“Recommended for you” is a computer virus, which will display pop-ups containing advertisements and sponsored links, with the sole purpose of generating revenue for the cyber criminals.
The “Recommended for you” pop-up ads will be appear in the bottom right corner of the browser window, either as a box containing sponsored links, or in the form of an iPhone with advertisements.
- “Recommended for you” pop-ups – Virus Removal Guide
- STEP 1: Remove “Recommended for you” infection with Kaspersky TDSSKiller
- STEP 2: Remove “Recommended for you” malicious files with Malwarebytes Anti-Malware FREE
- STEP 3: Remove “Recommended for you” rootkit with HitmanPro
- STEP 5: Remove “Recommended for you” redirects from Internet Explorer, Firefox and Google Chrome
- STEP 6: Remove “Recommended for you” residual damage from your browser with AdwCleaner

This infection is designed specifically to make money. It generates web traffic, collects sales leads for other dubious sites, and can display advertisements and sponsored links within your web browser.
The “Recommended for you” virus is distributed through several means. Malicious websites, or legitimate websites that have been compromised, may drop this trojan onto a compromised computer. This drive-by-download often happens surreptitiously. Another method used to propagate this type of malware is spam email containing infected attachments or links to malicious websites. The threat may also be downloaded manually by tricking the user into thinking they are installing a useful piece of software.
The “Recommended for you” virus is also prevalent on peer-to-peer file sharing websites and is often packaged with pirated or illegally acquired software.
Once install on a computer, “Recommended for you” virus will modify the HOSTS file and will drop several other malicious files which will cause browse redirects to malicious websites.
Furthermore, this virus will also install a browser extension which will display advertisements pop-ups on Facebook, Amazon, Google and other websites that you are visiting.
![Recommended for you virus [Image: Recommended for you virus]](http://malwaretips.com/blogs/wp-content/uploads/2013/05/recommended-for-you-virus.jpg)
These “Recommended for you” pop-ups cannot be closed because their isn’t any option to do so, and the only solution to remove this pop-ups is to click on the advertisement.
“Recommended for you” is a scam and a malicious software, we strongly recommend that you remove this trojan from your computer as soon as possible.
“Recommended for you” pop-ups – Virus Removal Guide
STEP 1: Remove “Recommended for you” infection with Kaspersky TDSSKiller
As part of its self defense mechanism, “Recommended for you” virus will install a ZeroAccess rootkit on the infected computer.In this first step, we will run a system scan with Kaspersky TDSSKiller to remove this rookit.
- Please download the latest official version of Kaspersky TDSSKiller.
KASPERSKY TDSSKILLER DOWNLOAD LINK(This link will automatically download Kaspersky TDSSKiller on your computer.) - Before you can run Kaspersky TDSSKiller, you first need to rename it so that
you can get it to run. To do this, right-click on the TDSSKiller.exe icon and select Rename.
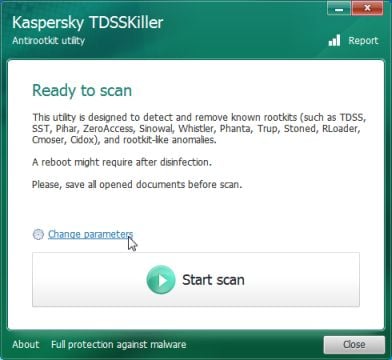
Edit the name of the file from TDSSKiller.exe to iexplore.exe, and then double-click on it to launch. - Kaspersky TDSSKiller will now start and display the welcome screen and we will need to click on Change Parameters.
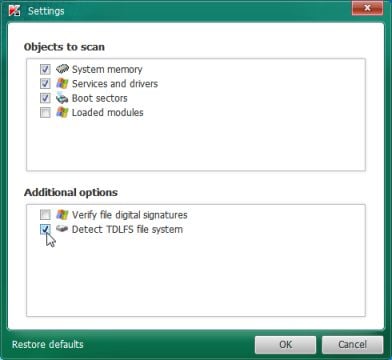
- In the new open window,we will need to enable Detect TDLFS file system, then click on OK.
