The release of the highly anticipated Grand Theft Auto VI trailer on December 5th, 2023 has unfortunately been accompanied by nefarious activity seeking to capitalize on unsuspecting fans. Just two days after Rockstar debuted footage from the upcoming GTA title, scammers have wasted no time in launching fake “giveaways” promoting GTA VI while fraudulently impersonating the Rockstar brand.
These sham crypto giveaways superficially resemble legitimate promotions, brazenly sporting official Rockstar and GTA insignia. However, they hide sinister intentions underneath the glossy veneer. This article will uncover the devious inner workings powering this scam, provide guidance on protecting yourself online, and deliver steps to take if you’ve already been victimized.
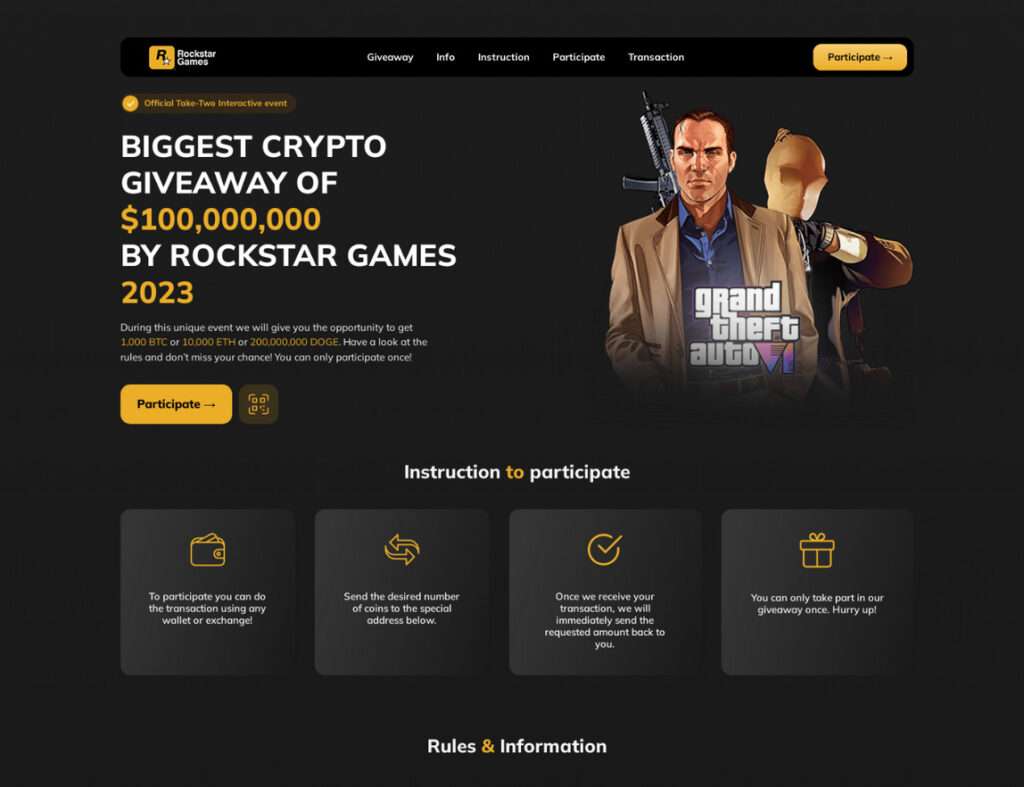
Overview of the GTA VI Crypto Scam
The fundamental strategy underpinning the Rockstar Games GTA VI crypto giveaway scam is quite simple: attackers want to separate victims from their digital assets under false pretenses. Promotional language tantalizes participants with extravagant cryptocurrency prizes valued at $100 million, including “1,000 BTC or 10,000 ETH or 200,000,000 DOGE.”
Lured by visions of exorbitant rewards, victims are persuaded to transfer their own crypto holdings to digital wallets controlled by scammers. Victims are led to believe these transactions are necessary to “activate” the promised giveaway payouts.
In reality, participants are transmitting funds directly into the hands of criminals who have no intentions of rewarding them. The advertised giveaways, prize calculators, and doubled returns are complete illusions fabricated to facilitate theft.
These GTA VI crypto scams capitalize on the anticipation surrounding the game’s launch to ensnare unsuspecting fans. By professing admiration for Rockstar’s work, mimicking official branding assets, and referencing milestone events like new trailer premieres, they cultivate an air of legitimacy.
However, investors must exercise extreme caution to avoid entrusting assets to deceitful schemes hiding behind the Rockstar name. Acting quickly to identify and sidestep such scams is imperative to safeguarding financial stability.
