In the world of online scams, few are as sinister and unsettling as the “I Managed To Install A Spyware Using Your Browser” sextortion email. This insidious attack preys on people’s deepest fears and insecurities, using the threat of public humiliation to extort money from its victims. In this article, we’ll take an in-depth look at how this scam operates, what you should do if you’re targeted, and how to protect yourself from falling victim in the first place.
Scam Overview
The “I Managed To Install A Spyware Using Your Browser” scam, also known as the sextortion email scam, has become a growing concern for internet users worldwide. This devious scheme involves scammers sending an email to unsuspecting victims, claiming to have installed spyware on their computer and recorded them while they were browsing adult websites or engaging in other compromising online activities. The scammer then threatens to expose the victim’s alleged behavior to their contacts, friends, and family unless a ransom is paid, usually in the form of Bitcoin or another cryptocurrency.
One of the most unnerving aspects of this scam is that it uses social engineering tactics to make the threat seem more credible. The scammer may include personal details about the victim in the email, such as their name, phone number, or even a password they’ve used in the past. This information is often obtained through data breaches or other publicly available sources, but when presented in the context of the sextortion email, it can make the victim feel as though their privacy has been genuinely compromised.
For example, the scammer might include a line like, “I know that your password is XYZ123, and I have access to all of your accounts.” By using a real password that the victim has used in the past (even if it’s not their current password), the scammer can create a sense of legitimacy and make the victim more likely to believe their claims.
Another tactic used in these scams is to create a sense of urgency and pressure. The scammer will often set a tight deadline for payment, usually within 24-48 hours, and claim that if the ransom isn’t received by then, the compromising footage will be released automatically. This high-pressure approach is designed to make the victim feel trapped and more likely to comply with the demands out of fear and desperation.
The scammer may also use language designed to shame and intimidate the victim. They might claim that the victim’s alleged behavior is “perverted” or “sick,” and that they deserve to be exposed and humiliated as punishment. This kind of language is intended to exploit the victim’s deepest insecurities and make them feel as though they have no choice but to pay up.
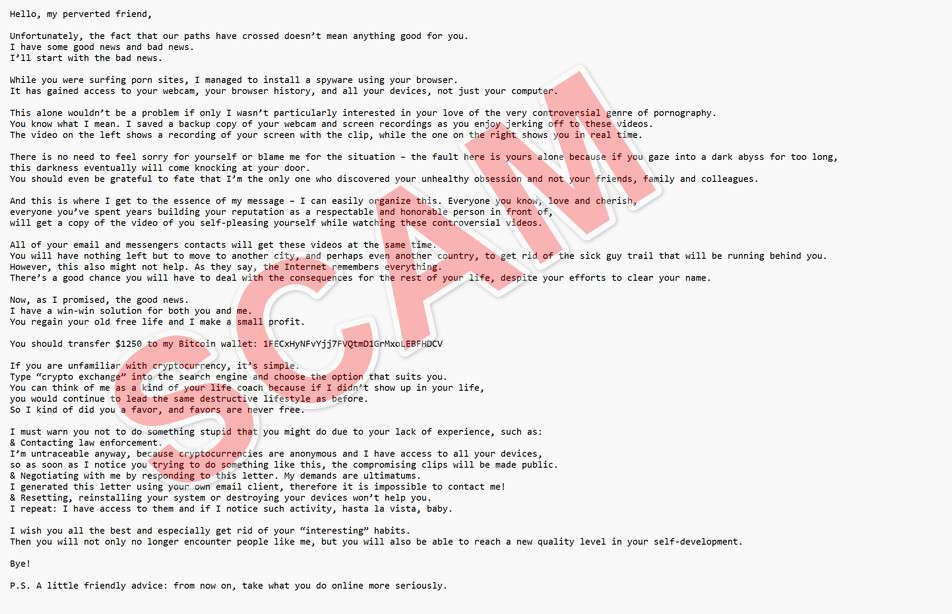
Here is how the email scam may look:
Hello, my perverted friend,
Unfortunately, the fact that our paths have crossed doesn’t mean anything good for you.
I have some good news and bad news.
I’ll start with the bad news.
While you were surfing porn sites, I managed to install a spyware using your browser.
It has gained access to your webcam, your browser history, and all your devices, not just your computer.
This alone wouldn’t be a problem if only I wasn’t particularly interested in your love of the very controversial genre of pornography.
You know what I mean. I saved a backup copy of your webcam and screen recordings as you enjoy jerking off to these videos.
The video on the left shows a recording of your screen with the clip, while the one on the right shows you in real time.
There is no need to feel sorry for yourself or blame me for the situation – the fault here is yours alone because if you gaze into a dark abyss for too long,
this darkness eventually will come knocking at your door.
You should even be grateful to fate that I’m the only one who discovered your unhealthy obsession and not your friends, family and colleagues.