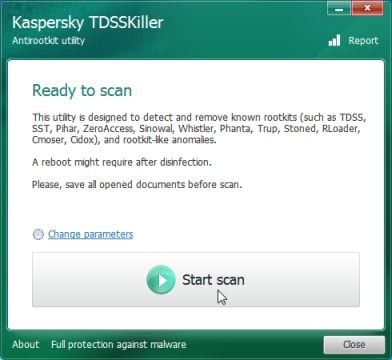
- Next,we will need to start a scan with Kaspersky, so you’ll need to press the Start Scan button.
- Kaspersky TDSSKiller will now scan your computer for “Recommended for you” virus.
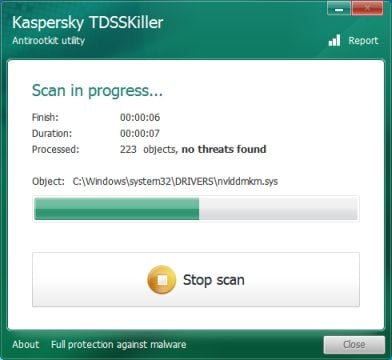
- When the scan has finished it will display a result screen stating whether or not the infection was found on your computer. If it was found it will display a screen similar to the one below.
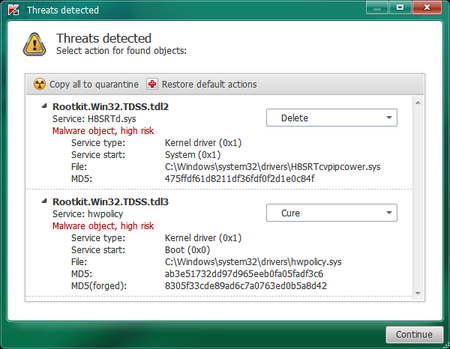
- To remove the infection simply click on the Continue button and TDSSKiller will attempt to clean the infection.A reboot will be require to completely remove any infection from your system.
STEP 2: Remove “Recommended for you” malicious files with Malwarebytes Anti-Malware FREE
Malwarebytes Anti-Malware is a powerfull on-demand scanner which will remove “Recommended for you” malicious files from your computer.
- You can download Malwarebytes Anti-Malware Free from the below link, then double click on it to install this program.
MALWAREBYTES ANTI-MALWARE DOWNLOAD LINK (This link will open a download page in a new window from where you can download Malwarebytes Anti-Malware Free) - When the installation begins, keep following the prompts in order to continue with the setup process. DO NOT make any changes to default settings and when the program has finished installing, make sure you leave both the Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware checked,then click on the Finish button.
![Malwarebytes Anti-Malware final installation screen [Image: Malwarebytes Anti-Malware final installation screen]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-installation.jpg)
- On the Scanner tab,select Perform quick scan and then click on the Scan button to start scanning your computer.
![Run a Quick Scan with Malwarebytes Anti-Malware [Image: Malwarebytes Anti-Malware Quick Scan]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-quick-scan.jpg)
- Malwarebytes’ Anti-Malware will now start scanning your computer for “Recommended for you” malicious files as shown below.
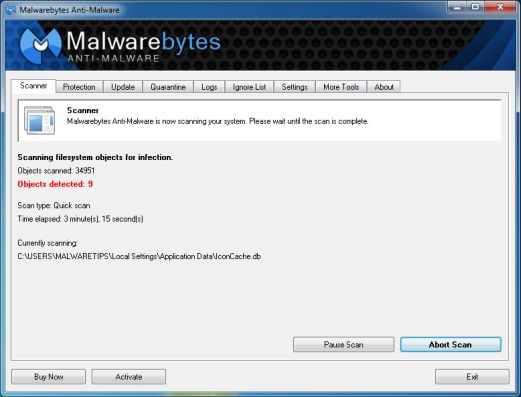
- When the Malwarebytes scan will be completed,click on Show Result.
![Malwarebytes when the system scan has completed [Image: Malwarebytes Anti-Malware scan results]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-scan-results.jpg)
- You will now be presented with a screen showing you the malware infections that Malwarebytes’ Anti-Malware has detected.Please note that the infections found may be different than what is shown in the image.Make sure that everything is Checked (ticked) and click on the Remove Selected button.
