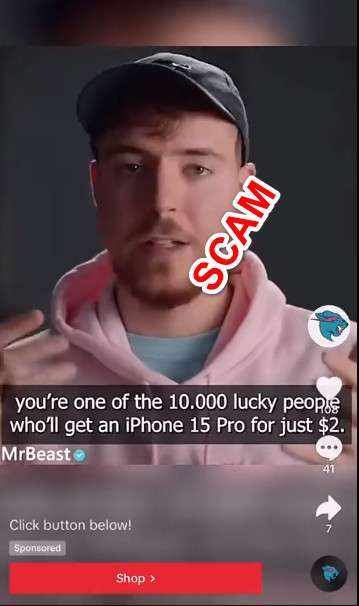
A fraudulent sponsored advertisement has been circulating on TikTok in recent weeks showing a deepfake version of YouTuber MrBeast announcing a contest giving away 10,000 free iPhone 15 Pro devices for only $2 each. The deceitful video directs users to a fake website that aims to steal personal information and money. Here’s what you need to know about how this “MrBeast iPhone 15” scam works and how to avoid becoming a victim.
Overview of the “MrBeast 10,000 iPhone 15 Pro For $2” Scam
A deceptive sponsored video has gone viral on TikTok in recent weeks, racking up millions of views and dupeing thousands into providing their personal information. This fraudulent ad shows a synthesized deepfake version of famous YouTuber MrBeast appearing to promote an iPhone 15 giveaway for just $2 per device.
“If you’re seeing this video right now, then you’re one of the lucky 10,000 people who can get the new iPhone 15 Pro completely free – all you have to pay is $2 for shipping,” the faux MrBeast states.
This unbelievable offer and use of MrBeast’s likeness is entirely fake and designed to scam viewers. The video directs users to a phishing website mimicking MrBeast’s official site. On this fraudulent domain, victims are instructed to enter sensitive personal, financial and account login details under the guise of claiming their $2 iPhone 15.
In reality, the data harvested is used by scammers to steal identities and money through fraudulent purchases, account hijacking, opening loans under the victim’s name and more. No iPhones are ever shipped out.
By the time users realize it was a scam, significant damage has often already been done through stolen funds and compromised personal data now sold on the dark web. The Federal Trade Commission has received numerous reports of victims falling for this viral TikTok ruse, underscoring the need for greater awareness about deceptive deepfake content on social media.
This scam represents a dangerous new evolution of fraud for platforms like TikTok. AI-generated synthetic media can make fake promotions and phishing schemes seem incredibly life-like and convincing, fooling significant numbers of users. Learn to recognize the red flags of this iPhone 15 con, think critically about unbelievable offers online, and report any scams to protect yourself and others.
How the Deepfake MrBeast 10,000 iPhone 15 Pro For $2 Scam Works
The “MrBeast 10,000 iPhone 15 Pro For $2” scam operates in several key stages to convince victims, gather their information, and generate illicit profits for scammers:
1. Crafting a Believable Deepfake Video of MrBeast
The scammers utilized advanced deepfake technology to digitally impose MrBeast’s face and voice into a video announcing the fake iPhone 15 contest. Deep learning algorithms can analyze many images, videos and audio clips of a person to produce an extremely lifelike replica.
The resulting AI-generated synthetic MrBeast displays natural facial expressions, lip syncing, and body language that makes the footage seem 100% authentic. This adds huge credibility to the scam offer.
2. Promoting the Deepfake Ad Widely on TikTok
Once created, the fraudsters paid to amplify the fabricated MrBeast video as a sponsored advertisement to reach a massive viewership on TikTok. Propagating through paid promotion and TikTok’s viral algorithm, the deepfake ad garnered millions of views.
The compelling offer of a $999 iPhone 15 Pro for just $2 proved enticing enough to continuously improve engagement metrics. TikTok then extended its reach further through additional algorithmic recommendations.
3. Directing Victims to a Deceptive Phishing Website
When users click the link in the deepfake video description, it brings them to a fake website designed to precisely mimic the appearance of an official MrBeast portal. The look and feel of the site helps build further trust in the scam.
No indicators on the page suggest it is fraudulent. However, inspection of the URL reveals it is slightly different than MrBeast’s real domain, using deceptive tricks to seem valid.
4. Collecting Personal and Financial Information
On the phishing site, users see instructions to enter their details into a registration form to claim their $2 iPhone 15 Pro unit. Information collected includes:
- Full name
- Home address
- Email address
- Phone number
- Credit card number
- Card expiration date
- CVV security code
- Bank account login credentials
An additional $10 shipping fee is requested to “cover delivery” of the non-existent iPhone.
5. Stealing Data for Financial Fraud and Identity Theft
With the user’s information harvested, the scammers can now use it to commit identity theft, charge fraudulent purchases to credit cards, drain bank accounts, take out loans in the victim’s name, file fake tax returns, hack into other accounts, resell data on the dark web, and more.
Meanwhile, the user waits for an iPhone 15 Pro that will never arrive. Any attempts to contact “MrBeast” about the order status go unanswered.
In the aftermath, victims are often left dealing with significant account breaches, damaged credit, and stolen funds in addition to never receiving the promised iPhone 15.
