester.com, are part of a growing wave of crypto wallet-draining operations designed to exploit user trust in legitimate-looking DeFi interfaces. These scams are not affiliated with any authentic crypto projects or foundations.
Their design, tone, and functionality mimic genuine governance and reward platforms, but their intent is purely malicious — to steal funds through fraudulent smart contracts.
If you ever encounter a website offering rewards for voting, staking, or early participation, pause and verify. Visit only official channels, confirm announcements, and never sign a transaction you don’t fully understand.
Write Article Now said:
Frequently Asked Questions
What is the HYPSTR Vote Rewards Scam?
The HYPSTR Vote Rewards Scam is a deceptive phishing scheme that pretends to be a legitimate cryptocurrency voting or reward event. The fake website, often found at votes-hypester.com and similar domains, claims users can vote on treasury allocations and earn early $HYPSTR token rewards. However, this is completely false. Once a user connects their crypto wallet to the site, the scammers execute a malicious contract that drains digital assets from the connected wallet.
The scam is structured to look legitimate, using professional web design, animated graphics, and real wallet connection prompts such as MetaMask, WalletConnect, and Trust Wallet. Its goal is to make victims believe they are participating in a governance vote, when in reality, they are authorizing the theft of their funds.
How do these scam websites operate?
The scam works through a combination of social engineering and malicious blockchain code. Here’s a breakdown of the process:
- Fake branding and domain setup: Scammers register domains that sound similar to real blockchain project URLs, such as “votes-hypester.com” or “hypstrrewards.net.” These are equipped with SSL certificates, making the page appear secure.
- Visual deception: The site copies the interface of real crypto voting dashboards, including colorful NFTs, token price tickers, and “Vote Now” buttons.
- Wallet connection: When users click “Vote Now,” a familiar wallet connection prompt appears, giving a false sense of legitimacy.
- Hidden approval request: Once connected, users are prompted to “sign” a transaction to confirm their vote. However, this signature grants token spending permission to the scammer’s wallet.
- Asset draining: The malicious smart contract instantly transfers available tokens, stablecoins, and NFTs from the victim’s wallet to the attacker’s addresses.
What happens after you connect your wallet?
Connecting your wallet to the HYPSTR Vote Rewards Scam site triggers an automatic approval request that appears harmless. Once you approve or sign the request, you essentially authorize the scammer to move tokens on your behalf.
The contract can then:
- Access your ERC-20 tokens (ETH, USDT, USDC, etc.).
- Transfer NFTs and staked assets.
- Drain your wallet within seconds.
Because blockchain transactions are irreversible, any funds sent cannot be recovered once stolen.
Why does the HYPSTR Vote Rewards Scam look so real?
Scammers behind these fraudulent sites understand the psychology of crypto investors. They replicate legitimate design elements from real projects, including:
- Animated backgrounds and branded NFTs.
- A live “token price” displayed in the header.
- Links labeled as “Docs,” “Stats,” and “Ecosystem.”
- Wallet connection buttons using real integrations.
These professional touches make users feel safe. The combination of urgency (“vote now for early rewards”) and authenticity tricks people into connecting wallets without verifying the site.
How can I tell if a crypto voting site is fake?
To determine if a website is part of the HYPSTR Vote Rewards Scam or a similar operation, look for these warning signs:
- Unverified URL: Always check that the website domain matches the project’s official one. “votes-hypester.com” and similar addresses are fake.
- Unrealistic offers: Legitimate projects rarely promise instant token rewards or early bonuses just for connecting a wallet.
- No public announcements: Check verified social channels or community servers. If there’s no official notice about a vote, it’s a red flag.
- Generic token names: Many scam tokens like $HYPSTR or $HYPESTR have no legitimate presence on CoinMarketCap or Etherscan.
- Anonymous pages: Lack of a whitepaper, team details, or transparent contact information usually indicates fraud.
What should I do if I already connected my wallet to votes-hypester.com?
If you interacted with this fake website, take immediate action to secure your assets:
- Disconnect your wallet from the scam website. In MetaMask, go to Settings → Connected Sites and remove any unrecognized links.