And this is where I get to the essence of my message – I can easily organize this. Everyone you know, love and cherish,
everyone you’ve spent years building your reputation as a respectable and honorable person in front of,
will get a copy of the video of you self-pleasing yourself while watching these controversial videos.
All of your email and messengers contacts will get these videos at the same time.
You will have nothing left but to move to another city, and perhaps even another country, to get rid of the sick guy trail that will be running behind you.
However, this also might not help. As they say, the Internet remembers everything.
There’s a good chance you will have to deal with the consequences for the rest of your life, despite your efforts to clear your name.
Now, as I promised, the good news.
I have a win-win solution for both you and me.
You regain your old free life and I make a small profit.
You should transfer $1250 to my Bitcoin wallet: 1FECxHyNFvYjj7FVQtmD1GrMxoLEBFHDCV
If you are unfamiliar with cryptocurrency, it’s simple.
Type “crypto exchange” into the search engine and choose the option that suits you.
You can think of me as a kind of your life coach because if I didn’t show up in your life,
you would continue to lead the same destructive lifestyle as before.
So I kind of did you a favor, and favors are never free.
I must warn you not to do something stupid that you might do due to your lack of experience, such as:
& Contacting law enforcement.
I’m untraceable anyway, because cryptocurrencies are anonymous and I have access to all your devices,
so as soon as I notice you trying to do something like this, the compromising clips will be made public.
& Negotiating with me by responding to this letter. My demands are ultimatums.
I generated this letter using your own email client, therefore it is impossible to contact me!
& Resetting, reinstalling your system or destroying your devices won’t help you.
I repeat: I have access to them and if I notice such activity, hasta la vista, baby.
I wish you all the best and especially get rid of your “interesting” habits.
Then you will not only no longer encounter people like me, but you will also be able to reach a new quality level in your self-development.
Bye!
P.S. A little friendly advice: from now on, take what you do online more seriously.
It’s important to note that in the vast majority of cases, the scammer does not actually have any compromising footage or information about the victim. The entire scam is a bluff, designed to trick the victim into paying money out of fear and shame. However, the psychological impact of these scams can be devastating, even if the threats are ultimately empty.
The sextortion email scam is particularly insidious because it doesn’t require any special technical skills or resources to carry out. All the scammer needs is a list of email addresses and some basic social engineering tactics, and they can potentially reach hundreds or even thousands of victims with minimal effort.
This low barrier to entry has made the scam incredibly popular among cybercriminals, and it’s estimated that millions of these emails are sent every year. In fact, according to a report by the FBI’s Internet Crime Complaint Center (IC3), sextortion scams were the second-most reported type of cybercrime in 2022, with losses totaling more than $70 million.
To protect yourself from falling victim to this scam, it’s essential to be aware of how it works and to take steps to secure your online accounts and protect your privacy. This includes using strong, unique passwords for all of your accounts, enabling two-factor authentication whenever possible, and being cautious about sharing personal information online.
If you do receive a sextortion email, it’s crucial not to panic or give in to the scammer’s demands. Instead, you should report the scam to the appropriate authorities and take steps to secure your accounts and devices. Remember, the scammer’s power lies in fear and intimidation, but you have the power to take control of the situation and protect yourself.
In the following sections, we’ll take a closer look at how the “I Managed To Install A Spyware Using Your Browser” scam works, what you should do if you’re targeted, and how to protect yourself from falling victim in the first place.
How the Scam Works
The “I Managed To Install A Spyware Using Your Browser” scam is a carefully orchestrated attack that relies on a combination of technical trickery, psychological manipulation, and social engineering to pressure victims into paying a ransom. Let’s take a closer look at each stage of the scam and how it unfolds.
Step 1: The Initial Email
The scam begins when the victim receives an email in their inbox with a subject line designed to grab their attention and create a sense of urgency or fear. Some common examples include:
- “You’ve Been Recorded”
- “I Have Proof of Your Perversion”
- “Your Secret is Out”
- “You’re In Trouble”
The email itself is often sent from a spoofed or fake email address, which makes it difficult to trace back to the actual scammer. In some cases, the scammer may use a script or bot to send out thousands of these emails at once, targeting as many potential victims as possible.
Step 2: The Hook
Once the victim opens the email, they’re confronted with a shocking claim: the scammer says they’ve installed spyware on the victim’s computer and have been monitoring their online activities. They may claim to have access to the victim’s webcam, browser history, and even their entire device, including files and photos.
For example, the email might include a line like:
“While you were browsing adult websites, I managed to install a spyware using your browser. It has given me access to your webcam, your browser history, and all of your devices, not just your computer.”
This claim is designed to create a sense of panic and vulnerability in the victim, making them feel as though their privacy has been violated and their personal information is at risk.