What To Do If You Fell for the MrBeast iPhone 15 Scam
If you supplied any personal or financial data to the fraudulent MrBeast iPhone website, here are important steps to take right away:
Contact Your Credit Card Company and Bank
Immediately call your credit card provider if you entered your card details on the phishing site. Report the charges as fraudulent so they can begin monitoring activity and send replacement cards with new account numbers.
Also request any recent unauthorized transactions be reversed. Speak to your bank as well to place alerts on all connected accounts in case the scammers try other withdrawal methods. Closely track statements for any suspicious charges.
Reset All Account Passwords
If you reused the same password entered on the scam site for any other online accounts, change them all immediately. Use strong unique passwords for every account going forward. Enable two-factor authentication wherever possible for an added layer of login security.
Check Your Credit Reports
Visit AnnualCreditReport.com to check your credit reports from Equifax, Experian and TransUnion. Look for any new accounts or loan inquiries you don’t recognize as these may indicate identity theft. You can also place a credit freeze to lock down your credit reports from scammers.
Monitor Accounts Closely
Keep close watch on your financial statements, credit reports and online accounts for any unusual activity indicating misuse of your data by criminals. Ensure you recognize every transaction, account and login attempt. Report anything suspicious promptly.
Avoid Further Phishing Attempts
Disregard any emails about confirming iPhone orders or requesting more details to process your supposed $2 iPhone 15 Pro. The scammers may use this info gathering ruse again via phishing emails. Do not open any links, attachments or respond with more personal data.
File Reports About the Scam
Submit a scam complaint with the FTC at ReportFraud.ftc.gov and flag the fraudulent video to TikTok so they can remove it and ban associated accounts. Reporting the rip-off helps authorities identify and stop scams faster.
By taking swift precautions, you can greatly limit the fallout from this scam. But remain vigilant about other potential schemes targeting your information moving forward.
Frequently Asked Questions About the Viral “MrBeast $2 iPhone 15” Scam
A fraudulent TikTok ad featuring an AI-generated deepfake of YouTuber MrBeast is promoting a scam iPhone 15 giveaway. Here are answers to common questions about this viral con targeting his fans.
What Exactly is This Scam About?
The scam uses a fake sponsored video of MrBeast claiming he is giving away 10,000 free iPhone 15 Pro units for just $2 each. It directs victims to a phishing website gathering personal data to commit identity theft and financial fraud. No actual iPhones are being awarded.
How Does this MrBeast Deepfake Scam Work?
- Scammers craft a deceptive video of MrBeast using deepfake AI technology.
- This fake ad spreads widely on TikTok through paid promotion and viral shares.
- The video description links to a phishing site mimicking MrBeast to build trust.
- Users are instructed to enter personal and payment data to claim an iPhone 15.
- Criminals steal this info to make fraudulent purchases and commit identity theft.
What Red Flags Indicate This Giveaway is Fake?
- Offering the latest iPhone model worth $999 for only $2 is unrealistic.
- Urgency to act fast before the invented limited supply is gone.
- Requesting extensive personal/financial data unnecessary for a contest.
- Using deepfakes instead of real endorsements from reputable sources.
- Subtle differences in the phishing URL from MrBeast’s actual site.
What Information is Being Collected?
The phishing site gathers a concerning amount of private user data including:
- Full name, home address, email address, phone number
- Credit/debit card numbers, security codes, expiration dates
- Bank account login credentials
- Passport/ID information
What Should I Do If I Shared My Information?
If you entered any data on the fraudulent website, take these steps immediately:
- Contact your bank to monitor accounts for unauthorized charges.
- Reset all account passwords and enable two-factor authentication on logins.
- Check credit reports for any suspicious new accounts or loan inquiries.
- Watch closely for any phishing follow-ups requesting more information. Do not respond.
- Report the scam to the FTC and TikTok to have the fake content removed.
How Can I Spot Similar Scams in the Future?
Look for these giveaways signs of a fraudulent offer online:
- Extremely low prices on expensive products.
- High pressure tactics urging fast action.
- Requests for personal details unnecessary for giveaways.
- Spelling/grammatical errors and strange URLs on linked sites.
- Lack of real contact information for the company.
- No actual terms and conditions describing the giveaway rules.
The Bottom Line
This “MrBeast 10,000 iPhone 15 Pro For $2” giveaway scam illustrates the serious threat posed by increasingly convincing deepfake technology on social media. While TikTok deleted the fake ad after MrBeast reported it, critics argue the platform’s protections still fail to catch many deceptive deepfakes before they go viral.
The scam was designed to take advantage of MrBeast’s fame and reputation around contests to fabricate a compelling promotion few would suspect as fraudulent. But users should remember that if an online deal seems too good to be true, it almost always is.
Guard your personal information closely, implement strong passwords, scrutinize links and offers carefully, and report any scams you encounter. Staying alert to red flags like unbelievable prices and requests for excessive personal details can help you steer clear of deepfake cons trying to hook the next victim.

![How to Remove 30dcf.com Pop-ups [Virus Removal Guide] 4 McAfee scam 4](https://malwaretips.com/blogs/wp-content/uploads/2023/08/McAfee-scam-4-290x290.jpg)