In the fast-moving world of cryptocurrency, scams are unfortunately inevitable. As cryptocurrencies gain mainstream traction, scammers have come up with ever-more sophisticated ways to exploit unsuspecting victims. One such scam that has been making the rounds recently is the “Tesla X Wallet” cryptocurrency giveaway fraud.
This extensive article will provide a deep dive into how the Tesla X Wallet scam operates, how to identify fake offers and websites, the techniques scammers use to ensnare victims, how to avoid falling prey, and what steps you can take if you have fallen victim.
What is the Tesla X Wallet Scam?
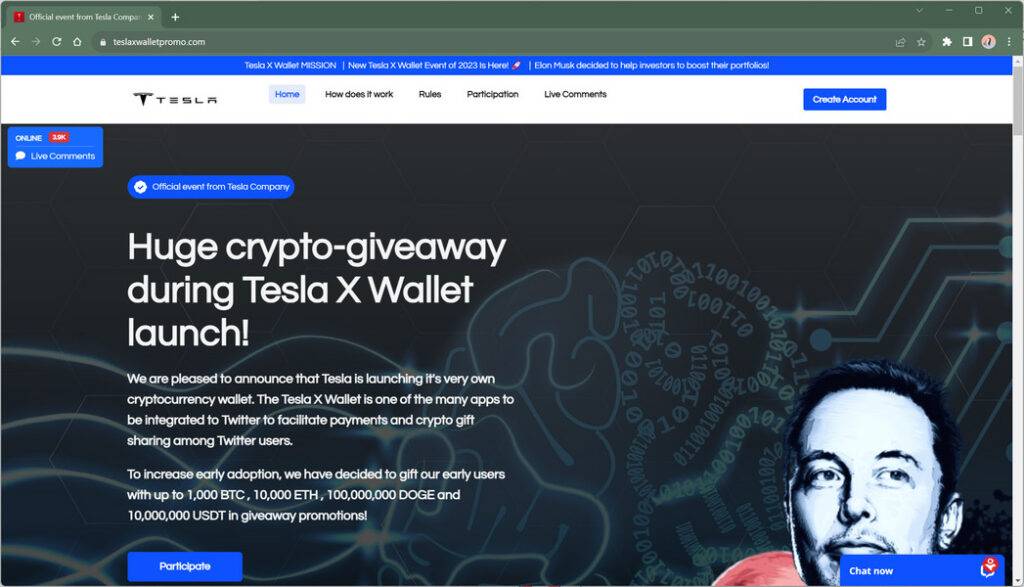
The Tesla X Wallet scam is essentially a fake cryptocurrency giveaway fraud that uses Tesla’s brand without authorization. The scammers create social media posts and websites that falsely claim Tesla is releasing a new cryptocurrency wallet and is giving away cryptocurrencies like Bitcoin, Ethereum and Dogecoin to promote it.
The scam promoters use Elon Musk’s name and image prominently to mislead victims into thinking the giveaway is real and endorsed by Tesla’s CEO. However posts, images, website and promises are completely fake with the sole intention of stealing cryptocurrency deposits from unaware victims.
This scam follows the blueprint of many other fake crypto giveaways and lottery frauds. By dangling free money in front of unsuspecting users, the scammers can easily pocket deposits from those looking to cash in on what seems like easy money.
How the Scam Spreads
The Tesla X Wallet scam relies on two main methods to reach as many potential targets as possible:
Social media – The scammers aggressively promote the fake offers via social media like Facebook, Twitter, Instagram, YouTube and TikTok. Images containing fake tweets from Elon Musk are created and shared along with the scam website and wallet addresses. These posts are boosted to reach more users.
Fake websites – Elaborate scam websites are set up like teslaxwalletpromo.com and teslacryptogiveaway.com. These sites contain fictitious information about the launch of the Tesla wallet, fake news updates, false claims of large payouts, and doctored images depicting Elon Musk.
By spreading across social media and creating authoritative looking scam websites, the promoters can make the giveaway appear legitimate and build hype around the offers. The ultimate goal is to get as many people as possible to visit the site and send cryptocurrency.
