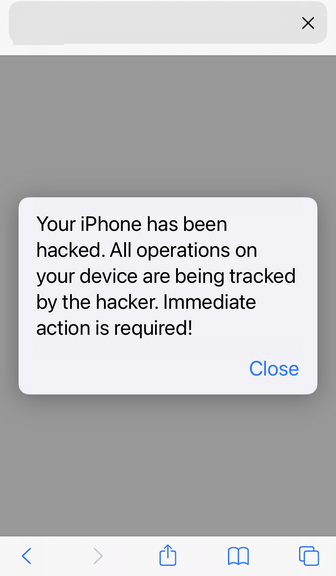
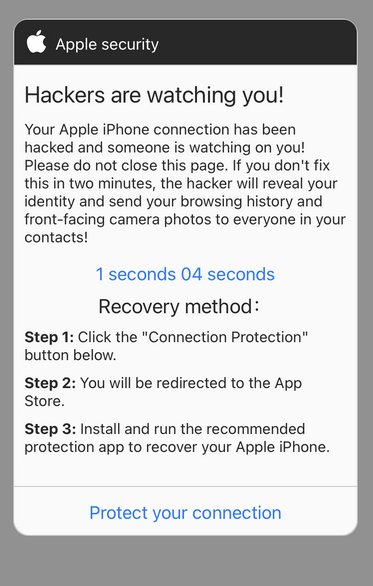
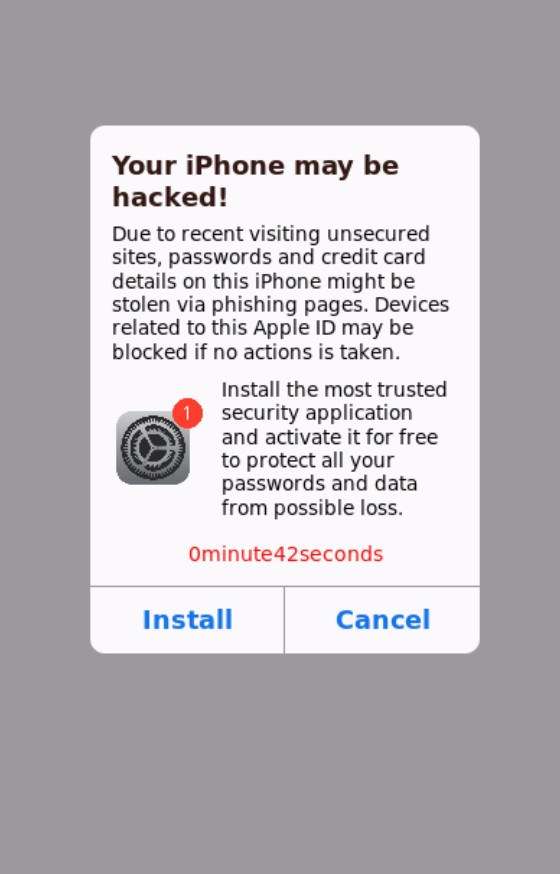
You’re browsing on your iPhone when a scary pop-up appears warning “Your iPhone Has Been Hacked.” It claims malicious spyware was detected on your iOS device. The message demands you call a support number immediately to remove the hackers. This dire alert seems concerning, but hold up – it’s actually a devious scam.
The “iPhone Hacked” pop-up scam has spread rapidly through shady ads and sites. The pop-ups use fear tactics about device takeovers to trick users. If you call the number, you’ll compromise your iPhone instead of securing it.
In this comprehensive guide, we’ll break down how this iPhone scam works, what the real motives are, and most crucially, how to avoid becoming a victim.
Overview of the iPhone Hacked Scam
The iPhone Hacked scam preys on fears of device hijacking and privacy theft. The pop-ups display an alarming message that hackers have infected your iPhone or iPad with spyware.
To remove the supposed infection, you are instructed to call the listed support number right away. This will purportedly allow Apple to delete the hackers and malware.
But here’s the catch – the phone number actually connects you to smooth-talking scammers pretending to be Apple support. They can remotely access your iPhone under the guise of removing viruses.
In reality, this gives them a gateway to install real spyware, steal private data, and further compromise your device security.
This social engineering attack exploits urgency to make users abandon caution and call the fraudulent number. Stay vigilant against this dangerous iPhone-targeted ruse.
How the iPhone Hacked Scam Works
Attackers have crafted this scam into an efficient multi-stage ploy to ensnare victims and profit. Here’s an inside look at how it unfolds:
Stage 1 – Scare Tactic Pop-Under Ads
The scam starts with malicious ads served through shady networks running pop-under ads. The ads evade blockers and use timers to appear.
Once displayed, the pop-unders show the alarming “iPhone Hacked” warnings to spark panic about device takeovers.
Stage 2 – Spoofed iOS Alert Style
The pop-ups precisely mimic the aesthetics and wording of real iOS security alerts. Names like “Apple Security Center” are used to seem legitimate.
Images and icons are copied from Apple to make the scam pop-ups look convincing at first glance.
Stage 3 – Social Engineering Manipulation
The text instills urgency by warning your iPhone is already under hacker control. Threats of stolen data, surveillance, and device damage scare users into calling the number immediately.