![Click on Remove Selected to get rid of [Image:Malwarebytes removing virus]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-virus-removal.jpg)
- After your computer restarts, open Malwarebytes Anti-Malware and perform a full system scan to verify that there are no remaining threats.
STEP 3: Remove “Recommended for you” rootkit with HitmanPro
In some cases,”Recommended for you” will also install a rootkit on victims computer.To remove this rootkit we will use HitmanPro.
- Download HitmanPro from the below link,then double-click on it to start this program.
HITMANPRO DOWNLOAD LINK (This link will open a new web page from where you can download HitmanPro)
IF you are experiencing problems while trying to start HitmanPro, you can use the Force Breach mode.To start HitmanPro in Force Breach mode, hold down the left CTRL key when you start HitmanPro and all non-essential processes are terminated, including the malware process. (How to start HitmanPro in Force Breach mode – Video) - HitmanPro will start and you’ll need to follow the prompts (by clicking on the Next button) to start a system scan with this program.
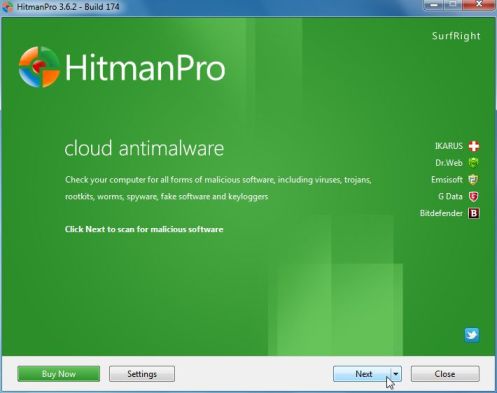
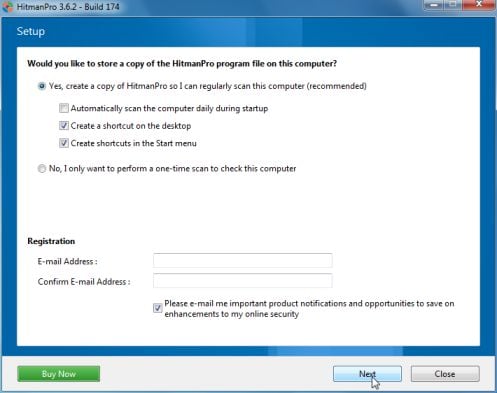
- HitmanPro will start scanning your computer for “Recommended for you” malicious files as seen in the image below.
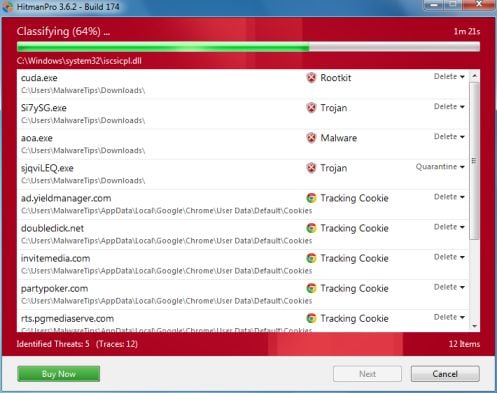
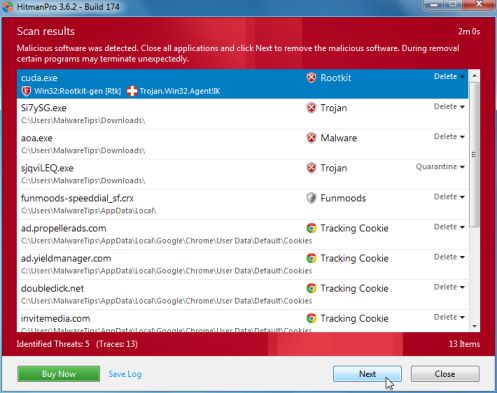
- Once the scan is complete,you’ll see a screen which will display all the infected files that this utility has detected, and you’ll need to click on Next to remove this malicious files.