Step 3: The Threat
Once the scammer has the victim’s attention, they drop the bombshell: they claim to have recorded the victim watching pornography or engaging in other compromising online activities. They may even claim to have video footage showing the victim’s face and screen side-by-side, to make the threat seem more credible.
For example, the email might include a line like:
“I saved a screen recording of you as you watched that adult content. The recording shows your screen on the left and your webcam on the right. I have clear evidence of what you’ve been up to.”
This threat is the crux of the scam, and it’s designed to exploit the victim’s deepest fears and insecurities. Even if the victim hasn’t actually been recorded, the mere suggestion that they have can be enough to create a sense of shame and desperation.
Step 4: The Shame
To further maximize the victim’s fear and shame, the scammer often includes personal details about the victim in the email, such as their name, phone number, or a password they’ve used in the past. This information is often obtained through data breaches or other publicly available sources, but when presented in the context of the sextortion email, it can make the threat seem even more credible.
For example, the email might include a line like:
“I know that your name is John Smith, and your phone number is 555-123-4567. I also know that you used the password ‘ilovecats123’ on one of your accounts.”
By including this kind of personal information, the scammer creates the impression that they have intimate knowledge of the victim’s life and online activities, which can be incredibly unnerving and make the victim more likely to comply with their demands.
Step 5: The Demand
Once the scammer has the victim in a state of panic and desperation, they make their demand: pay a ransom, usually in the form of Bitcoin or another cryptocurrency, in exchange for not releasing the alleged video footage to the victim’s contacts, friends, and family.
The amount demanded can vary, but it’s often in the range of several hundred to several thousand dollars. The scammer may claim that this is a small price to pay to keep the victim’s reputation intact and prevent the alleged footage from ruining their life.
For example, the email might include a line like:
“To prevent me from releasing this video to all of your contacts and ruining your life, you need to send me $1,500 in Bitcoin within the next 24 hours. If you don’t know how to buy Bitcoin, just search for ‘how to buy Bitcoin’ on Google.”
This demand is designed to create a sense of urgency and pressure the victim into acting quickly, before they have time to think things through or seek help.
Step 6: The Deadline
To further ratchet up the pressure, the scammer often sets a tight deadline for payment, usually within 24-48 hours. They may claim that if the ransom isn’t received by the deadline, the alleged video footage will be automatically released to the victim’s contacts.
For example, the email might include a line like:
“You have 48 hours to send the payment to the following Bitcoin address: 1FECxHyNFvYjj7FVQtmD1GrMxoLEBFHDCV. If I don’t receive the payment by then, the video will be sent to everyone you know.”
This deadline is another psychological tactic designed to make the victim feel trapped and more likely to comply with the scammer’s demands out of fear and desperation.
Step 7: The Follow-Up
If the victim doesn’t pay the ransom by the initial deadline, the scammer may send follow-up emails to increase the pressure even further. They may claim to have already sent the video to some of the victim’s contacts or threaten to release it more widely if payment isn’t received immediately.
For example, a follow-up email might include a line like:
“You missed the deadline, and now I’ve sent the video to your boss and a few of your coworkers. If you don’t want me to send it to everyone else you know, you need to send the payment NOW.”
These follow-up emails are designed to wear down the victim’s resistance and make them feel as though they have no choice but to comply with the scammer’s demands.
Throughout this entire process, the scammer relies on a combination of technical trickery, psychological manipulation, and social engineering to pressure the victim into paying the ransom. By creating a sense of urgency, exploiting the victim’s fears and insecurities, and using personal information to make the threat seem credible, the scammer is able to convince even the most cautious and tech-savvy individuals that their privacy has been violated and their reputation is at risk.
It’s important to remember, however, that in the vast majority of cases, the scammer does not actually have any compromising footage or information about the victim. The entire scam is a bluff, designed to trick the victim into paying money out of fear and shame. By understanding how this scam works and taking steps to protect your online privacy and security, you can avoid falling victim to this insidious attack.
What to Do If You’ve Fallen Victim to This Scam
If you’ve received an email like the one described above, it’s important to remember that you are not alone, and you have options. Here are some steps you can take:
- Don’t Panic: The first and most important thing to do is to stay calm. The scammer wants you to feel afraid and ashamed, but panicking will only make it harder to think clearly and take effective action.
- Don’t Pay: No matter how convincing the scammer’s threats may seem, paying the ransom is never a good idea. There’s no guarantee that the scammer will actually delete the alleged footage, and paying will only mark you as an easy target for future scams.
- Report the Scam: If you’ve received a sextortion email, you should report it to the appropriate authorities. In the United States, you can file a complaint with the FBI’s Internet Crime Complaint Center (IC3) at www.ic3.gov. You should also report the scam to your local police department, as well as to your email provider and any relevant social media platforms.