Countdown timers, progress bars, and other visuals add to the pressure to call right away before it’s too late.
Stage 4 – Fake Apple Support
When users call the number, smooth-talking scammers posing as Apple support pretend to detect massive infections. They offer to fix it by remotely accessing the iPhone.
This gives them full control to stealthily install spyware, steal data, take pictures, harvest emails, and hold the phone for ransom.
Stage 5 – Ongoing Abuse
With remote access granted, the scammers can:
- Monitor all online activity, messages, and logins
- Brick devices and demand payment to unlock them
- Remotely install banking trojans and crypto miners
- Leverage saved credentials to access financial and social media accounts
- Resell access to the compromised device on dark web markets
This allows endless abuse and monetization of the hacked iPhone over time.
Avoiding iPhone Hacked Scams
Now that you know this scam’s misleading tactics, here are tips to avoid becoming a victim:
- Use an ad blocker like AdGuard to stop the scam ads from appearing in the first place.
- If an iPhone alert pops up, don’t instantly panic. Verify it’s really from Apple before calling any numbers.
- Never call or give remote access to unsolicited numbers claiming device hacks or security issues.
- Hang up immediately if a caller claims to be Apple support and asks to remote access your device.
- Keep your iPhone’s iOS version updated and use security tools like Norton Mobile Security.
- Avoid shady websites and apps that may serve as vectors for malware or unwanted profiles.
- Use strong passcodes and two-factor authentication everywhere for account security.
- Setup automatic backups so you can easily wipe your iPhone and restore if it’s ever compromised.
What to Do if You Fell for This Scam
If you called the phone number and granted remote access, take these steps to undo the damage:
- Force restart your iPhone to disconnect any remote access.
- Change ALL passwords immediately from a different device. Prioritize financial accounts and email.
- Contact your bank and credit card companies to report unauthorized charges or accounts opened in your name.
- Remove any suspicious apps you didn’t install and reset iPhone to factory settings.
- Check connected accounts like iCloud and social media for posts made by scammers.
- Run security scans using tools like Malwarebytes to detect potential lingering threats.
- Monitor all accounts closely for fraudulent activity indicating wider identity theft.
Though falling victim can have serious repercussions, acting swiftly can help contain the damage and regain control of your device security.
The End Goal of This iPhone Scam
The “iPhone Hacked” scam aims for several opportunistic goals:
1. Charging Victims for Unneeded Services
If users grant remote access, the fake Apple support scammers can charge exorbitant amounts for useless “security” services. These fees quickly rack up through credit cards.
2. Stealing Personal Data
With backdoor access, the scammers can harvest and sell sensitive photos, messages, emails, contacts and other private data from the iPhone.
3. Financial Account Access
Once inside the iPhone, scammers leverage saved passwords and cookies to log into banking and financial accounts for theft and fraudulent transactions.
4. Ransoming Devices
Scammers can encrypt files or brick the iPhone entirely, holding it hostage until the owner pays a ransom to regain functionality.
In essence, the iPhone hacked scam converts phone access into endless monetary gain through theft, extortion, and selling off data – making it highly alluring to criminals.
Frequently Asked Questions
What is the “Your iPhone Has Been Hacked” pop-up scam?
This is a deceptive pop-up that claims hackers infected your iPhone with spyware. It instructs you to call a number so Apple can supposedly remove the hackers. But the number actually connects you to scammers who can install real malware.
How does the pop-up appear on my iPhone?
It shows up through malicious third-party ads on shady websites. The pop-under ads mimic real iOS security alerts.
What happens if I call the phone number listed?
You’ll be connected to smooth-talking scammers pretending to be Apple support. They can gain remote access to your iPhone under the pretense of removing viruses, and install spyware or steal data.
What’s the end goal of this scam?
The scammers want to charge victims money for fake services, steal personal data, access financial accounts, hold devices for ransom, or resell device access on the dark web.
Can I trust iPhone security pop-up warnings?
No, legitimate Apple alerts would never tell you to call a third-party number. Assume any pop-up demanding you call about hackers is a scam attempt.
How can I remove malware if I fell for this?
Immediately change ALL passwords from a different device. Contact banks about unauthorized charges. Remove suspicious apps. Wipe and reset your iPhone. Check connected accounts for scammer misuse.
How can I avoid this scam in the future?
Use ad blockers, don’t call or click pop-ups, keep iPhone software updated, avoid shady sites, hang up on unsolicited support calls, use strong passcodes everywhere, and setup backups.
Does this scam only target iPhones?
While styled as an iPhone alert, the scam can target Android and other smartphones too. Scammers aim to infect as many mobile devices as possible.
Closing Thoughts
Pop-up scams that instill urgency via fake security warnings threaten all devices – including iPhones. But understanding the social engineering tactics allows you to recognize and avoid the scam.
No legitimate iOS alert will demand immediate calls to unverified numbers. Use caution rather than haste if faced with a dire-sounding pop-up.
With proper precautions, you can keep your iPhone free of intruders and infections – without fear of alarmist security scams trying to fool you for profit. Don’t let them prey on fear.