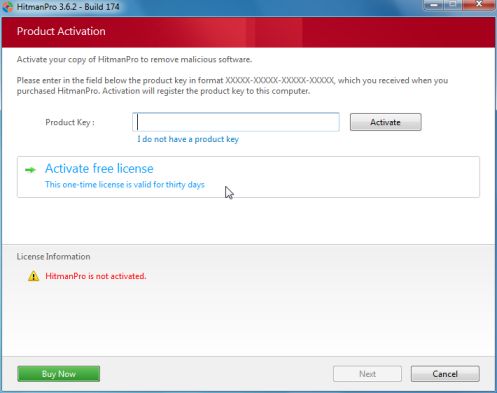
- Click Activate free license to start the free 30 days trial and remove all the malicious files from your computer.
STEP 4: Reset the Windows Hosts file back to its default settings
The “Your website access has been restricted for downloading pirated software” trojan has modified your Hosts file, so that you’ll be redirected to those survey websites. To reset the Hosts file back to its default settings, we will run Microsoft Fix it 50267, however because usually the cyber criminals have changed the permissions for the HOSTS file, we will first need to revert this modification.
- Hosts-perm.bat is a batch file that will reset the permissions for the Windows HOSTS file.
This infection will change the permissions on the HOSTS file so that you are unable to delete it or modify it. Hosts-perm.bat will reset these permissions so that you will once again have full access to it.
You can download Hosts-perm.bat from the below link:
HOSTS-PERM.BAT DOWNLOAD LINK (This link will open a new web page from where you can download Hosts-perm.bat)
Double-click the hosts-perm.bat file and when it is done you will see a message stating “The Permissions on the HOSTS file have been reset.”.Press any key on your keyboard to exit the batch file. - Download Microsoft Fix it 50267 from the below link.
MICROSOFT FIX IT 50267 DOWNLOAD LINK (This link will automatically download Microsoft Fix it 50267 on your computer) - Double click on MicrosoftFixit50267, then follow the prompts to reset your Windows Hosts file.
![Reset Hosts file back to default settings [Image: Repair HOSTS file]](//malwaretips.com/blogs/wp-content/uploads/2013/03/reset-hosts-file.jpg)
STEP 5: Remove “Recommended for you” redirects from Internet Explorer, Firefox and Google Chrome
Remove “Recommended for you” from Internet Explorer
- Open Internet Explorer, click on the gear icon
![Remove "Recommended for you" pop-up virus (Removal Guide) 2 [Image: icongear.jpg]](//malwaretips.com/images/removalguide/icongear.jpg) (Tools for Windows XP users) at the top (far right), then click again on Internet Options.
(Tools for Windows XP users) at the top (far right), then click again on Internet Options.
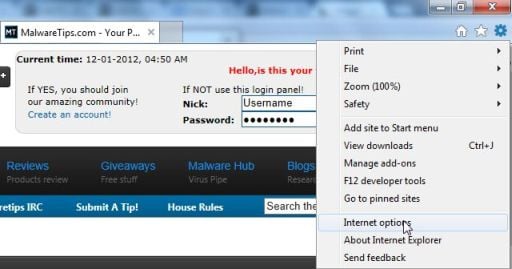
- In the Internet Options dialog box, click on the Advanced tab, then click on the Reset button.
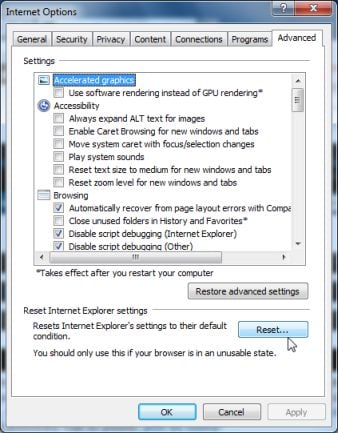
- In the Reset Internet Explorer settings section, check the Delete personal settings box, then click on Reset.
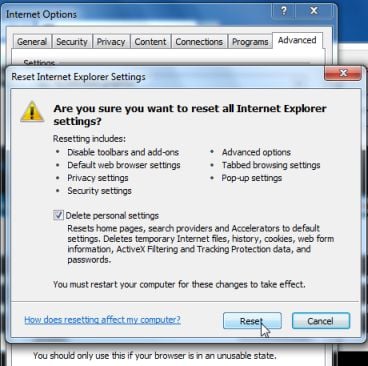
- When Internet Explorer finishes resetting, click Close in the confirmation dialogue box and then click OK.