Hallmarks of the Fraudulent GTA VI Promotions
Several consistent traits can help distinguish the counterfeit crypto giveaways from authentic events:
- Usage of Rockstar Games’ trademarks without permission
- Promises of disproportionate rewards (like doubling deposits)
- “Time-limited” pressures to compel hasty decision making
- Poor grammar, spelling slip-ups, stylistic issues
- Inconsistent domain names and website credentials
- No association with reputable crypto wallets or exchanges
- No verified social media presence or customer service channels
Criminals conducting these scams essentially bathe themselves in Rockstar’s brand legitimacy without actually maintaining any formal ties to the video game publisher. Avoiding affiliation with regulated financial entities also frees them to operate outside laws dictating acceptable fund management practices.
Massive Scale Cybercrime Campaign
Due to GTA’s recognition as an iconic cultural franchise beloved by millions internationally, attackers have crafted an expansive fraudulent ecosystem around these giveaways.
The implementations follow extremely similar templates, featuring slight logo and prize pool variations while rerouting to common destinations. Many rely on basic site cloning tactics, copying elements directly from Rockstar’s official pages.
Such large volumes allow orchestrators to cast an extremely wide net at negligible relative cost. Experts posit sophisticated hacking collectives are likely coordinating these dissemination strategies, leveraging botnets and malware to infect vulnerable devices.
If even a tiny fraction of visitors transfer funds, the orchestrators still walk away enormously profitable given participation scales. With reputational assets like GTA driving interest, the campaigns unfortunately tend to thrive.
How the GTA VI Crypto Scams Work
Attackers rely on multiple forms of deception to facilitate their GTA VI crypto cons. By understanding their step-by-step methods, investors stand a better chance of detecting signs of fraud before engagement.
Step 1: Directing Traffic to Scam Websites
Luring victims begins by funneling web traffic towards fraudulent portal sites granting access to the sham giveaways. Scammers harness email spamming, search engine manipulation, social media impersonation, pop-up advertisements, and malware injections as user acquisition vectors.
Spam campaigns in particular blast out emails boasting tantalizing subject lines like “Claim your GTA VI rewards now!” to millions. Curious recipients who click embedded links get rerouted to scam landing pages.
Step 2: Harvesting User Information
Upon arriving at portal sites, users witness flashy graphics touting extravagant cryptocurrency prizes, accompanied by requests to “connect your wallet” or “input your details.” If participants comply, attackers gain account login credentials granting direct asset access.
Some portals even pressure visitors to download executable files by promising advanced giveaway eligibility. These contain embedded keylogging malware capturing everything typed into infected devices. Either method provides keys to the victim’s financial kingdom.
Step 3: Fueling The Illusions
After securing account access, scammers leverage additional smoke and mirror tactics to string victims along until funds get extracted. Fake “progress trackers” update balances to reflect false transfers from Rockstar Games, quando non-existent prize pools.
Browser extensions are also deployed showing crypto transfers from attackers’ wallets to victims. However, these transfers only display locally to reinforce perceptions that “rewards” are en route. No actual asset movement occurs, but victims observing the mimicked transactions may remain convinced otherwise.
Step 4: Draining the Accounts
Finally, once targets’ defenses are softened under the weight of multi-pronged illusions, scammers directly siphon as many assets as possible from compromised wallets. With access rights secured from harvested logins or malware, attackers issue legitimate transfers sending victims’ holdings straight into their own criminal coffers.
By this final stage, counterfeit sites may suddenly display ransomware messages demanding payment to unlock access. However, given the financial damage already inflicted, even meeting ransom demands likely will not salvage much.
Step 5: Disposing the Evidence
As a finishing move, attackers quickly dismantle supporting infrastructure to conceal traces of illegitimate activity. Fraudulent domains get taken offline, keylogging malware uninstalled from devices, and tracing identifiers scrubbed from transactions.
Within days of accumulating sufficient assets from victims, the entire scam operation vanishes. All that remains are empty wallets and unanswered questions for authorities attempting to pursue accountability.
For orchestrators, rinsed infrastructure gets rebuilt around the next lucrative viral event. And thus the predatory cycle continues enabled by new fraud techniques and naive targets.