Hallmarks of the Tesla X Wallet Scam
The Tesla X Wallet scam exhibits typical red flags found in the majority of giveaway frauds. Being able to identify these signs can help you avoid becoming a victim. Some notable characteristics include:
- Too good to be true claims – The promises of huge free cryptocurrency payouts in exchange for a small deposit are always exaggerated lies. Legitimate giveaways never require an upfront payment.
- Fake celebrity affiliation – The scam prominently uses Elon Musk’s name and image without his permission to appear credible. Any endorsement by Musk is completely false.
- Aggressive hype techniques – Scam websites utilize tactics like fake news stories, false scarcity and fake user comments to create hype and FOMO. This pressures visitors to act quickly.
- Dodgy website – Scam sites have grammatical errors, anonymous domains registered recently and other unprofessional red flags. Some even steal content from legitimate websites.
- No verified registration – The entities behind scams remain anonymous with no company registration or documentation provided on the site. Contact details are also usually fake.
- Cryptocurrency only – Scammers only ever ask for payment in cryptocurrency like Bitcoin since such transactions are irreversible once sent. Fiat payments can be more easily recovered and traced.
No actual product or service – Beyond vague claims, no real product, company or innovation actually exists. The only purpose is to collect payments.
Staying alert for these signs can help you detect and avoid cryptocurrency giveaway scams before becoming their next victim. If it looks suspicious, it most likely is.
Scam Tactics Used Against Victims
Scammers employ a variety of psychological tricks and persuasive tactics to convince victims to send money. Some techniques witnessed in the Tesla X Wallet scam include:
- Appealing to greed – The most common tactic is promising free or easy money. People tend to abandon caution when presented with a chance to profit.
- Faking authority – Scammers use the Tesla brand and Elon Musk’s image to portray legitimacy and credibility to overcome doubts.
- Manufacturing urgency – False claims of limited time offers and fake notifications of limited slots remaining pressure visitors to act quickly.
- Building social proof – Fake comments, reviews and activity notifications provide a false sense of security in numbers to reinforce the scam’s authenticity.
- Layering on incentives – Additional bonuses and payouts are offered if more cryptocurrency is sent. This hooks victims to invest more and more into the scam.
- Blaming the victim – If any issues arise, scammers accuse the target of making a mistake to force them to send additional funds to “fix” it.
Falling for such techniques is not a personal failure. Scammers are masters at psychological manipulation. Being aware of these tactics can help resist their effectiveness.
How Does the Scam Work?
Now that we have explored the background of the Tesla X Wallet scam, let’s examine the step-by-step process of how the scam unfolds:
- Bait – The first step is posting enticing offers on social media and scam websites promising free crypto if users deposit a small sum into a provided wallet.
- Hook – When users visit the site, further false claims, fake endorsements, and pressure tactics convince visitors to participate.
- Payment – Enticed users are instructed to deposit cryptocurrency into the scammer’s wallet address to register for the fake giveaway.
- Stalling – After receiving payment, scammers claim further funds are needed for fake fees, taxes, or transaction charges.
- Disappearance – Once payments stop flowing, scammers cut off all contact and disappear with the stolen funds.
- Damage Control – Angry users try reporting the scams and contacting scammers, but rarely recover lost funds. The scam cycle continues with new victims.
By following this process, scam operators can rake in a significant amount of illicit income with little effort. The ease of scamming highlights the need for caution when dealing with offers that seem too good to be true.
Can Victims Recover Lost Funds?
The unfortunate truth is recovering funds lost in cryptocurrency scams is extremely unlikely. Unlike bank transactions and credit card payments, cryptocurrency transfers are designed to be irreversible and untraceable. This makes retrieval nearly impossible.
If caught very early, wallet providers may be able to stop or reverse transactions in some cases. But the chances diminish the longer the scam goes on. Cryptocurrency sent to scammers is likely gone for good.
This points to the importance of identifying and avoiding scams proactively rather than attempting to recover losses reactively. Prevention is by far the best solution. Promoting awareness also helps protect others from falling victim and limit the scammer’s success.
How to Stay Safe from the Tesla X Wallet Scam
Here are proactive tips to avoid falling prey to the Tesla X Wallet scam and other similar cryptocurrency frauds:
- Avoid random offers – Be wary of giveaways and deals promoted via unsolicited messages, emails and ads. Only deal with trusted sources.