- Revoke token approvals using trusted tools such as Revoke.cash or Etherscan’s Token Approval Checker. Revoke any permissions granted to suspicious contract addresses.
- Transfer your remaining assets to a new wallet created with a fresh seed phrase. Do not reuse the compromised wallet.
- Alert your community and report the scam to blockchain security services like CertiK, Chainabuse, or ScamSniffer. Include the fraudulent URL and related wallet addresses.
- Monitor your wallet for unauthorized transactions and future phishing attempts.
Can I recover stolen funds from this scam?
Unfortunately, once the assets are stolen, recovery is extremely difficult. Blockchain transactions are permanent and irreversible by design. However, you can:
- Report the scam to your local cybercrime authority.
- Submit wallet addresses to blockchain analytics platforms like Chainalysis or Etherscan to flag them publicly.
- Notify major exchanges in case the stolen funds are moved through them.
- Warn others to prevent further thefts.
Although direct fund recovery is unlikely, reporting helps increase visibility and can aid law enforcement investigations.
How can I avoid falling for crypto reward scams in the future?
You can reduce the risk of becoming a victim of scams like the HYPSTR Vote Rewards fraud by following these best practices:
- Always verify URLs. Bookmark official project sites and double-check domain names before connecting your wallet.
- Avoid clicking on links in private messages or social media posts. Scammers often spread phishing links via Discord and Telegram impersonations.
- Use a hardware wallet for long-term storage of valuable assets. Hardware wallets require physical confirmation for transactions, making it harder for scammers to drain funds.
- Check for official announcements. Real projects publish governance events on verified websites, GitHub repositories, or recognized media outlets.
- Revoke unused permissions regularly. Use Revoke.cash to ensure no old approvals are left active.
- Stay informed about new scams. Follow reliable cybersecurity researchers and blockchain watchdog accounts.
Why are scams like this becoming more common?
Phishing scams in the crypto space are increasing because DeFi and Web3 ecosystems rely on wallet connections instead of traditional logins. This model gives scammers an opportunity to exploit human error. Users get used to approving transactions quickly, and malicious actors take advantage of that familiarity.
Additionally, tools to create convincing websites and smart contracts are easy to access. Fraudsters can replicate real interfaces within hours, launch domains cheaply, and target communities globally using bots and paid ads.
Are all crypto voting or airdrop sites scams?
No, but users must remain cautious. Some legitimate blockchain projects hold governance votes or distribute airdrops. However, authentic events will:
- Be announced through official channels only.
- Never require private key access or unusual transaction signatures.
- Provide clear information about the purpose and smart contract address of the vote.
If you are unsure, verify the information directly through the project’s official social media accounts or GitHub repositories before connecting your wallet.
How can I verify a legitimate project’s website?
To confirm whether a crypto project’s website is real:
- Search on CoinMarketCap or CoinGecko. Official project pages list verified URLs.
- Check social media verification. Many legitimate teams have verified profiles on X (Twitter) or LinkedIn.
- Use trusted Web3 security extensions like WalletGuard or ScamSniffer, which can flag suspicious connections.
- Inspect domain history. Tools like WHOIS can reveal when a website was created. Newly registered domains pretending to be established projects are likely scams.
Who operates the HYPSTR Vote Rewards Scam?
The individuals or groups behind the HYPSTR Vote Rewards Scam have not been officially identified. These operations are often run by organized cybercrime networks that manage multiple fake domains simultaneously. They rotate sites, addresses, and smart contracts frequently to stay ahead of takedowns.
What are wallet drainers and how do they work?
A wallet drainer is a malicious smart contract designed to transfer funds without the victim’s consent. Instead of directly stealing passwords, it relies on users unknowingly granting token approvals. Once permissions are granted, the contract uses blockchain functions like approve() and transferFrom() to move assets to the attacker’s address.
These drainers often:
- Analyze wallets for high-value assets.
- Prioritize liquid tokens or stablecoins.
- Execute transfers immediately after approval.
- Send funds through mixers or cross-chain bridges to hide origins.