Here is an additional SEO optimized section with examples on how to spot GTA VI crypto scam websites:
How to Spot GTA VI Crypto Scam Websites
As scammers build increasingly sophisticated fraudulent websites to ensnare victims, arming yourself with critical identification tips helps avoid entanglement. Look for these common red flags when evaluating any website promoting GTA VI cryptocurrency giveaways:
1. Suspicious Domain Properties
Fraudulent sites often sport domains comprised of random characters or containing typos of the Rockstar brand, such as “Roackstargames”. Scammers also frequently register sites using top-level domains like .net instead of .com to superficially mimic legitimate sites.
For example, the fraudulent domain “rockstargames.net” blends in easily alongside the real “rockstargames.com” at first glance. Check site domains carefully when assessing legitimacy.
2. Promotional Impracticalities
If promotional language boasts disproportionate incentives like “Send 1 BTC to receive 200 BTC free,” likelihood points to fraud. No legally compliant company gifts assets at such irrational rates. Suppose proposed “giveaways” sound too extravagant compared to reasonable marketing. In that case, you have likely uncovered a con.
3. Text Content and Imagery
Poor grammar, spelling inconsistencies, stylistic issues, and low-quality images all indicate scam attempts. Genuine brands like Rockstar thoroughly polish public-facing content and imagery.
Amateur mistakes spotlight insufficient effort invested to sell scams convincingly. Always quadruple check finer details.
Identifying GTA VI Crypto Scams on Social Media
Beyond fraudulent websites, GTA VI cybercriminals leverage social platforms to promote giveaways disguising their true intentions. Exercising caution when interacting with potential scams on networks like Facebook, Instagram, and TikTok saves investors from compromising consequences.
Spotting GTA VI Scams on Facebook
Fraudulent Facebook crypto promoters typically mirror official Page naming while lacking verification badges. For example, an imposter “Rockstar Games” profile with a profile pic of the iconic Rockstar “R” logo may seem convincing, but lacks the blue checkmark indicating an authentic business presence.
Investigator imposter About and Contact info sections as well. Scam Pages display nonsensical locations like “Rockstar HQ City” or feature email addresses from free providers. Legitimate companies display legitimate contact information and locations.
Also beware sponsored posts promoting prize pools or crypto giveaways. Facebook Ad transparency tools showing an advertiser named “Rockstar Fans” linking to shady portal sites should instinctively seem suspicious.
Spotting GTA VI Scams on Instagram
Scam Instagram accounts also steal branding elements from Rockstar’s verified @rockstargames profile. Usernames like “@rockstar_game” or “@rockstargamesgta” intend to deceive fans. Besides verifying the blue checkmark, compare follower counts since fakes have significantly lower numbers than the 61 million trailing the real Rockstar account.
Additionally, scam accounts display limited posting history focused exclusively on giveaway promotions. Rockstar’s Instagram features vast game asset diversity across thousands of colorful, high-quality posts.
Spotting GTA VI Scams on TikTok
Deceptive tactics seen on other platforms persist with TikTok as well. Impersonator accounts pretend affiliation with Rockstar by using edited logos and stolen game footage as backdrops.
Video captions drive urgency around fictional crypto contests, while comments filled with bot accounts amplify legitimacy claims.
However, the verified @rockstargames profile again allows differentiating countersuits. Red flags like low view counts on scam uploads hint limited authentic community interaction.
When In Doubt, Verify
Social networks all provide tools confirming whether brands maintain official presences. Seek verification before sharing data with any potential impersonators. Remain vigilant about guarding personal details to avoid not just gaming scams, but wider identity theft and cyber fraud.
What To Do If You Are A Victim
Falling prey to criminal crypto scams elicits gut-wrenching reactions as hard-earned assets get siphoned away. But succumbing to paralysis only compounds adversity. By promptly pursuing sensible reactive measures, investors can mitigate damages and regain their footing:
Step 1: Report The Crime
Immediately document fraudulent transactions by filing reports with relevant authorities at local and national levels. Provide as many specific identifiers, wallet addresses, and website details as possible to instigate investigations. Reports create official records that may aid tracking and recovery efforts.
Reputable crypto exchanges like Coinbase also operate dedicated investigation teams assisting scam victims. Filing cases directly through your wallet or exchange provider also helps get safeguarding resources engaged more quickly in some instances.
Step 2: Lock Down Compromised Accounts
Assume login credentials and financial systems are fully compromised in a breach scenario. Log into accounts from secure devices immediately to lock down access and reset all credentials. Enable two-factor authentication anywhere possible as added protection against repeat intrusion attempts.
Completely scrub machines infected with malware by performing factory resets and wiping drives. Backup critical personal files externally before wiping systems to limit lasting damage. Destroying malware footholds denies attackers further chances to inflict harm.