- Verify legitimacy – Thoroughly research any giveaway promotion, website and entity to uncover red flags and ensure authenticity.
- Beware of endorsements – Scammers fake endorsements from celebrities like Elon Musk. Verify all claims directly with official sources.
- Check account details – Review the history, post patterns and follower counts of accounts spreading offers to spot fraudulent accounts.
- Analyze site quality – Evaluate the domain age, editing quality, contact info, and legal pages of any website you visit.
- Never send unsolicited funds – No legitimate reason exists to send payments to claim giveaway winnings, release bonuses, or pay fees.
- Enable security measures – Use wallet protections like 2FA and multi-signature to add layers of security for your cryptocurrency.
- Stay updated – Keep learning about the latest cryptocurrency scams and threats to more easily avoid becoming a victim.
Exercising skepticism, verifying every offer extensively, and never sending payments or deposits unless completely certain can go a long way in protecting yourself from crypto scams.
What to Do if You Are a Victim
If you unfortunately sent cryptocurrency and fell victim to the Tesla X Wallet scam, here are some recommended steps to take:
- Report the scam – Alert relevant websites, social networks, wallet providers and authorities to try getting scam pages blocked and taken down.
- Warn your network – Let your followers and friends know about the scam to prevent the news of it spreading further.
- Do not send more funds – Under no circumstances should you send additional payments to the scammers for any reason whatsoever.
- Check for transaction reversals – Some wallets providers can reverse unauthorized transactions made quickly. But options are very limited.
- Gather evidence – Collect screenshots, wallet addresses and transaction details that may assist authorities in investigating the scam.
- Seek legal counsel – Consulting a lawyer experienced in cryptocurrency fraud may reveal options for recovering losses through legal means.
- Learn from the mistake – While losing funds is extremely frustrating, treat it as a lesson for the future. Be more vigilant to avoid repeating the same mistake.
- Spread awareness – Share your experience and warn others about the scam. This helps curb the scam’s spread and limit the scammers’ success.
Though the chances of getting money back after a scam are low, taking proactive measures can at least help prevent further losses by you and others.
The Future of Crypto Scams
As cryptocurrencies continue gaining prominence, related fraud schemes are inevitably going to rise as well. The pseudonymous and irreversible nature of cryptocurrency makes it extremely lucrative for criminal entities.
Scams are also becoming more sophisticated with the use of fake celebrity endorsements, artificial hype techniques, social media marketing and bait offers of free cryptocurrency giving away money.
Staying vigilant requires keeping up with the ever-evolving cryptocurrency scamming landscape. Some emerging scenarios include:
- AI-generated profile photos – Scammers are using AI to generate fake but realistic profile photos to create more believable fraudulent accounts.
- Deepfakes – Videos of celebrities like Elon Musk promoting scams can now be faked using deepfake technology.
- Mass customization – Automated tools allow scammers to customize scam websites and messages for individual targets at scale.
- New platforms – Expect scams to grow on Web3 platforms, metaverse worlds, and throughout decentralized finance markets.
Regulation – Government policies on marketing, consumer protection, identity verification and cryptocurrency transactions could help address certain vectors enabling scams.
The information security industry will need to continue innovating to help identify and mitigate new forms of cryptocurrency fraud. On the user level, maintaining vigilance, verifying diligently, and keeping knowledge levels current is essential.
Conclusion
In closing, the Tesla X Wallet scam offers a blueprint into how cryptocurrency giveaway frauds operate, tactics scammers use, and key steps the public can take to avoid falling prey. With cryptocurrency adoption increasing, users must exercise ample caution to avoid losing hard-earned money.
Heeding warning signs, resisting pressure tactics, verifying offers extensively, and never sending unsolicited funds can help protect you from the Tesla X Wallet scam. Equipping yourself with the knowledge and tools to trade cryptocurrency securely is the most effective way to steer clear of scams as cryptocurrencies become further integrated into the financial mainstream. Share your knowledge and help spread awareness to others.


![Remove Rentecterapplic.co.in Pop-up Ads [Virus Removal Guide] 10 McAfee scam 4](https://malwaretips.com/blogs/wp-content/uploads/2023/08/McAfee-scam-4-290x290.jpg)