- Close and open Internet Explorer.
Remove “Recommended for you” from Mozilla Firefox
- At the top of the Firefox window, click the Firefox button, go over to the Help sub-menu (on Windows XP, click the Help menu at the top of the Firefox window), and select Troubleshooting Information.
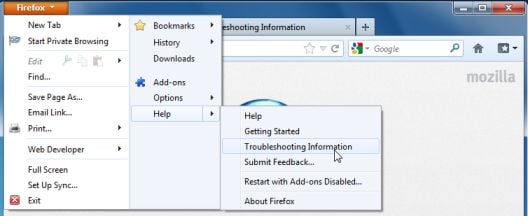
- Click the Reset Firefox button in the upper-right corner of the Troubleshooting Information page.
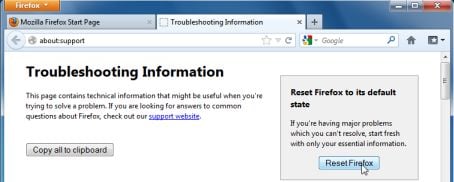
- To continue, click Reset Firefox in the confirmation window that opens.
- Firefox will close and be reset. When it’s done, a window will list the information that was imported. Click Finish
Remove “Recommended for you” from Google Chrome
- Click the Chrome menu
 button on the browser toolbar, select Tools and then click on Extensions.
button on the browser toolbar, select Tools and then click on Extensions.
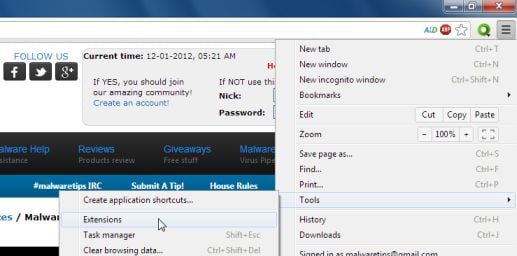
- In the Extensions tab, remove (by clicking on the Recycle Bin button) Flash Player Update 11.0 and any other unknown or unwanted extensions.
STEP 6: Remove “Recommended for you” residual damage from your browser with AdwCleaner
- You can download AdwCleaner from the below link.
ADWCLEANER DOWNLOAD LINK (This link will automatically download AdwCleaner on your computer) - Before starting this utility, close all open programs and internet browsers.
- Double click on adwcleaner.exe to run the tool.
- Click on Delete, then confirm each time with Ok.

- Your computer will be rebooted automatically. A text file will open after the restart.
- NEXT, double click on adwcleaner.exe to run the tool.
- Click on Uninstall, then confirm with yes to remove this utility from your computer.

![Remove "Recommended for you" pop-up virus (Removal Guide) 1 [Image: Recommended for you virus]](https://malwaretips.com/blogs/wp-content/uploads/2013/05/recommended-for-you-virus.jpg)





![Malwarebytes Anti-Malware final installation screen [Image: Malwarebytes Anti-Malware final installation screen]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-installation.jpg)
![Run a Quick Scan with Malwarebytes Anti-Malware [Image: Malwarebytes Anti-Malware Quick Scan]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-quick-scan.jpg)

![Malwarebytes when the system scan has completed [Image: Malwarebytes Anti-Malware scan results]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-scan-results.jpg)
![Click on Remove Selected to get rid of [Image:Malwarebytes removing virus]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-virus-removal.jpg)





![Reset Hosts file back to default settings [Image: Repair HOSTS file]](http://malwaretips.com/blogs/wp-content/uploads/2013/03/reset-hosts-file.jpg)








![Remove Cosmobotshield.co.in Pop-up Ads [Virus Removal Guide] 6 McAfee scam 4](https://malwaretips.com/blogs/wp-content/uploads/2023/08/McAfee-scam-4-290x290.jpg)