Step 3: Dispute Transactions
Most major cryptocurrencies allow users to flag transactions as unauthorized or fraudulent. Reporting disputed transfers freezes assets until reconciled, preventing liquidation. Work quickly to label any dubious outgoing transactions from your wallet so redeeming parties cannot abscond.
Blockchains cannot reverse fraudulent debits outright. However, coherent disputes accompanied by crime reports aid recovery efforts like law enforcement seizures envisioning repatriation. Documenting controversies also helps crystallize investigative priorities.
Step 4: Monitor Financial Accounts
Expand monitoring across banking and financial accounts in case attackers pivot towards auxiliary identity theft or fraud. Installing credit freezes prevents new lines of credit opening without consent as an extra fraud curb. Frequently reviewing account notices and statements helps sniff out emerging misuse swiftly.
Step 5: Seek Legal Counsel
Depending on breach severity, retaining professional legal guidance around navigating reporting, asset recovery, and civil action processes can prove invaluable for equipping victims with optimal recourse. Lawyers also help crystallize realistic expectations for restitution timelines, which often extend months based on response coordination.
Step 6: Place Emotional Health First
Traumatic financial crimes inflict deep personal wounds stretching beyond quantitative assets lost. Be compassionate with yourself while managing heightened emotions like violation, anger, confusion, and hopelessness. Seeking counseling or peer support groups helps process these feelings constructively during turbulent times. No investor is invulnerable to well-orchestrated cybercrime – don’t shoulder misplaced blame that will only slow eventual healing.
Frequently Asked Questions About the GTA VI Crypto Scam
The notorious frauds imitating Rockstar Games to swindle cryptocurrency investments spark urgent inquiries from concerned fans worldwide. Addressing critical areas of interests empowers investors to protect assets and enjoy GTA VI safely upon release.
Is Rockstar Games Really Giving Away Cryptocurrency?
No legitimate relationship exists between Rockstar and supposed “promotional giveaways” pledging Bitcoin or Ethereum payments. As a proprietary video game publisher, Rockstar focuses primarily on entertainment rather than direct cryptocurrency speculation or transfers.
Any contests sponsoring prizes as extravagant as “1,000 BTC” or “200 million DOGE” should automatically trigger skepticism. Comparable to lottery windfalls, such rewards remain virtually unattainable through random free distribution by any corporation.
Are the Rockstar and GTA VI Crypto Scams Global?
Research confirms the frauduleent campaigns have indeed secured footholds across international jurisdictions. Deceptive websites attracting traffic originate from hosting services within various countries attempting to disguise true registry.
Without geographic restrictions, the scam reaches any region where fans eagerly await GTA VI. Targeting is indiscriminate beyond markers of engagement like active crypto participation or gaming interest.
Is Fan Participation in the Scam Illegal?
While scam victims certainly gain unwanted attention from cybersecurity authorities, participants acting in good faith face no criminal charges themselves. Those submitting cryptocurrency operate under likely false assumptions rather than unlawful intents.
The orchestrators behind constructing fraudulent ecosystems should remain the exclusive subject of legal inquiries, provided targets demonstrate prudent cyber conduct moving forward. Still, inadvertently financing criminals rarely brings joy.
Is Rockstar Taking Action Against Scams?
Rockstar has not issued direct public comment addressing the reported GTA VI crypto scams. However, as an industry leader fighting against unfair usage of its intellectual property, swift preventative measures conducted firmly behind the scenes feel assured.
Trademark filings help restrict further branding dilution while legal pressure may shut down fraudulent operations entirely. Ongoing cooperation with authorities also seeks to indict actors responsible for orchestration and protect future game launches.
Vigilance remains essential from fans and investors as well until justice gets served completely.
Key Takeaway Points
- Verify cryptocurrency giveaways with brands directly before participating
- Enable multi-factor authentication to secure online assets
- Carefully inspect website domains, branding, and contact information
The Bottom Line
The allure surrounding GTA VI’s release has unfortunately attracted profound cybercriminal attention leveraging the game’s iconic status to anchor deceptive crypto scams. Lured by prospects of giveaways, rewards, or prize pools, unsuspecting fans instead get stripped of their invested assets after engaging with fraudulent websites.
By recognizing the quintessential warning signs of such frauds, sidestepping participation urges, and responding swiftly if exposed, investors have tools to limit damage inflicted by schemes impersonating beloved brands. As cybercrime larger evolves in sophistication, nurturing one’s cybersecurity and fraud detection capabilities serves as a timeless safeguard.