- Secure Your Accounts: If the scammer has included a password or other personal information in their email, it’s important to change your passwords immediately and enable two-factor authentication on all of your accounts. This will help prevent the scammer from gaining access to your accounts and using them to cause further harm.
- Seek Support: Falling victim to a scam like this can be a deeply traumatic experience, and it’s important to seek support from friends, family, or a professional counselor if you’re struggling to cope with the emotional fallout. Remember, you are not to blame for being targeted by a scammer, and there is no shame in seeking help.
Frequently Asked Questions (FAQs)
Q1: What is the “I Managed To Install A Spyware Using Your Browser” scam?
A1: The “I Managed To Install A Spyware Using Your Browser” scam, also known as the sextortion email scam, is a type of online blackmail where scammers send an email claiming to have installed spyware on your device and recorded you while visiting adult websites. They threaten to expose your alleged online activities to your contacts unless you pay a ransom, usually in Bitcoin or another cryptocurrency.
Q2: How do the scammers get my personal information?
A2: Scammers often obtain personal information, such as email addresses, passwords, and phone numbers, through data breaches or by purchasing it on the dark web. They may include this information in their email to make their threat seem more credible, but it doesn’t necessarily mean they have actually installed spyware on your device or recorded your activities.
Q3: Is the scammer’s threat legitimate? Do they really have a video of me?
A3: In most cases, the scammer’s threat is a bluff, and they do not actually have any compromising footage or information about you. They rely on fear and intimidation to pressure victims into paying the ransom, even if their claims are baseless.
Q4: What should I do if I receive a sextortion email?
A4: If you receive a sextortion email, the most important thing is to stay calm and not panic. Do not reply to the email or attempt to contact the scammer, as this may encourage them to send more threats. Instead, report the email to the appropriate authorities, such as the FBI’s Internet Crime Complaint Center (IC3) or your local law enforcement agency.
Q5: Should I pay the ransom if I receive a sextortion email?
A5: No, you should never pay the ransom demanded in a sextortion email. Paying the scammer will not guarantee that they will delete any alleged footage or keep their promise to leave you alone. In fact, paying may only encourage them to target you again in the future or share your information with other scammers.
Q6: How can I protect myself from falling victim to the “I Managed To Install A Spyware Using Your Browser” scam?
A6: To protect yourself from sextortion scams, it’s essential to maintain good online security practices, such as using strong and unique passwords for all your accounts, enabling two-factor authentication, and keeping your software and devices up to date. Additionally, be cautious about opening emails from unknown senders and avoid clicking on suspicious links or attachments.
Q7: What should I do if the scammer has included one of my real passwords in the email?
A7: If the scammer includes a legitimate password in their email, it’s crucial to change that password immediately on any accounts where you may have used it. Enable two-factor authentication on these accounts for added security. The scammer likely obtained the password from a data breach, not from actually installing spyware on your device.
Q8: Can the scammer be traced or caught?
A8: Tracing and catching scammers can be difficult, as they often operate from foreign countries and use various techniques to hide their identities. However, by reporting sextortion emails to the proper authorities, you can help law enforcement agencies gather evidence and potentially identify patterns that may lead to the scammer’s capture.
Q9: What are the psychological effects of falling victim to a sextortion scam?
A9: Falling victim to a sextortion scam can be a traumatic and emotionally distressing experience. Victims may feel ashamed, anxious, or depressed, and may struggle with feelings of vulnerability and helplessness. It’s essential to remember that you are not alone and that there is no shame in seeking help from friends, family, or mental health professionals to cope with the aftermath of a scam.
Q10: Are there any resources available for victims of sextortion scams?
A10: Yes, there are several resources available for victims of sextortion scams. In addition to reporting the scam to law enforcement, victims can seek support from organizations such as the Cyber Civil Rights Initiative (CCRI), which provides information, resources, and a crisis helpline for victims of online harassment and abuse. The Federal Trade Commission (FTC) also offers guidance on steps to take if you’re the target of a sextortion scam.
The Bottom Line
The “I Managed To Install A Spyware Using Your Browser” sextortion scam is a particularly vicious and manipulative attack that preys on people’s deepest fears and insecurities. By using a combination of personal information, psychological manipulation, and high-pressure tactics, scammers are able to convince even the most cautious individuals that their privacy has been violated and their reputation is at risk.
If you’ve fallen victim to this scam, it’s important to remember that you are not alone, and you have options. By staying calm, reporting the scam to the appropriate authorities, securing your accounts, and seeking support, you can take back control of your life and move forward with confidence.
Ultimately, the best defense against scams like this is awareness and education. By understanding how these scams work and taking steps to protect your online privacy and security, you can reduce your risk of falling victim and help prevent others from being targeted as well. Remember, no matter how convincing a scammer’s threats may seem, you always have the power to say no and seek help from those who can support you.

